Advanced Anti-Exploit
Advanced Anti-Exploit is a proactive technology that detects exploits in real-time. Based on machine learning, it protects against a series of known and unknown exploits, including memory file-less attacks.
The settings are available in the Antimalware > Advanced Anti-Exploit section of the policy.
Note
This module is available for:
Windows for workstations
Windows for servers
Linux
To check the compatible operating systems, refer to Endpoint Protection.
For Linux systems, Advanced Anti-Exploit is a preventative security control intended to identify and block Zero-Day and Advanced Persistent Threat activities and related processes in real-time (On-Execution). The module is capable to perform Kernel Integrity checks as well as monitor user-space implementation relying on eBPF and KProbes.
Note
Availability and functioning of this feature may differ depending on the license included in your current plan.
Click the toggle to enable Advanced Anti-Exploit.
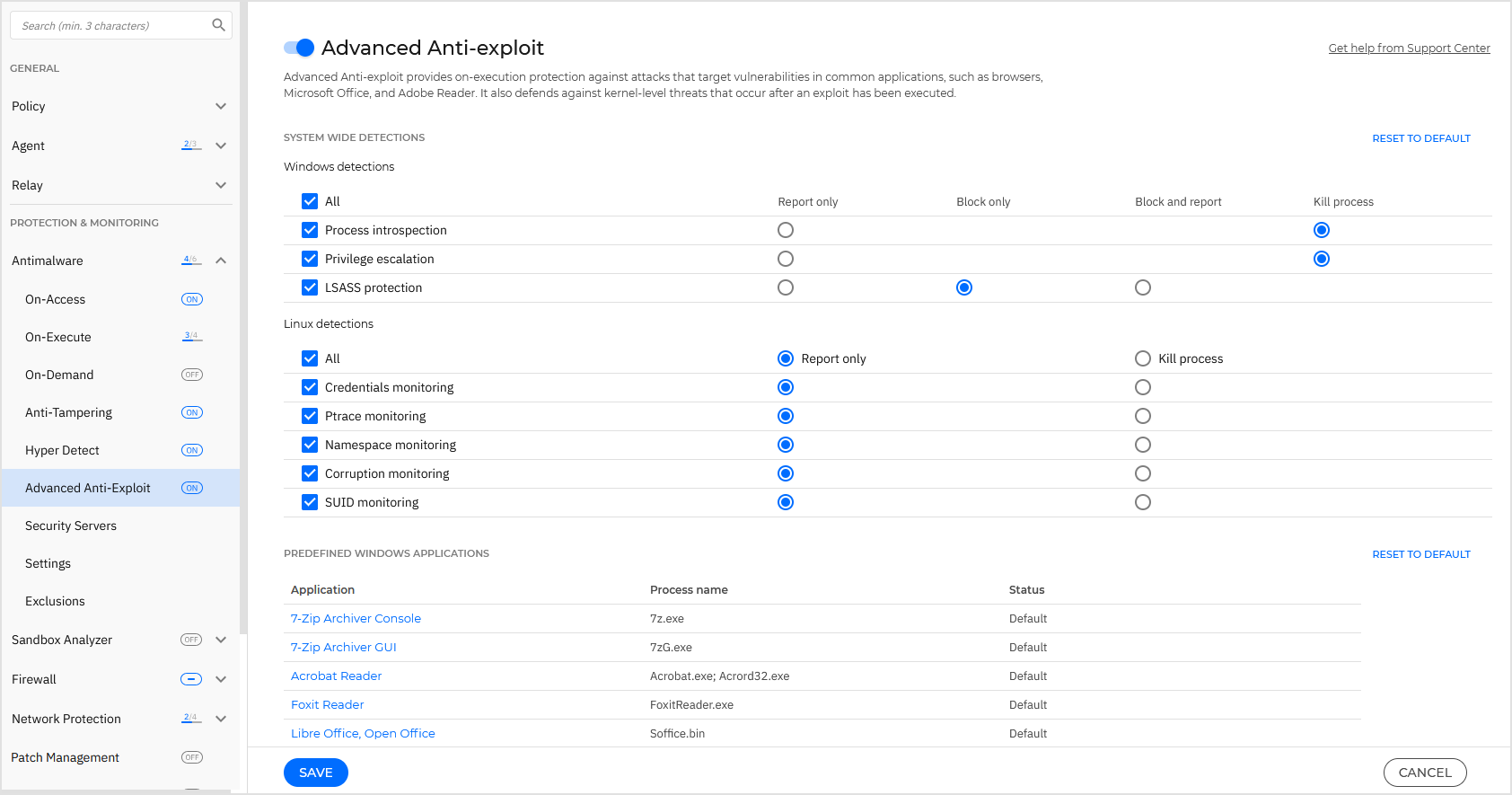
Advanced Anti-Exploit is set to run with the recommended settings. You can adjust protection differently if needed.
To restore the initial settings, click the Reset to default option in the upper-right corner of the page.
GravityZone has the anti-exploit settings organized in three sections:
System-wide detections
The anti-exploit techniques in this section monitor the system processes that are targets of exploits.
For more information about the available techniques and how to configure their settings, refer to Configure System-Wide Mitigation.
Predefined applications
The Advanced Anti-Exploit module is preconfigured with a list of the common applications such as Microsoft Office, Adobe Reader, or Flash Player, which are the most exposed to exploitations.
For more information about the available techniques and how to configure their settings, refer to Configure Application-Specific Techniques.
Additional applications
In this section, you can add and configure protection for as many other applications as you want.
For more information about the available techniques and how to configure their settings, refer to Configure Application-Specific Techniques.
You can expand or collapse each section by clicking its heading. This way, you will quickly reach the settings you want to configure.
Configure system-wide mitigation
Under the System-wide detections section, you have the following options:
Technique | Description | Operating system |
|---|---|---|
Privilege escalation | Prevents processes from gaining unauthorized privileges and access to resources. Default action: Kill process | Windows |
Process introspection | Performs an in-depth analysis of the process state when a child process is created, examining potential indicators of compromise. The analysis offers an overview of detected parent processes and the child processes they have spawned. Default action: Kill process | Windows |
LSASS process protection | Protects the LSASS process from leaking secrets such as password hashes and security settings. The feature monitors when system applications require read access to the memory of the LSASS process and takes action if configured accordingly. Default action: Block only The recommended action is Block only. This action blocks an application's capability to access LSASS memory, and not the application itself like in a classic scenario. Specifically, Advanced Anti-Exploit denies the application access request to read from LSASS memory. Application incompatibilities are uncommon. Using the Block and report action enables you to deny applications access to LSASS memory and to be notified about these attempts. This configuration is useful if you want to view and further analyze the detection events, but it may generate a high volume of notifications. The Report only action notifies you about applications' attempts to access the LSASS memory. This configuration may generate a high volume of notifications, including for any process asking for more permissions than needed, and should be used with caution, as the LSASS memory is not actively protected. You can view the blocked events in the security agent local console under the Antiexploit category. You can add LSASS-related exclusions in the Configuration Profiles section of Control Center. The excluded processes will not be able to access LSASS but will no longer trigger detections. | Windows |
Credentials monitoring | Inspects process behavior to detect unexpected credential changes for a thread. Default action: Report only | Linux |
Ptrace monitoring | Monitors the use of debugging mechanisms to detect attempts of using Default action: Report only | Linux |
Namespace monitoring | Inspects process behavior to detect unexpected changes in the namespace of a thread. Default action: Report only | Linux |
Corruption monitoring | Monitors syscall activity to detect memory corruption attempts via crafted syscalls. Default action: Report only | Linux |
SUID monitoring | Reports all attempts to set a SUID flag to a file. Default action: Report only | Linux |
These anti-exploit techniques are enabled by default. To disable any of them, clear their check box.
Optionally, you can change the action taken automatically upon detection. Choose an action available in the associated menu:
Report only: GravityZone reports the event without taking any mitigation action. You can view the event details in the Advanced Anti-Exploit notification, and in Blocked Applications and Security Audit reports.
Block only: prevents the malicious process from accessing unauthorized resources without GravityZone reporting the event.
Block and report: prevents the malicious process from accessing unauthorized resources and GravityZone reports the event. You can view the event details in the Advanced Anti-Exploit notification, and in Blocked Applications and Security Audit reports.
Kill process: ends immediately the exploited process.
Configure application-specific techniques
Whether predefined or additional applications, they all share the same set of anti-exploit techniques. You can find them described herein:
Technique | Description |
|---|---|
ROP Emulation | Detects attempts to make executable the memory pages for data, using the Return-Oriented Programming (ROP) technique. Default action: Kill process |
ROP Stack Pivot | Detects attempts to hijack the code flow using the ROP technique, by validating stack location. Default action: Kill process |
ROP Illegal Call | Detects attempts to hijack the code flow using the RO Ptechnique, by validating callers of sensitive system functions. Default action: Kill process |
ROP Stack Misaligned | Detects attempts to corrupt the stack using the ROP technique, by validating the stack address alignment. Default action: Kill process |
ROP Return to Stack | Detects attempts to execute code directly on stack using the ROP technique, by validating return address range. Default action: Kill process |
ROP Make Stack Executable | Detects attempts to corrupt the stack using the ROP technique, by validating the stack page protection. Default action: Kill process |
Flash Generic | Detects Flash Player exploitation attempts. Default action: Kill process |
Flash Payload | Detects attempts to execute malicious code into Flash Player, by scanning Flash objects in memory. Default action: Kill process |
VBScript Generic | Detects VBScript exploitation attempts. Default action: Kill process |
Shellcode Execution | Detects attempts to create new processes or download files, using shellcode. Default action: Kill process |
Shellcode LoadLibrary | Detects attempts to execute code via network paths, using shellcode. Default action: Kill process |
Anti-Detour | Detects attempts to bypass security checks for creating new processes. Default action: Kill process |
Shellcode EAF (ExportAddress Filtering) | Detects attempts of malicious code to access sensitive system functions from DLL exports. Default action: Kill process |
Shellcode Thread | Detects attempts to inject malicious code, by validating newly-created threads. Default action: Kill process |
Anti-Meterpreter | Detects attempts to create a reverse shell, by scanning executable memory pages. Default action: Kill process |
Obsolete Process Creation | Detects attempts to create new processes using obsolete techniques. Default action: Kill process |
Child Process Creation | Blocks creation of any child process. Default action: Kill process |
Enforce Windows DEP | Enforces Data Execution Prevention (DEP) to block code execution from data pages. Default: Disabled |
Enforce Module Relocation (ASLR) | Prevents code from being loaded in predictable locations, by relocating memory modules. Default: Enabled |
Emerging Exploits | Protects against any new emerging threats or exploits. Rapid updates are used for this category before more comprehensive changes can be made. Default: Enabled |
To monitor other applications except for the predefined ones, click the Add a Windows application button under Custom Windows applications.
To configure the anti-exploit settings for an application:
For existing applications, click the application name. For new applications, click the Add Windows application button.
A new page displays all techniques and their settings for the selected application.
Important
Use caution when adding new applications to be monitored. Bitdefender cannot guarantee compatibility with any application. Thus, it is recommended to test the feature first on a few non-critical endpoints, and then deploy it in the network.
If adding a new application, enter its name and its processes names in the dedicated fields. Use the semicolon (;) to separate process names.
If you need to quickly check the description of a technique, click the arrow next to its name.
Select or clear the checkboxes of the exploitation techniques, as needed.
Use the All option if you want to mark all techniques at once.
If needed, change the automatic action upon detection. Choose an action available in the associated menu:
Kill process: ends immediately the exploited process.
Report only: GravityZone reports the event without taking any mitigation action. You can view the event details in the Advanced Anti-Exploit notification and in reports.
By default, all techniques for predefined applications are set to mitigate the issue, while additional applications are set to just report the event.
To quickly change the action taken for all techniques at once, select the action from the menu associated with All option.
Click Save to confirm the settings for an existing application.
Click Add to confirm the settings for a new application.