Viewing analysis details
The Sandbox Analyzer page displays submission cards by day, in reverse chronological order.
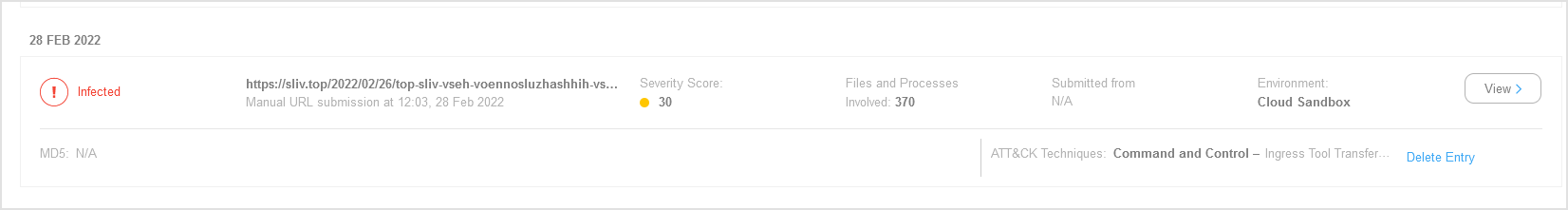
A submission cards includes the following data:
Analysis result
Sample name
Submission type
Severity score
Files and processes involved
Detonation environment
Hash value (MD5)
ATT&CK techniques
Submission status when a result is unavailable
Each submission card includes a link to a detailed HTML analysis report, if available. To open the report, click the View button.
The HTML report provides rich information organized on multiple levels, with descriptive text, graphics and screen captures that illustrate the sample’s behavior in the detonation environment.
This is what you can learn from a Sandbox Analyzer HTML report:
General data about the analyzed sample, such as: malware name and classification, submission details (file name, type and size, hash, submission time and analysis duration).
Behavioral analysis results, which include all the security events captured during detonation, organized into sections.
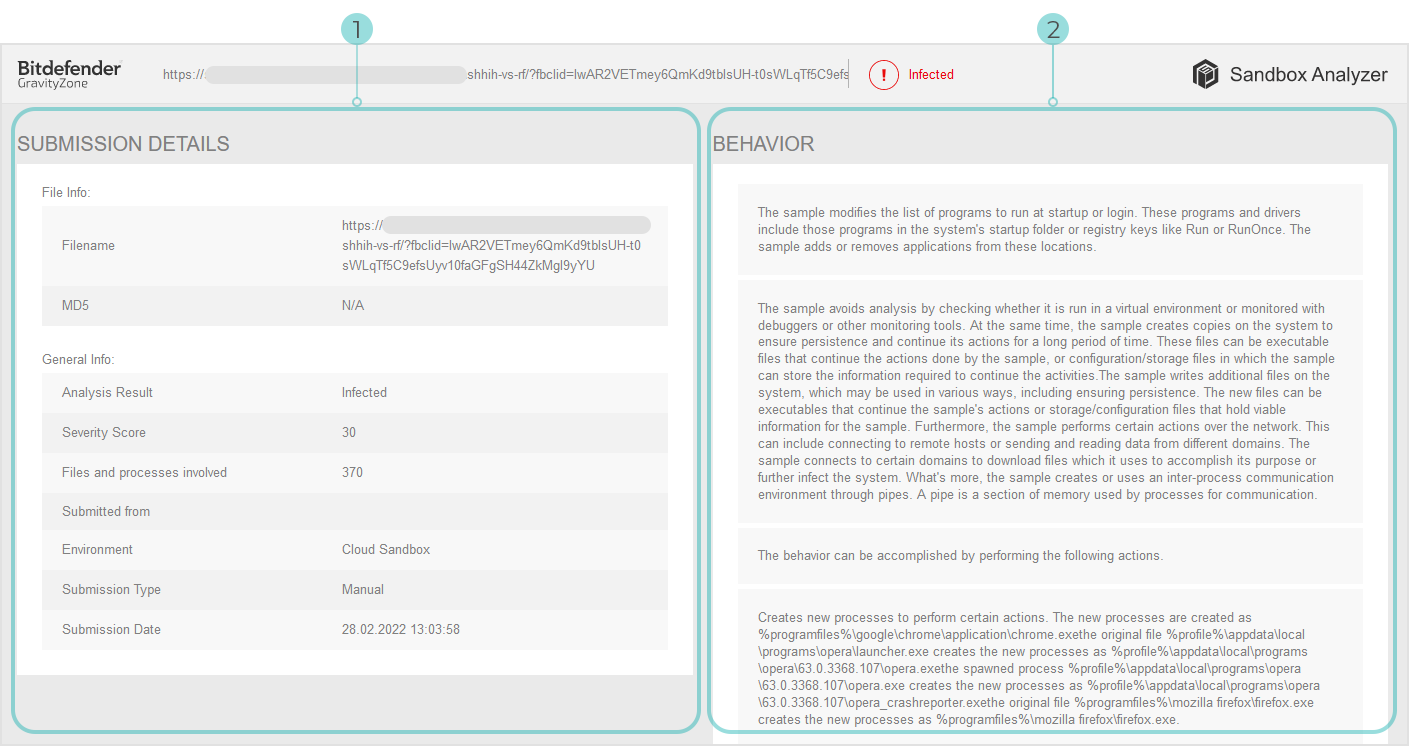
The security events refer to:
Writing / deleting / moving / duplicating / replacing files on the system and on removable drives.
Execution of newly-created files.
Changes to the file system.
Changes to the applications running inside the virtual machine.
Changes to the Windows taskbar and Start menu.
Creating / terminating / injecting processes.
Writing / deleting registry keys.
Creating mutex objects.
Creating / starting / stopping / modifying / querying / deleting services.
Changing browser security settings.
Changing Windows Explorer display settings.
Adding files to firewall exception list.
Changing network settings.
Enabling execution at system startup.
Connecting to a remote host.
Accessing certain domains.
Transferring data to and from certain domains.
Accessing URLs, IPs and ports through various communication protocols.
Checking the indicators of virtual environment.
Checking the indicators of monitoring tools.
Creating snapshots.
SSDT, IDT, IRP hooks.
Memory dumps for suspicious processes.
Windows API functions calls.
Becoming inactive for a certain time period to delay execution.
Creating files with actions to be executed at certain time intervals.
Note
Samples submitted to Cloud Sandbox are deleted immediately after detonation. The resulting HTML reports are available for 365 days.
You can also retrieve the Sandbox Analyzer HTML reports via API.