Adding process exclusions for Mac in GravityZone
As a GravityZone administrator, you can configure process exclusions for Mac computers in the Policies > Configuration Profiles page and in the policy settings, under Antimalware and Network Protection.
Overview
In macOS, the entities listed in the Applications folder are in fact containers that include all binary files, libraries, and dependencies for those apps.
Therefore, when configuring profiles or adding antimalware exclusions, you must enter the entire path to the executable file from the application’s container. When adding exclusions in Network Protection, you only need to enter the name of the executable file.
To browse one container and obtain the name of the executable file, right-click that container and select Show Package Contents.
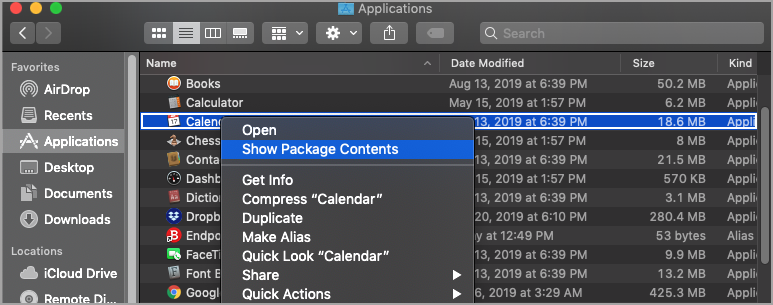
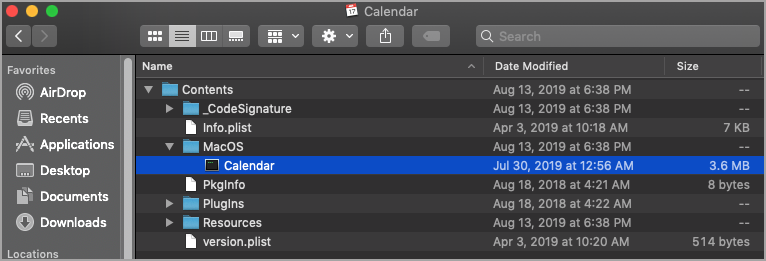
Usually, the path to the executable file is /Application.app/Contents/MacOS/binary, where Application.app is the name of the container and binary is the name of the executable file.
For example, the complete path for the Calendar application in macOS is /Applications/Calendar.app/Contents/MacOS/Calendar
Note
Some applications have different names for the executable files. For example, Visual Studio Code has the executable file with the name Electron. Therefore, the complete path is /Applications/Visual Studio Code.app/Contents/MacOS/Electron.
Adding process exclusions in Configuration Profiles
To create a process exclusion in the Configuration Profiles page, follow these steps:
Log in to GravityZone Control Center.
Go to the Policies > Configuration profiles page from the left side menu.
On the Exclusions page, click Add Exclusions.
In the configuration page, select Process as object type.
In the Excluded item field, enter the complete path to the executable file of the application. For example:
/Applications/Visual Studio Code.app/Contents/MacOS/Electron.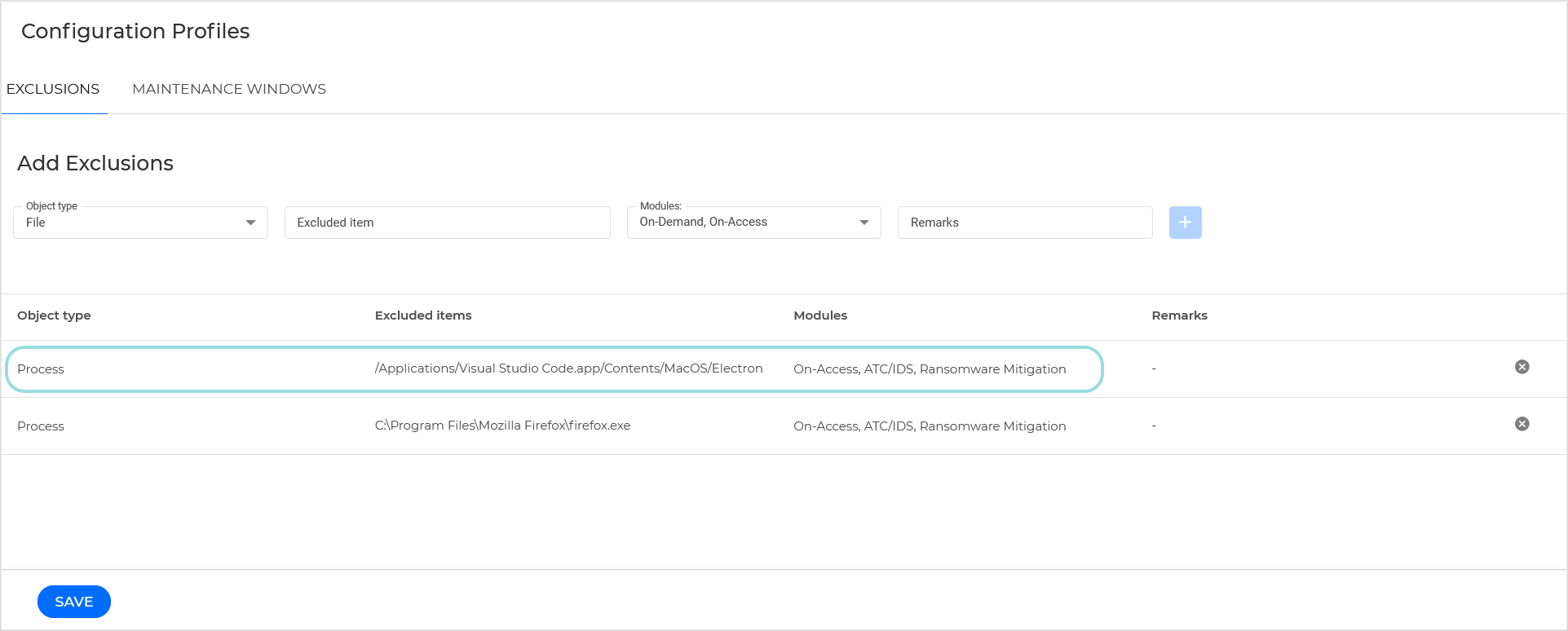
Select the scanning modules to which the exclusion applies:
On-Access
ATC/IDS
Ransomware Mitigation
LSASS Protection
All the above modules
Optionally, enter a note about the exclusion in the Remarks field.
Click the
 icon to add the exclusion in the list.
icon to add the exclusion in the list.Click the Save button.
Next, you have to assign the exclusion to a list. That list will be used with a policy. To assign the exclusion to a list, follow these steps:
On the Configuration profiles > Exclusions page in the GravityZone main menu, select the process exclusion that you created.
Click the Assign to lists button to add the exclusion to an existing list.
Note
If you want to use the exclusion with a new list, click the New list option in the left panel to first create the list.
In the configuration window, select the list you want to include the exclusion.
Click the Save button.
Next, you have to add the list to the policy that is active on the Mac endpoints. Follow these steps:
Go to the Policies page from the left side menu.
Click the policy name to open it.
Go to the Antimalware > Exclusions page.
Enable the Exclusions from configuration profiles option.
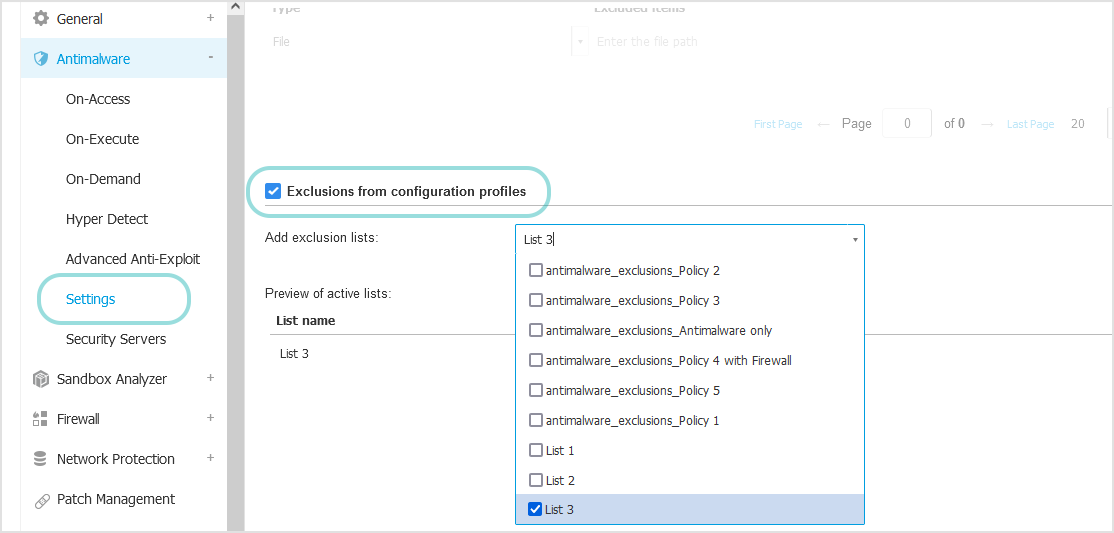
Select the list that includes the exclusion and click Apply.
Click Save.
On the Configuration profiles page, you can take actions on exclusions, such as edit, delete, or change the list assignment.
Adding process exclusions in the Antimalware section of the policy
To exclude a process from scanning for malware in the Antimalware section of the policy settings, follow these steps:
Log in to GravityZone Control Center.
Go to the Policies page from the left side menu.
Create or edit a custom policy.
Go to Antimalware and click Exclusions.
Enable the In-policy exclusions option.
From the menu, select Process as exclusion type.
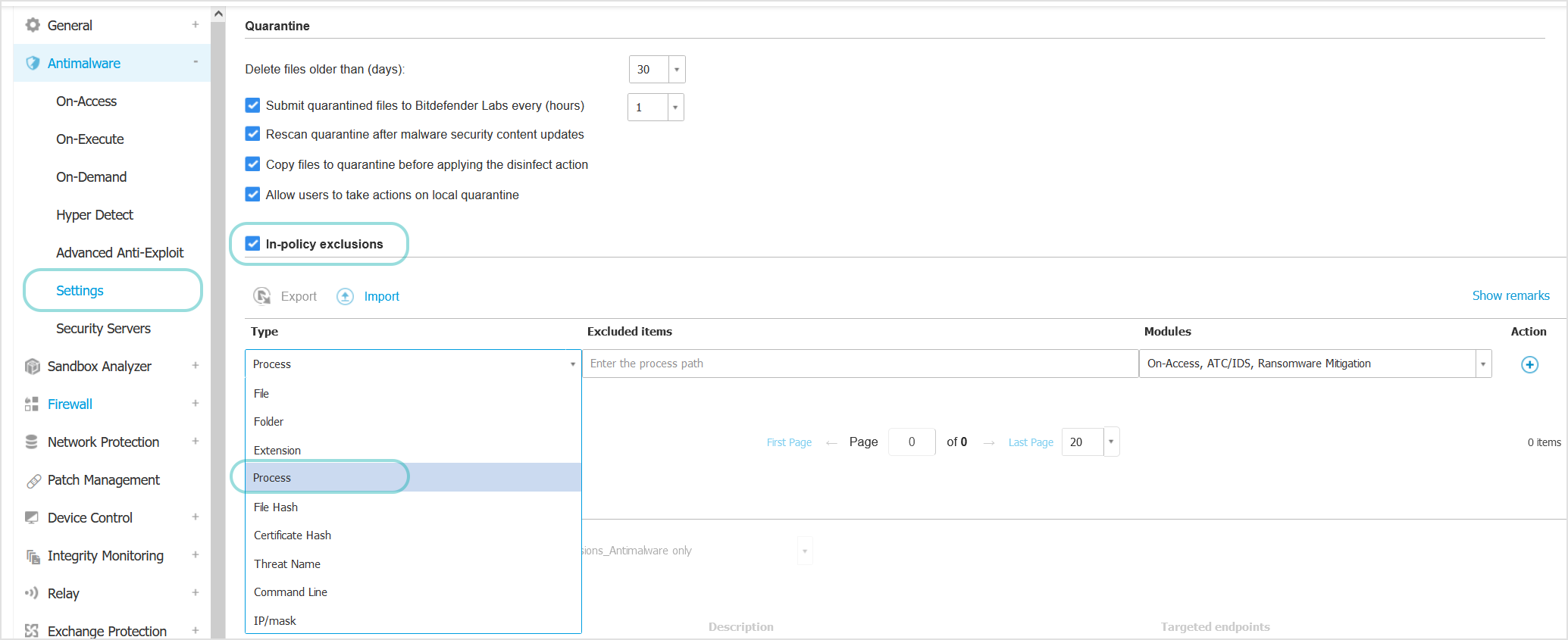
Enter the complete path to the executable file of the application. For example, the complete path for the Time Machine application is
/Applications/Time Machine.app/Contents/MacOS/Time Machine.Select the scanning modules to which the exclusion applies:
On-Access
ATC/IDS
Ransomware Mitigation
All the above modules
Optionally, add a note about the exclusion in the Description field.
Click the
 Add button.
Add button.Click Save.
To remove a rule from the list, open the three-dot menu in the table and click the Delete option. Alternatively, select the exclusion and click the Delete button at the top of the table.
Adding process exclusions in the Network Protection section of the policy
To exclude a process from traffic scanning in the Network Protection section of the policy settings, follow these steps:
Log in to GravityZone Control Center.
Go to the Policies page from the left side menu.
Create or edit a custom policy.
Go to Network Protection > General and select the Exclusions check box.
From the menu, select Application as exclusion type.
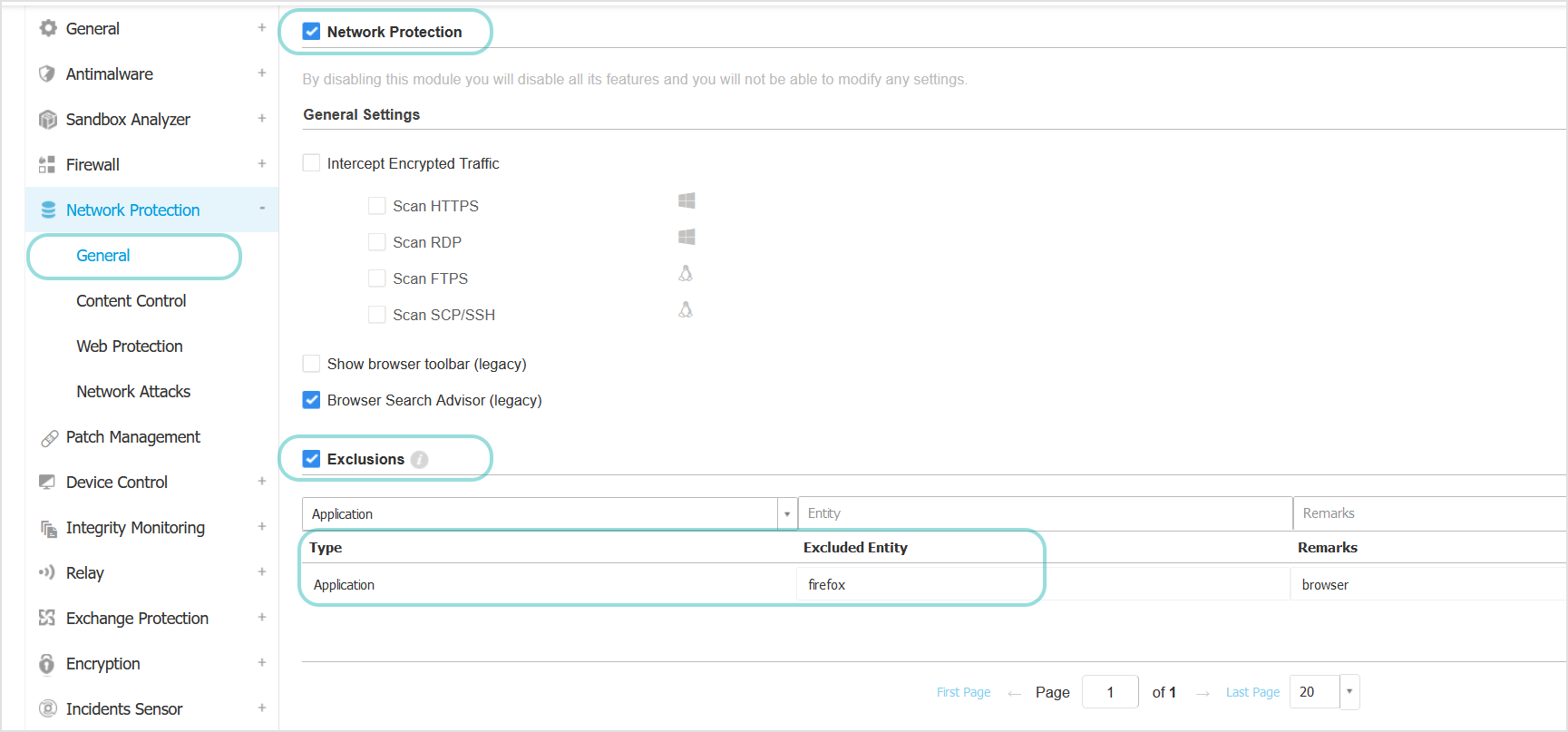
Enter the name of the executable file of the application to be excluded.
For example, enter
calendarto exclude the Calendar application,firefoxto exclude the Mozilla Firefox browser, orelectronto exclude the Visual Studio Code application.Use wildcards to specify any applications matching a certain name pattern.
For example:
c*.exematches all applications starting with "c" (chrome.exe).??????.exematches all applications with a name that contains six characters (chrome.exe, safari.exe, etc.).[^c]*.exematches all application except for those starting with "c".[^ci]*.exematches all application except for those starting with "c" or "i".
Note
You do not need to enter a path and the executable file does not have an extension.
Optionally, add a note about the exclusion in the Description field.
Click the
 Add button.
Add button.Click Save.
To remove a rule from the list, open the three-dot menu in the table and click the Delete option. Alternatively, select the exclusion and click the Delete button at the top of the table.