Blocklist
The Blocklist feature allows you to effectively manage and control access to files and network connections identified as potential threats during incident investigations. By adding potentially harmful files to the blocklist, you ensure these files are prohibited from running on the network, mitigating the risk of damage or the spread of malicious software.
In the Blocklist page you can view and manage Blocklist rules. The activity records can be viewed in User activity log.
Important
The feature requires a Business Security Premium license, or any license that supports the EDR feature.
Blocking rules are added recursively for all companies with a license that includes EDR.
In the Blocklist table, you can view the following details for each item:
Target company
Note
Created by
Date created
Rule type
Source type
Hash type
File name
File hash
Firewall rule name
Command line
Local IP/Mask
Remote IP/Mask
Local port/Port range
Remote port/Port range
Directly connected computers
Remote MAC
Protocol
Direction
IP version
Note
The Blocklist feature includes the following file types:
.exe, .bat, .js, .vbs, .ps1, .jar, .scr, .dll, .hta, .reg, .lnk, .msi, .cpl, .com, .pif, .tmp, .cmd.Date and time are reported according to your local settings.
Add rules to the Blocklist
Blocklist rules serve as guidelines or criteria for creating and managing a list of entities that are denied access for potential threats.
Adding hash values to the Blocklist
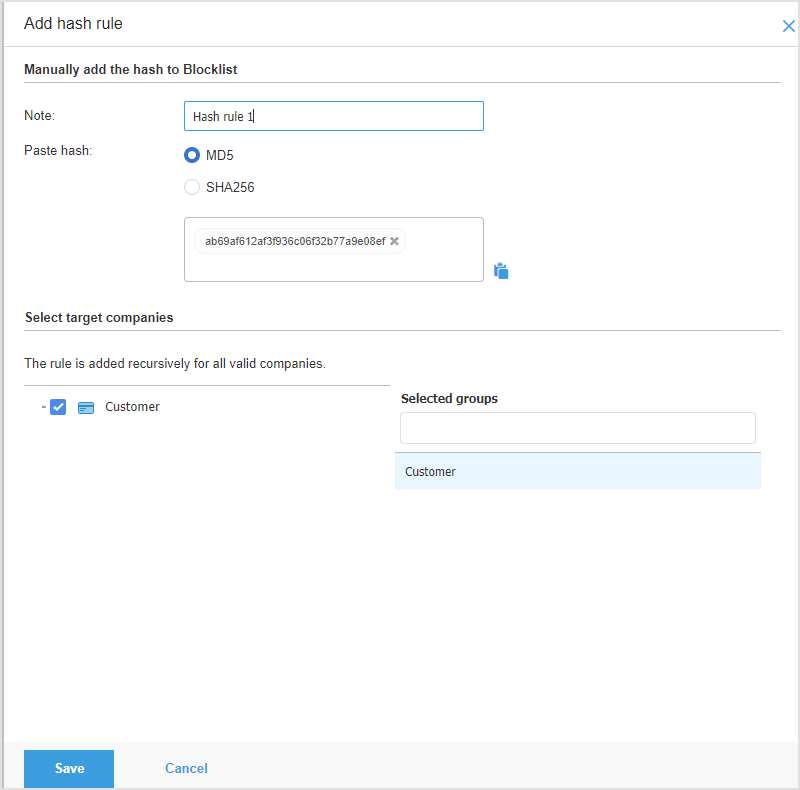
Click the Add rule button at the top of the table.
From the dropdown select Application hash.
Optionally you can type in a Note relevant to the Blocklist rule you are creating.
Choose from MD5 or SHA256 and paste the value in the box below.
Select the target companies for the Blocklist rule.
Note
You can add up to 100.000 hash values to the Blocklist for your companies.
Important
On Linux endpoints, this functionality is available only with specific kernels. For more information, refer to Linux kernels supported by Blocklist and Application Blacklisting.
Any blocking rule applied to Linux containers will be ignored. Applications on the container host can be blocked by hash.
Adding application path values to the Blocklist
Prerequisites
The Content Control module needs to be installed on the endpoint and Application blacklisting must be enabled in the policy of the endpoint for the Path based app blocklist to work on the endpoint.
Important
On Linux endpoints, the Content Control module is not required.
Steps
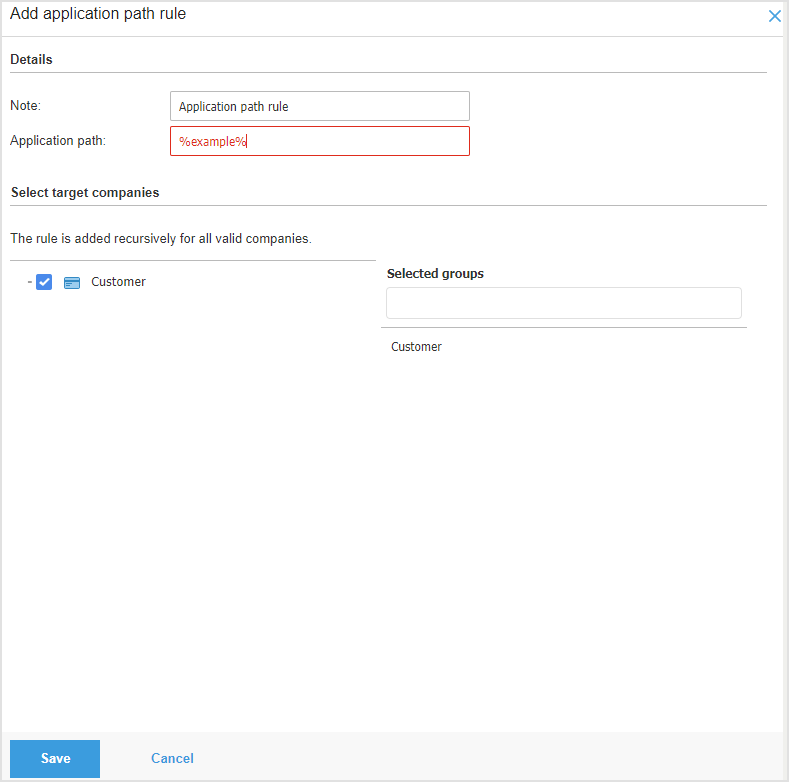
Click the Add rule button at the top of the table.
From the dropdown select Application path.
Optionally you can type in a Note relevant to the Blocklist rule you are creating.
Add the Application path in the specific field.
Note
Please make sure the path format matches the operating system of the target endpoints.
Select the target companies for the Blocklist rule.
Note
You can add up to 10.000 application path values to the Blocklist for your companies.
Adding connection rules to the Blocklist
Important
This functionality is available only on Windows and macOS endpoints.
Prerequisites
The Firewall module needs to be installed on the endpoint and enabled in the policy of the endpoint for the blocklist connection rules to work on a given endpoint.
Steps
Click the Add rule button at the top of the table.
Note
Blocklist rules will be executed before the policy rules. This means that any restrictions or allowances specified in the blocklist will take precedence over the general policy rules.
The blocklist rules are unaffected by changes in the monitor process or adapter settings, and all rules will always be applicable to all adapters.
From the dropdown select Connection.
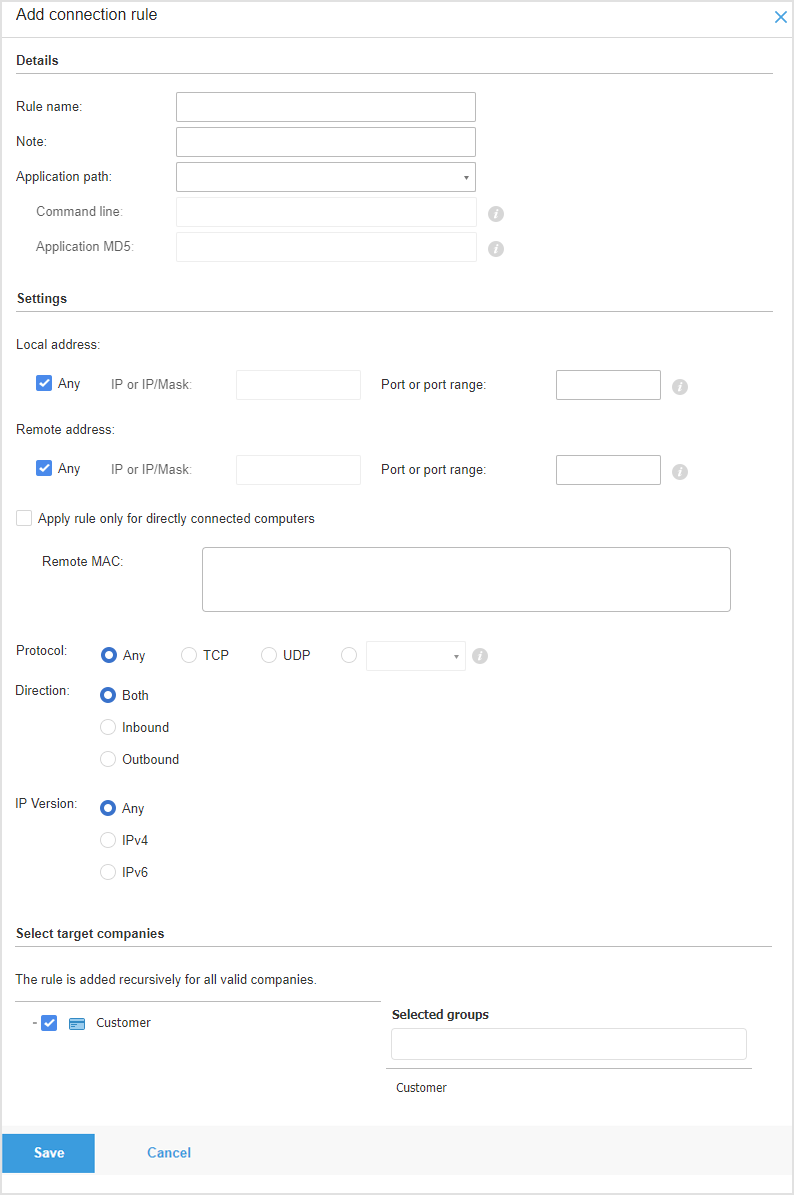
In the Add connection rule screen start filling in the required details:
Firewall rule name - Enter the name under which the rule will be listed in the rules table ( for example, the name of the application the rule applies to).
Note - Optionally you can type in a Note relevant to the Blocklist rule you are creating.
OS type - Select one of the available OS types. Unsupported options are disabled when that OS is selected, but any existing values are preserved if you switch back to a supported OS.
Application path - You can specify the path to the application executable file on the target companies.
Choose from the menu a predefined location and complete the path as needed.
For example, for an application installed in the
Program Filesfolder, select%ProgramFiles%and complete the path by adding a backslash (\) and the name of the application.Enter the full path in the edit field.
It is advisable to use system variables (where appropriate) to make sure the path is valid on all target computers.
Command line - If you want the rule to apply only when the specified application is opened with a specific command in the Windows command line interface, type the respective command in the edit field. Otherwise you can leave it blank.
Application MD5 - If you want the rule to check the application's file data integrity based on its MD5 hash code, enter it in the edit field. Otherwise, leave the field blank.
Note
Make sure that both the command line and the MD5 hash are correctly linked to the application's path. For the rule to function correctly, the application's file path must be accurately specified along with its MD5 hash and any related command line instructions.
Select the Connection rule Settings you want to apply.
Local Address
Can be set to IP or IP/Mask. Specify the local IP address, IP/Mask and port, the rule applies to.
If you have more than one network adapter, you can clear the Any check box and type a specific IP address.
Likewise, to filter connections on a specific port or port range, enter the desired port or port range in the corresponding field.
Remote Address
Specify the remote IP address and port the rule applies to.
To filter the traffic to and from a specific computer, clear the Any check box and type its IP address.
Apply rule only for directly connected computers
You can filter access based on Mac address.
Protocol
Select the IP protocol the rule applies to.
If you want the rule to apply to all protocols, select Any.
If you want the rule to apply to TCP, select TCP.
If you want the rule to apply to UDP, select UDP.
If you want the rule to apply to a specific protocol, select that protocol from the Other menu.
Note
IANA Assigned Internet Protocol Numbers are assigned by the Internet Assigned Numbers Authority (IANA).
You can find the complete list of assigned IANA Assigned Internet Protocol Numbers at http://www.iana.org/assignments/protocol-numbers.
Direction
Select the traffic direction the rule applies to.
Direction
Description
Outbound
The rule applies only for the outgoing traffic.
Inbound
The rule applies only for the incoming traffic.
Both
The rule applies in both directions.
IP version
Select the IP version (IPv4, IPv6 or Any) the rule applies to.
Select the target companies for the Blocklist rule.
Note
You can add up to 1000 connection rules to each of your companies. If you encounter an issue when trying to add a large number of connections check the detailed list of the affected targets and companies provided in Control Center.
To resolve this, you can either select valid child companies as targets or return to the main table and delete some of the old blocklists. Additionally, if you want to add some of the blocklists for child companies that were previously ignored, go back to the bottom target list, select only valid companies, and then try again.
Import rules to Blocklists
Importing hash values to the Blocklist
Click the Import CSV button.
Browse for and select your CSV file.
Click Save.
You may also import local CSV files from your device into the Blocklist page, but first you must make sure your CSV is valid.
To create a valid CSV file for import you must populate the first three columns with the following data:
The first column of the CSV must contain the Hash type: either
md5orsha256.The second column must contain corresponding hexadecimal hash values.
The third column may contain optional string information related to the Note column in the Blocklist page.
Note
Information corresponding to the other columns in the Blocklist page will be filled in automatically when importing the CSV file.
A note is considered valid if it has less than 256 characters.
Importing connection rules to the Blocklist
Click Import at the upper side of the Rules table.
In the new window, click Add and select the CSV file.
Click Save. The table is populated with the valid rules.
To create a valid CSV file for import you must populate the CSV columns with the following data:
The first column should display the corresponding text for each entry in the Column value column, as demonstrated in the example below.
The second column may contain optional string information related to the Note column in the Blocklist page.
The third column should contain the accepted values for each specific entry.
Note
When importing a connection blocklist CSV file, do not include the column value names (headers) in the file. The CSV should only contain the accepted values for each column, in the exact order defined by the format.
Column number | Column value | Note | Accepted values |
|---|---|---|---|
1 |
| Mandatory field The maximum allowed length is 256 characters. | Text |
2 |
| Optional field The maximum allowed length is 256 characters. | Text |
3 |
| Optional field The maximum allowed length is 260 characters. | Absolute paths, system variables and the NoteNot supported when the rule targets both Windows and macOS. |
4 |
| Optional field | Text that contains a command. Example: NoteNot supported when the rule targets both Windows and macOS. |
5 |
| Optional field The maximum allowed length is 32 hexadecimal characters. | md5 NoteNot supported when the rule targets both Windows and macOS. |
6 |
| Mandatory field |
|
7 |
|
This field is mandatory only if you previously chose the value | The accepted values are the decimal values found here. |
8 |
| Mandatory field |
|
9 |
| Mandatory field |
|
10 |
| Mandatory field | Accepted values are yes or no. |
11 |
|
This is a mandatory field only if you previously chose In this case you must enter any valid IP address or subnet. Multiple entries can be added if separated by semicolon (;). | Valid IP addresses or subnets. |
12 |
| Optional field Multiple entries can be added if separated by semicolon (;). | Any valid port number or port ranges are accepted (e.g.: 443-446). |
13 |
| Mandatory field | Accepted values are yes or no. |
14 |
|
This is a mandatory field only if you previously chose | Valid IP addresses or subnets. |
15 |
| Optional field Multiple entries can be added if separated by semicolon (;). | Any valid port number or port ranges (e.g.: 443-446) are supported. |
16 |
| Mandatory field | Accepted values are yes or no. |
17 |
| Optional field You must add a value only if you previously chose yes in the | Any valid MAC address is accepted, and up to 100 entries can be added if separated by semicolon (;). NoteThis field is not supported on macOS. |
18 |
| Optional field | Example: Windows; macOS. Default: Windows |
Importing application path values to the Blocklist
Click Import at the upper side of the Rules table.
In the new window, click Add and select the CSV file.
Click Save. The table is populated with the valid rules.
To create a valid CSV file for import you must follow these steps and populate the columns with the following data:
The first column must contain valid application paths. A path is considered valid if it matches these criteria:
Contains less than 260 characters.
Contains the Windows absolute path.
Does not contain any wildcards
The second column is optional and may contain the rule note.
A note is considered valid if it has less than 256 characters.