Integrity Monitoring
Integrity Monitoring reviews and validates changes made on Windows and Linux endpoints to assess the integrity of multiple entities.
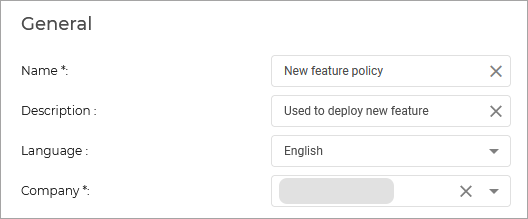
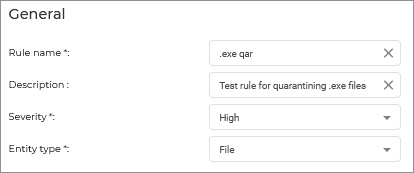
Integrity Monitoring operates based on default rules, provided by Bitdefender, and custom rules. These rules are available in the Policies > Integrity Monitoring Rules page of the Control Center .
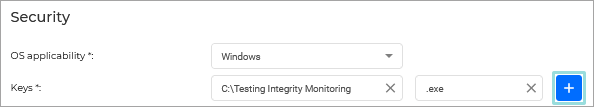
Based on these rules, Integrity Monitoring takes action when events are generated for files, folders, registry entries, users, services and installed software. These events are displayed on the Reports > Integrity Monitoring Events page of the Control Center.
You can also create a portlet, as well as two types of reports based on Integrity Monitoring events:
Integrity Monitoring activity, which displays events from the events page.
Integrity Monitoring configuration changes, which displays Bitdefender Trusted as well as Unapproved events.
Integrity Monitoring also comes with hardcoded restrictors, which automate best practices to reduce alert fatigue and prevent a negative impact on performance.
Integrity Monitoring is available for all standard products, except for GravityZone EDR and Bitdefender FRAT . It is delivered as an add-on for products with a license key, and as a licensing option for monthly subscriptions.
By default, it stores the detected events for 7 days. In addition, it comes with a data retention add-on to store the events. You have three options from which can choose: 90 days, 180 days, and 365 days of data retention.
Note
Events are linked to the data retention add-on in use at the time they were created. If the data retention add-on is modified, only events generated after the change will be subject to the new data retention period.
After you add the license, log back in to GravityZone. Two new pages are available in the main menu of the Control Center:
Under Policies, the new page named Integrity Monitoring Rules contains the rules, rule sets and related options for configuring Integrity Monitoring .
Under Reports, the new page named Integrity Monitoring Events contains all the detected events. The events listed in this page are based on default and/or custom rules.
In addition, the policy settings include a new section called Integrity Monitoring, where you can enable the module and select the rule set that you want to apply with the policy.
Components
Integrity Monitoring uses the following components:
GravityZone Control Center
Security agent (Windows, Linux)
Integrity Monitoring limitations
Windows
Integrity Monitoring monitors a large set of registry keys and values, with some exceptions. For a full list of monitored registry keys and values, refer to this document.
Changes made by GravityZone excluded processes do not generate events.
Custom EDR exclusions do not apply to incidents that are generated based on Integrity Monitoring rules.
Custom EDR exceptions do not apply to incidents that are generated based on Integrity Monitoring rules.
Linux
Integrity Monitoring does not support protected containers.
Integrity Monitoring does not start if the backend is switched from kprobes to auditd.
The InstalledSoftware event is only generated for Debian-based operating systems.
The service_added events only work once per service.
Multiple sequential events are processed at a slower rate.
Different text editors could generate different events for the same file modification due to their use of different APIs.
Operations performed as another user, using the
runusercommand, trigger events with a void user field.Integrity Monitoring is not compatible with 32-bit operating systems.
Permission and ownership change events cannot generate endpoint incidents.
Custom EDR exclusions do not apply to incidents that are generated based on Integrity Monitoring rules.
Install and configure Integrity Monitoring
To start using this feature, follow the steps below:
Important
If your endpoints already have the BEST agent deployed, but the Integrity Monitoring module is not installed, you can use a Reconfigure agent task to add the module to the endpoint.
If no agent is installed, you will need to use an installation package to deploy BEST on your endpoints along with all required modules.
Below we have included both procedures.
Test out the feature
In-depth documentation
For more information about Integrity Monitoring, refer to: