Control Center at a glance
This section serves as orientation through the GravityZone Control Center console and provides a quick description of all first level pages available in GravityZone. The pages are presented in the order that they appear in the console, from top to bottom.
Main pages
Toggle menu view
Use the View Menu button to view, hide, or expand the menu options. Click the button to run though the options sequentially, or double-click to skip.
Main menu options
The menu contains links to all the main Control Center pages.
Pagination toolbar
Depending on the page that is displayed, the Page Toolbar contains buttons or drop-down menus that allow you to interact directly with the information being displayed on the page.
User menu
The User menu provides several account and company management options:
My account. Click this option to manage your user account details and preferences.
My company. Click this option to manage your company account details and preferences.
Integrations. Click this option to manage GravityZone integration with other management platforms.
Credentials manager. Click this option to add and manage the authentication credentials required for remote installation tasks.
Help and support. Click this option to find help and support information.
Feedback. Click this option to display a form allowing you to edit and send your feedback messages regarding your experience with GravityZone.
Theme. You can customize your GravityZone Control Center theme by choosing from: System theme (default), Light theme, Dark theme, or High contrast theme.
Logout. Click this option to log out of your account.
What's new
For important Control Center updates, we add a short description of changes and additions in the What's New section. For all updates, we also include in the section a link to the more detailed Release Notes.
Notifications
Notifications provide easy access to notification messages and also to the Notifications page.
Page content
Displays and allows you to interact with information relevant to the page that is currently selected.
Control Center pages
Home
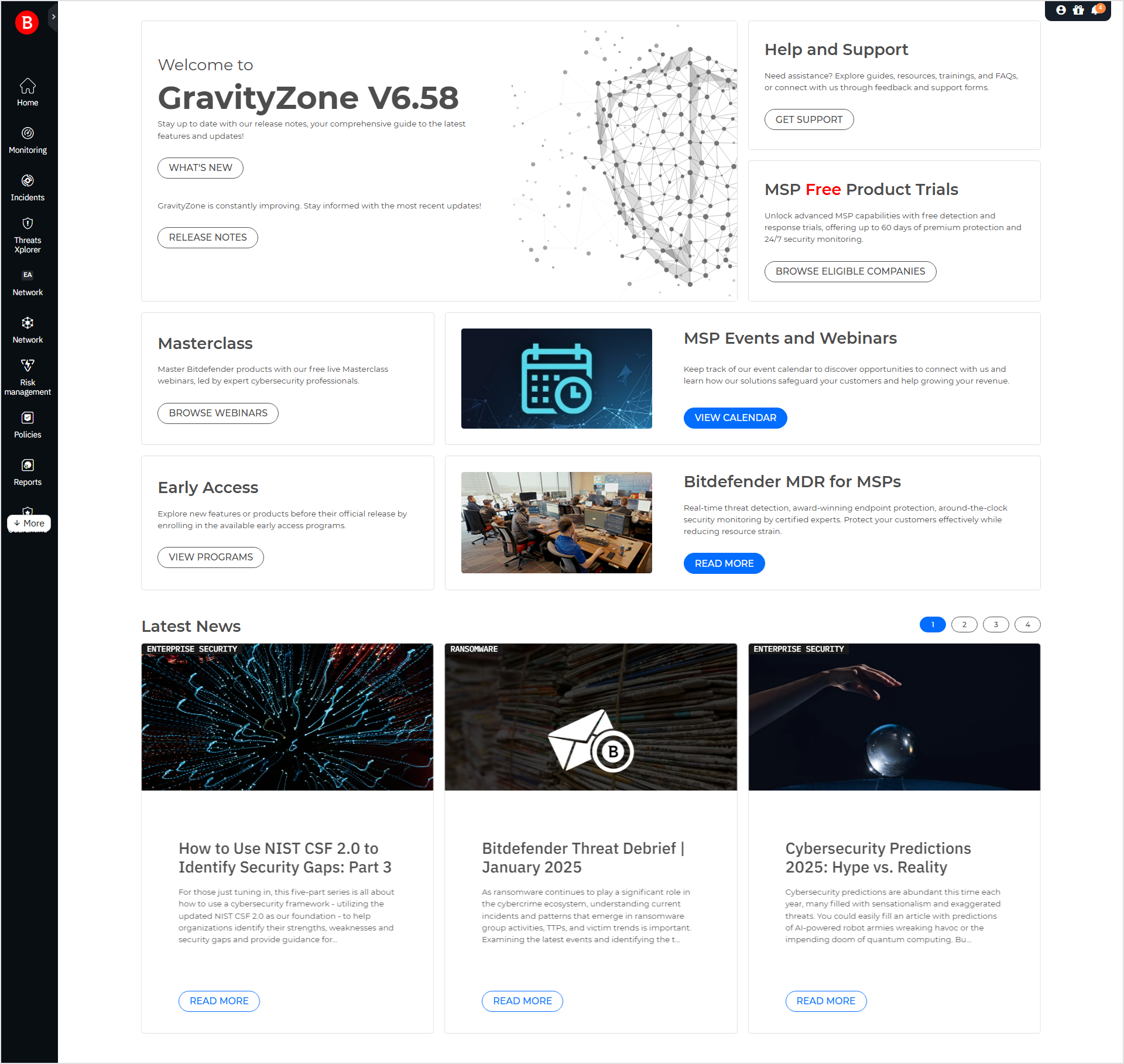
Partner type companies with a monthly subscription can view a Control Center home page that presents a high-level overview of the GravityZone capabilities. By employing a series of widgets, the page displays user-friendly content that simplifies basic tasks and provides access to the latest news.
Monitoring
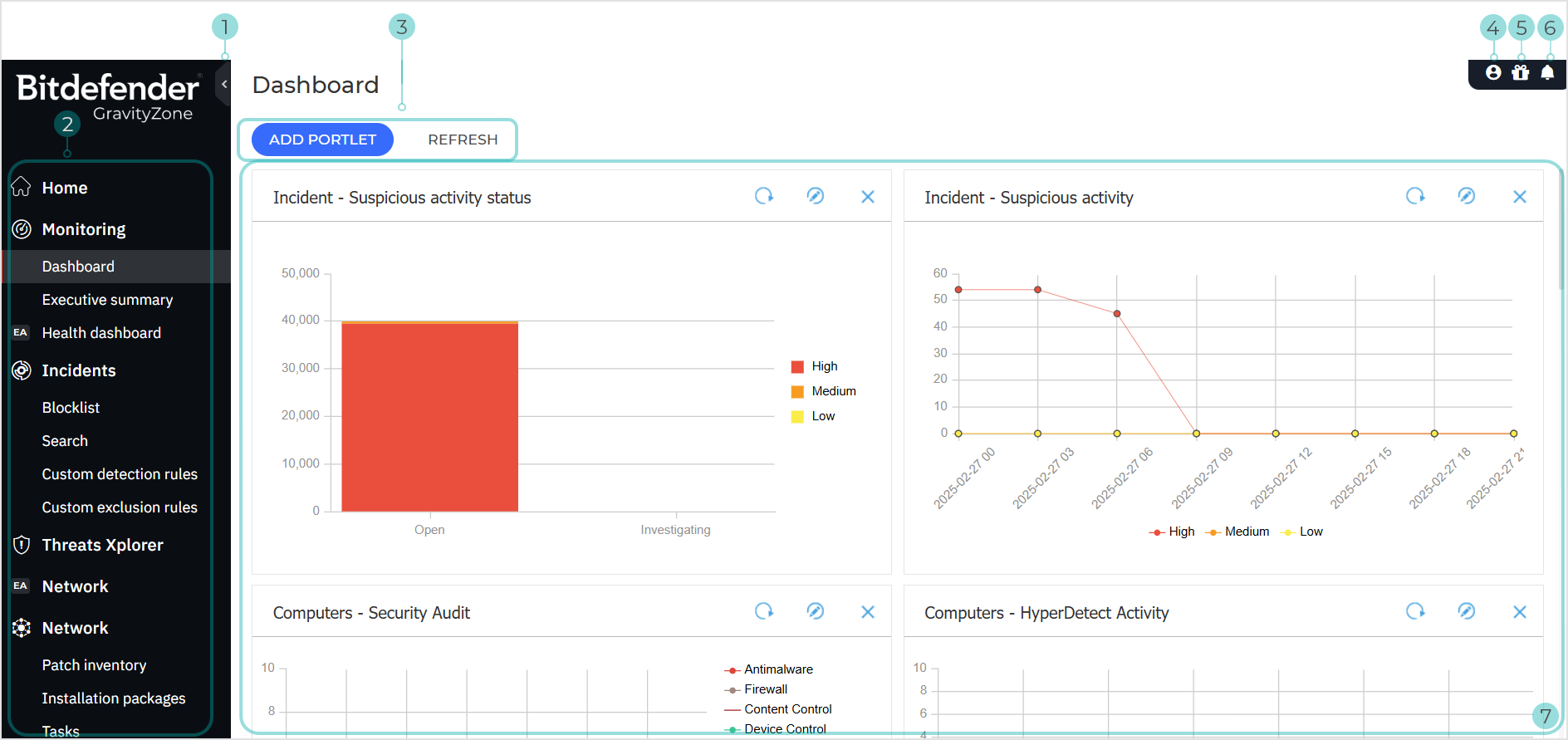
Dashboard
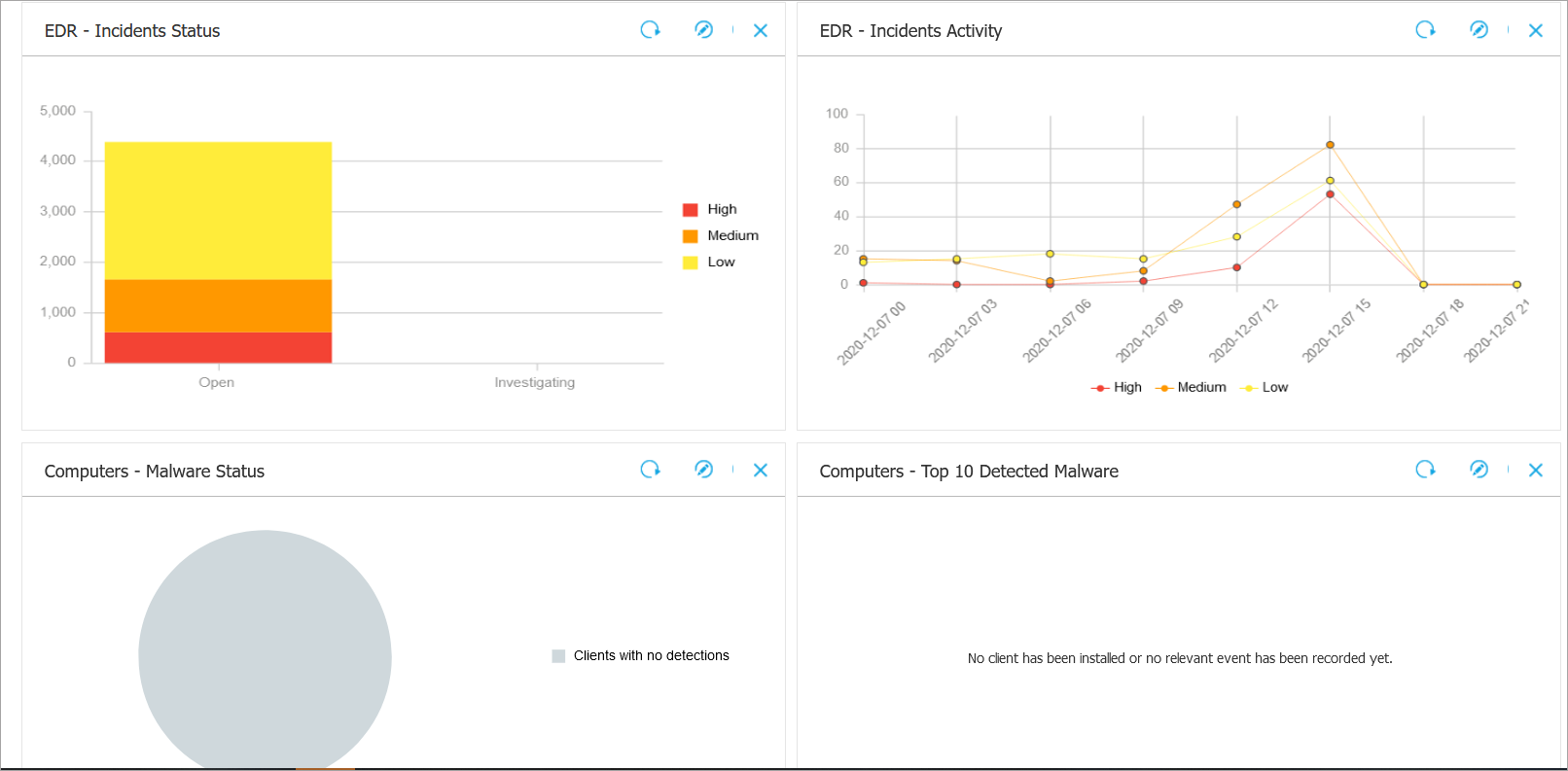
The Dashboard consists of a series of portlets that provide you with security event information from your environment. You can customize the portlets and create your own, specifying the protection mechanism you would like the monitor and the time interval you would like to see in the data.
Portlets are interactive; if you wish to display further information on any event you can click on the datapoint in the portlet representing said event. Doing so will display a report that is representative of the time interval in which the event occurred and provides more in-depth information.
Executive Summary
The Executive Summary page presents a high-level, endpoint-focused version of the Dashboard, providing a series of widgets displaying details about endpoint modules, detections and taken actions, threat types and techniques, your company risk score, threat breakdowns, statistics, and many more.
Note
As opposed to Dashboard portlets, the widgets in the Executive Summary screen are static and read-only.
Incidents
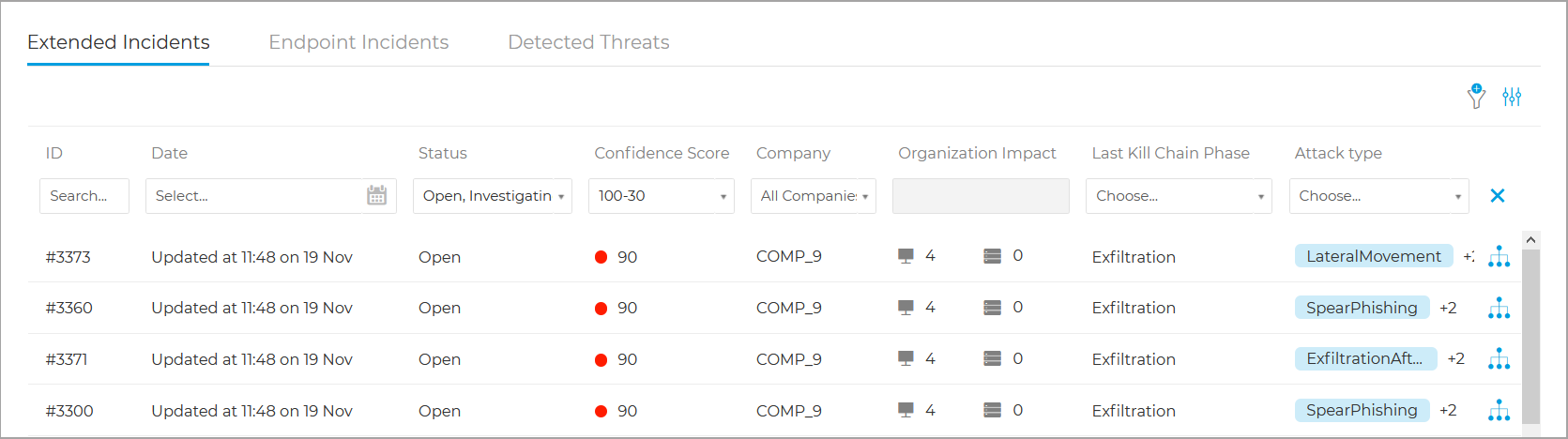
The Incidents screen provides you with a list of recent security incidents going back 90 days, and the ability to search for security incidents in all your managed companies or using a variety of filters and search criteria.
Clicking any incident will display additional information about the event.
You can search for three types of incidents:
Extended Incidents
Note
Available in Ultra Plus.
The Extended Incidents tab displays all organization-wide incidents which require further investigation.
Endpoint Incidents
Note
Available in GravityZone Business Security Enterprise, Ultra Plus and EDR companion standalone.
The Endpoint Incidents tab displays all endpoint-related incidents detected by the BEST Cross-Technology Correlations module which require further investigation.
Detected Threats
Note
Available in GravityZone Business Security Enterprise, Ultra Plus and GravityZone Business Security Premium.
The Detected Threats tab displays a list of threats that have been identified and stopped (or reported, depending on your policies) by GravityZone prevention technologies.
Blocklist
Blocklists stop the spread of malware detected by EDR to other endpoints. To be able to identify these threats, they are given a hash value.
The Blocklist screen displays incidents related to a specific hash value and manage the hashes you are currently tracking.
Search
The search page provides you a complex search engine to locate incidents based on a high number of criteria and parameters. It also provides several predefined search options and the ability to save your preferred search criteria.
Custom Rules
The Custom Rules page allows you to create and manage rules that block or whitelist specific behavior or events.
Detections - They mark specific behavior that might occur in your environment as a valid detection. Any event matching this behavior will generate an appropriate incident.
Exclusions - They mark specific behavior that might occur in your environment as safe. Any event matching this behavior, even if it would normally be flagged, will not generate any incident.
Threats Xplorer
Threats Xplorer is specially designed to offer you highly increased visibility over the detected threats in your network. The feature centralizes detection events from multiple GravityZone technologies and classifies them by category, threat type, remediation actions, and many others. You can easily identify and analyze any event from your company over a specific time interval by using the available filters. You can select filters from the drop-down menu or type keywords that match your desired results.
Network
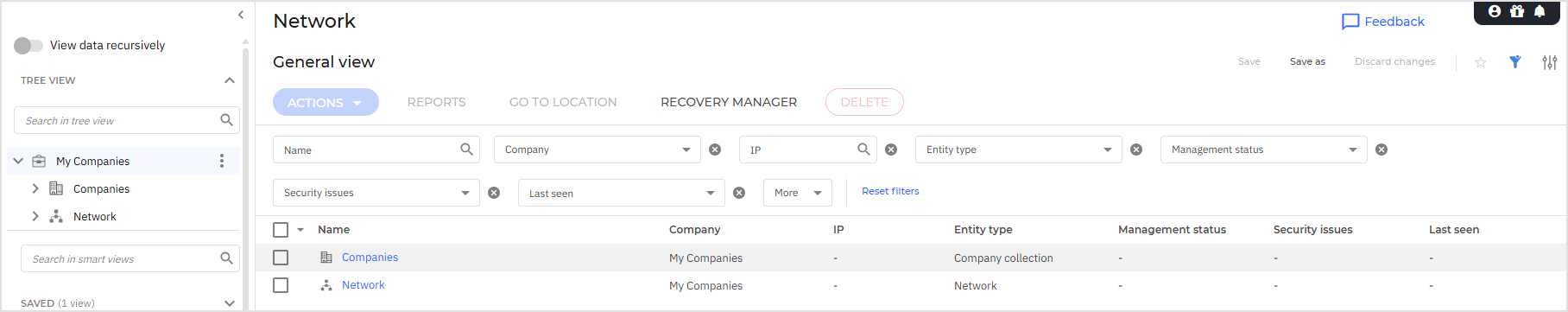
In the Network page you can display, search for, and manage your companies, networks and endpoints. For each entity you can perform various operations such as display additional information, create tasks and reports, assign policies, troubleshoot and more.
Patch Inventory
The Patch Inventory page displays all patches discovered for the software installed on your Windows and Linux endpoints and provides several actions you can take on these patches.
Installations Packages
The Installation Packages page allows you to manage, create, download and send agent installation kits.
You can customize an installation package to specify the language, modules, roles, scan mode and method of installation.
Tasks
The tasks page displays a list of all the tasks that were initiated inside your managed companies. Each task provides additional information. You can narrow down the list of displayed tasks by using several filters.
Tags Management
The Tags Management page displays the list of all endpoint tags available in the Network. Tags are pieces of information that help you easily identify and take actions on managed endpoints, such as assigning policies based on specific rules or filtering items in the Network page.
Risk Management
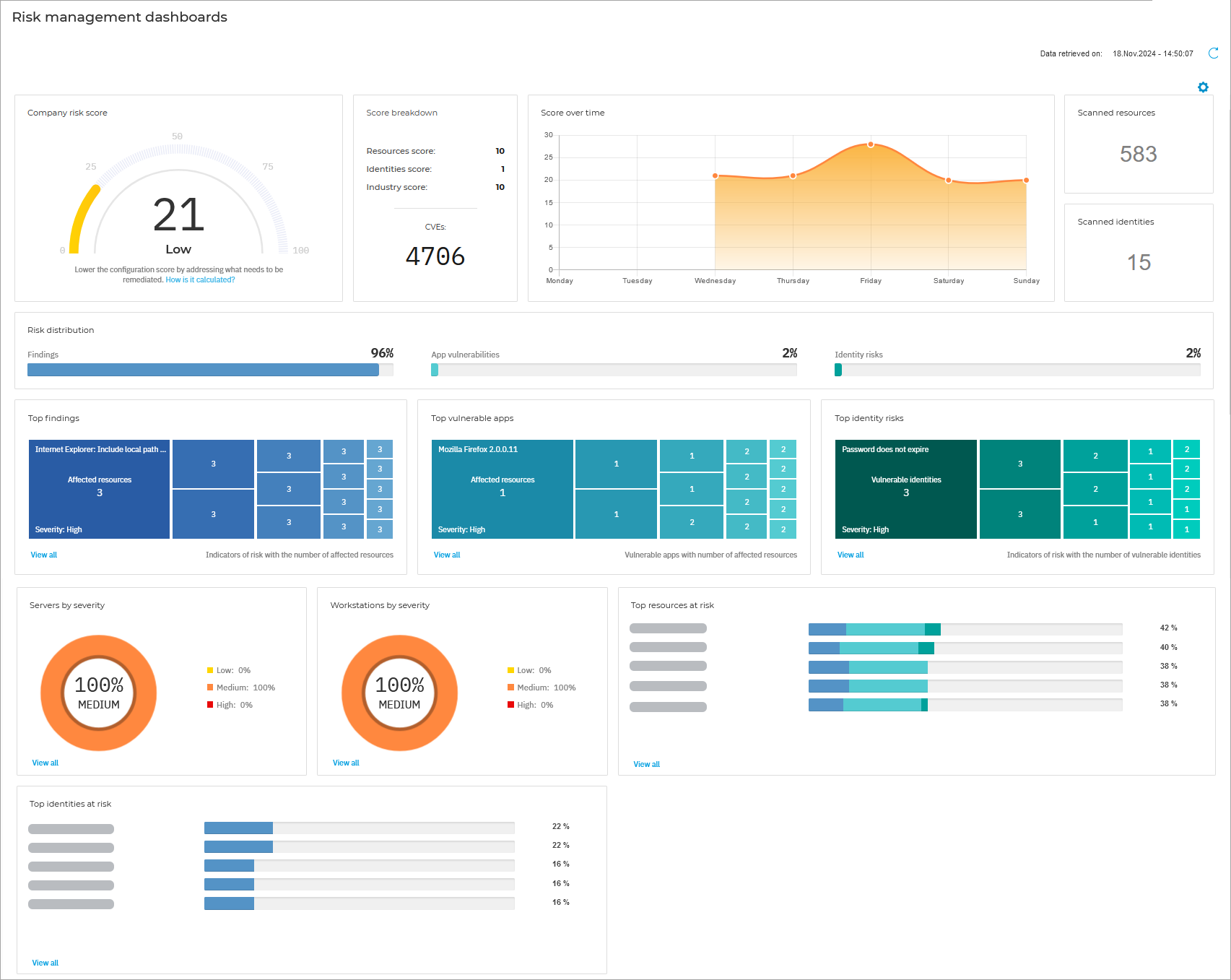
The Risk Management page provides you with a network and operating system risk overview and with the capability of creating and managing scan tasks. You can set the tasks to run recurrently on specific endpoints and choose from a large number of indicators of risk to search for to locate any vulnerabilities.
Security Risks
The Security Risks page displays the results of the scan tasks created in the Risk Management page. The results contain information on possible risks, affected devices and vulnerable users in a fully customizable table formation with complex filtering options.
Companies View
As a partner, in the Companies View page you can display a high level overview of risk management applied over all your companies. You can view each company's risk score, search or filter out results and export lists as .csv files.
Policies
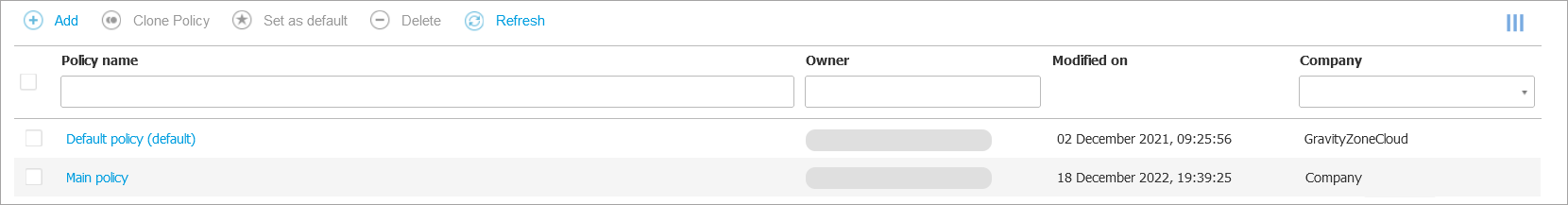
In the Policies page you can create, customize and assign your company's security policies.
A policy specifies the security settings to be applied on target network inventory objects (computers, virtual machines or mobile devices). You can create as many policies as you need based on security requirements, for each type of managed network object.
Configuration Profiles
In the Configuration Profiles page, you can create and manage collections of settings outside policies so that you apply them in your network in an efficient manner.
Assignment rules
In the Assignment Rules page you can define user and location-aware policies. For example, you can apply more restrictive firewall rules when users connect to the internet from outside the company or you can enable Web Access Control for users that are not part of the administrators group.
Integrity Monitoring Rules
In the Integrity Monitoring Rules page you can set up rules that allows the Integrity Monitoring feature to take action when events are generated for files, folders, registry entries, users, services and installed software.
Reports
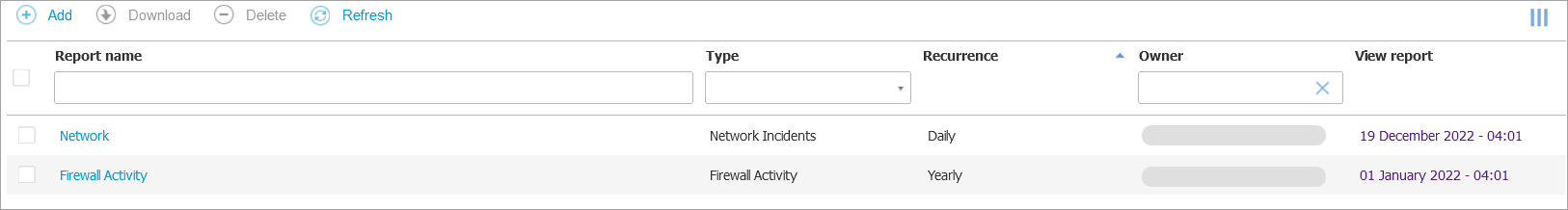
The Reports page allows you to create and view the results of multiple types of reports reports on the security status of your managed network objects. Reports can consolidate data from the entire network of managed network objects or from specific groups only can be used for multiple purposes.
Several different report types are available so that you can easily get the information you need. The information is presented as easy-to-read interactive charts and tables, allowing you to quickly check the network security status and identify security issues.
Ransomware Activity
The Ransomware Activity page provides information on the ransomware attacks that GravityZone has detected on the endpoints you manage, and provides you with the necessary tools to recover the files affected during the attacks.
Integrity Monitoring Events
The Integrity Monitoring Events page contains all the detected events which have been triggered by on default and/or custom rules.
Quarantine
Computers and Virtual Machines
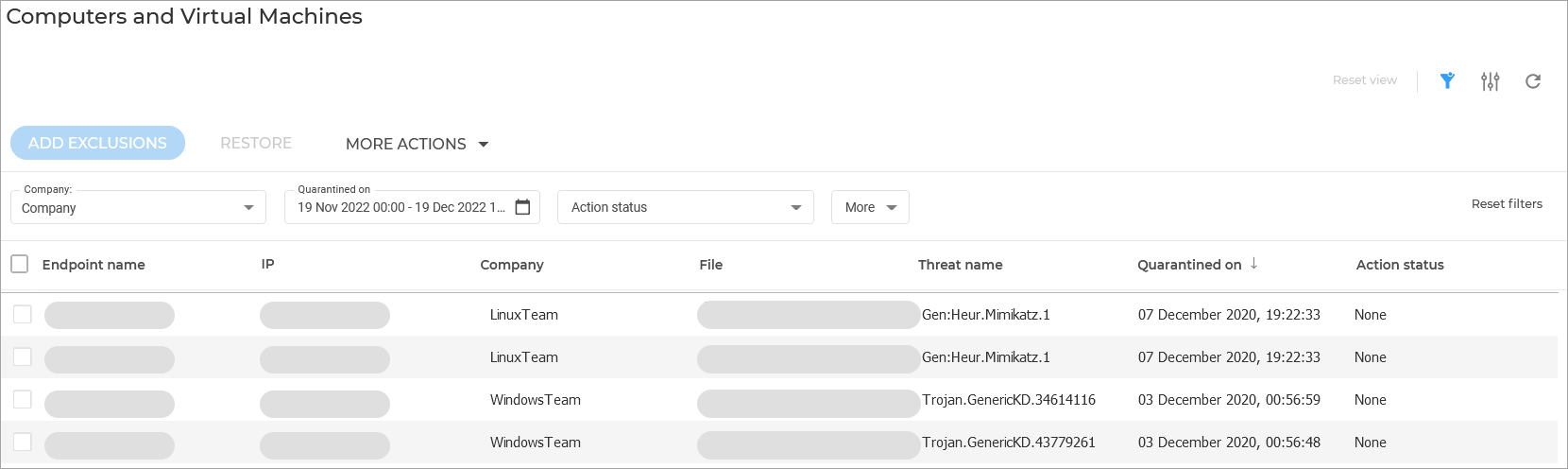
The Quarantine page provides on overview on all malicious files, such as malware-suspected, malware-infected or other unwanted files that have been detected by GravityZone protection. You can search or filter through the list of files, display additional information on each of them and decides on whether to restore, download or delete the files.
When a virus or other form of malware is in quarantine, it cannot do any harm because it cannot be executed or read. GravityZone moves files to quarantine according to the policies assigned to endpoints.
Exchange Servers
The Exchange quarantine contains emails and attachments. The Antimalware module quarantines email attachments, whereas Antispam, Content and Attachment Filtering quarantine the whole email.
Companies
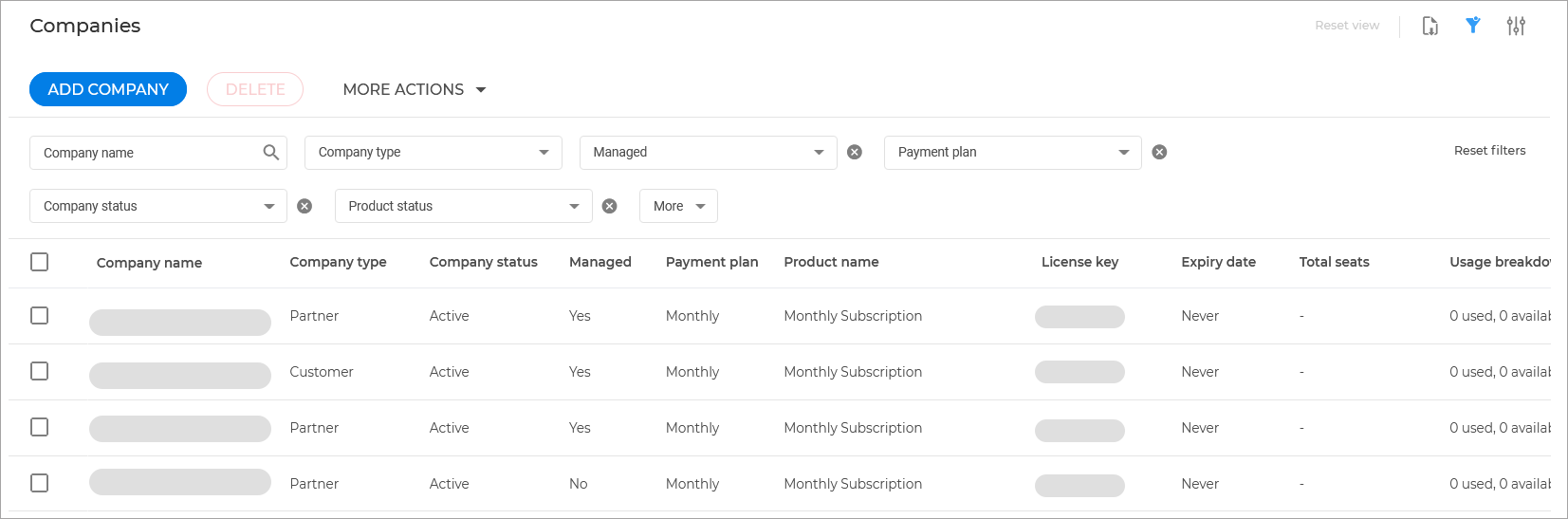
The Company page provides you with a list of all managed companies and allows you to create additional companies or manage already existing ones. You can modify company information, login security settings, license usage and assigned protection modules.
Custom Fields
In the Custom Fields page you can manage, import and export custom fields used to store third party or other custom data and facilitating billing automation.
Accounts
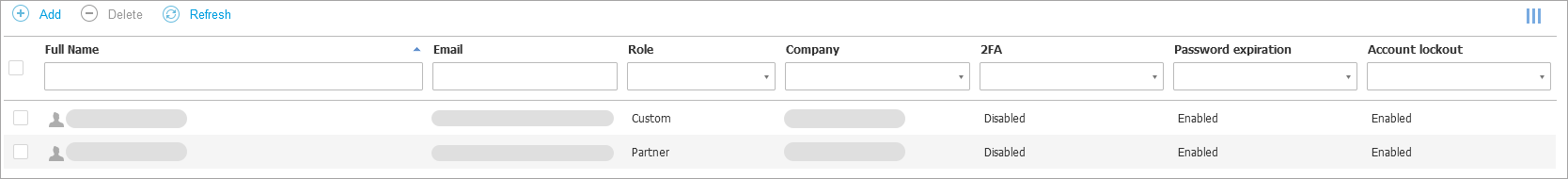
In the Accounts page you can create and manage all your company user accounts. For each user you can add personal information, modify login security settings and assign a default language, timezone and user role.
User Activity
You can use the User Activity page to search for any actions taken by a specific user on a specific company and logged by Control Center.
Sandbox Analyzer
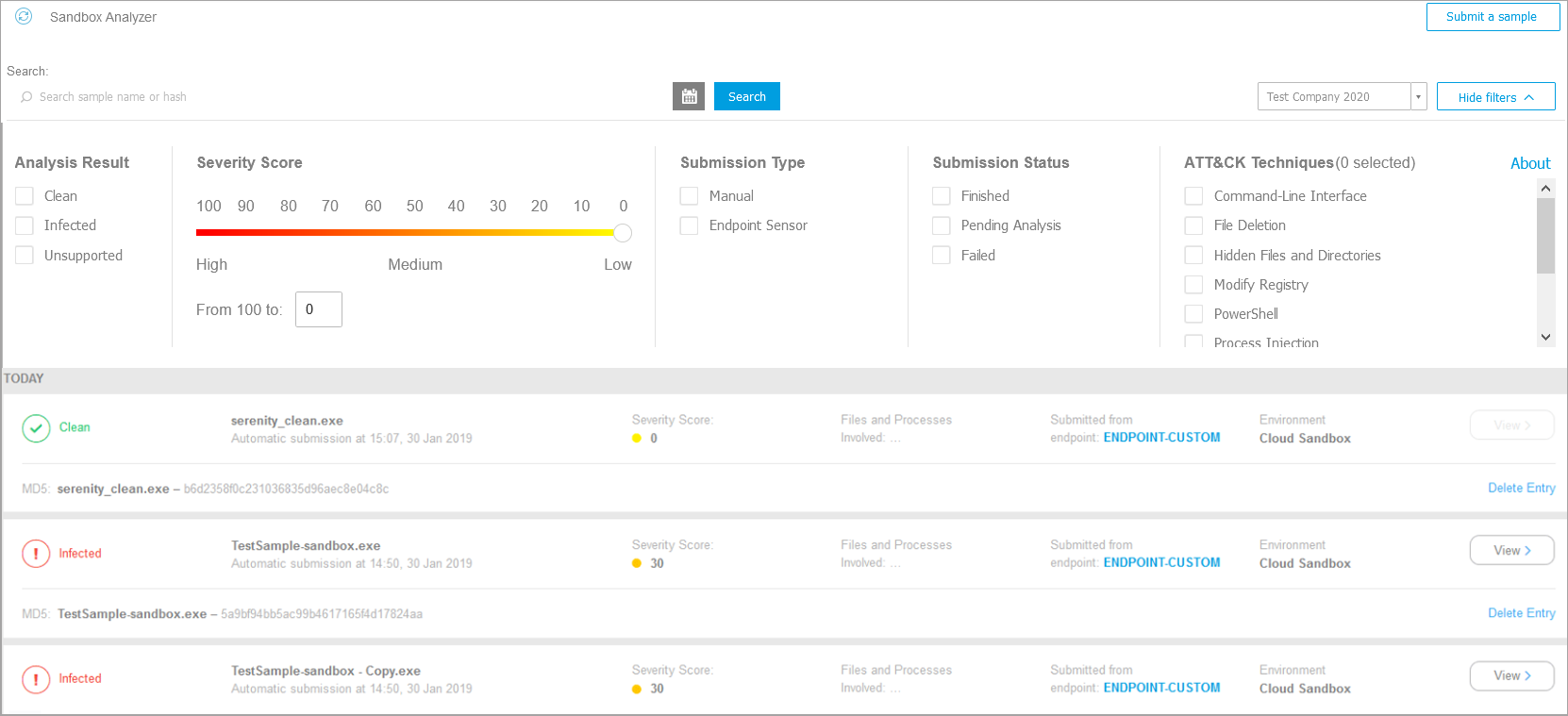
In the Sandbox Analyzer page you can configure the Sandbox Analyzer settings for automatic submission via Bitdefender Endpoint Security Tools.
Sandbox Analyzer provides a powerful layer of analysis by performing automatic detonation of suspicious content in a secure cloud environment, for files not yet signed by Bitdefender antimalware engines.
Manual Submission
In the Manual Submission page you can send samples of suspicious objects to Sandbox Analyzer, to determine whether they are threats or harmless files.
Email Security
In the Email Security page you can access the Email Security console and create accounts for your managed companies.
Bitdefender GravityZone Email Security is a cloud-driven email security gateway able to protect any type of email service against various types of email-centric threat vectors.
Mobile Security
In the Mobile Security page you can access the Mobile Securityconsole and create accounts.
Mobile Security is a cloud-only mobile security solution able to protect mobile devices with Android or iOS operating systems against multiple threat vectors.
Configuration
In the Configuration page, you can configure settings related to Network Settings, Security Servers Settings, and Sensors Management.