Making SELinux compatible with On-Access scanning in BEST for Linux
Security-Enhanced Linux (SELinux) is a kernel feature that provides a mechanism for supporting access control security policies.
When the SELinux policies are set to Enforcing, this mechanism interferes with the Antimalware module in specific situations:
when using BEST for Linux v7 with CentOS 6 and where DazukoFS is present.
when using
auditdto support EDR.when deploying Bitdefender Security for Container on virtual machines.
To overcome this issue, you need to change the SELinux policies to Permissive or Disabled (recommended). This is how you make SELinux compatible with On-Access Scanning:
Check the status of SELinux on the endpoint, by running the following command:
sudo sestatus
If the SELinux Current mode is set to Enforcing, you need to change it to Permissive or Disabled (recommended).
To change the SELinux policy status:
Edit the configuration file with the text editor of your choice (such as vim or nano).
On Red Hat based systems (RHEL, CentOS, Fedora, SuSE), the configuration file is /etc/sysconfig/selinux.
On Ubuntu / Debian based systems, the configuration file is /etc/selinux/config.
Note
If you cannot find the SELinux configuration file on your system, please consult the documentation of your Linux distribution.
Example:
# nano /etc/sysconfig/selinux
Edit the line starting with SELINUX= as follows:
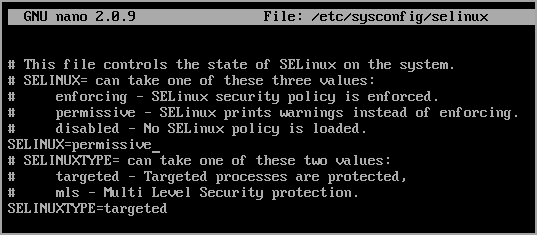
For Permissive mode:
SELINUX=permissive
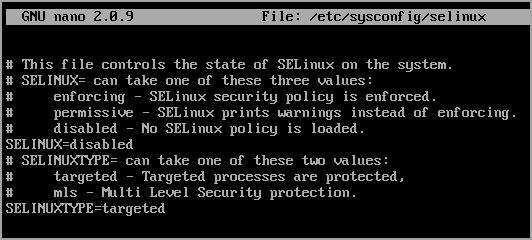
For Disabled mode:
SELINUX=disabled
Save the file.
If you use nano to edit the configuration, to save the file and exit, use the following sequence:
Ctrl+O,Enter,Ctrl+X.Reboot the endpoint.
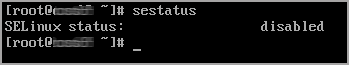
After reboot, check the SELinux status by running the command again:
sudo sestatus
The output should be permissive or disabled.
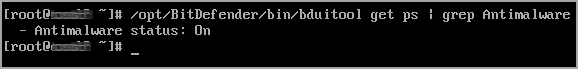
Check the Antimalware module status with the following command:
# /opt/bitdefender-security-tools/bin/bduitool get ps | grep Antimalware
The Antimalware module status should be On (active).
If the Antimalware module is Off, although SELinux is properly configured, refer to On-access scanning in Bitdefender Endpoint Security Tools for Linux for troubleshooting Bitdefender Endpoint Security Tools for Linux.