Searching and filtering submission cards
This is what you can do in the filters area:
Search and filter submissions by various criteria. The page will automatically load only the security event cards matching the selected criteria.
Reset filters by clicking the Clear Filters button.
Hide or show the filters area by clicking the corresponding button.
Note
As a Partner, you can view submissions from direct companies even after their license keys expire.
You can search and filter the Sandbox Analyzer submissions by the following criteria:
Company name. From the drop-down list next to Show/hide filters, select all direct companies or the specific company for which you want to see submissions. By default, this page displays your company's submissions.
Sample name and hash (MD5) - Enter in the search field a part or the entire name or hash of the sample you are looking for, then click the Search button.
Note
The displayed cards contain the name of the company on whose behalf the submission was made. You cannot use the company name in the search field.
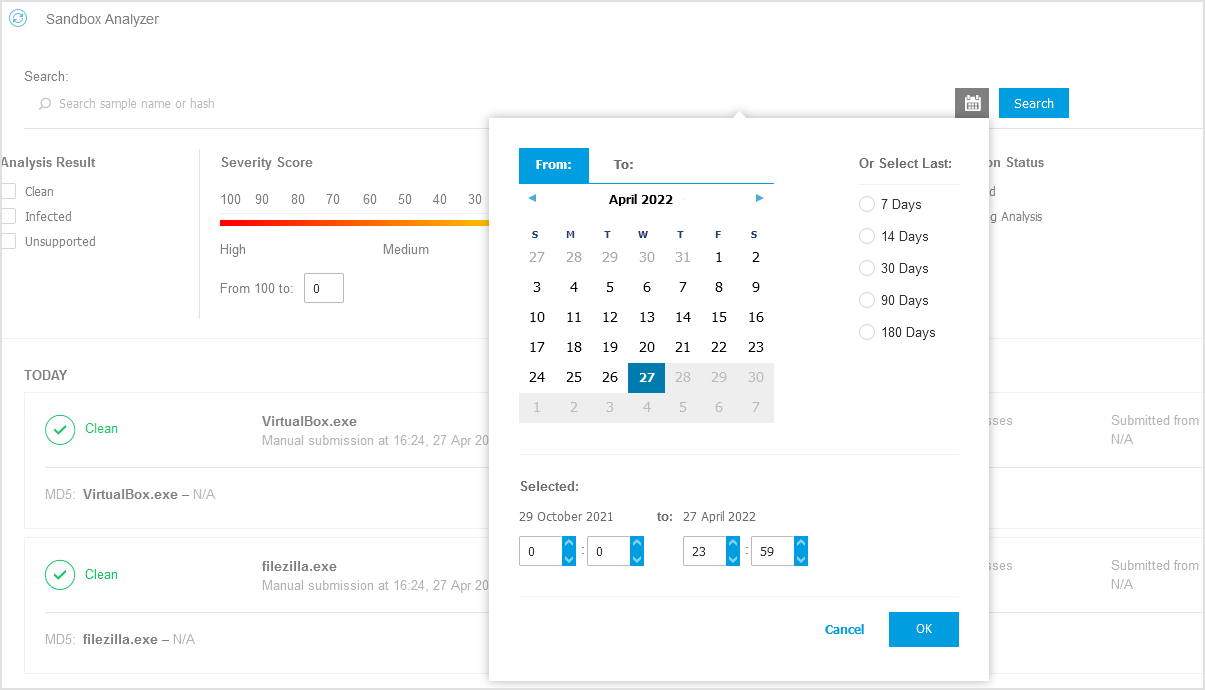
Date - To filter by date:
Click the
 calendar icon to configure the searching time frame.
calendar icon to configure the searching time frame.Click the From and To buttons to select the dates defining the time interval.
You can also select a predetermined period from the list of options, relative to the current time (for example, the last 30 days).
You can also specify the hour and minutes for each date of the time interval, using the options beneath the calendar.
Click OK to apply the filter.
Note
Date and time are reported according to your local settings.
Analysis result - Select one or more of the following options:
Clean – the sample is secure.
Infected – the sample is dangerous.
Unsupported – the sample has a format that Sandbox Analyzer could not detonate. To view the complete list with file types and extensions supported by Sandbox Analyzer, refer to Supported File Types and Extensions for Manual Submission.
Severity score - The value indicates how dangerous is a sample on a scale from 100 to 0 (zero). The higher the score, the more dangerous the sample is.
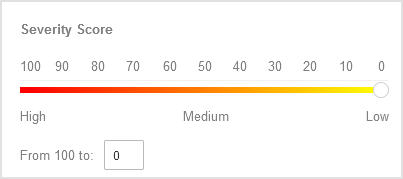
Note
The severity score applies to all submitted samples, including those with Clean or Unsupported status.
Submission type - Select one or more of the following options:
Manual - Sandbox Analyzer has received the sample via Manual Submission option.
Endpoint sensor - Bitdefender Endpoint Security Tools has sent the sample to Sandbox Analyzer based on policy settings.
Submission status - Select one or more of the following check boxes:
Finished – Sandbox Analyzer has delivered the analysis result.
Pending analysis – Sandbox Analyzer is detonating the sample.
Failed – Sandbox Analyzer could not detonate the sample.
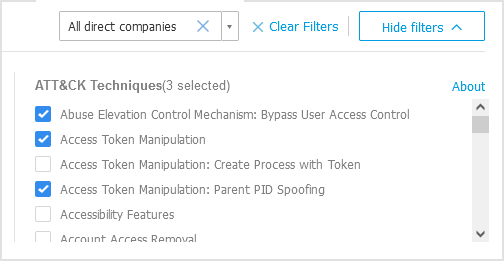
ATT&CK techniques. This filtering option integrates MITRE's ATT&CK knowledge base, if applicable. The ATT&CK techniques values change dynamically, based on the security events.
Click the About link to open ATT&CK Matrix in a new tab.