Encryption
In the Encryption section of the policy, you can control the encryption settings on the endpoints.
The Encryption module manages full disk encryption on endpoints by leveraging BitLocker on Windows, and FileVault and the diskutil command-line utility on macOS, respectively.
GravityZone is able to provide these benefits:
Data secured in case of lost or stolen devices.
Extensive protection for the most popular computer platforms in the world, by using recommended encryption standards with full support from Microsoft and Apple.
Minimal impact on the endpoints’ performance due to the native encryption tools.
Note
This module is available for:
Windows for workstations
Windows for servers
macOS
The Encryption module operates the following solutions:
BitLocker version 1.2 and later, on Windows endpoints with a Trusted Platform Module (TPM), for boot and non-boot volumes.
BitLocker version 1.2 and later, on Windows endpoints without a TPM, for boot and non-boot volumes.
FileVault on macOS endpoints, for boot volumes.
diskutil on macOS endpoints, for non-boot volumes.
For the list of operating systems supported by the Encryption module, refer to GravityZone requirements.
Note
Availability and functioning of this feature may differ depending on the license included in your current plan.
Activation
To use Full Disk Encryption, you first must make sure that this feature is activated with your GravityZone product and then you must configure it in the policy settings.
Full Disk Encryption is a feature that requires activation based on license key. To do this, go to Configuration > License and enter the license key. To check the availability of Full Disk Encryption, open the policy settings or create a new installation package and see if Encryption appears among the listed modules.
Full Disk Encryption is activated differently for customer companies with yearly and monthly licenses.
For customer companies with yearly license, Full Disk Encryption comes as an add-on that requires activation based on license key.
For customer companies with monthly license, you can allow Full Disk Encryption management for each company, without providing a license key.
Customer companies with yearly license
To activate Full Disk Encryption for customer companies with yearly license:
Log in to Control Center.
Go to Companies page from the left side menu.
Click the name of the company you want to enable Full Disk Encryption for.
Under the License section, enter the license key for Full Disk Encryption in the Add-on key field.
Click Add. The add-on details appear in a table: type, license key and the option to remove the key.
Click Save to apply the changes.
Customer companies with monthly license
To allow Full Disk Encryption management for customer companies with monthly license:
Log in to Control Center.
Go to Companies page from the left side menu.
Click the
 Add button in the action toolbar.
Add button in the action toolbar.Fill in the required details, select Customer for company type and Monthly Subscription for license type.
Select the Allow company to manage Encryption check box.
Click Save to apply the changes.
The partner companies have by default the Full Disk Encryption settings and they cannot enable or disable this feature.
Configuration
To manage endpoint encryption in Control Center, click the Encryption Management toggle on the Encryption > General page to enable the feature. As long as this setting is active, endpoint users cannot manage encryption locally and all their actions will be canceled or reverted.
Note
Disabling this setting will leave the endpoint volumes in their current state (encrypted or unencrypted) and the users will be able to manage encryption on their machines.
Note
This topic covers the Full Disk Encryption settings from the GravityZone console perspective. For details on encryption and decryption flows on endpoints, best practices and use cases, refer to GravityZone Full Disk Encryption FAQ. See also the requirements section for Full Disk Encryption.
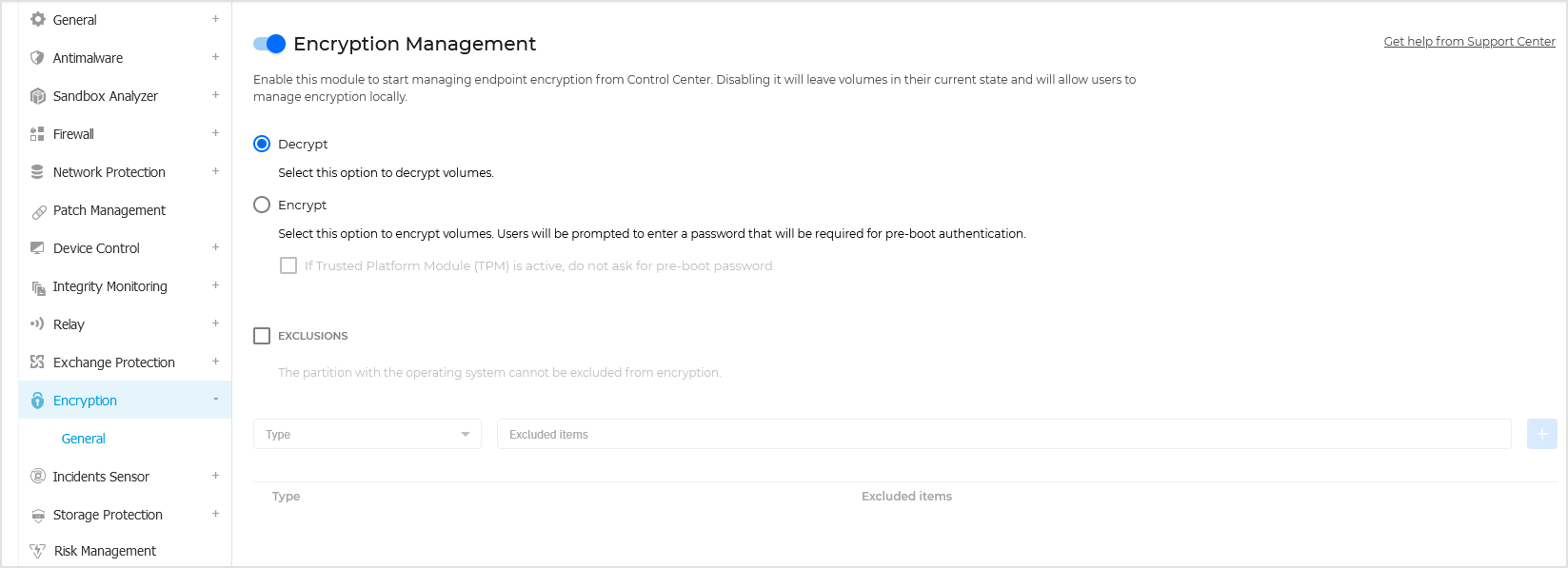
To manage the encryption and decryption processes, two options are available:
Decrypt – decrypts volumes and keeps them unencrypted when the policy is active on the endpoints.
Encrypt – encrypts volumes and keeps them encrypted when the policy is active on the endpoints.
Under the Encrypt option, you can select the check box If Trusted Platform Module (TPM) is active, do not ask for password to encrypt. This setting provides encryption on Windows endpoints with TPM, without requiring an encryption password from users.
GravityZone supports the Advanced Encryption Standard (AES) method with 128 and 256-bit keys on Windows and macOS. The actual encryption algorithm used depends on each operating system configuration.
Note
GravityZone detects and manages volumes manually encrypted with BitLocker, FileVault and diskutil. To start managing these volumes, the security agent will prompt the endpoint users to change their recovery keys. In case of using other encryption solutions, the volumes must be decrypted before applying a GravityZone policy.
Encrypting volumes
To encrypt volumes:
Click the Encryption Management toggle to enable the feature.
Choose the Encrypt option.
The encryption process begins after the policy becomes active on the endpoints, with some particularities on Windows and Mac.
Note
Encryption and decryption are managed exclusively by device-type policies. Volume encryption cannot be managed by rule-based policies.
On Windows
By default, the security agent will prompt the users to configure a password to start encryption. If the machine has a functional TPM, the security agent will prompt the users to configure a personal identification number (PIN) to start encryption.
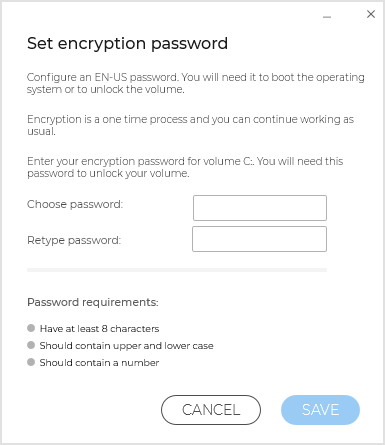
The users have to enter the password or PIN configured at this stage every time the endpoint starts, in a pre-boot authentication screen.
Note
The security agent allows you to configure the PIN complexity requirements and the users’ privileges to change their PIN through BitLocker Group Policy (GPO) settings.
To start encryption without requiring a password from the endpoint users, enable the check box If Trusted Platform Module (TPM) is active, do not ask for pre-boot password. This setting is compatible with Windows endpoints having TPM and UEFI.
When the check box If Trusted Platform Module (TPM) is active, do not ask for pre-boot password is enabled:
On unencrypted endpoint:
The encryption proceeds without requiring a password.
The pre-boot authentication screen does not appear when starting the machine.
On endpoint encrypted with password:
The password is removed.
The volumes remain encrypted.
On encrypted or unencrypted endpoint without TPM or with TPM not detected or not functioning:
The user is prompted to enter a password for encryption.
The pre-boot authentication screen appears when starting the machine.
When the check box If Trusted Platform Module (TPM) is active, do not ask for pre-boot password is disabled:
The user must enter a password for encryption.
The volumes remain encrypted.
On Mac
To start encryption on boot volumes, the security agent will prompt the users to enter their system credentials.
To start encryption on non-boot volumes, the security agent will prompt the users to configure an encryption password. This password will be required to unlock the non-boot volume every time the computer starts. If the computer has more than one non-boot volume, the users must configure an encryption password for each one of them.
Note
The Encryption module bypasses silent mode on macOS. Therefore, even if you disable notifications in the policy active on endpoints, users will still be prompted to take action if the case.
Decrypting volumes
To decrypt volumes on the endpoints:
Click the Encryption Management toggle to enable the feature.
Choose the Decrypt option.
The decryption process begins after the policy becomes active on the endpoints, with some particularities on Windows and Mac.
On Windows
The volumes are decrypted with no interaction from users.
On Mac
For boot volumes, the users must enter their system credentials. For non-boot volumes, the users must enter the password configured during the encryption process.
In case the endpoint users forget their encryption passwords, they need recovery keys to unlock their machines. For details about retrieving the recovery keys, refer to Using Recovery manager for encrypted volumes.
Note
If the encryption module expires, access to recovery keys from GravityZone will no longer be available, and encrypted drives will become inaccessible. We strongly recommend decrypting all drives before the module’s expiration date to avoid data loss.
Excluding partitions
You can create a list of exclusions from encryption for Windows endpoints by adding specific drive letters, partition labels and names, and partition GUIDs. You cannot exclude from encryption the partition where the operating system is installed.
Note
On macOS, Bitdefender supports encryption only for boot and local partitions (not volumes). Therefore, it is not necessary to define exclusions for external hard disks, USB drives, or other such devices.
To create a rule to exclude partitions from encryption:
Select the Exclusions checkbox.
In the Type drop-down menu, select the partition identifying method.
In the Excluded items field, enter the identifiers for each partition to be excluded. Use the following formatting:
For Drive letter, enter the drive letter followed by a colon, such as
D:.For Label / Name, enter the drive label, such as
Work.For GUID, enter the partition GUID enclosed as follows:
\\?\Volume{6a2d53fe-c79a-11e1-b189-806e6f6e6963}\.Tip
To find a volume GUID in Windows, use the
mountvolcommand without any parameters.
Click
 Add to add the exclusion to the list.
Add to add the exclusion to the list.
To edit an exclusion:
Open the inline menu.
Click Edit exclusion.
Make the change.
Click the
 confirmation icon to save the change.
confirmation icon to save the change.Alternately, click the
 cancel icon to close the editing field without changes.
cancel icon to close the editing field without changes.
To delete an exclusion, open the inline menu and click Delete.