Mesh Gateway
Organizations on all email platforms can use Mesh Gateway as long as they can accept email on port 25 and can point the MX records to Mesh.
Mesh Gateway for Google Workspace
Mesh Gateway for all other email platforms
Mesh Gateway for Microsoft 365
This guide outlines how to install Mesh Gateway for organizations on Microsoft 365.
Tip: If this is your first time setting up a customer in Mesh (or even if it’s not), it is worthwhile familiarizing yourself with this checklist ⟶ Before You Start Checklist
Tip
Installation Time: 10-15 minutes
Step 1: Create a Mail Flow for Rule for Mesh in Microsoft 365
In order to allow email filtered by Mesh to be delivered safely without any double filtering from Microsoft, you need to create a mail flow rule in Microsoft 365 for our IP ranges.
This video walks you through the process step by step:
Ensure that the IP ranges applicable to your region are used. You can find this here
View our step by step guide on creating a mail flow rule.
Visit Microsoft’s documentation on this here
Step 2: Populating Users via Azure Sync
In order to allow users to receive quarantine digests and to be able to create their own allow/block rules, users need to be populated in the users table.
Login as Customer and navigate to Users ⟶ Import & Sync ⟶ Azure Sync
Select "O365 Authorize" to permit Mesh to sync the users from Azure.
View more information on user population and role types.
Note: The Azure sync will automatically run every hour. For any mailboxes synced that do not require an account in Mesh, please select and set to “disable”
Step 3: Import Allow & Block Rules (optional)
You can import a list of safe senders or domains using our CSV template.
Step 4: Update Your MX Records
Update your MX records with the values applicable to your service region.
MX records are region specific and there should be no other records present.
If you use MTA-STS, ensure you also update the MX entries there.
Note
Important: Please wait at least 15 minutes after creating your account in Mesh before updating your MX records to ensure there is no interruption to delivery while our system updates.
Step 5: Create A Connector In Microsoft 365
In order to prevent threats from bypassing Mesh filtering and ensuring emails from our MTAs can deliver to your mail environment, you should create a Connector for Mesh in Microsoft 365.
Note
Important:
Only complete this step after you point your MX records to Mesh. We recommend waiting 24 hours to allow for DNS propagation.
If you are moving from another Secure Email Gateway, you will likely have an existing connector in place to reject emails that aren't sent from a specific IP range.
You will need to remove this before changing MX records to prevent clean email filtered by Mesh from being rejected.
This video walks you through the process step by step:
Ensure that the IP ranges applicable to your region are used. You can find this here.
View our step by step guide on creating a connector.
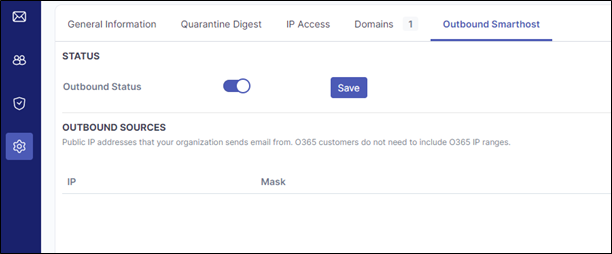
Step 6: Enable Outbound Email Scanning (Optional)
View our step-by-step guide on enabling our outbound email scanning.
Note
If your tenant uses an autoforward in some capacity, please ensure you read the above guide.
 |
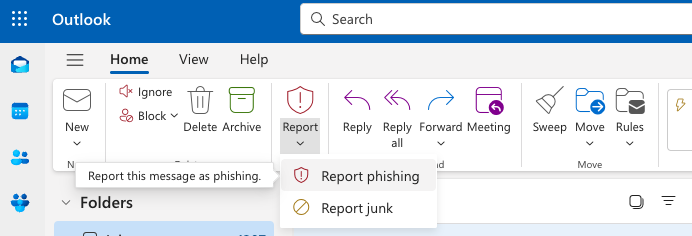
Step 7: Configure Report Junk & Phishing Button (Optional)
The Outlook report button can be utilised to share potential false negatives / false positives with your helpdesk and the Mesh detection team. View our step-by-step guide.
 |
Tip
You’re all set. Your email is now protected by Mesh Gateway.
Mesh Gateway for Exchange
This guide outlines how to install Mesh Gateway for organizations on Exchange.
Tip: If this is your first time setting up a customer in Mesh (or even if it’s not), it is worthwhile familiarizing yourself with this checklist ⟶ Before You Start Checklist
Tip
Installation Time: 10-15 minutes
Step 1: Create a Mail Flow for Rule for Mesh in Exchange
In order to allow email filtered by Mesh to be delivered safely without any double filtering from Microsoft, you need to create a mail flow rule in Exchange for our IP ranges.
This video walks you through the process step by step:
Ensure that the IP ranges applicable to your region are used. You can find this here
View our step by step guide on creating a mail flow rule.
Visit Microsoft’s documentation on this here
Step 2: Populating Users via CSV Import
In order to allow users to receive quarantine digests and to be able to create their own allow/block rules, users need to be populated in the users table.
Login as Customer and navigate to Users ⟶ Import & Sync ⟶ Manual
View more information on user population and role types.
Step 3: Import Allow & Block Rules (optional)
You can import a list of safe senders or domains using our CSV template.
Step 4: Update Your MX Records
Update your MX records with the values applicable to your service region.
MX records are region specific and there should be no other records present.
If you use MTA-STS, ensure you also update the MX entries there.
Note
Important: Please wait at least 15 minutes after creating your account in Mesh before updating your MX records to ensure there is no interruption to delivery while our system updates.
Step 5: Create A Connector in Exchange
In order to prevent threats from bypassing Mesh filtering and ensuring emails from our MTAs can deliver to your mail environment, you should create a Connector for Mesh in Exchange.
Note
Important:
Only complete this step after you point your MX records to Mesh. We recommend waiting 24 hours to allow for DNS propagation.
If you are moving from another Secure Email Gateway, you will likely have an existing connector in place to reject emails that aren't sent from a specific IP range.
You will need to remove this before changing MX records to prevent clean email filtered by Mesh from being rejected.
This video walks you through the process step by step:
Ensure that the IP ranges applicable to your region are used. You can find this here.
View our step by step guide on creating a connector.
Step 6: Enable Outbound Email Scanning (Optional)
View our step-by-step guide on enabling our outbound email scanning.
Note
If your tenant uses an autoforward in some capacity, please ensure you read the above guide.
 |
Step 7: Configure Report Junk & Phishing Button (Optional)
The Outlook report button can be utilised to share potential false negatives / false positives with your helpdesk and the Mesh detection team. View our step-by-step guide.
 |
Tip
You’re all set. Your email is now protected by Mesh Gateway.
Mesh Gateway for Google Workspace
This guide outlines how to install Mesh Gateway for organizations on Google Workspace.
Tip: If this is your first time setting up a customer in Mesh (or even if it’s not), it is worthwhile familiarizing yourself with this checklist ⟶ Before You Start Checklist
Tip
Installation Time: 10-15 minutes
Useful links
Step 1: Create an Inbound Gateway for Mesh in Google Workspace
In order to allow email filtered by Mesh to be delivered safely without any double filtering from Google, you need to create a mail flow rule for our IP ranges.
View our step by step guide on creating an inbound gateway.
Note
Important: If you are moving from another Secure Email Gateway, you will likely have an existing connector in place to reject emails that aren't sent from a specific IP range.
You will need to remove this before changing MX records to prevent clean email filtered by Mesh from being rejected.
Step 2: Configure internal emails to remain within the tenant in Google Workspace
Unlike Microsoft 365 where internally sent emails are not seen by Mesh Gateway, Google routes internal email through the mx record. This means they are subject to filtering by Mesh Gateway and its impersonation detection, which will result in false positives. This can be avoided by configuring internal emails to remain within the Google Workspace tenant.
View our Routing Internal Emails in Google Workspace guide.
Step 3: Populating Users
In order to allow users to receive quarantine digests and to be able to create their own allow/block rules, users need to be populated in the users table.
Users can be populated manually or via our CSV import.
View more information on user population and role types.
Step 4: Import Allow & Block Rules (Optional)
You can import a list of safe senders or domains using our CSV template.
Step 5: Update your MX records
Update your MX records with the values applicable to your service region.
MX records are region specific and there should be no other records present.
If you use MTA-STS, ensure you also update the MX entries there.
Note
Important: Please wait at least 15 minutes after creating your account in Mesh before updating your MX records to ensure there is no interruption to delivery while our system updates.
Step 6: Reject all mail not from gateway IPs
We recommend locking down your mail environment to only accept emails from Google and Mesh. To do this check the box "Reject all mail not from gateway IPs" within the Inbound Gateway section found in this guide: https://docs.emailsecurity.app/help-center/Create-an-Inbound-Gateway-for-Mesh-in-Google-Workspace.869236945.html
Note
Please wait 24 hours before completing this step to allow for DNS propagation.
Step 7: Enable Outbound Email Scanning (Optional)
View our step-by-step guide on enabling our outbound email scanning.
 |
Tip
You’re all set. Your email is now protected by Mesh Gateway.
Create an Inbound Gateway for Mesh in Google Workspace
To ensure email filtered by Mesh is delivered safely without any double filtering from Google, you need to create an inbound Gateway for Mesh in Google Workspace.
It is recommended that you consult Google’s official documentation.
Note
Important:
Only complete this step after you point your MX records to Mesh. We recommend waiting 24 hours to allow for DNS propagation.
If you are moving from another Secure Email Gateway, you will likely have an existing connector in place to reject emails that aren't sent from a specific IP range.
You will need to remove this before changing MX records to prevent clean email filtered by Mesh from being rejected.
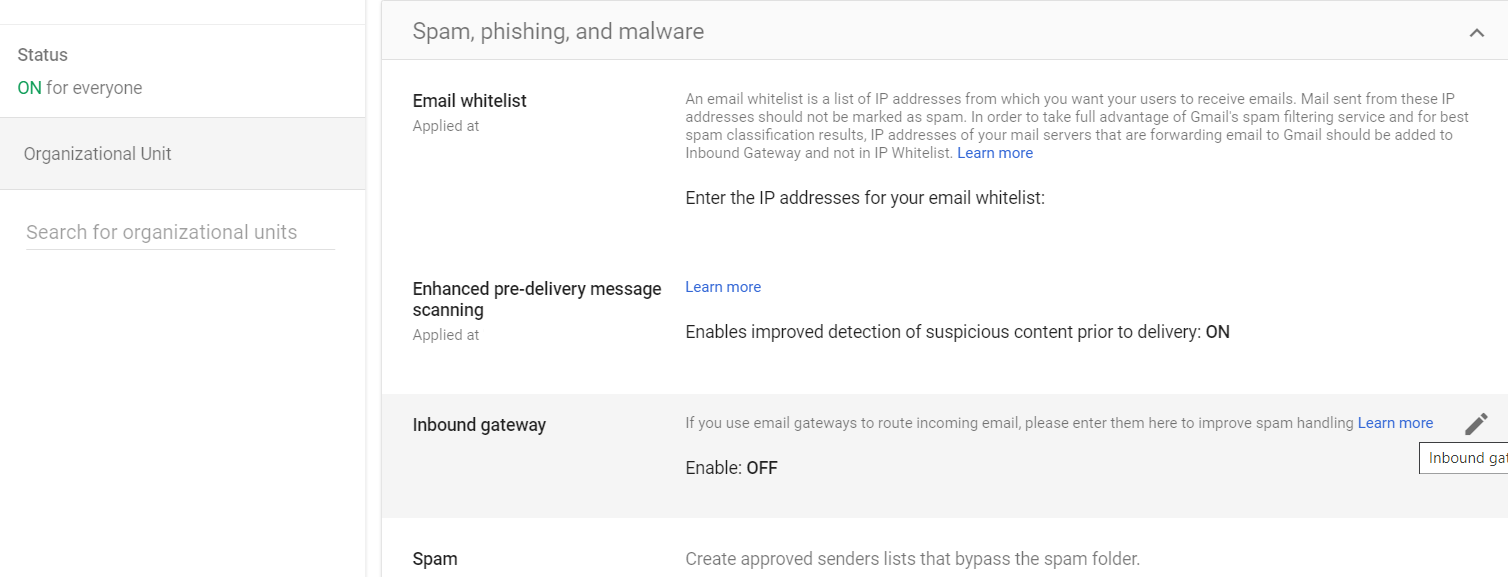
Step 2: Edit Inbound Gateway
Click on edit Inbound Gateway.
 |
Step 3: Add Gateway IPs
You will need to add two sets of IP addresses:
Mesh delivery IP ranges specific to your region.
Google’s sending IP ranges.
List of Google IPs Extracted from _spf.google.com (Google could changes these without notice. It is recommended to double check) 66.249.80.0/20 72.14.192.0/18 74.125.0.0/16 108.177.8.0/21 173.194.0.0/16 209.85.128.0/17 216.58.192.0/19 216.239.32.0/19 2001:4860:4000::/36 2404:6800:4000::/36 2607:f8b0:4000::/36 2800:3f0:4000::/36 2a00:1450:4000::/36 2c0f:fb50:4000::/36 172.217.0.0/19 172.217.32.0/20 172.217.128.0/19 172.217.160.0/20 172.217.192.0/19 172.253.56.0/21 172.253.112.0/20 108.177.96.0/19
Step 4: Select Checkboxes
Click the following checkboxes:
Automatically detect external IP (recommended).
Require TLS for connections from the email gateways listed above.
Note
Important: For now, leave “Reject all mail not from gateway IPs” unchecked. This will be enabled at the very end of our setup guide.
When using the “Reject all mail not from gateway IPs” we recommend to including Google’s sending IP ranges to prevent circumstances where they can reject emails from their own servers.
If you decide to leave “Reject all mail not from gateway IPs” unchecked, senders can bypass the Mesh or Google gateway.
Step 5: Create Regexp
Check the box "Message is considered spam if the following header regexp matches"
Enter a random string into the Regexp text box.
This value does not matter as long as it will not appear in the email headers.
Step 6: Disable Spam Evaluation
Check the box "Disable Gmail spam evaluation on mail from this gateway; only use header value"
The setup should now look like this:
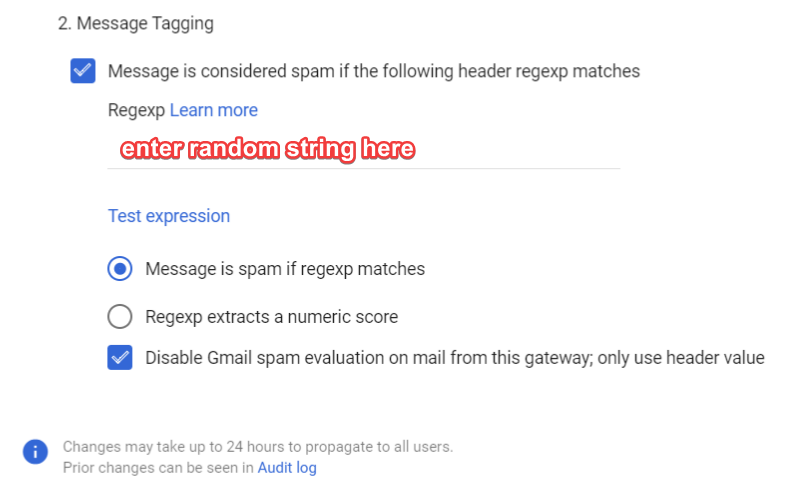 |
Step 7: Continue Mesh Gateway Setup Guide
The next step is to continue Mesh Gateway setup guide which includes details to keep internal emails within Google’s infrastructure.
Tip
You’re all set!
Routing Internal Emails in Google Workspace
Note
Failure to complete this step will mean internally sent emails are very likely to be quarantined as impersonation by Mesh. Internal emails should remain within the tenancy in Google, they should not pass through Mesh Gateway.
Create Mail Route
Go to https://admin.google.com
Go to Apps -> Google Workspace -> Gmail.
Scroll down to "Hosts". Click "Add Route"
Give the new route a name such as "Internal Emails Route".
Under "Specify email server", choose "Single Host", and enter "aspmx.l.google.com". Port 25. (If applicable, you can instead use the
smtp.google.comoption from here: https://support.google.com/a/answer/174125?hl=en).Important: Uncheck "Perform MX lookup".
Ensure the following boxes are checked:
a. Require mail to be transmitted via a secure (TLS) connection (Recommended).
b. Require CA signed certificate (Recommended).
c. Validate certificate hostname (Recommended).
Click Save.
Apply Routing Rule
Go to Apps -> Google Workspace -> Gmail.
Scroll down to the section labelled “Routing”.
Click “Configure” or “Add Another Rule”.
Give the new route a name like "Internal Emails Route Rule".
Select the checkbox "Internal - Sending".
In section 2, select "Modify message" from dropdown. Choose the checkbox "Change Route" and select the host you set up earlier.
Scroll to the bottom and click "Show options".
Ensure the following boxes are checked:
a. Users
b. Groups
Under Section C, select "Only affect specific envelope senders", choose "Pattern Match" from, and enter in your domain/customer domain in the Regexp field in the format "example.com".
Click Save.
Disable SPF/DKIM checks
SPF and DKIM checks are performed by Mesh. Validating a second time after passing through our servers can cause emails to be falsely marked as spam within Gmail.
Go to Apps -> Google Workspace -> Gmail.
Go to "Safety" section.
Select "Spoofing and Authentication".
Uncheck "Protect against any unauthenticated emails" and "Apply future recommended settings automatically".
Click Save.
Continue Mesh Gateway Setup Guide
Please return to this guide to complete the remaining steps:
https://docs.emailsecurity.app/help-center/mesh-gateway-for-google-workspace
Tip
You’re all set!
Mesh Gateway for all other email platforms
This guide outlines how to install Mesh Gateway for organizations NOT using Microsoft 365, Exchange, or Google Workspace.
Tip: If this is your first time setting up a customer in Mesh (or even if it’s not), it is worthwhile familiarizing yourself with this checklist ⟶ Before You Start Checklist
Tip
Installation Time: 10-15 minutes
Step 1: Create an Allow Rule for Mesh
In order to allow email filtered by Mesh to be delivered safely you need to create an allow rule for Mesh on your mail server. Please use the IP range for your specific region.
Note
Important: If you are moving from another Secure Email Gateway, you will likely have an existing connector in place to reject emails that aren't sent from a specific IP range.
You will need to remove this before changing MX records to prevent clean email filtered by Mesh from being rejected.
Step 2: Populating Users via CSV Import
In order to allow users to receive quarantine digests and to be able to create their own allow/block rules, users need to be populated in the users table.
Login as Customer and navigate to Users ⟶ Import & Sync ⟶ Manual
View more information on user population and role types.
Step 3: Import Allow & Block Rules (Optional)
You can import a list of safe senders or domains using our CSV template.
Step 4: Update your MX records
Update your MX records with the values applicable to your service region.
MX records are region specific and there should be no other records present.
If you use MTA-STS, ensure you also update the MX entries there.
Note
Important: Please wait at least 15 minutes after creating your account in Mesh before updating your MX records to ensure there is no interruption to delivery while our system updates.
Step 5: Lockdown Your Server to Only Accept Email Filtered by Mesh
In order to prevent threats from bypassing Mesh filtering and ensuring emails from our MTAs can deliver to your mail server, you should configure it to reject email not from Mesh’s IP range.
Note
We recommend waiting 24 hours before completing this step to allow for DNS propagation.
Step 6: Enable Outbound Email Scanning (Optional)
View our step-by-step guide on enabling our outbound email scanning.
Note
If your tenant uses an autoforward in some capacity, please ensure you read the above guide.
 |
Tip
You’re all set. Your email is now protected by Mesh Gateway.