GravityZone Full Disk Encryption FAQ
This section addresses some of the most frequent questions about the functionality and features of GravityZone Full Disk Encryption.
GravityZone Full Disk Encryption is a solution that helps companies comply with data regulations and prevent the loss of sensitive information in case of lost or stolen devices.
GravityZone Full Disk Encryption provides centralized handling of BitLocker (on Windows), FileVault and the diskutil command-line utility (both on macOS), taking advantage of the native device encryption and ensuring optimal compatibility and performance.
How do I know that an endpoint supports GravityZone Full Disk Encryption?
GravityZone Full Disk Encryption is available for the most Windows endpoints and Macs that can run BitLocker, FileVault and diskutil. In the Windows space, this feature is not accessible for users with "Home" editions of the OS.
For more information, refer to Full Disk Encryption.
Does this feature work only with endpoints that have BitLocker capability/TPM chip?
GravityZone Full Disk Encryption works with both systems with or without TPM. For most systems TPM is optional, except for Windows 7 and Windows Server 2008 R2, where TPM is required. TPM must be version 1.2 or higher.
What kind of disks does GravityZone encrypt?
GravityZone encrypts boot and non-boot volumes, on fixed disks, on desktop computers and laptops. Removable drives are not encrypted.
GravityZone uses:
BitLocker to encrypt boot and non-boot volumes on Windows.
FileVault to encrypt boot volumes on Mac.
diskutil to encrypt non-boot volumes on Mac.
How do I encrypt volumes with GravityZone?
GravityZone leverages the native applications for encryption available on the Windows and macOS platforms.
When applying a GravityZone policy with the Full Disk Encryption module enabled:
On Windows, the security agent manages BitLocker to encrypt or decrypt volumes according to the policy.
On macOS, the security agent manages FileVault to encrypt or decrypt boot volumes and diskutil to encrypt or decrypt non-boot volumes.
Endpoint users can operate BitLocker, FileVault and diskutil on their own as long as the Full Disk Encryption module in the security agent is disabled.
Encryption on Windows
To encrypt volumes on Windows endpoints, you need to apply a policy with the Full Disk Encryption module enabled and the Encrypt option selected. On the endpoint, the encryption flow depends whether the machine has a functioning Trusted Platform Module (TPM) or not.
Endpoints with TPM
When the policy is applied:
The security agent prompts the users to configure a PIN. For details, refer to Encryption.
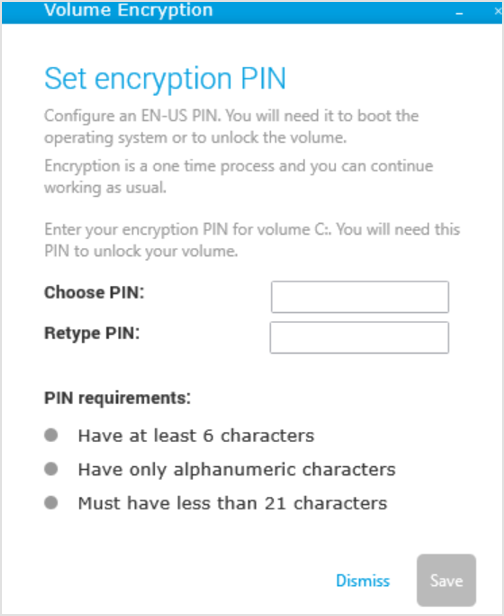
If the TPM does not work or GravityZone does not detect it, the user will be prompted to configure an encryption password. For details, see the section below referring to the encryption process on endpoints without TPM.
After clicking the Save button, the security agent sends a recovery key associated with the encryption PIN to the GravityZone console.
Once the GravityZone console returns a confirmation response to the security agent, the encryption process starts on the boot disk (C:) and continues with the other disks.
If clicking the Dismiss option, the encryption window disappears and reappears after a while, as long the policy is active on the endpoint.
On endpoints with TPM, the encryption process starts without requiring a PIN from users when the GravityZone policy has the option If Trusted Platform Module (TPM) is active, do not ask for pre-boot password enabled. For details, refer to Encryption.
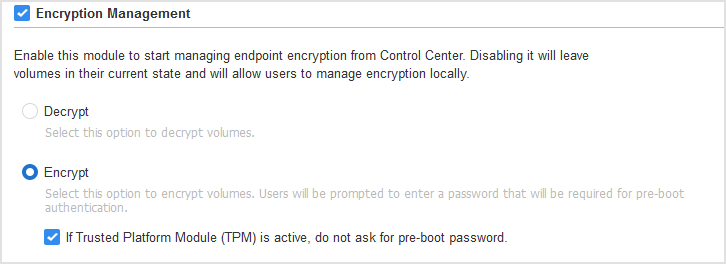
When starting an encrypted machine, the users first have to enter the PIN in the pre-boot environment to unlock the boot volume, then the system credentials. The non-boot volumes are automatically unlocked.
Users do not need to enter any PIN in the pre-boot environment when the option If Trusted Platform Module (TPM) is active, do not ask for pre-boot password is enabled in the GravityZone policy. For details, refer to Encryption.
Note
You can control the PIN complexity requirements and the users’ privileges to change their PIN by enabling the following BitLocker Group Policy (GPO) settings:
Configure minimum PIN length for startup
Configure use of passwords for operating system drives, with Require password complexity
Configure use of passwords on fixed data drives, with Require password complexity
Disallow standard users from changing the PIN or password.
Endpoints without TPM
When the policy is applied:
The security agent prompts the users to configure a password. For details, refer to Encryption.
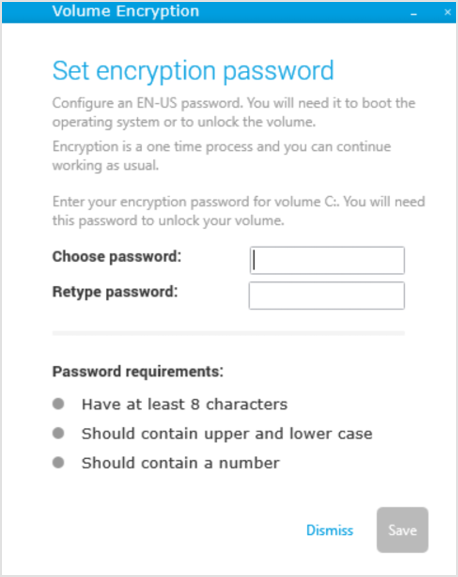
After clicking the Save button, the security agent sends a recovery key associated with the encryption password to the GravityZone console.
Once the GravityZone console returns a confirmation response to the security agent, the encryption process starts on the boot disk (C:) and continues with the other disks.
If clicking the Dismiss option, the encryption window disappears and reappears after a while, as long the policy is active on the endpoint.
When starting an encrypted Windows machine, the users first have to enter the encryption password in the pre-boot environment to unlock the boot volume, then the system credentials. Non-boot volumes are automatically unlocked.
In case the users have forgotten their encryption passwords, they can ask their security administrator for the recovery key to unlock the boot volume.
Decryption on Windows
To decrypt volumes on Windows endpoints, you need to apply a policy with the Full Disk Encryption module enabled and the Decrypt option selected. When the policy is applied, the decryption process starts without prompting the users to enter their encryption password.
If trying to encrypt or decrypt independently with BitLocker while a policy with adverse action is enabled, GravityZone will revert the user’s command after a while.
Encryption on macOS
To encrypt volumes on macOS endpoints, you need to apply a policy with the Full Disk Encryption module enabled and the Encrypt option selected. When the policy is applied:
For the boot volume:
The security agent prompts the users to enter their system credentials to start encryption with FileVault.
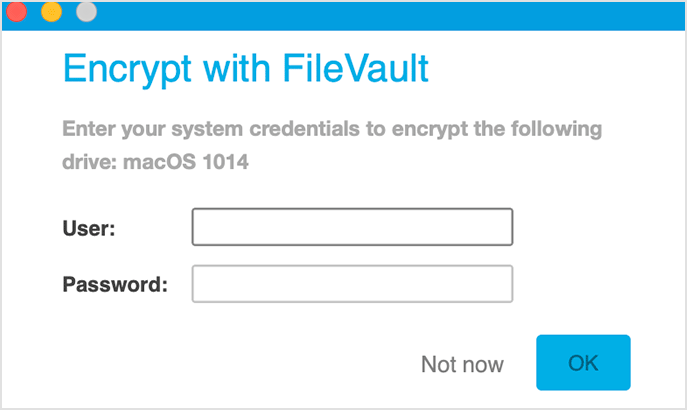
After clicking the OK button, the security agent sends a recovery key to the GravityZone console and the encryption process starts.
If clicking the Not now option, the encryption window will disappear and reappear after a while, as long as the policy is active on the endpoint.
Note
In case of dual-boot systems, the other boot volume will not be encrypted.
For any non-boot volume:
The security agent prompts the users to configure a password to start encryption with diskutil.
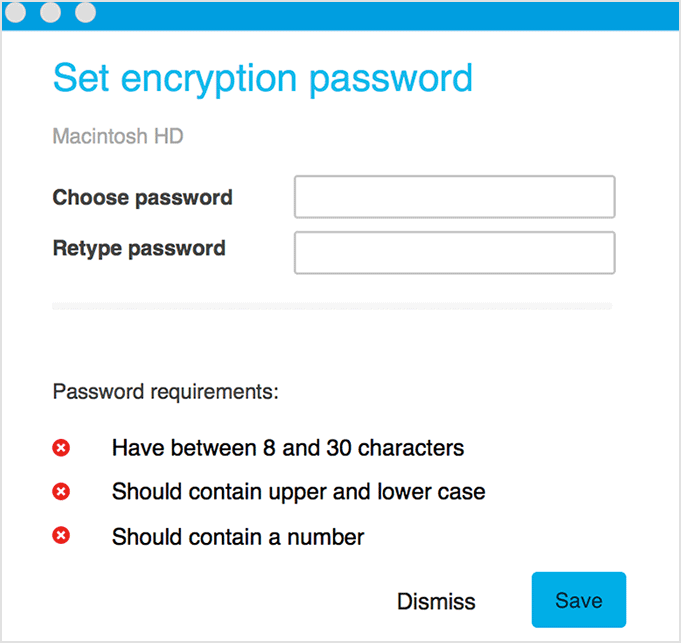
After clicking the Save button, the security agent sends a recovery key to the GravityZone console and the encryption process starts.
If clicking the Dismiss option, the encryption window will disappear and reappear after a while, as long as the policy is active on the endpoint.
Users have to configure a separate password for each non-boot volume connected to the Mac.
When starting encrypted macOS machines, users have to enter their system credentials. Only users having local accounts with administrative privileges can enable encryption. If those Macs have non-boot volumes, the users also have to enter the passwords they have configured to encrypt those volumes.
If users have forgotten their passwords, they can ask their security administrator for the recovery key.
Decryption on macOS
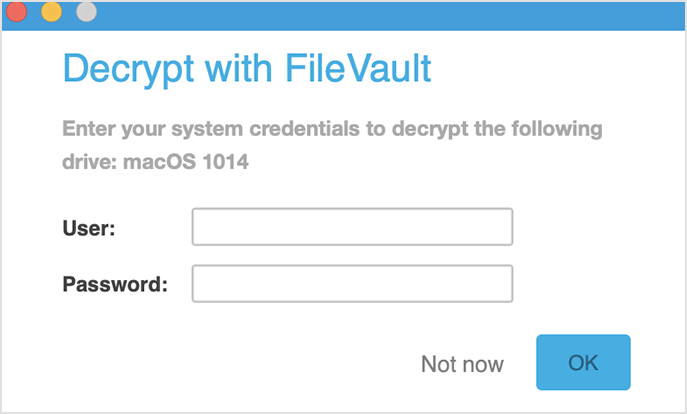
To decrypt volumes on Mac, you need to apply a policy with the Full Disk Encryption module enabled and the Decrypt option selected. When the policy is applied:
For the boot volume, the users have to enter their system credentials.
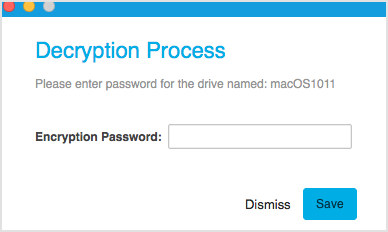
For the non-boot volumes, the users have to enter the disk password they have configured to encrypt those volumes.
Users can change, at any time, the recovery key for the boot volumes encrypted with FileVault in the security agent interface, by providing the system credentials.
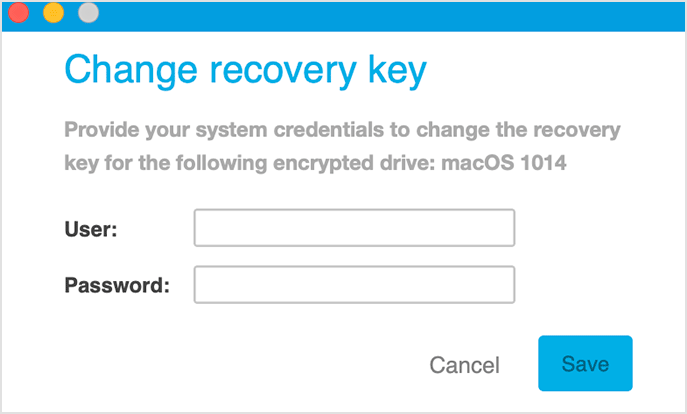
Users can also change the encryption password for the non-boot volumes encrypted with diskutil, by providing the existing encryption password.
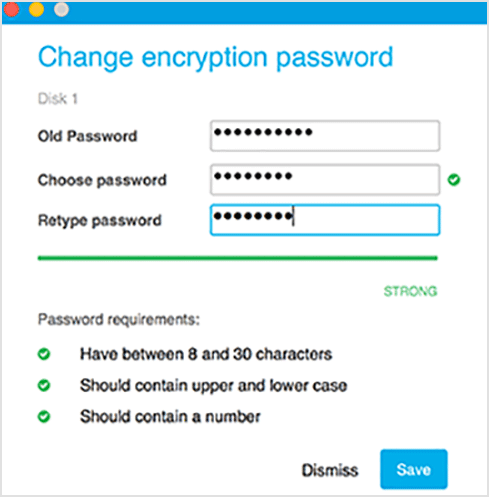
Changing the system password on the endpoint does not affect the recovery key stored in GravityZone.
If trying to encrypt or decrypt independently with FileVault or diskutil while a policy with adverse action is enabled, GravityZone will not interfere with the ongoing process. Once the encryption or decryption completes, GravityZone will check the volume status and it will take an action (encrypt or decrypt) in accordance with the policy.
How do I set the encryption password?
When a security policy with Encrypt is applying on the endpoint, the user must configure a password that starts the encryption process.
As GravityZone manages encryption through BitLocker, FileVault and diskutil, the workflow and the limitations of password configuration are related to these tools.
On Windows
The following paragraphs explain what you should know about configuring the encryption password on Windows machines, following BitLocker specifications.
The encryption password format for machines with TPM is different from the password format for machines without TPM:
On machines with TPM (such as newer laptops), the user must enter a personal identification number (PIN) as encryption password. The PIN must contain:
At least 6 characters.
Only alphanumeric characters.
Less than 21 characters.
The user does not need to enter a password when the GravityZone policy has the option If Trusted Platform Module (TPM) is active, do not ask for pre-boot password enabled. For details, refer to this Encryption.
On machines without TPM (such as virtual machines), the encryption password must contain:
At least 8 characters.
Capital and small letters.
One or more digits.
The password with this format is also required when the TPM is not functional or not detected by GravityZone.
The encryption password is used to boot the operating system. In this context, BIOS or UEFI (Unified Extensible Firmware Interface) may only support an EN-US keyboard layout, while the BIOS-based systems are limited to 7-bit ASCII input. Therefore, the password entry may fail when using non-English characters or keys that differ in position from the EN-US layout, such as QWERTZ or AZERTY keyboards.
The users are recommended to set their keyboards to EN-US during the password configuration to avoid possible issues in the pre-boot environment.
These characters are not supported by system firmware:
Roman characters on keyboards with a non en-US layout, such as "Z" and "Y" on German keyboards and "Q" and "A" on French keyboards.
Characters that are not available in 7-bit ASCII, such as characters with umlauts ("Ä"), grave accents ("È") and tildes ("Ñ").
Symbols that are not available in 7-bit ASCII, such as square superscript, fractions, copyright (©) and international currencies symbols ($, £, € etc.).
For more information on setting the encryption password on Windows, refer to this Microsoft article.
On macOS
On Mac, the user is prompted with two types of windows to start the encryption process, because GravityZone uses FileVault to encrypt the boot drive and diskutil to encrypt the non-boot drives.
To encrypt the boot drive with FileVault, the user must enter his system credentials.
To encrypt a non-boot drive with diskutil, the user must configure a password that must contain:
Between 8 and 30 characters.
Capital and small letters.
One or more digits.
When setting the password and encryption is starting, make sure you don’t have any USB drive plugged into your computer. If that drive is missing at the moment you restart the computer, the operating system fails to boot.
Does GravityZone support pre-boot authentication?
GravityZone Full Disk Encryption supports pre-boot authentication. When configuring the encryption password, make sure you met the conditions at the previous step to avoid password entry failure in the pre-boot environment, if you use a non EN-US keyboard layout.
Is GravityZone Full Disk Encryption FIPS compliant?
No, GravityZone Full Disk Encryption is not compliant with the Federal Information Processing Standard (FIPS).
Does GravityZone provide reporting of full disk encryption already performed by BitLocker, FileVault or diskutil?
If a volume has already been encrypted with BitLocker, FileVault or diskutil, when enabling encryption on the endpoint through GravityZone, the security agent will generate a new recovery key for that volume and will send it to Control Center.
In other cases, the volumes must be decrypted before applying a GravityZone encryption policy.
Does GravityZone provide the ability of recovering password automatically to the end user?
No, but Bitdefender has plans to support it in the future.
What should customers do if they already encrypted data using other solutions?
They first must decrypt data using their current solution, then they can safely use GravityZone Full Disk Encryption.
What is the average time to perform Full Disk Encryption? Can end users work during that time?
The average time for encryption depends on multiple factors: disk type and size, the CPU speed, the number of processes and applications running at that time. However, this does not impact the end user because the encryption occurs in the background, while he can work as usual on his computer.
Does GravityZone Full Disk Encryption require prerequisites like installing and enabling BitLocker manually?
Full Disk Encryption requires BitLocker to be installed on the computer and, in most cases, it is. Only Windows Server systems don’t have BitLocker by default, so the administrator must add it.
Is it a single sign-on to Windows or do you need two passwords: one for Full Disk Encryption and another one for Windows?
On Windows, the users need first to enter the encryption password in the pre-boot environment, then their user account password to log in to OS.
Is Full Disk Encryption light-weight and fast enough to be imperceptible by the user and not hard on computer’s resources?
Encryption occurs in the background and the user can continue his work as usual. There are chances that he would not even notice that the process is going on because GravityZone only manages native BitLocker, FileVault and diskutil, without supplementary burden on the system. However, if you encrypt very large drives it is better to set this process when you are not using them.
How many different users can access an encrypted computer?
The access on a computer is not limited by the number of users. On multi-user computers, the user that is logged in when the encryption policy is applied is the one who sets the encryption password.
Does Full Disk Encryption come as an add-on to the existing GravityZone license?
Yes. Full Disk Encryption is available as an add-on for all GravityZone cloud and on-premises editions and out-of-the-box for MSP. Find out here the availability of Full Disk Encryption across the GravityZone editions.
How do I get a trial?
To get a free trial, create an account here. If you already have a GravityZone Cloud account, use another email address to set up a trial account.
Can I change the boot password for encryption from GravityZone Control Center?
The encryption password can only be changed by the user from the Bitdefender security agent GUI.
Can I disable Full Disk Encryption from Control Center?
Yes, you can disable the encryption management from Control Center to allow local control of BitLocker (on Windows) and FileVault and diskutil (on Mac). Also, you can decrypt data by applying a GravityZone policy.
Do you have to enter the boot encryption password when the computer comes out of hibernation or sleep?
Yes, that is the standard behavior on Windows machines: the encryption password, then the user's account password. On macOS, you have to enter your user's account password.
Can I encrypt without being asked for a password when the computer is starting?
Yes, but only on Windows systems with a Trusted Platform Module (TPM) chip. In GravityZone Control Center, go to the Policies > Encryption and select the check box If Trusted Platform Module (TPM) is active, do not ask for pre-boot password.
This way, the endpoints will be encrypted without a password and the users will not need to enter it every time the computers start, before their account password.
This option is supported only on machines with TPM and Unified Extensible Firmware Interface (UEFI).
A user will still have to provide a password, whether the check box is selected or not, when:
The machine does not have TPM.
The TPM is not functional or not detected by GravityZone.
The machine is not UEFI-based.
The machine is a Mac.
For other details, refer to Encryption.
What happens to encryption keys when an endpoint is migrated between GravityZone Cloud instances?
When an endpoint is migrated between GravityZone Cloud instances its encryption keys are automatically regenerated. As a result, any previously stored recovery keys become invalid for the new instance. This impacts recovery key availability, so it's important to plan accordingly before performing such a migration.