Managing recommendations
PHASR provides actionable recommendations to enhance security by analyzing user behavior on its devices. These recommendations will be issued for pairs of users and devices named Behavioral profiles. A recommendation can contain multiple behavioral profiles.
PHASR will generate Restrict access recommendations for the behavioral profiles that are not actively using tools from the monitored categories. If the user's behavior changes, PHASR will adapt by generating Allow access recommendations.
PHASR bases its recommendations on monitored rules related to activity types such as Tampering tools, Living off the land binaries, Crypto miners, Piracy tools, Remote admin tools.
You can find a list of all PHASR recommendations under the PHASR recommendations page.
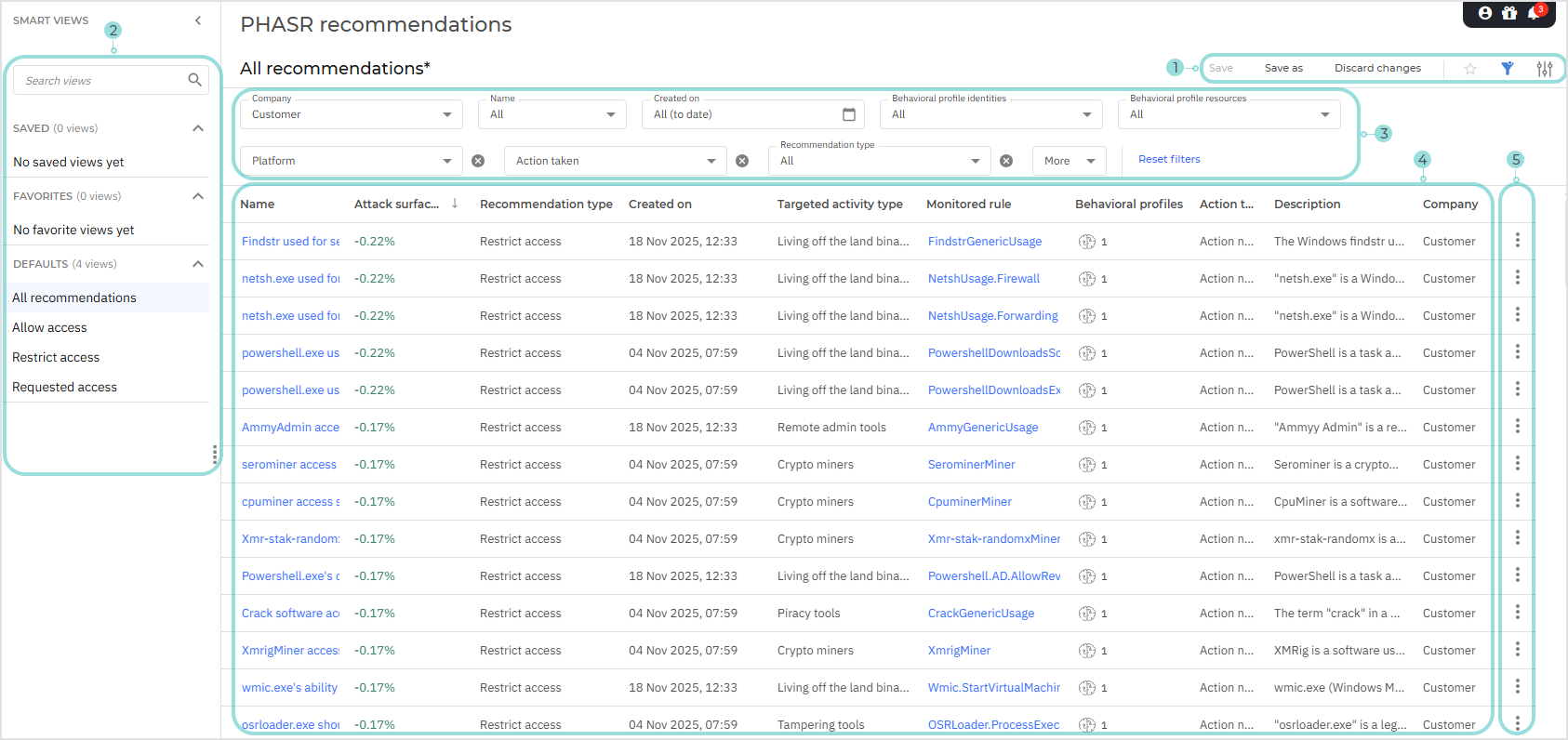
The View options menu. This section provides you with multiple functions for working with smart views:
Save - saves the current smart view with your latest changes
Save as - creates a new smart view based on the current one
Discard changes - reverts all unsaved edits to the last saved version.
Add to favorites - add a saved smart view to your favorites.
Show or hide filters - hide or display the filters menu.
Open settings - displays the Settings panel.
You can use this panel to customize what columns are displayed in the view and enable or disable the Compact view.
The Smart views section. Smart views add a new level of customization to your recommendations page. You can create your own customized views or use predefined ones and quickly switch between them as needed.
The Filters section. You can use these options to customize the risks that are displayed in the below grid.
The following filters are currently available:
Filtering option
Details
Company
Use the searchable drop-down menu to filter the list of recommendations based on the name of the company they belong to.
Only recommendations belonging to the selected company are displayed. This filter is available only to Partner type companies.
Name
Use the searchable drop-down menu to filter the list of recommendations based on their name.
Only selected recommendations are displayed.
Created on
Use the calendar to select two dates.
Only recommendations created between the selected dates are displayed.
Behavioral profile identities
Use the searchable drop-down menu to filter the list of recommendations based on the name of the identity they were made for.
Only recommendations made for the selected identities are displayed.
Behavioral profile resources
Use the searchable drop-down menu to filter the list of recommendations based on the name of the resource they were made for.
Only recommendations made for the selected resources are displayed.
Targeted activity type
Use the drop-down menu to filter the recommendations based on the name of the targeted activity type.
Only recommendations targeting the selected activity types are displayed.
Action taken
Use the drop-down menu to filter the recommendations based on the action they recommend to be taken.
Only recommendations that suggest the selected actions be taken are displayed.
Recommendation type
Use the drop-down menu to filter the recommendations based on their type.
The Recommendations grid. The grid displays all known PHASR recommendations, based on the PHASR learning phase.
The information available for each findings is displayed under the following columns:
Name - The name of the recommendation.
Attack surface reduction - Indicates the impact applying the recommendation would have on the total attack surface.
Recommendation type - The type of the recommendation generated based on PHASR analysis.
Allow access - this option displays the recommendations that have Allow as the suggested action, indicating access will be granted to the recommended asset for the selected users.
Restrict access - this option displays the recommendations that have Restrict as the suggested action, indicating access will be granted to the recommended asset for the selected users.
Allow access request - this option displays the recommendations where users have requested access to a tool that is currently restricted, allowing you to review and decide whether to grant access.
Created on - The time and date when the recommendation was created.
Description - A description for the recommendations.
Targeted activity type - The type of activity targeted by the recommendation.
Possible values:
Tampering tools
Living of the Land Binaries
Crypto miners
Remote admin tools
Piracy tools
Monitored rule - Displays the rule name that was used to generate the recommendation. This column can be hidden.
Behavioral profiles - The total number of profiles affected by the vulnerability covered by the recommendation. The column displays a maximum of 9999 items, with the exact count displayed when hovering over the icon.
Clicking the behavioral profiles icon in the grid opens the Behavioral profiles side panel, which lists the behavioral profiles for which this recommendation was generated.
Action taken - The action that was taken as a result of the recommendation.
Possible values:
Action needed- the default status for recommendations generated by PHASR. The user has to review the recommendations and take action on them.Applied- this status is set after the recommendation has been applied to all the behavioral profiles for which it was generated.Partially applied- this status is set after the recommendation has been applied only to a specific set of behavioral profiles selected by the user.
When an action is required, the status can move in one of two directions. It can change from Action needed to Applied if the action is completed successfully, or it can change from Action needed to Partially applied when the recommendation has been applied only to a specific subset of behavioral profiles selected by the user.
Company - The company where the recommendation was made.
Actions menu - For the Allow access request recommendations you can allow or restrict access, directly from clicking on the inline menu button:
Restrict access - This option will automatically apply the actions suggested by the recommendation and restrict access for the selected users to the recommended asset. The Action taken field associated with the recommendation will change to
AppliedorPartially applied.Allow access - This option will automatically apply the actions suggested by the recommendation and allow access for the selected users to the recommended asset. The Action taken field associated with the recommendation will change to
AppliedorPartially applied.
Note
PHASR issues recommendations as it completes the learning phase for different behavioral profiles. The same recommendation may be generated multiple times, but only if the previous one has a status of Applied or Partially Applied, because the initial learning phase is completed at different times on different endpoints.
If the recommendation has the Action Needed status, it will be updated with more behavioral profiles as the learning phase completes.
Using the smart views
Smart views let administrators customize how recommendations are displayed. A smart view saves the current configuration of filters, columns, and layout preferences, allowing quick switching between different contexts (for example, by company, recommendation type, or activity type).
Smart Views can be:
Predefined - standard views available by default.
Custom - user-created configurations saved for later reuse.
Changes made to a smart view can be saved to update the existing one (except predefined views) or saved as a new custom view.
Allowing access based on a received recommendation
When PHASR detects that user behavior has changed for a user which previously had its access restricted, it may generate an Allow access recommendation. Once this recommendation is generated you can review the behavioral profiles for which it was generated and allow the recommendation to be applied.
You can restrict access based on a specific recommendations by using on of these methods:
In the GravityZone console go to the PHASR recommendations section.
In the table, select a process that is available in one of the targeted activity type by PHASR. Alternatively, click the menu button on the right side of the Recommendations grid and select Allow access.
Click the process name. The recommendation details side panel is displayed.
Select Allow access.
In the Allow access window, under the Behavioral profiles section, select the device for which you wish to allow access.
You can allow access for an entire department, for specific users, or for specific users on specific devices using the checkboxes available in the Behavioral profiles section.
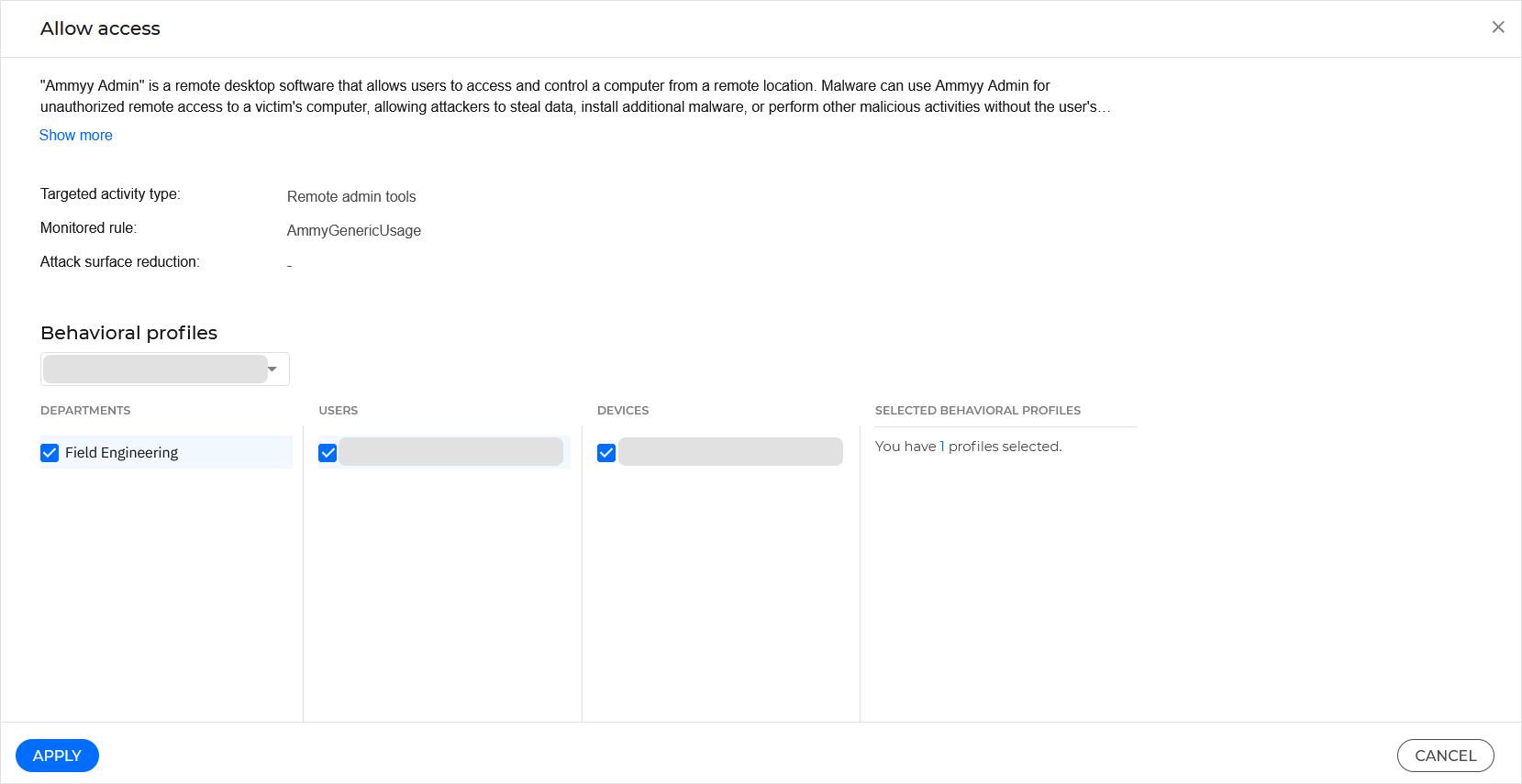
Select Apply.
Restricting access based on a received recommendation
When PHASR detects that user behavior has changed for a user which currently has access to certain assets, it will generate an Restrict access recommendation. Once this recommendation is generated you can review the behavioral profiles for which it was generated and allow the recommendation to be applied.
You can restrict access based on a specific recommendations by following this procedure:
In the GravityZone console go to the PHASR recommendations.
In the table, select a process that is available in one of the targeted activity type by PHASR. Alternatively, click the menu button on the right side of the Recommendations grid and select Restrict access.
Click the process name. The recommendation details side panel is displayed.
Select Restrict access.
In the Restrict access window, under the Behavioral profiles section, select the device for which you wish to restrict access.
You can restrict access for an entire department, for specific users, or for specific users on specific devices using the checkboxes available in the Behavioral profiles section.
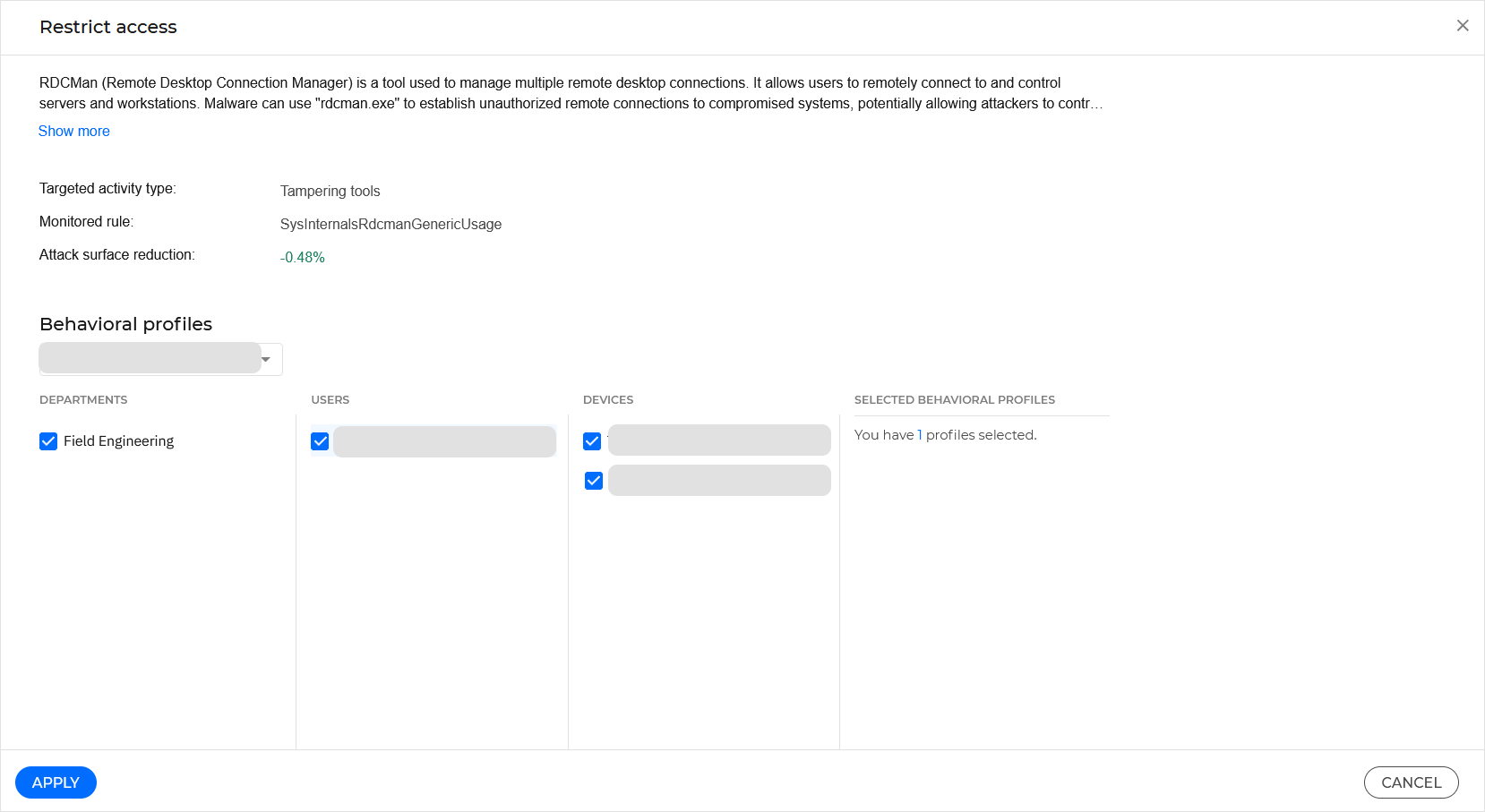
Select Apply.
You can see what applications PHASR is restricting on a specific endpoint by checking the Bitdefender Endpoint Security Tools interface.
Requesting access to a tool
When PHASR blocks a tool, behavioral profiles can request access directly from the BEST interface, whether the restriction was applied automatically (Autopilot) or manually (Direct Control).
Note
This functionality is available only in the BEST new UI. Request access is supported exclusively on endpoints running Windows 10 version 1809 or later or Windows Server 2019 version 1809 or later.
For the behavioral profile to receive alert pop-ups for Request access, the Display alert pop-ups option must be enabled in the applied policy in General > Agent > Notifications.
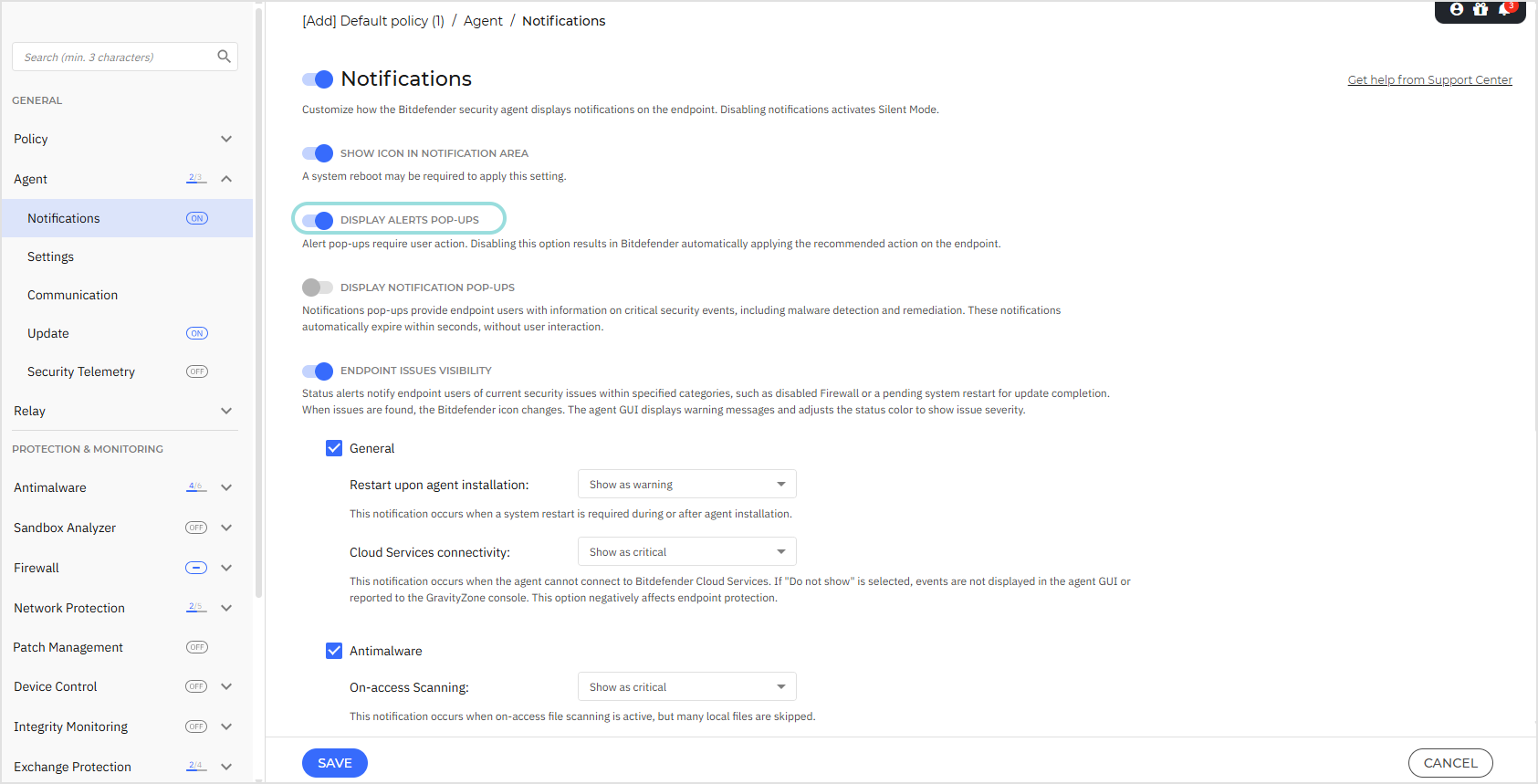
The option to request access is available only if the Request access setting is enabled in the applied security policy under Risk Management > PHASR for the corresponding PHASR category.
When a behavioral profile tries to access a process that PHASR blocks based on a recommendation, a PHASR event is generated in the BEST interface.
The behavioral profile clicks on the Request access button in the generated event.
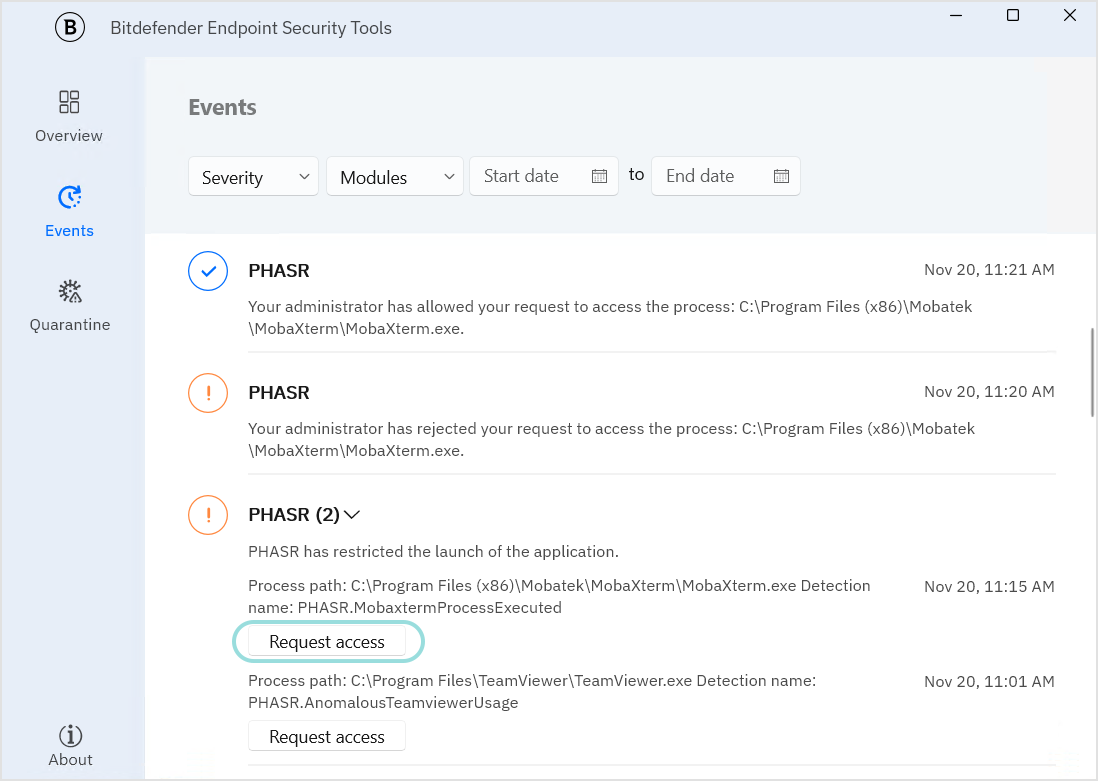
In the dialog window that opens, the behavioral profile enters a short business justification and clicks the Request access button.
Note
If the endpoint is offline, the request is queued locally and sent automatically once the connection to GravityZone is restored.
If the behavioral profile submits multiple access requests for the same application, duplicate recommendations are not created, and the existing recommendation is automatically updated with the latest request.
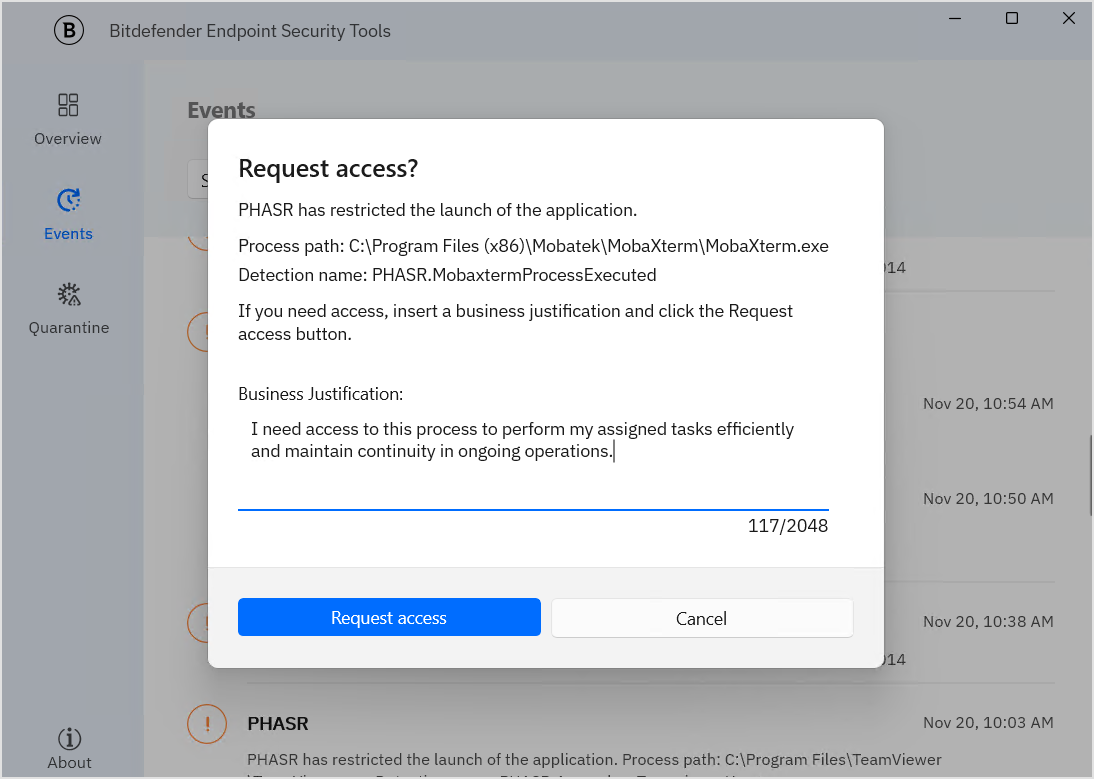
Once submitted, the request is sent to GravityZone, where administrators can review and take action.
In the PHASR recommendations page, open the Requested access smart view to display the requests received. Alternatively you can display the items by using the Recommendation type filter and selecting Allow access request.
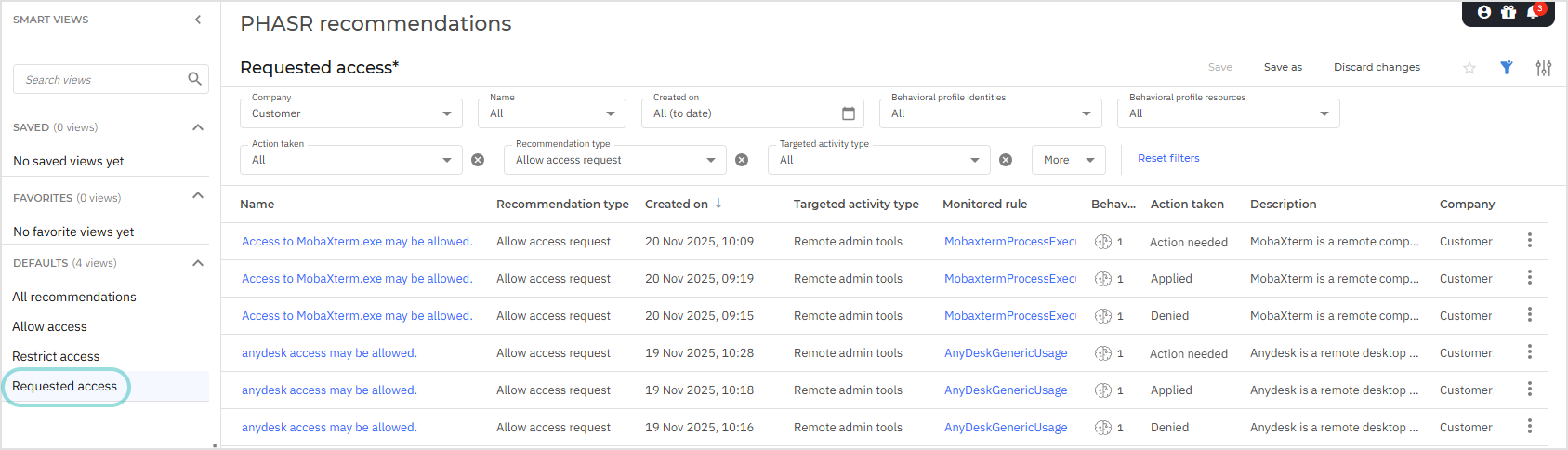
Click the recommendation name to view the request details, including the business justification and available actions.
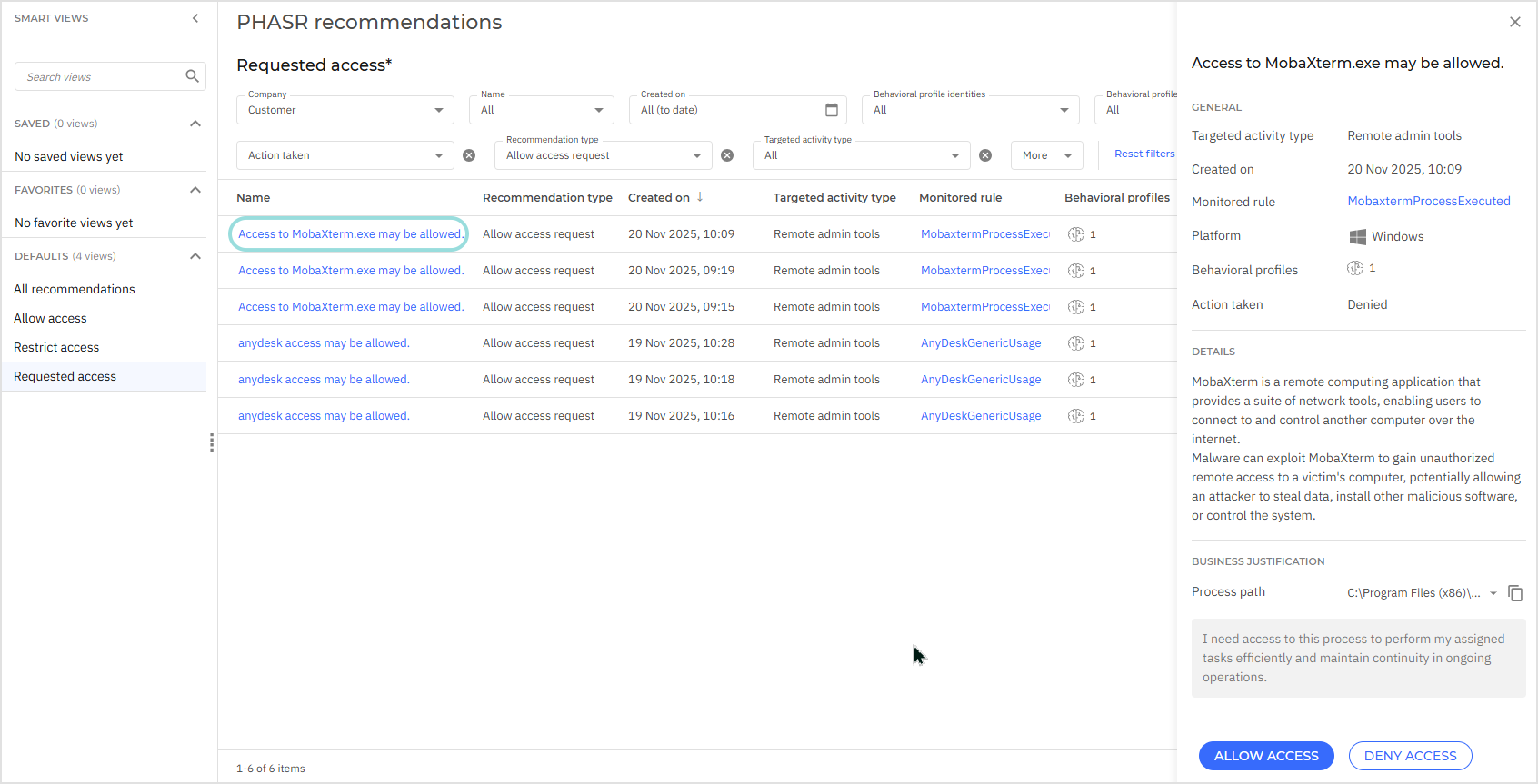
Select one of the following actions:
Allow access - This option automatically applies the actions suggested by the recommendation and allow access for the selected behavioral profiles to the recommended asset.
Deny access - This option automatically denies the request, maintaining the restriction for the selected behavioral profile to the recommended asset.
Note
Request access actions are recorded in User Activity. To view them filter the entries by the corresponding action in the PHASR recommendations area (such as Request access granted or Request access denied).
After an action is applied, the Action taken field for the recommendation updates to Applied.
The behavioral profile has a five-day window to use the tool.
If the tool is not used within those five days, it will be blocked again.
If the behavioral profile does use the tool, access remains active as long its usage continues.
PHASR will block the tool again only if the behavioral profile stops using it and the PHASR learning period has passed, which takes a minimum of 30 days and can extend up to 60 days depending on the rule.
Viewing recommendation details
You can view additional information regarding a recommendation by opening the Recommendation details side panel. To open the side panel, click the name of the recommendation under the Name column:
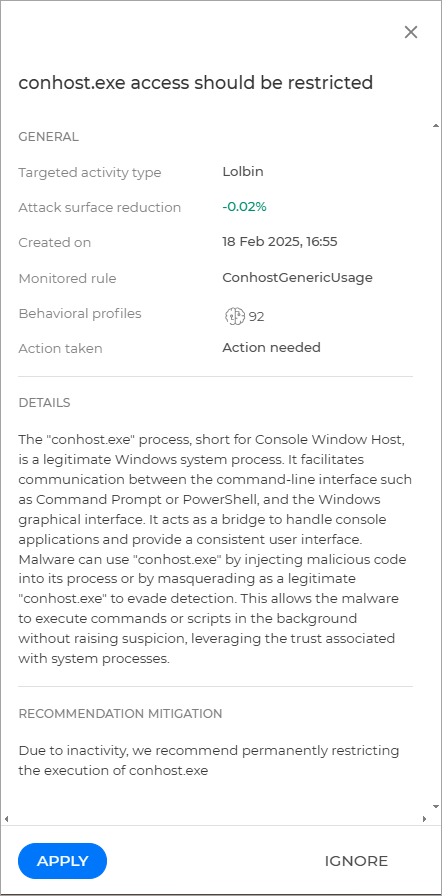
General - this section contains the following information:
Target activity type - The type of activity targeted by the recommendation.
Attack surface reduction - Indicates the impact applying the recommendation would have on the total attack surface.
Created on - The time and date when the recommendation was created.
Monitored rule - Displays the rule name that was used to generate the recommendation.
Note
The monitored rule name is displayed as a link that opens the PHASR monitored rules grid in a new tab, pre-filtered by the selected rule.
Behavioral profiles - Displays the total number of profiles for recommendation.
Action taken - The action that was taken as a result of the recommendation.
Details - This section provides a written description of the vulnerability and how it can be exploited
Recommendation mitigation - The action suggested to fix the vulnerability.
The action button - Depending on the status of the recommendation this button will allow you to Restrict access.