Using the Mobile Security apps
Device
In the dashboard, the Device tile displays the current state of the device itself. Examples of threats that show up in this category include:
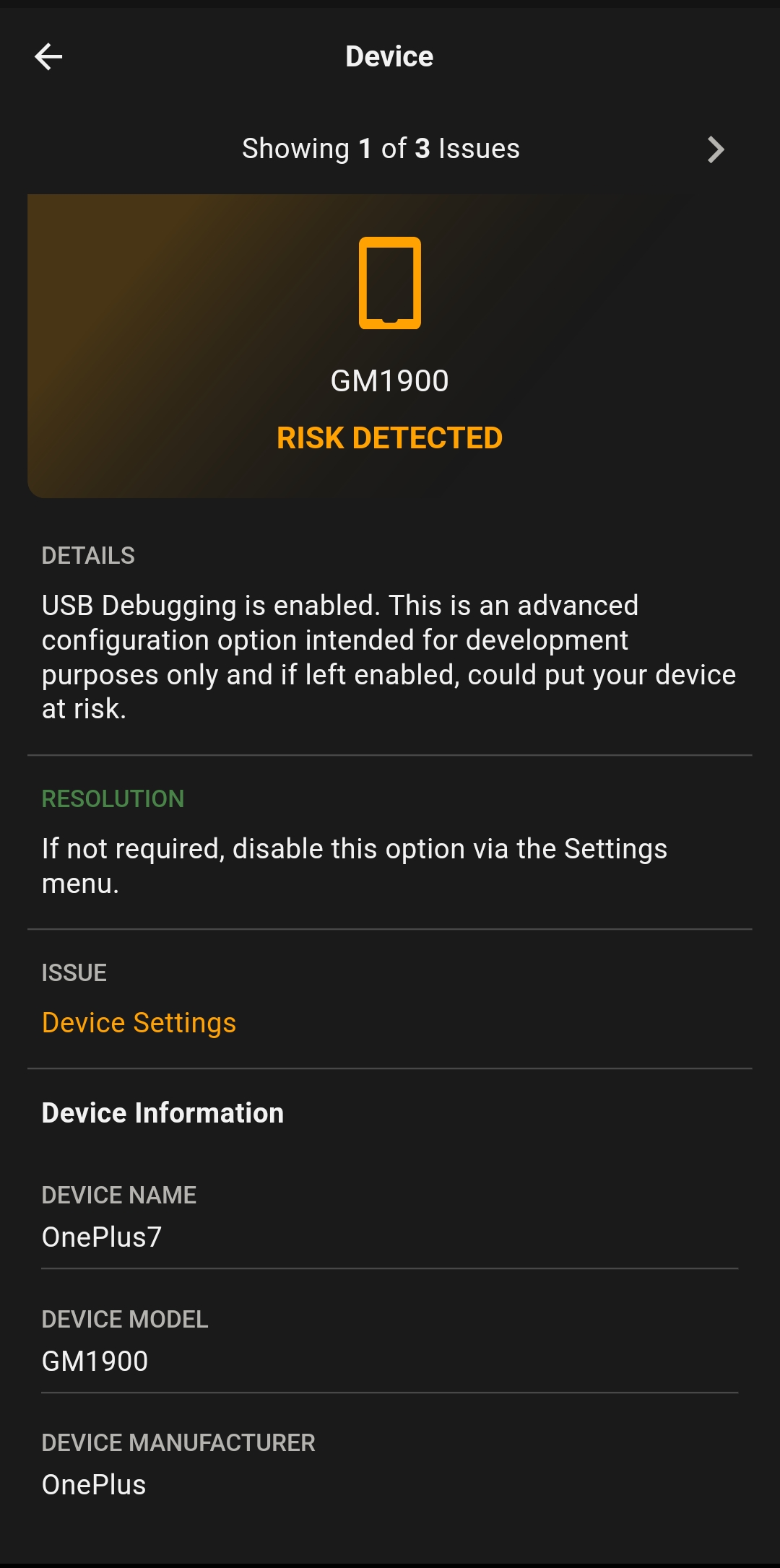
App Tampering
Device Jailbroken / Rooted
File System Changed
Selecting this category navigates to the Device page. Critical events or risks display issue items with details and Yes/No values. The GravityZone MTD uses color codes to indicate issue severity. Title bar turns red when a critical threat is detected according to the Threat Policy.
Yellow bar = risk detected
Green bar = no risks/threats detected.
If any detections are set to Yes, tap the down arrow for recommendations and additional item information.
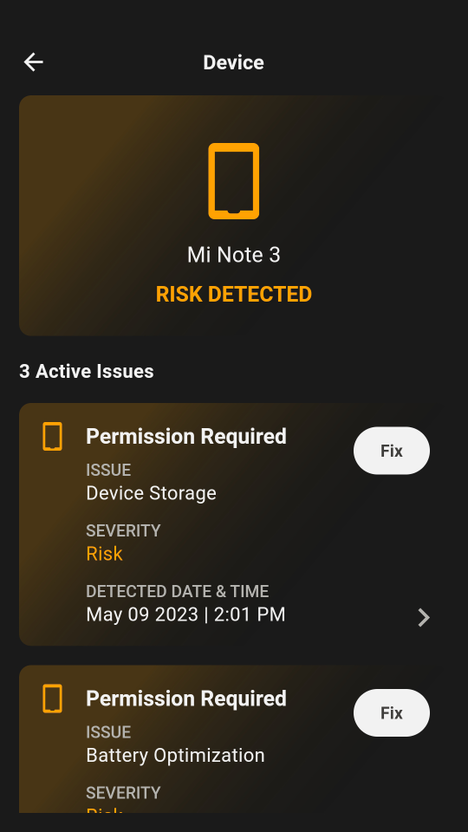
If you press Fix, a screen with details and resolution displays.
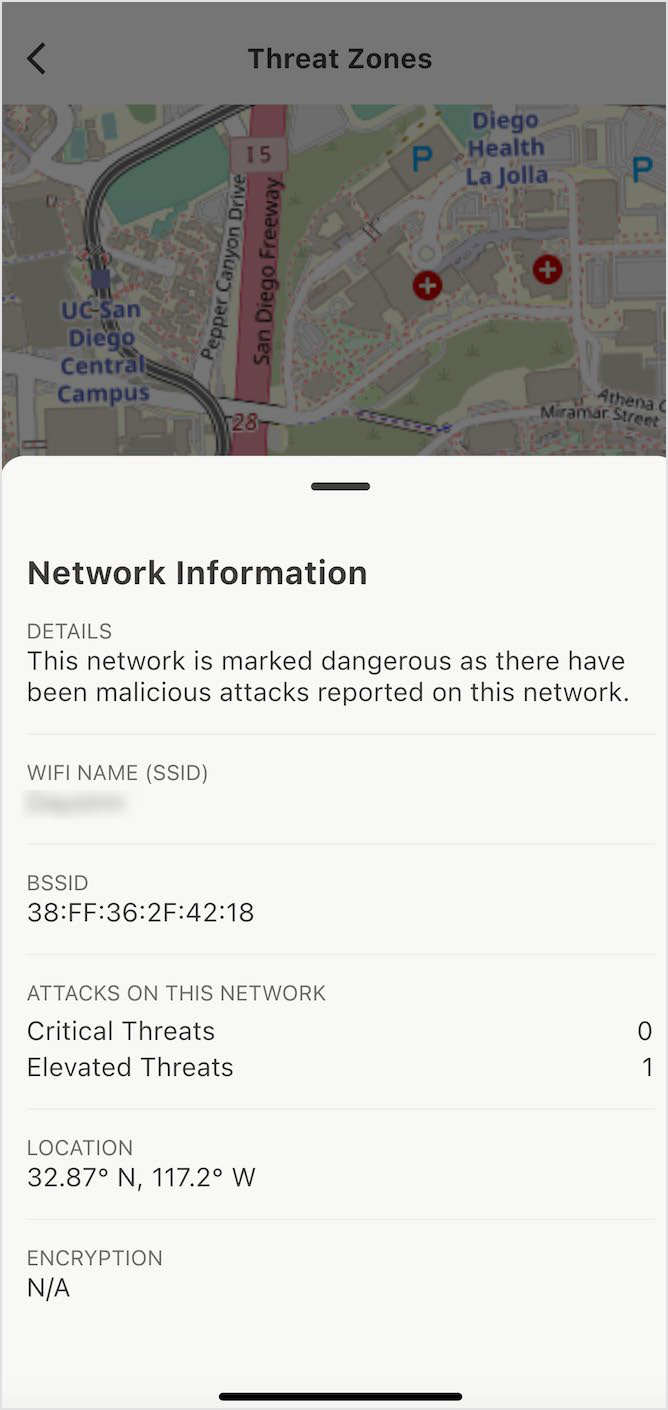
Threat Zones
Travelers often connect to Wi-Fi networks for internet access. Open Wi-Fi networks can be traps for attackers who exploit victims seeking access to gain their information.
Threat zones indicate high-risk networks to avoid. These are known as Danger Zones. To select a network, access the app and click on Threat Zones.
Admin can customize the Threat Zones tile display and alerts for threat zone functionality. Alert text settings are configured in the Policy page, like other threat management settings. The user can mark a network as trusted on their device to avoid future prompts.
Using the Threat Zones map
The feature displays a map that is initially based on the user's location. The presented map displays red markers that indicate the presence of nearby high-risk networks. The red icons displaying numerical values indicate the quantity of identified threats on access points that are deemed high-risk. The zoom in and out functionality can be accessed by performing a two-finger gesture on the screen.
Pressing an icon dives deeper into the location chosen, and eventually to the SSID for nearby or unsecured Wi-Fi networks.
Location permission prompt on the Threat Zones tile
A location permission prompt on the Threat Zones tile improves users' privacy. When the user logs in to the MTD enabled device, the MTD app will request a location permission only when the user uses the Threat Zones feature, and when the following conditions are met:
Location is set to None under Manage > Privacy
Location permission required for iOS or Android are disabled in policy
Danger Zone functionality is enabled under Manage > General
The user can manage location access from the Android system option. If location permission is denied, a default location is displayed. This ensures that location data is accessed only when needed, reducing unnecessary data collection.
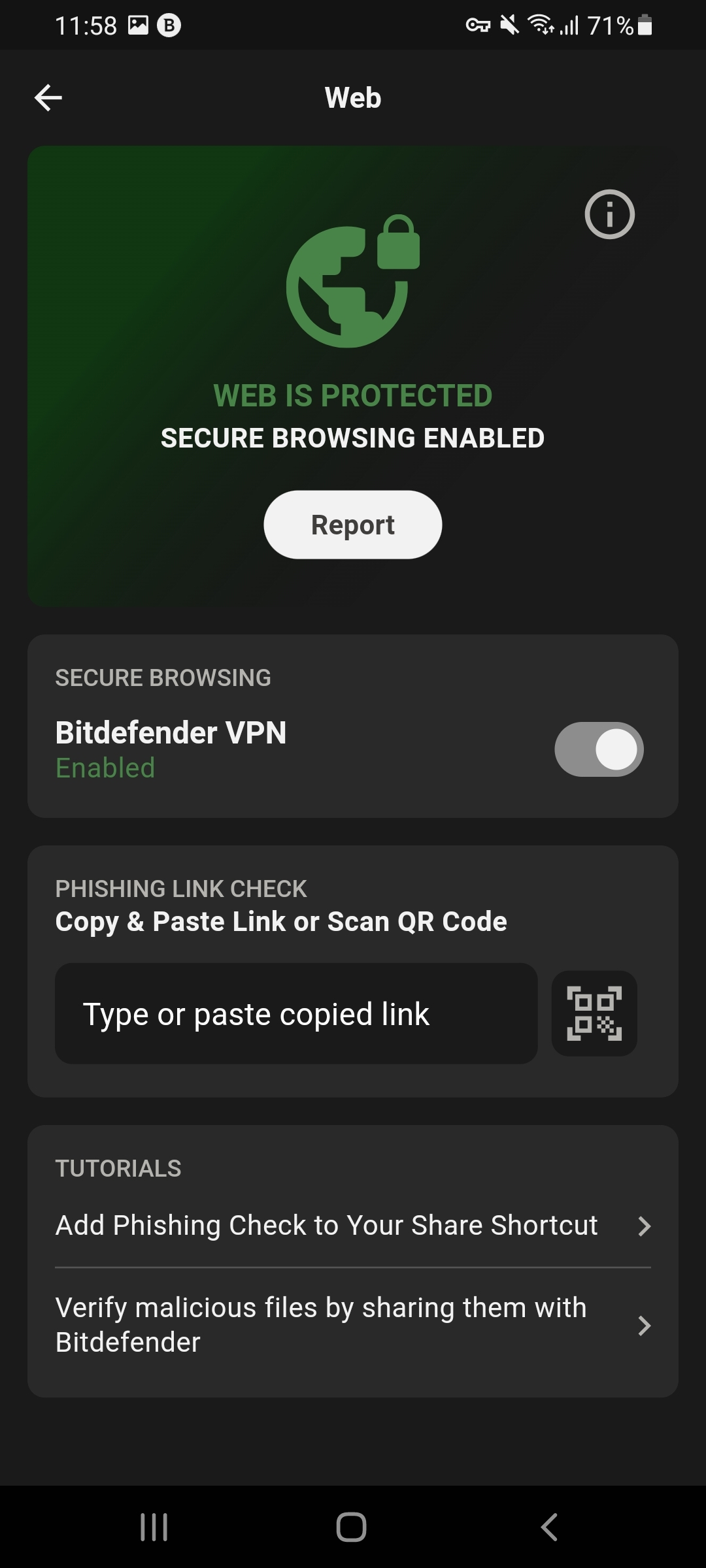
Mobile Security web threat protection
The GravityZone MTD system performs a check for phishing links and has the capability to activate or deactivate VPN connections based on the policy settings configured on the GravityZone MTD.
The system employs web content filtering to alert and safeguard users against accessing potentially hazardous websites and links, including malware, phishing, botnets, and suspected domains.
The GravityZone MTD offers users options to safeguard themselves against hazardous phishing links through SMS/MMS protection and the Safari browser on iOS, without requiring the VPN to be configured.
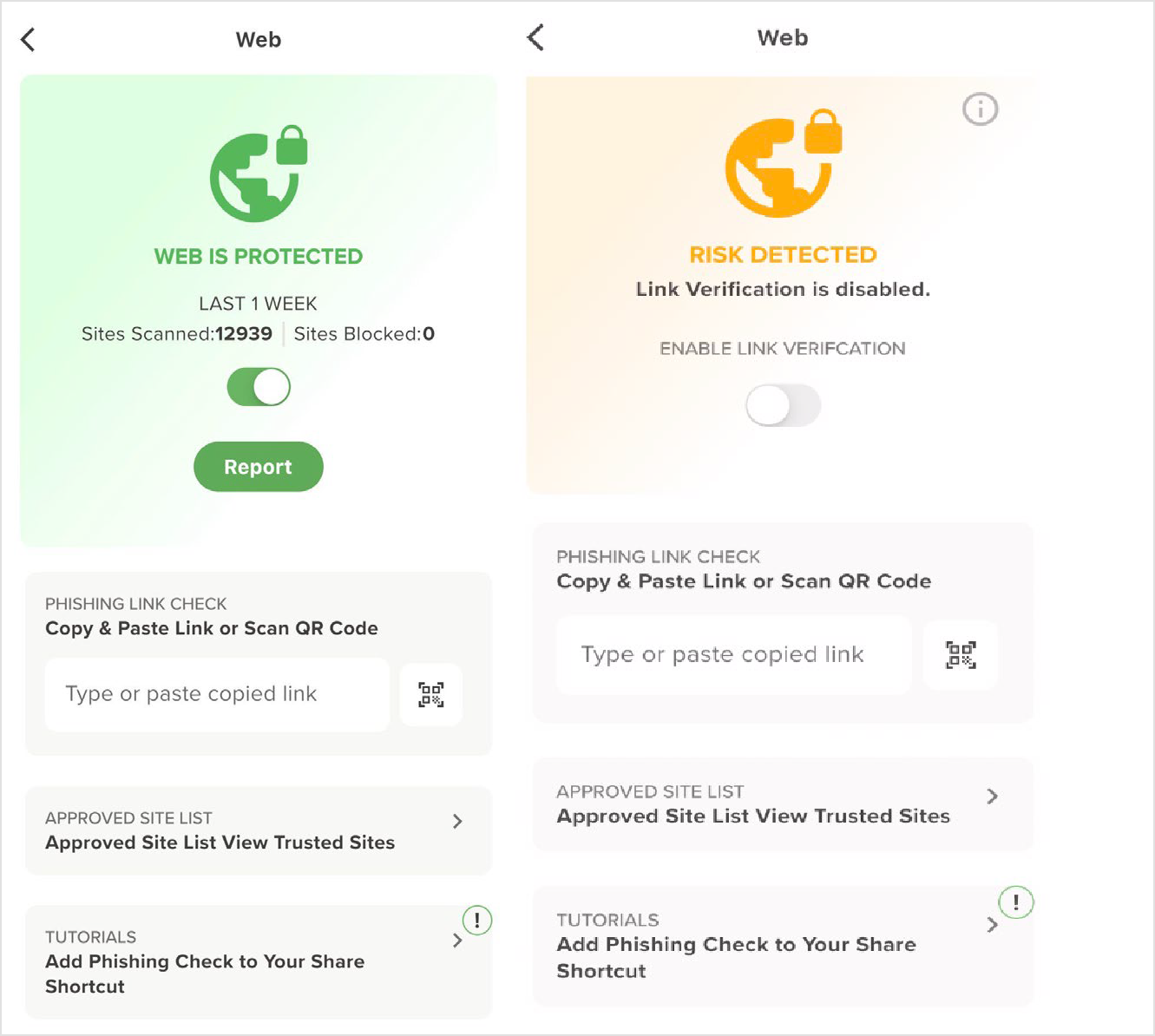
It is possible to define a fresh action for content filtering categories, which involves preventing access and potentially generating a notification. The Web tile in the dashboard exhibits the current state of threat detection, which is represented by the colors red, yellow, or green. Selecting this tile will navigate to the Web interface.
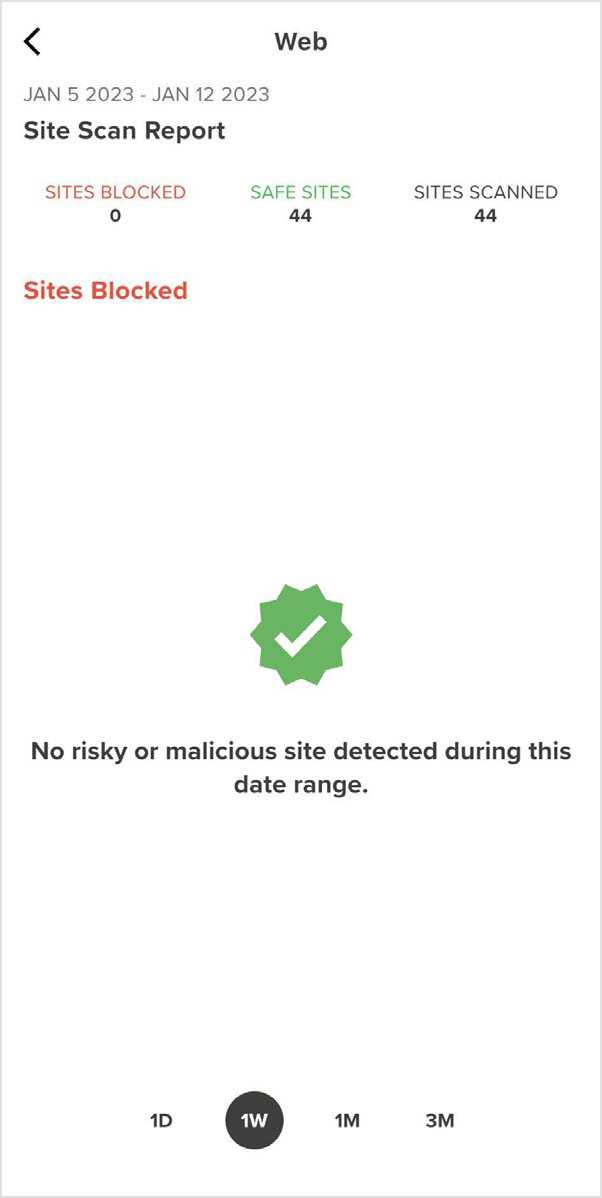
If you press the Report button, a Site Scan report displays. This report shows the number of sites that are blocked and their URLs, along with the number of safe sites and sites scanned.
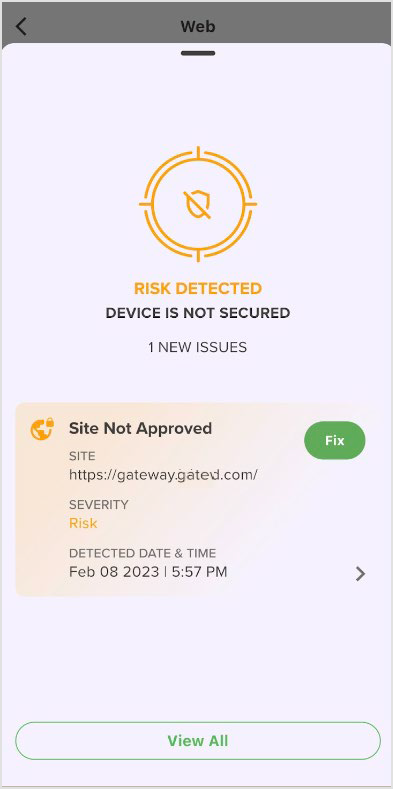
If a threat is detected the following screen will be displayed.
When you click on the threat, the following screen displays. If the administrator sets a site to alert the user instead of blocking that site, options to Continue Anyway and Mark this site as “Trusted” appear for the user to select if they choose to bypass the warnings in the future.
Phishing and Content policy
The phishing and web content filtering policy enables an administrator to establish measures for safeguarding users against accessing potentially harmful websites and links. These may include malware, phishing, botnets, and suspected domains that contain risky content.
Note
For best results, we recommend activating the VPN when using Web content filtering and standard phishing protection.
You can specify a new content filtering category action to block and optionally create an alert.
Actions that can be set include:
Alert the user giving a warning.
Alert the user giving a warning and create a threat.
Block the site.
Block the site and create a threat.
Block the site and do not create a threat.
The GravityZone MTD offers website categorization to users who receive alerts or perform safety checks on websites. This feature is contingent on the administrator's activation of content filtering and provides information on the website's category, such as gambling or illegal drugs. This guidance provides the user with instructions on how to determine the appropriate course of action to take.
When a specific website category or URL is determined to be harmful, it is blocked. An alert displays when a site is accessed from the browser, which includes the site and category.
Checking for phishing risk
When you press the Web dashboard tile, the screen shows the protection available for insecure (HTTP) connections. To check a link for phishing risk, you can:
Type or paste a copied link.
Press the QR code icon and scan a QR code. You will be prompted to allow the GravityZone MTD to use the camera.
Additional phishing protection with iOS
The GravityZone MTD offers alternative methods for continuously protecting you from malicious and risky links that are either displayed by the Safari browser or contained in SMS/MMS messages.
Protection When Running the iOS Safari Browser - The GravityZone MTD enables the expansion of anti-phishing and web content filtering capabilities to the Safari browser on iOS mobile devices. It can install a Safari extension provided that the administrator has enabled this functionality. The extension can be enabled manually to grant the required permissions for it to operate on browser pages. To utilize this feature, it is necessary to have either the Phishing Protection policy or the Enhanced Phishing Protection plus Web Content Filtering policy enabled in the GravityZone MTD. The feature does not necessitate the VPN Link Verification permission.
Protection from Risky Links in iOS SMS/MMS Messages - The GravityZone MTD enables anti-phishing for the Messages app on iOS mobile devices. This feature offers an alternate way to protect GravityZone MTD users from harmful links in SMS and MMS messages.
This feature blocks risky SMS links in Messages app and displays all blocked messages in a separate folder.
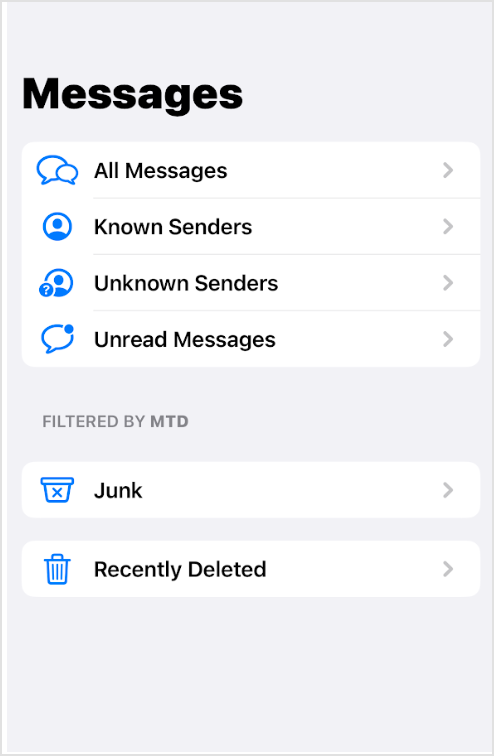
Enabling SMS message filtering moves risky messages to a separate folder in the Messages app. This feature enhances protection against risky and malicious links.
Additional phishing protection with Android
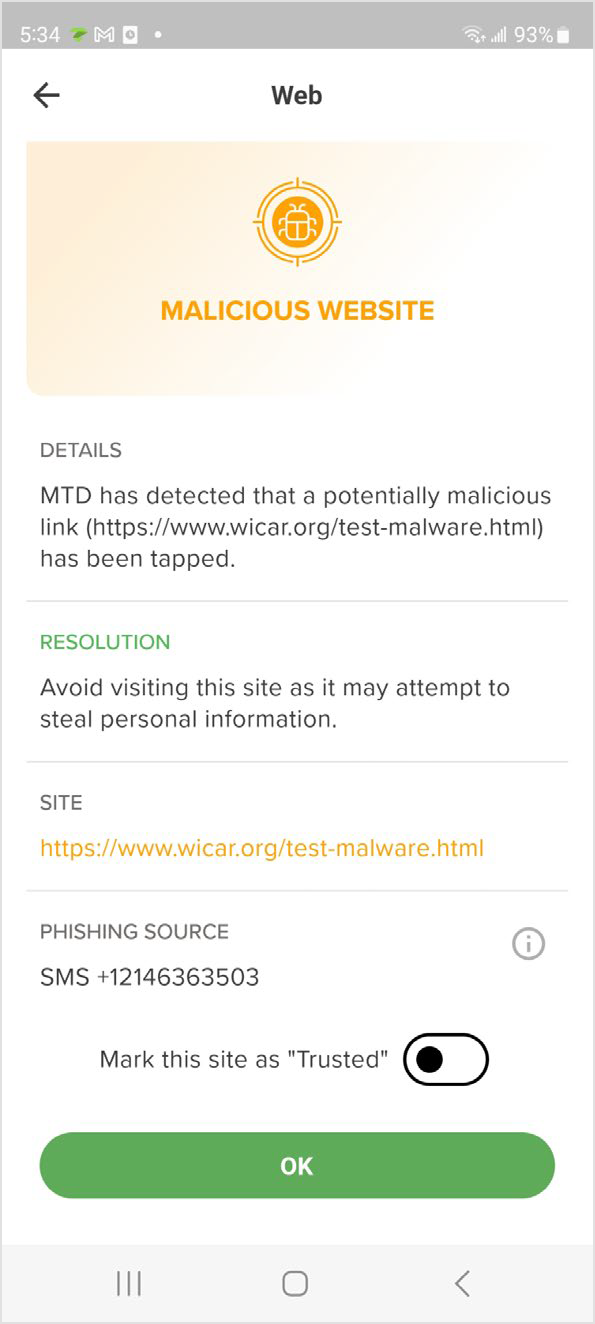
Protection from Risky Links in Android SMS/MMS Messages - The GravityZone MTD enables anti-phishing for the Messages app on Android mobile devices. This feature protects GravityZone MTD users from clicking malicious links in SMS and MMS messages on their device.
Enable the feature in the GravityZone MTD in Phishing or Web Content Filtering policy and obtain the user's permission in Android for detecting risky links in messages. This feature identifies and notifies users of potentially harmful links in SMS/MMS messages within the Messages app prior to user interaction. Threat details include message phone number with risky link.
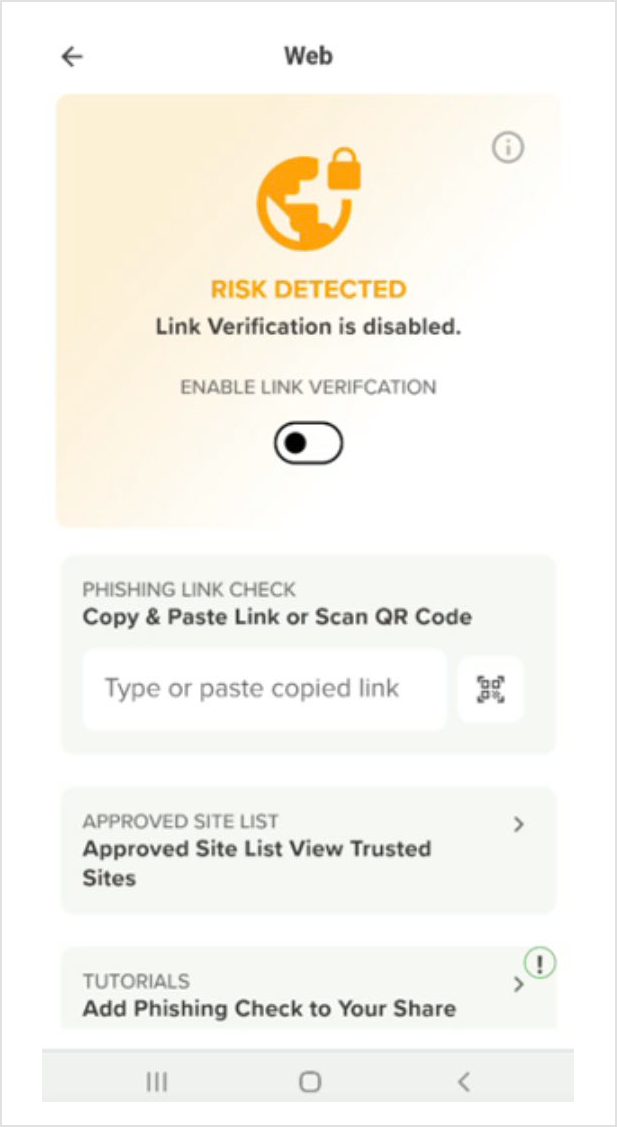
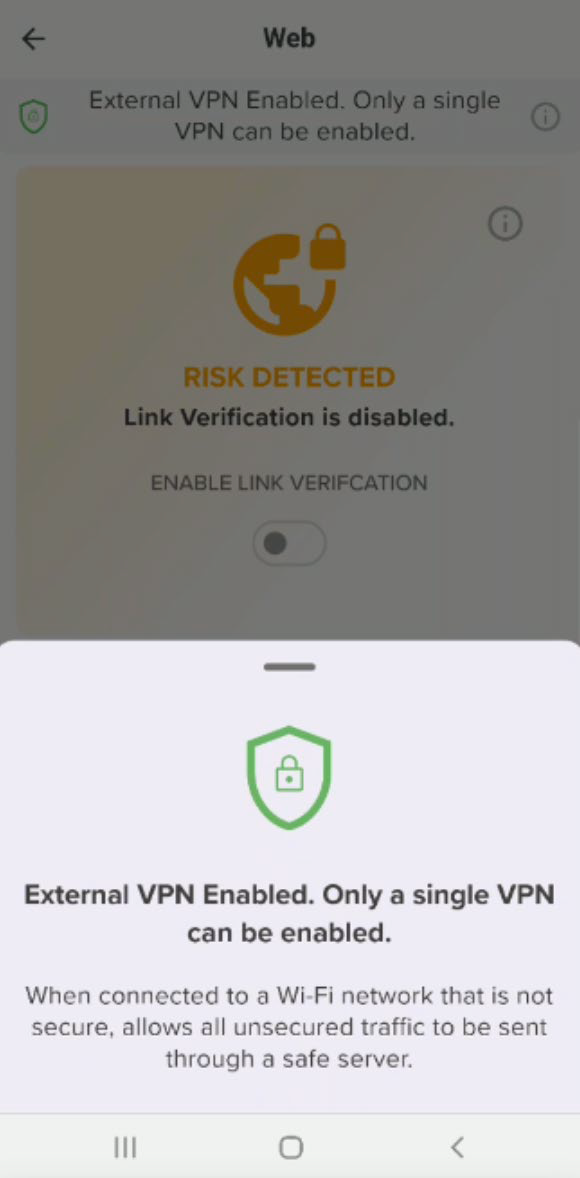
Enabling Link Verification - If enabled by the administrator, the user is able to toggle Enable Link Verification on and off as shown in this figure.
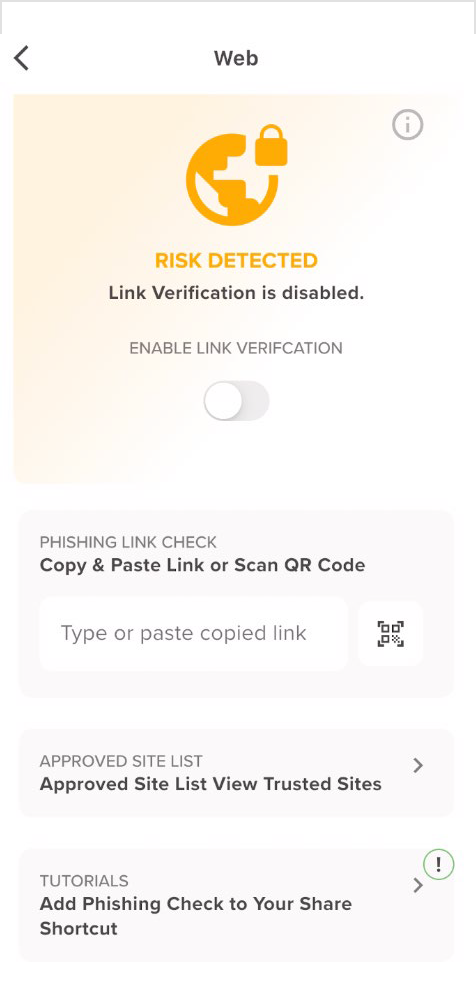
If the link is risky, the app displays a screen indicating the status, along with details, resolution, site, and category. You can enable the Mark this site as Trusted to bypass this warning and proceed to the site without being alerted again.
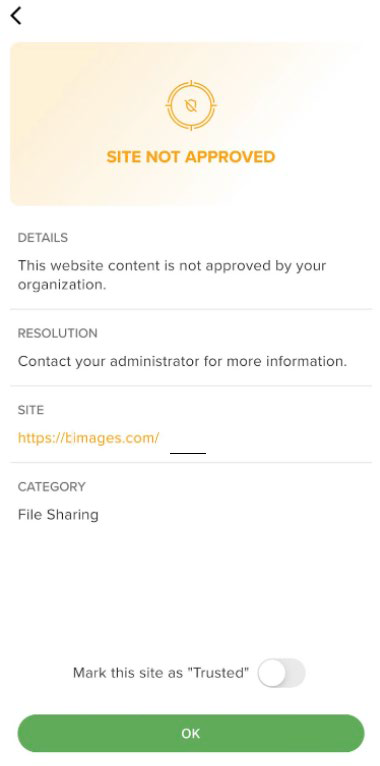
VPN Protection - In order to activate Link Verification on the device, it is necessary to grant permission to the GravityZone MTD to include the local VPN on the device.
The local Virtual Private Network (VPN) serves the purpose of identifying and obstructing potentially hazardous hyperlinks on the device. The local VPN has the capability to tunnel unsecured Wi-Fi traffic when it is properly configured within the GravityZone MTD policy.
After the successful establishment of the VPN configuration on the device, a notification will be presented to the user whenever the device detects an endeavour to connect to an unsecured Wi-Fi network. The app system facilitates the automatic establishment of a secure Virtual Private Network (VPN) connection between the device and the network. This VPN connection encapsulates and transmits potentially vulnerable (HTTP) traffic over the unsecured Wi-Fi network.
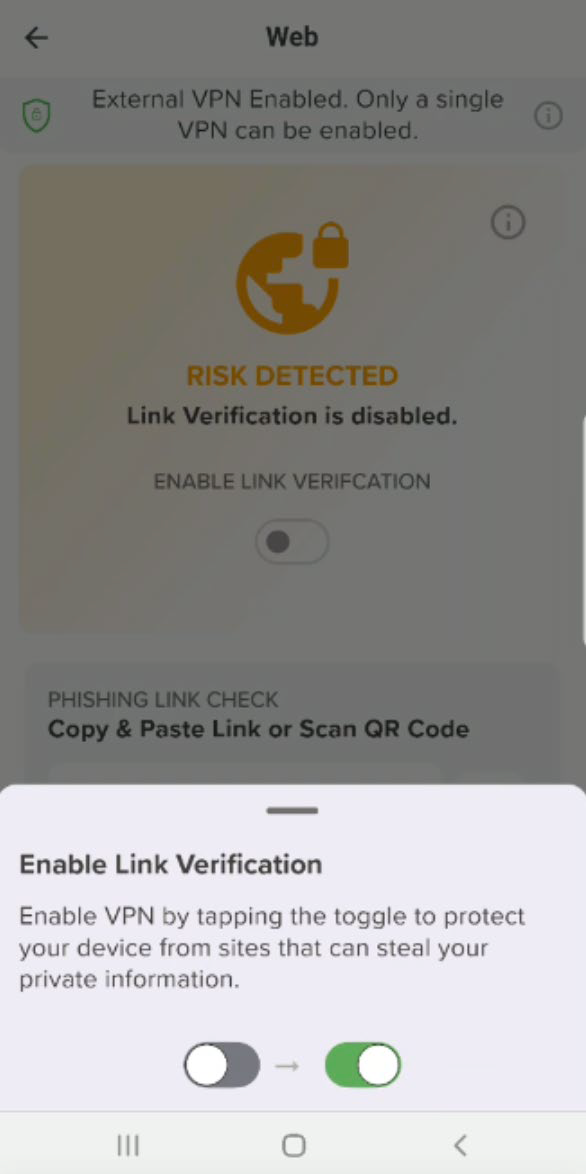
If you toggle Enable Link Verification on, a popup displays.
The following message displays as confirmation that link verification is enabled.
GravityZone MTD threat protection
The GravityZone MTD scans specific categories for threats to your security. These categories are displayed in tiles on the dashboard:
Apps
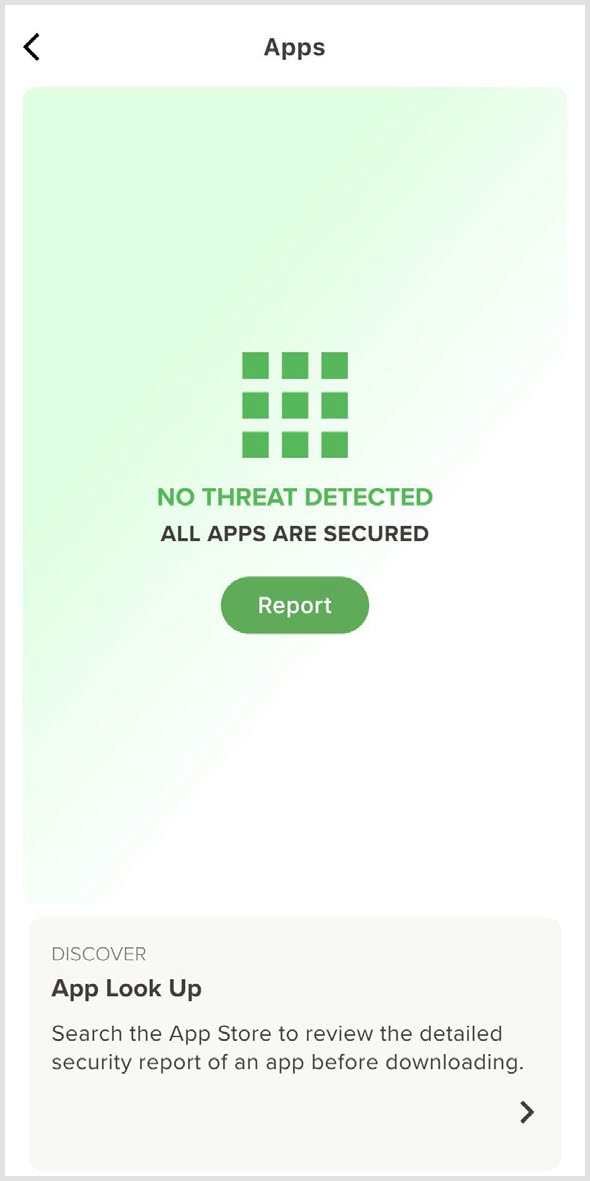
The Apps tile in the dashboard presents the current status of the system. Selecting this tile will navigate the user to the Apps interface.
The status is indicated by the colors green, yellow, or red.
Green signifies that no threats have been detected.
Yellow indicates the detection of risks.
Red indicates the detection of threats.
If a risky app is found, the screen provides the user with information on the application and a recommendation on how to proceed.
Categories for risky apps include:
Suspicious apps are installed and are high risk. They have the potential to compromise the device.
Sideloaded apps were installed outside of the Google Play Store or App Store. They have not been officially validated and are considered risky.
Out of Compliance (OOC) apps, which have characteristics that do not comply with the organization’s privacy and security policies.
Note
iOS will only provide access to the apps if the app is used with an MDM.
Application scanning
The GravityZone MTD automatically scans the device for risky apps when it is initially installed. Apps are also scanned when they are downloaded and installed.
Searching apps to determine risk
Users can search for an app from a comprehensive database to ensure its safety before installing it on their device. The application's privacy and security rating is presented in a concise format, allowing users to assess whether it may pose a risk to their device. The app risk report for currently installed apps can be viewed on Android devices. Non-English language searches are also supported.
The App Risk Lookup feature must be activated from the Mobile Security console, by following the steps below:
Go to your Mobile Security console.
Go to the Manage section.
In General allow the App Risk Lookup feature.
Access the Apps tile and follow these steps to search for an app risk report:
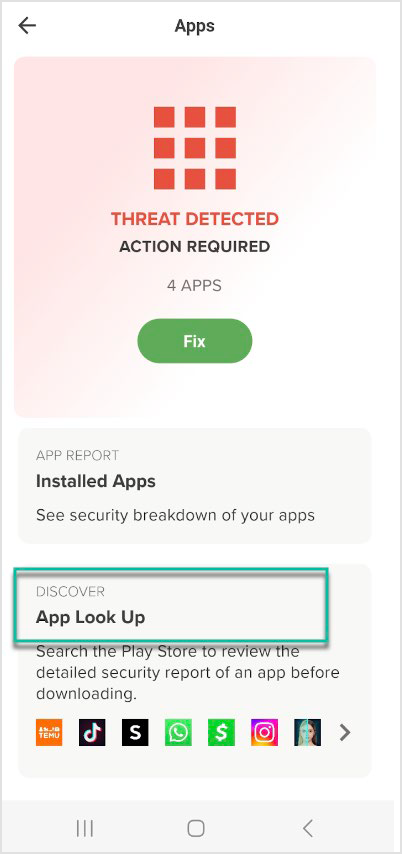
Press App Look Up on the Apps tile.
Search for an app name.
Tap the app name to view the privacy and security risk report for the app.
For your Android device follow these steps to view the app risk report for your installed apps:
Press Installed Apps on the Apps tile.
Search for and select an app.
Tap the app name to view the privacy and security risk report for the app.
Difference for allow-listed apps on the Mobile Security console
Find out how the apps that are allow-listed in Mobile Security console show up in the App Store Search view.
Android
For apps installed on the device, the app is flagged as Trusted App and the message App name has been reviewed by your company and is approved for you to use is displayed.
For apps from Play Store, the GravityZone MTD does not look for apps that are allowed and displays the app risk along with privacy and security risk levels.
iOS
Apps installed on the device cannot be listed/scanned on iOS.
For apps from the App Store, the GravityZone MTD does not look for apps that are allowed and displays the app risk along with privacy and security risk levels.
Network
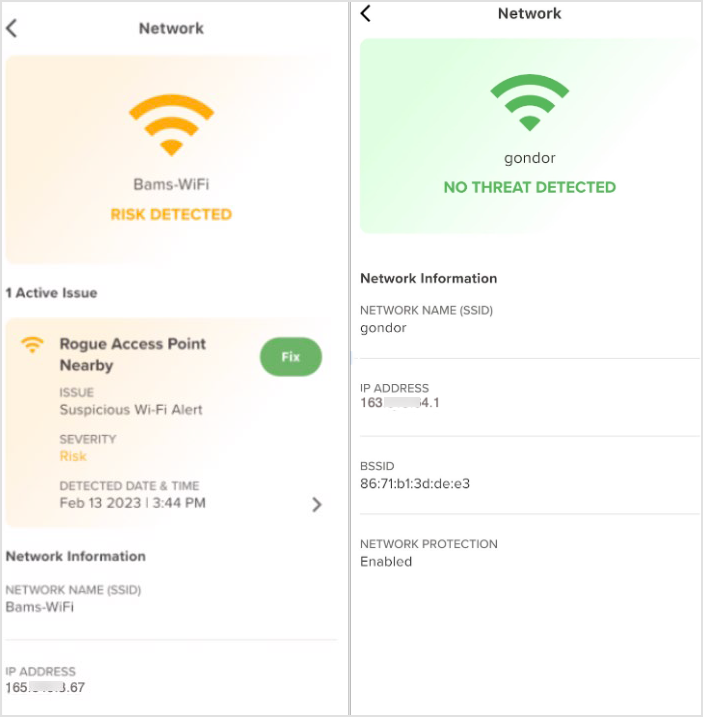
In the dashboard, the Network tile displays the current state of the network or Wi-Fi connection. Examples of threats that show up in this category include:
Compromised Network
Danger Zone Connected
MITM (Man in the Middle)
Rogue Access Point
SSL/TLS Downgrade
The title bar changes color when detecting a threat:
Red = critical threat
Yellow = risk detected
Network Anomaly Behavior
The feature detects unusual network patterns on devices, identifying potential security risks like unauthorized data exfiltration, malware, or app permission misuse. It monitors traffic and location-based behaviors to identify deviations from typical usage. Key functionalities include traffic analysis, which adapts to new applications after learning, and geographic analysis, which tracks anomalies in new countries. Users can mark apps as trusted.
Important
Make sure that the following threats are activated and have the elevated status in the Mobile Security console.
Network Anomaly with a Country Connection-Android
Network Anomaly with a Country Connection IOS
Network Anomaly with a Traffic Peak-Android
Network Anomaly with a Traffic Peak-IOS
Tag tracker
The Android-exclusive functionality provides notification alerts in case of any tracking devices, such as Apple AirTags, are near you. Upon detection of the device, a notification will appear containing the AirTag's identification number, Media Access Control (MAC) address, and initial identification date.
Note
This type of detection requires Bluetooth permission.
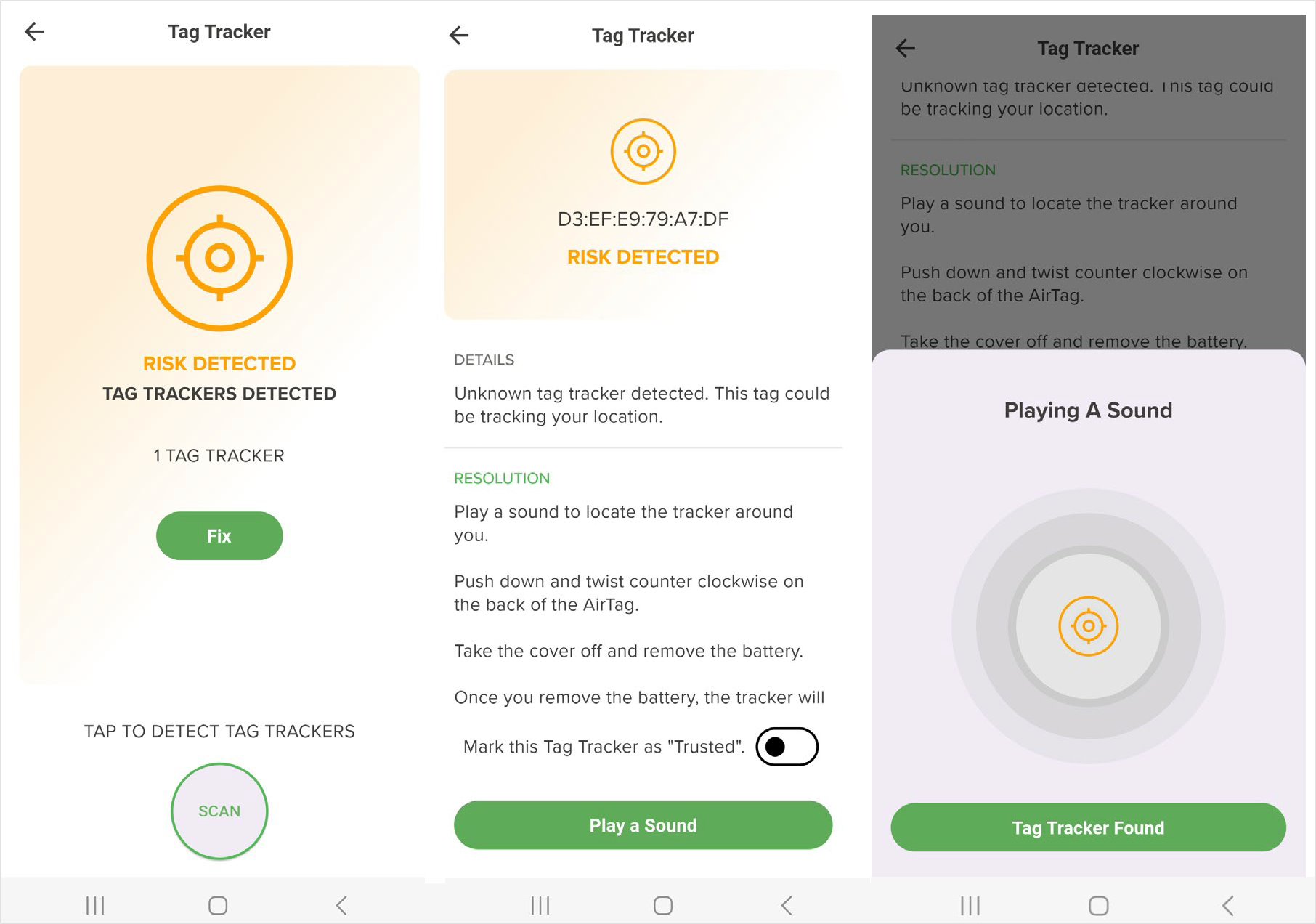
The user has the ability to choose the option of activating an audible alert on the tracker, which can assist in locating it. The AirTag can be designated as "trusted" if it is deemed safe, giving you the option to do so.
Deep Scan Forensic Analysis (iOS only)
With forensic analysis, users can perform a thorough scan on the device. It presents a concise overview of practical outcomes, highlighting the presence of potential risks or threats and offering suggestions to address any concerns. This feature improves on-device detection, enhancing the ability to identify system tampering and rogue access points for better security measures.
Note
This feature requires the user to share iOS log files (system diagnostic logs) with the GravityZone MTD for analysis.
Activating the feature in the Mobile Security console
In the Mobile Security console access the Manage page.
In the General section, under Forensic Analysis select the Enable Forensic Analysis feature.
Save the settings.
Running Forensic Analysis
When you open the GravityZone MTD, the Forensic Analysis tile displays in the dashboard, if enabled (for iOS devices).
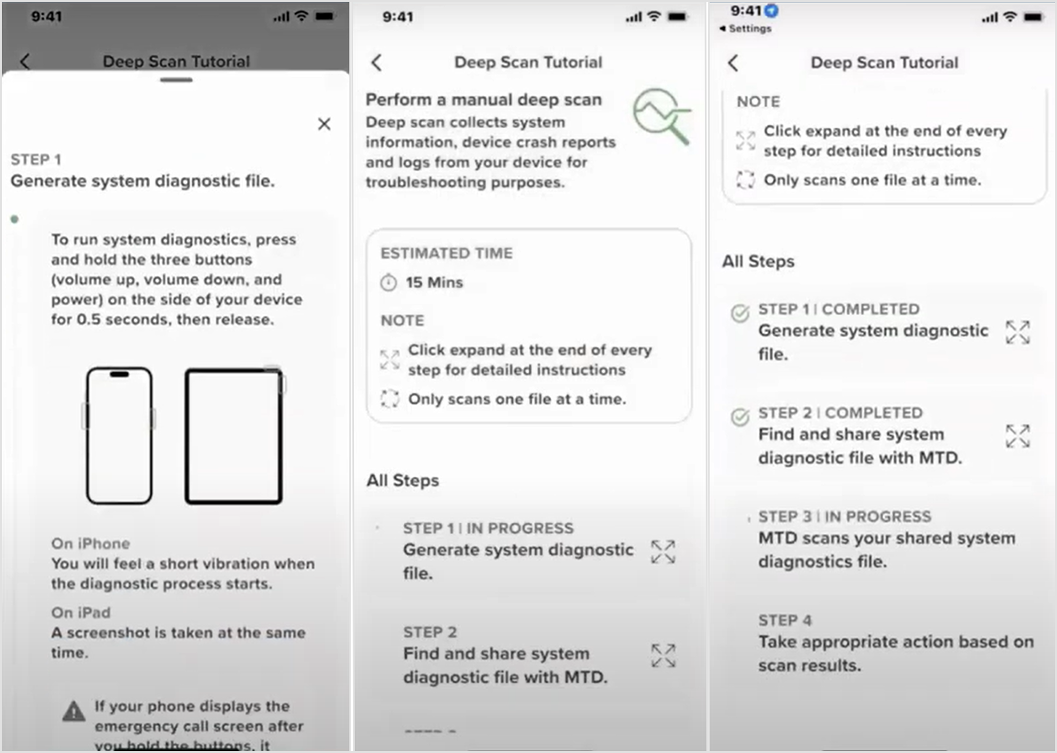
To perform a deep scan tap the Forensic Analysis tile to open the details and tap the Tutorial link. The tutorial displays an arrow to the left of the step that needs to be performed. Once that step is completed, the arrow is replaced by a checkmark and moves to the subsequent step.
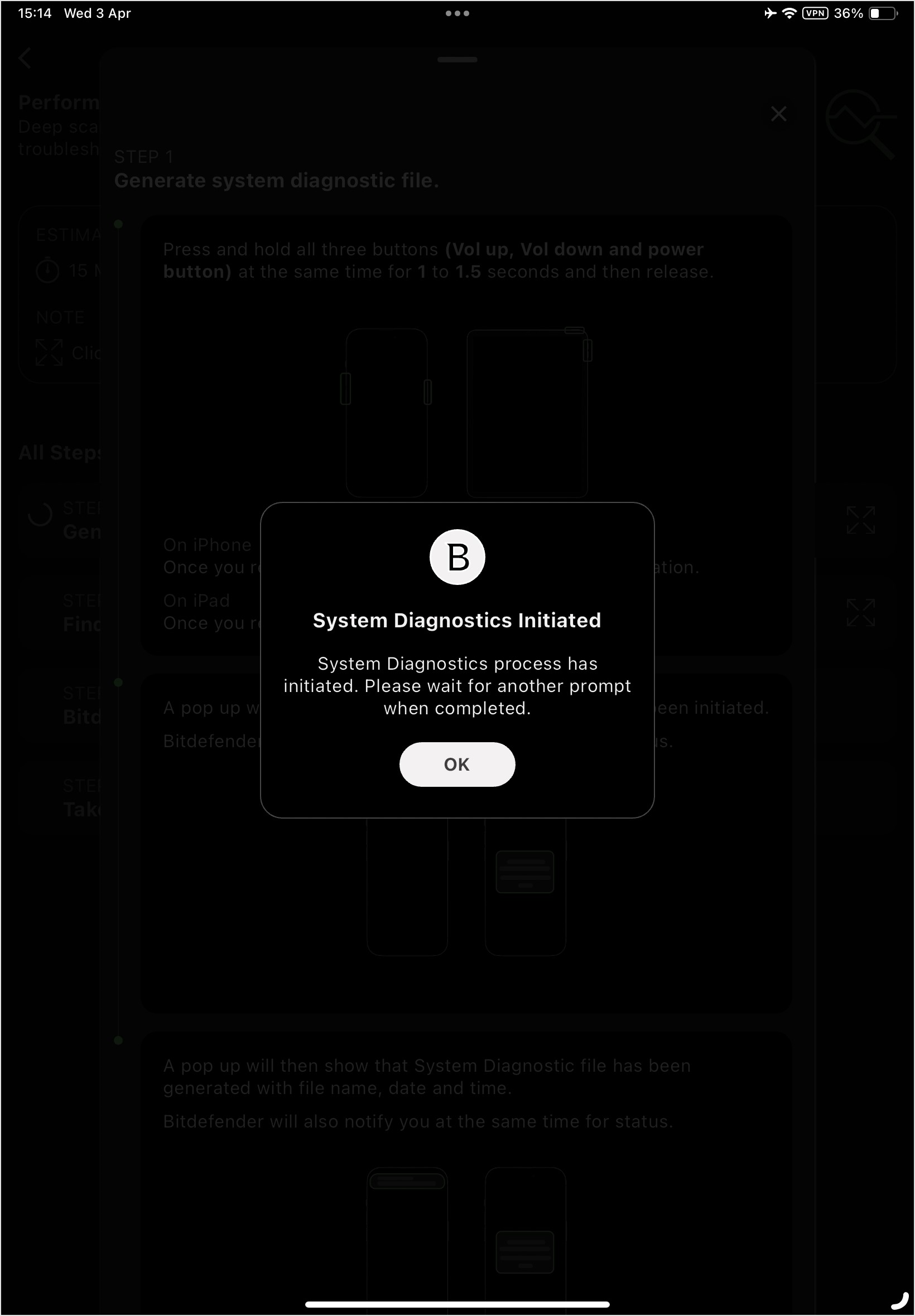
Generate System Diagnostics.
To run system diagnostics, press and hold the three buttons on your device for 1 to 1.5 seconds, then release.
Click OK to close the popup and return to the tutorial screen. Step 1 is now checked and an arrow displays beside step 2.
Find and Share the System Diagnostic File with GravityZone MTD.
Note
This step involves going to iOS security and analytics and sharing the system diagnostic file with GravityZone MTD.
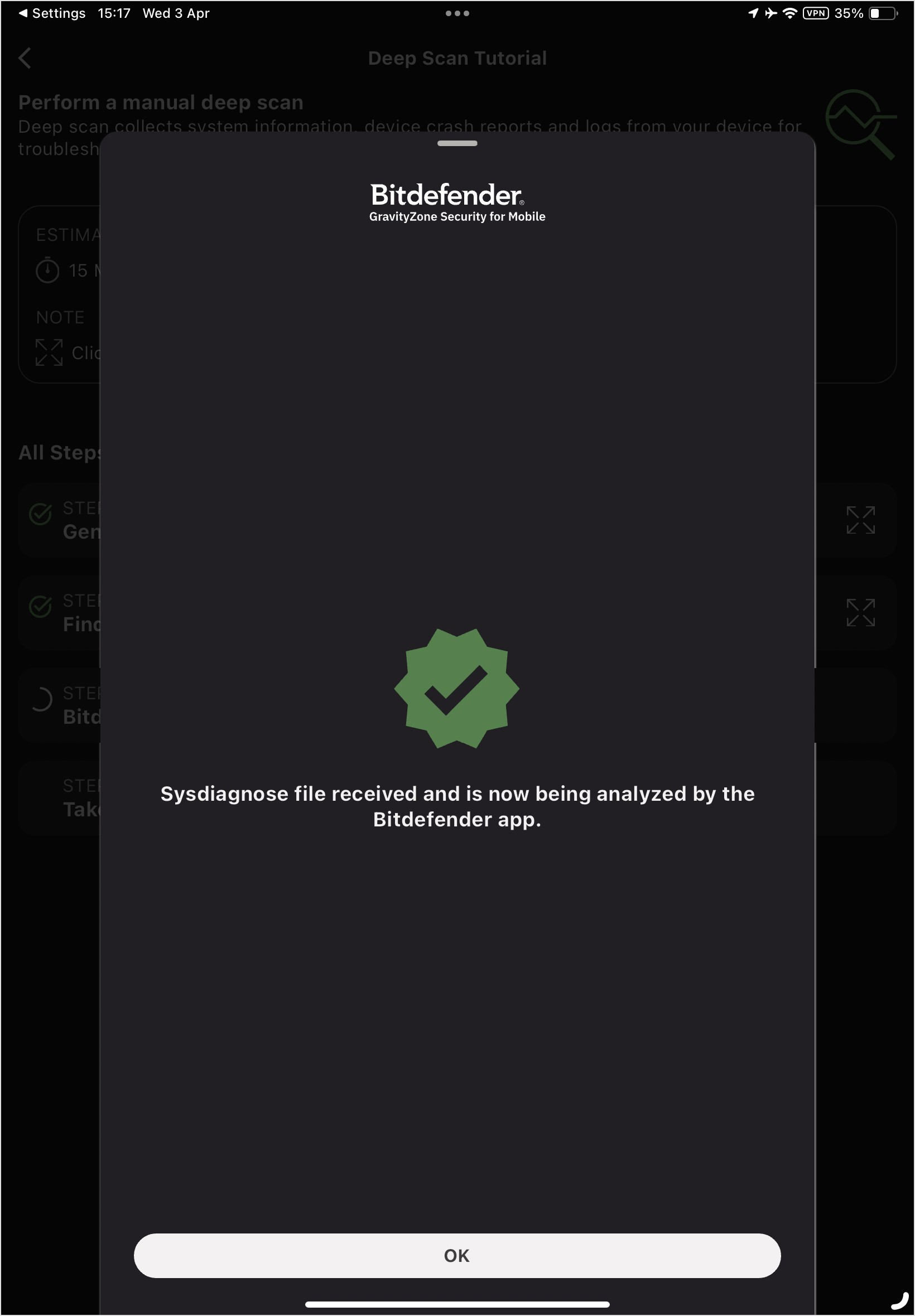
Tap the expand icon in the tutorial to display the instructions for step 2.
Open the Settings screen on your device and select Privacy & Security.
In Privacy & Security, select Analytics & Improvements.
Select Analytics Data.
Search and select or paste the name of the latest sysdiagnose file.
Tap the share icon in the top right and select the GravityZone MTD icon. If there are multiple versions of that file, the most recent one will be furthest down in the list.
If you have selected the correct sysdiagnose file, a popup that confirms the sysdiagnose file was received is displayed.
GravityZone MTD performs the Scan.
Note
GravityZone MTD scans the device and indicates when the data generation process ends and a confirmation popup displays.
View Results on the Device.
With Findings - If issues are found, the Forensic Analysis tile appears yellow on the dashboard. You can tap Fix to display the details about the threat or risk and how to resolve it.
No Findings - If no issues are found, the Forensic Analysis tile and screen show No Threat Detected.
Deep Linking into iOS Settings via Shortcut
Expedites the user experience by simplifying feature configuration and usage by leveraging iOS deep linking to reduce the number of steps for an end user to perform a function in GravityZone MTD.
The implementation of iOS deep linking in the GravityZone MTD has streamlined user interactions, significantly decreasing the number of steps required for various functions.
Deep Scan Analysis: Reduced from 7 steps to 2–3 steps.
Safari Extension Setup: Reduced from 6 steps to 2 steps.
SMS Filtering Setup: Reduced from 5 steps to 3 steps.
To activate the iOS shortcut-related threats feature, follow these steps:you must enable it in the Mobile Security console. Subsequently, end users will receive prompts to install the shortcut,
Enable the feature it in the Mobile Security console.
The users will receive a prompt asking them to install the shortcut.
The user will now have to generate a system diagnostic file.
After the diagnostic file is created, share the file with the GravityZone MTD.
Users can now take the appropriate action based on the result of the scan.
Shortcuts (iOS only)
Executing actions on iOS devices through shortcuts can potentially compromise security and privacy. This feature notifies users when potentially harmful iOS shortcuts are detected on their device, allowing them to easily remove them. Additionally, users will receive alerts if the GravityZone MTD shortcut, necessary for iOS shortcut threat detection, is not found on their device.
To use this feature, the following threats must be enabled by the administrator in the GravityZone MTD Threat policy:
Risky iOS Shortcut Found - a potentially risky iOS shortcut has been found to be installed on your device.
Malicious iOS Shortcut Found - a potentially malicious iOS shortcut has been found to be installed on your device.
iOS Shortcut Detection Disabled - the device is not configured to detect risky or malicious iOS shortcuts.
Installing the GravityZone MTD Shortcut
In order to detect malicious shortcuts, the GravityZone MTD shortcut must be installed on the device. If this shortcut is not installed, GravityZone MTD identifies it as a risk and the Shortcuts tile appears yellow.
To install the GravityZone MTD shortcut and resolve the issue:
Tap the Shortcuts tile on the dashboard to display this screen.
Press Install GravityZone MTD Shortcut.
Press Add Shortcut. This opens the Shortcuts app on your device, with the GravityZone MTD Shortcut tile displayed.
Tap the GravityZone MTD Shortcut tile to install it and choose Always Allow to provide consent. The tile displays a checkmark once the shortcut is installed.
When you return to the dashboard, the Install GravityZone MTD Shortcut issue is now added.
If the GravityZone MTD detects a risky or malicious shortcut, the Shortcuts tile displays in yellow or red, respectively and you can tap the tile for details about the issue and how to resolve it.
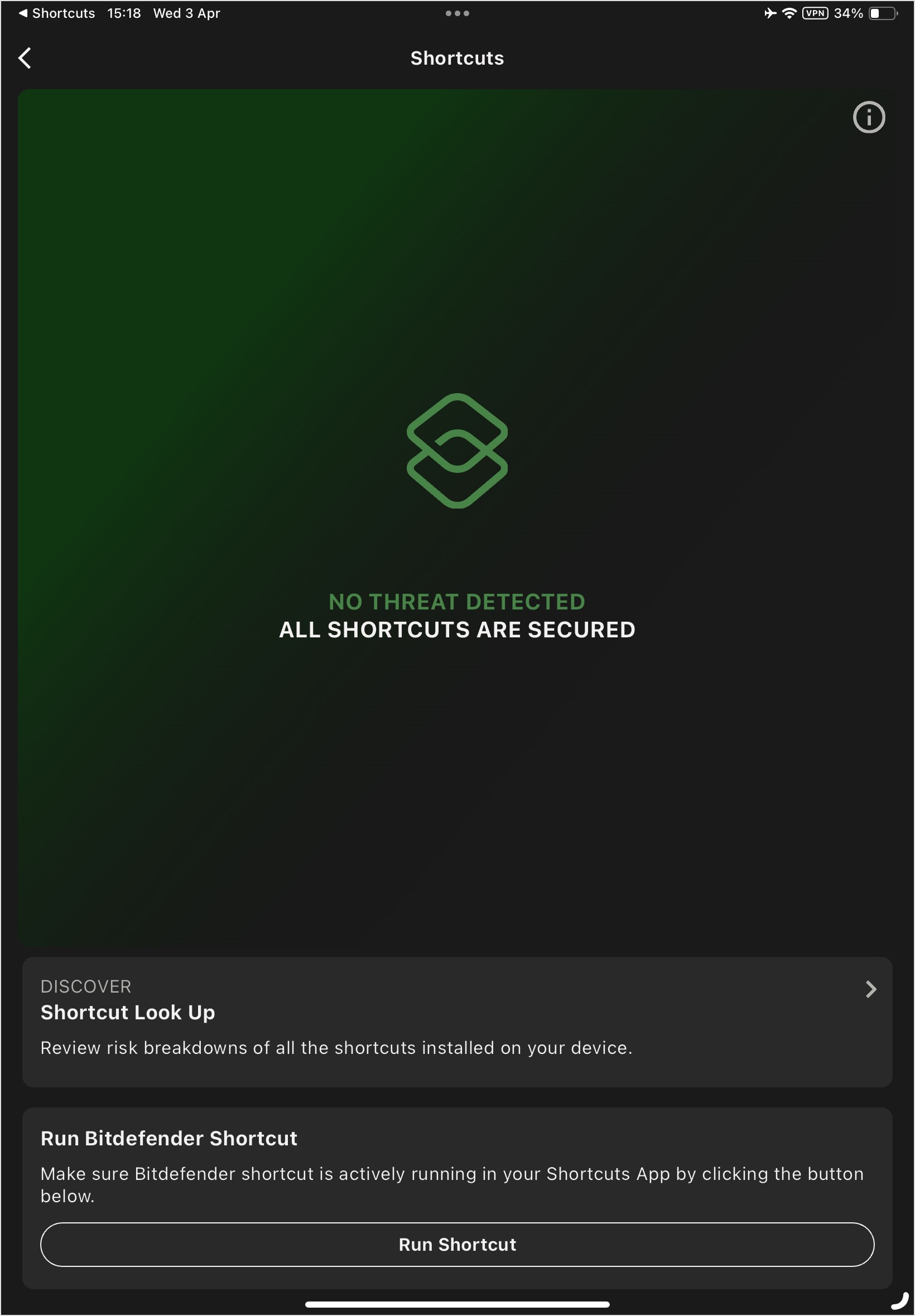
Running the GravityZone MTD Shortcut to Detect Threats
Unless automation is set up, you need to tap Run Shortcut in the Shortcuts detail screen each time you install a new shortcut to find out if it is risky.
To continue running the shortcut even when the device is locked follow these steps:
Tap the ellipsis button on the GravityZone MTD Shortcut icon in the iOS Shortcuts app.
Tap the “i” icon at the bottom of the screen.
Toggle on Allow Running When Locked to ensure the shortcut continues to run.
Setting Up GravityZone MTD Shortcut Automation
You can set up automation for the GravityZone MTD shortcut to check for issues when a new shortcut is added, and to ensure the iOS shortcut list in MTD is up-to-date after adding or removing shortcuts on your device.
Note
Keep in mind that the shortcut will run at the time interval you specify when setting up automation, so it may not be immediate.
Tap GravityZone MTD Shortcut Automation from the Shortcut Look Up screen or the Tutorials tile in the GravityZone MTD dashboard.
From the tutorial, you can open the Shortcuts app on your iOS device and follow the steps provided to set up automation.
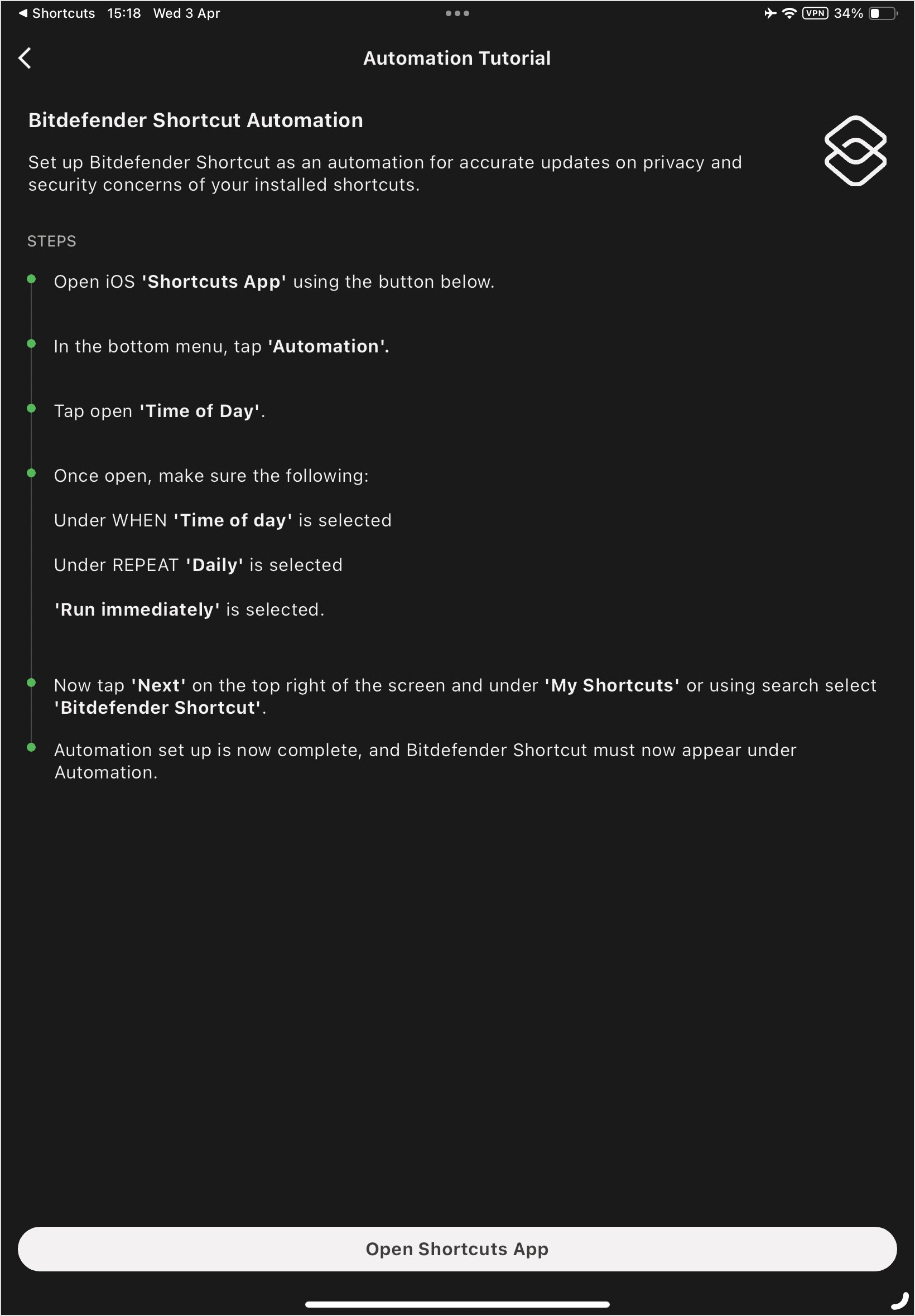
Once automation is set up, this screen displays.
Shortcut Look Up
The Shortcut Look Up screen allows you to view a breakdown of the shortcuts that are installed on the device.
Each shortcut that is found is color-coded to indicate the risk level:
Risk detected
Threat detected
No threat detected
To access this screen, tap the Shortcut Look Up link in the screen that displays after tapping the Shortcuts tile. You can tap on a specific shortcut to view details.
Tip
If the shortcut was last updated a while ago (as shown in the Last Updated field at the top of the Shortcut Look Up screen), you may want to run the GravityZone MTD shortcut to verify there are no issues.
PDF Scanning (Android only)
PDF documents contain URLs and scripts that can be exploited for malicious activities. This feature enables GravityZone MTD to detect PDFs stored in the Downloads folder on your device, effectively addressing new phishing methods that bypass conventional email security measures. While the scan is in progress, you have the ability to monitor its status. After the scan finishes, it will alert you about any problems discovered so that you can take care of them promptly.
To activate this feature, the following threats must be enabled in the GravityZone MTD Console Threat policy:
PDF - Unscanned Files - MTD will pause the scan when it determines that the number of files may affect performance or battery consumption during installation. Unscanned PDFs pose potential risks. Immediate resume scan is advised.
PDF - Malicious Document - There is harmful code or behavior within the PDF file, indicating a potential threat has been detected.
PDF - Phishing Document - The document exhibits a suspicious structure that could potentially be a phishing attempt.
Detection Process and Results
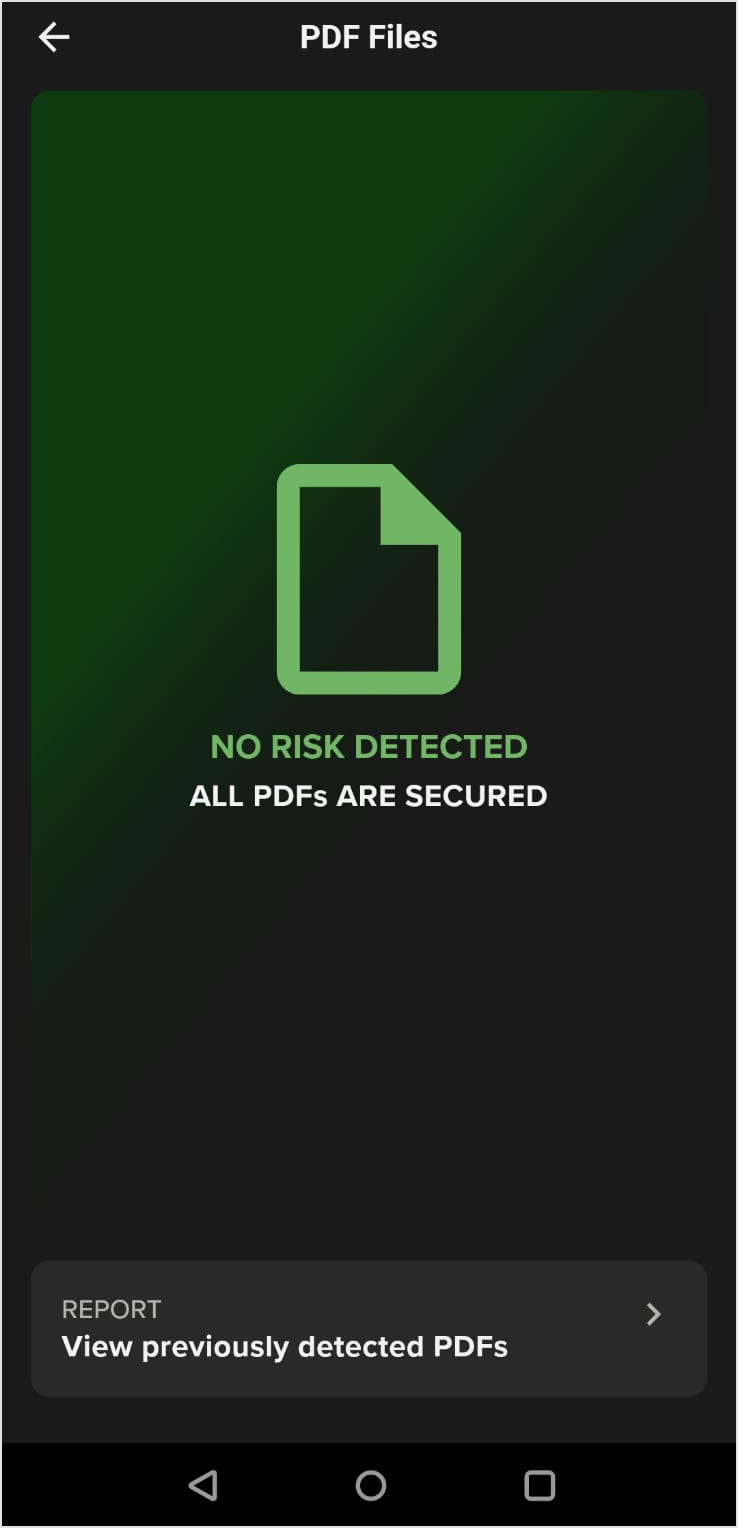
This section explains what happens for different detection scenarios.
No Issues Detected - The PDF Files tile appears green on the dashboard when no issues are detected. If you tap this tile, it shows the screen below along with a link to a report where you can view previously detected PDFs.
Malicious or Phishing PDF Detected - If a malicious PDF or phishing PDF is detected, the PDF Files tile will appear yellow. An example is shown here, and in this case a malicious PDF was found.
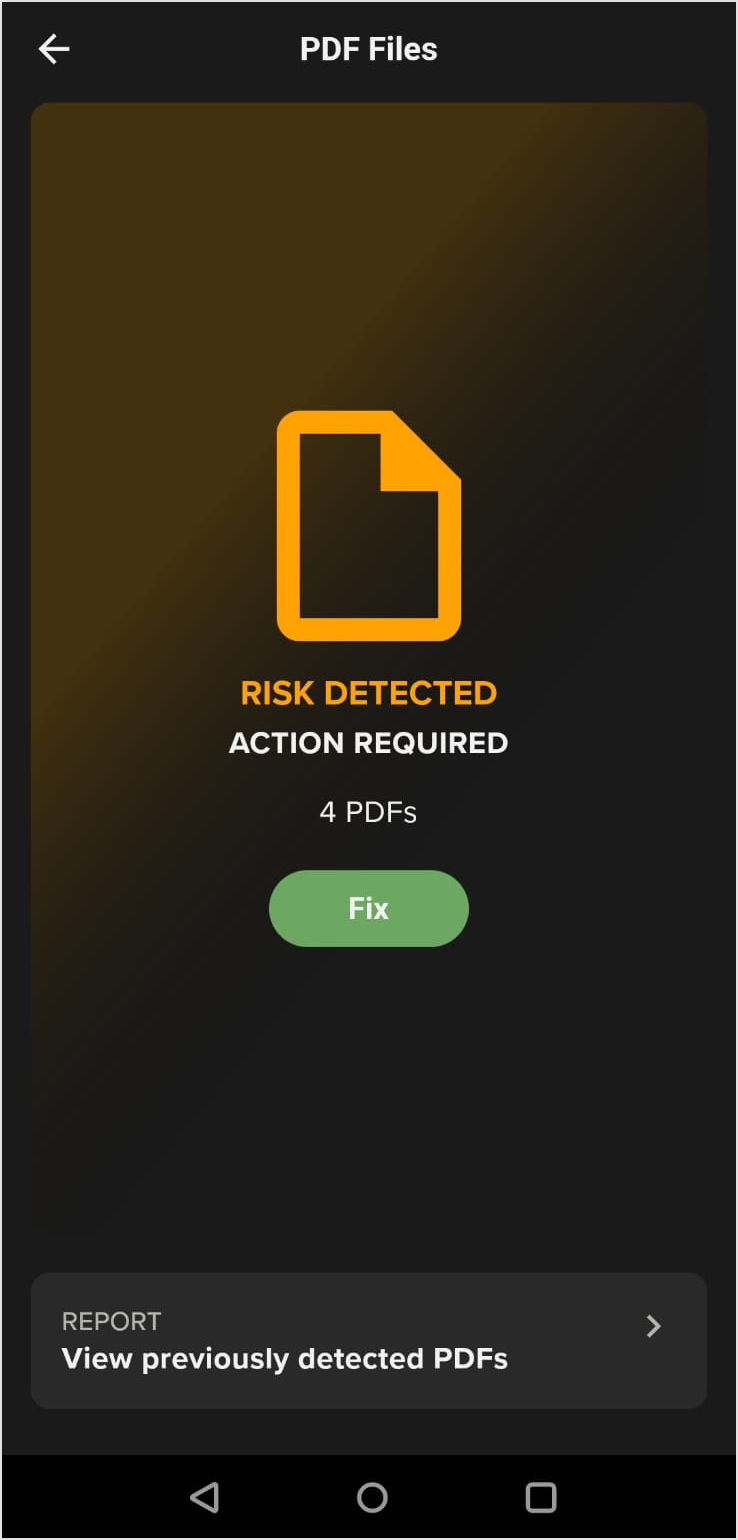
To resolve this issue:
Tap Fix to display the details screen shown next.
Click Delete PDF to remove the malicious PDF from the device. The threat is then resolved.
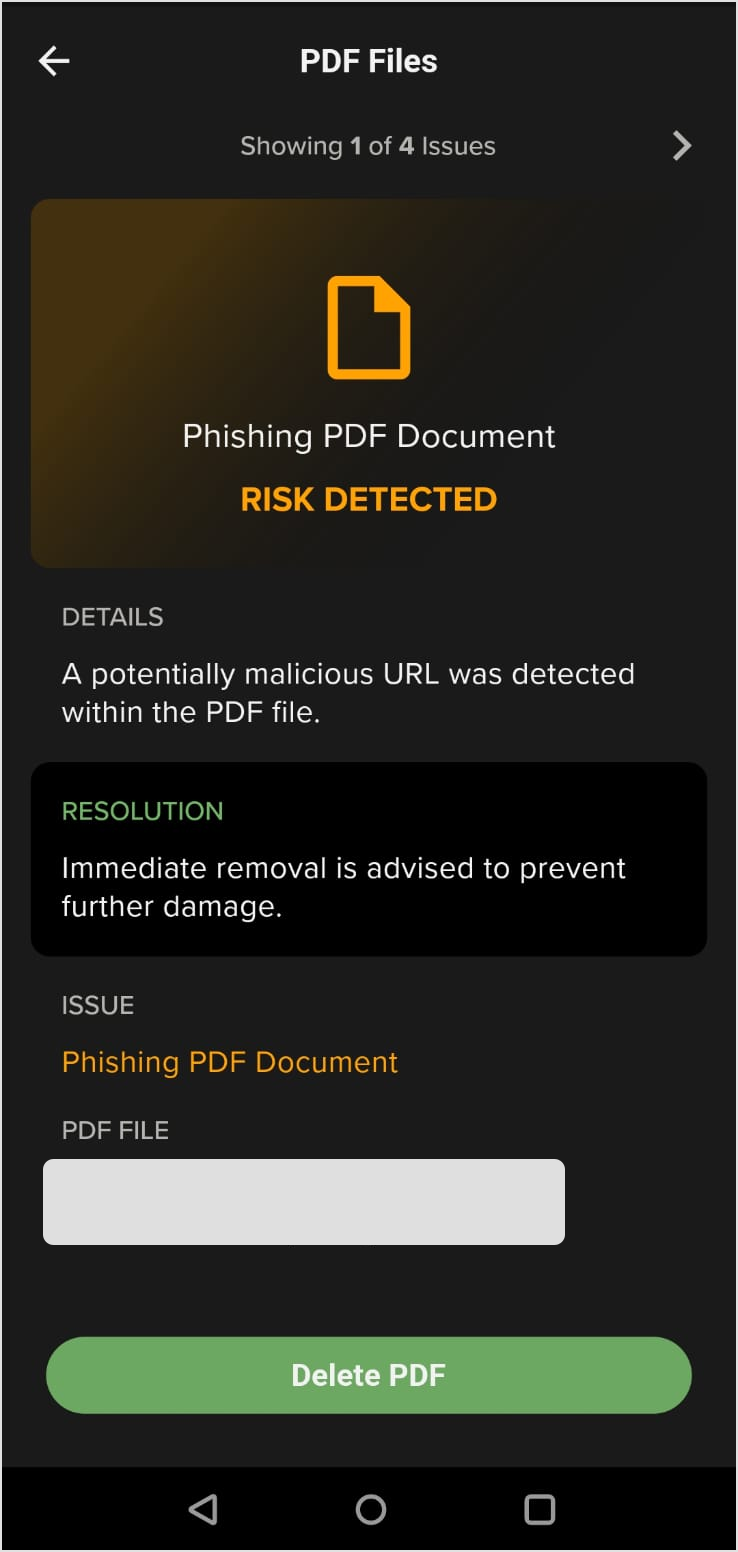
After you delete the PDF, you can view the Full Event Log to see that the threat has been mitigated.
Scanning Status and Threshold
During the scan, a progress bar will show the number of files scanned and notify you when the scan finishes. MTD will temporarily halt the scan if it detects that the volume of files could potentially impact the system's performance or drain the battery during the installation process. In this scenario, a button labeled Resume Scan is displayed.
To resume scanning:
Press Resume Scan to continue scanning whenever you choose. It is recommended that you plug in your device while doing this.
If you return to the dashboard and tap the PDF Files tile, it shows that the scan is complete.
If a risk is detected during the scan, you can tap the Fix button to find out how to resolve the issue.
Viewing the PDF Scan Report
In the PDF Files detail screen, tap View Previously Detected PDFs to display the PDF Scan Report.
There are two possible scenarios for the scan report results:
No malicious PDFs are detected.
Potentially malicious PDFs detected.
Additional Device Data from Google Logs (Android only)
The GravityZone MTD can read additional information from the device, given specific EMM/MDM permissions and the data in the Google logs. This feature provides:
Enhancements in our on-device detection capabilities for new detections and additional forensics for existing threats.
Enhancements in our forensics events generated for analysis.
Detections are improved for these existing threats:
System Tampering
Site Blocked
Risky Site - Link Tapped
Risky Site - Link Visited Risky Site Blocked
Important
For this feature to work properly, the device must be in device owner mode
Local Proxy for Web Content Filtering
The local proxy feature in the GravityZone MTD enhances anti-phishing protection on Android devices with corporate VPNs by using the Bitdefender proxy engine. This upgrade improves monitoring of HTTP/HTTPS traffic, assesses link risks, and reports security issues.
This feature offers:
Offers web content filtering, including anti-phishing.
Supports zero-touch activation for managed Android devices using an existing corporate VPN.
The system features zero-touch activation for Mobile Device Management (MDM), which sets up a local proxy on the Chrome browser and activates the GravityZone MTD without interfering with existing corporate VPNs. It provides comprehensive threat detection across devices, networks
Activation is performed by the administrator via Mobile Device Management (MDM) solutions, requiring no action from end users.
Auto-reconnect for on-device VPN
This feature provides ongoing protection against risky web links by enabling users or administrators to establish intervals for VPN reconnection, accommodating both managed and unmanaged devices.
The feature allows customers and end users to set a specific interval for automatically when reconnecting a disconnected on-device VPN, which is utilized for web content filtering and anti-phishing. This functionality enhances security by maximizing protection against risky links.
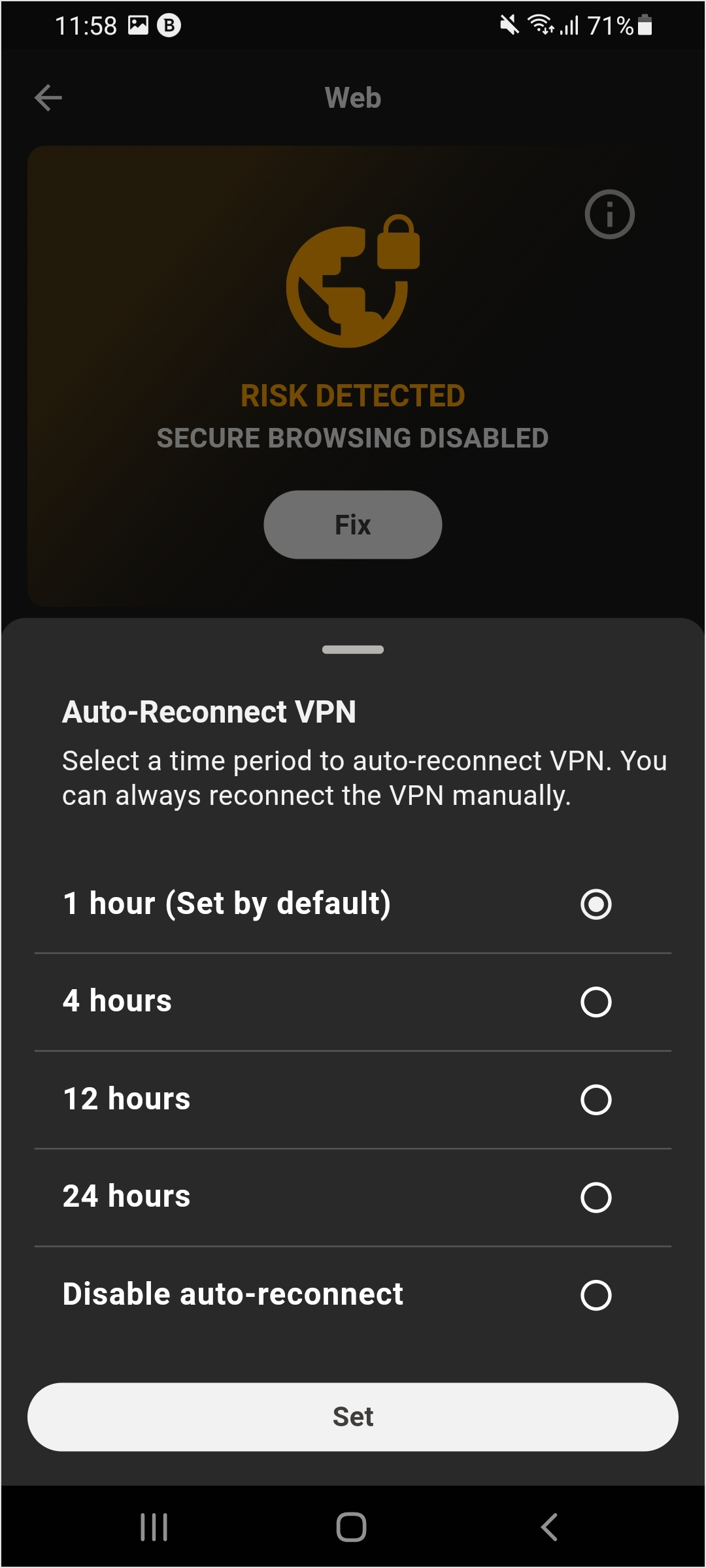
For devices managed by MDM, the administrator can deploy the auto-reconnect setting through the MDM system.
For non-managed devices, the end user has the option to select their preferred auto-reconnect interval.
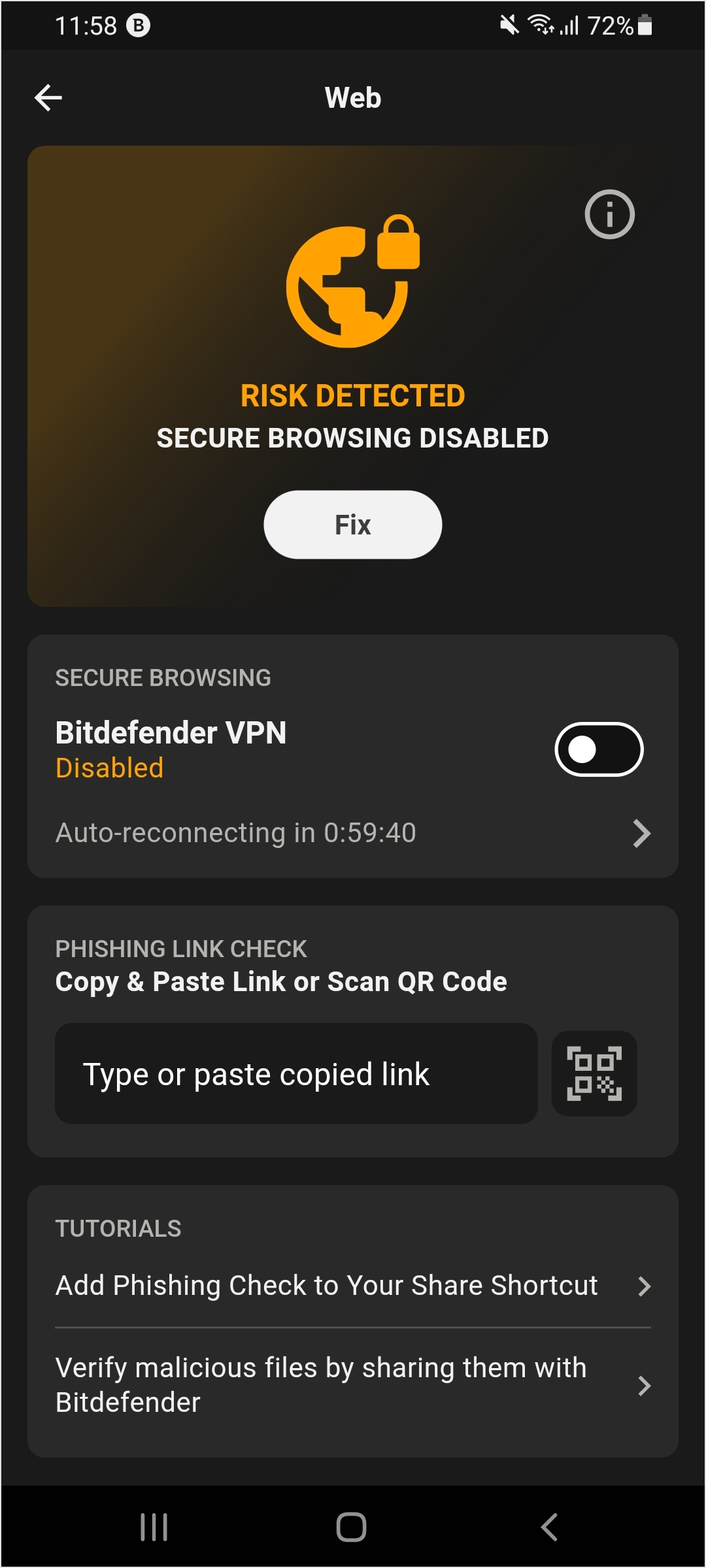
The on-device VPN can be deployed via an MDM solution to the user and within the GravityZone MTD. Additionally, administrators can determine whether to allow end users the option to temporarily disconnect the VPN, as this may be necessary for other activities on the device.
Note
Implement a mechanism for the automatic reconnection of the VPN to maintain active content filtering protection on the device.