Container Security
The Container Protection feature offers protection for Linux container workloads and the host, by extending and augmenting the security layers of the host operating system. It uses the Endpoint Detection and Response (EDR), Advanced Anti-Exploit, and Antimalware features. You can independently enable or disable the Antimalware module for each Linux container. You can enable or disable the other modules only simultaneously from the container host.
Important
This feature can be deployed through two components:
A BEST agent that has been installed on the Linux host endpoint with the Container Protection module included.
A Security Container deployed under the Linux host endpoint. A Security Container is a dedicated Docker container running an Ubuntu 20.04 base image and the official Debian package of BEST for Linux. It runs as a privilege container on a Kubernetes node or a container host.
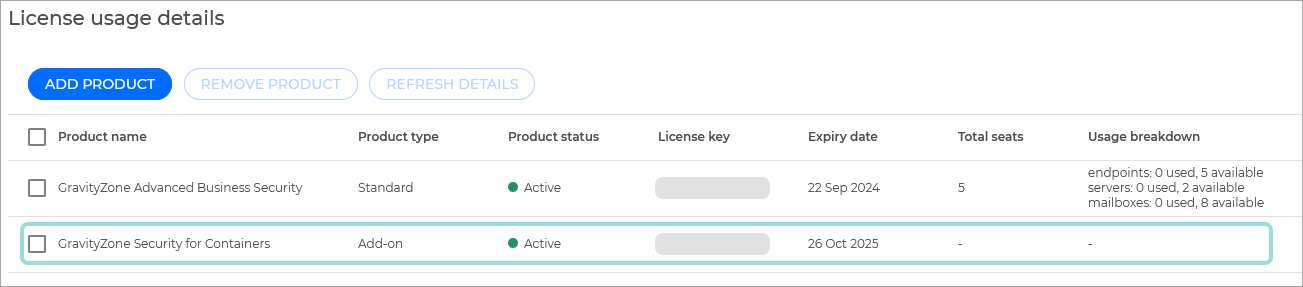
The feature is available as an add-on, which, when added to your company, is listed next to your main license:
Start the trial
To start the trial, follow the steps below:
Log in to GravityZone with your administrator account.
Click the
 button on the upper right side of the console to access the Products hub page.
button on the upper right side of the console to access the Products hub page. Select Learn more under the Security for Containers section.
Select Start free trial.
The add-on will be added to your company's list of licenses as a separate product. You will be redirected the home page where you will see the new sections in GravityZone available to you.
Note
To remove the Security Containers key, you can use the Stop Trial button. Learn more
Configure and install the new feature
Important
We recommend trying out the new feature on a limited number of Linux container hosts.
You can test out the functionality by having a BEST agent installed or deploying a Security Container on a container host. We have included both procedures in this section:
Important
The Network Attack Defense feature is not compatible with endpoints where Container Protection is installed.
Log in to GravityZone Control Center.
Go to the Policies page from the left side menu.
You can either:
Under Antimalware > On-Access, make sure the On-access scanning option is enabled and configure the feature.
Under Antimalware > Advanced Anti-Exploit, make sure the Advanced Anti-Exploit option is enabled and configure the feature.
Under Incident Sensor, enable the module.
Save your policy.
If you created a new policy, apply it to the endpoints you want to test it on.
If you edited an existing policy, the changes will take place on all endpoints it was applied to.
This will allow you to enable the newly available features on all selected endpoints.
Note
Different policies can be applied on different containers. Those policies may be different than the one that is applied on the endpoint (which we will refer to as the container host).
Log in to GravityZone Control Center.
Go to the Network page from the left side menu and select the endpoints you wish to deploy the module on.
Click the Tasks button and select Reconfigure client.
Under Modules select Add and enable Container Protection, Advanced Anti-Exploit and EDR.
Note
For more information on using the Reconfigure client task refer to Reconfigure agent.
Click Save.
Once the feature is installed, all the containers managed by the host will be visible in GravityZone. You can view them from the Network page, under the Containers folder. For more information, refer to Viewing endpoint details.
Follow the steps in this article to deploy the Security Container. Make sure that no BEST agent is installed on the Linux host endpoint.
Once the feature is installed, all the containers managed by the host will be visible in GravityZone. You can view them from the Network page, under the Containers folder. For more information, refer to Viewing endpoint details.
Decide what endpoints you wish to test the feature on.
Deploy Docker on the endpoints.
Test out the new feature
Create a new container and make sure it is detected and appears in GravityZone inventory
For the purpose of this guide, we have chosen creating a Docker image for Ubuntu. You can use any supported Linux distribution when creating containers, as long as the image can be retrieved from the Docker registry. The distribution chosen for the container may differ from the container host’s distribution.
Create a new container:
root@ubuntu23-x64-tcor:~# docker run -dt ubuntu:latest bash 529ca9f8970c879eb8e1192077afb059a0a14dde291478863056417ef12a16dc
Check that the container is running:
root@ubuntu23-x64-tcor:~# docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 529ca9f8970c ubuntu:latest "bash" 32 seconds ago Up 17 seconds xenodochial_hermann
In GravityZone go to the Network page from the left side menu and check if the new container is displayed and has no issues. For more information, refer to Viewing endpoint details.
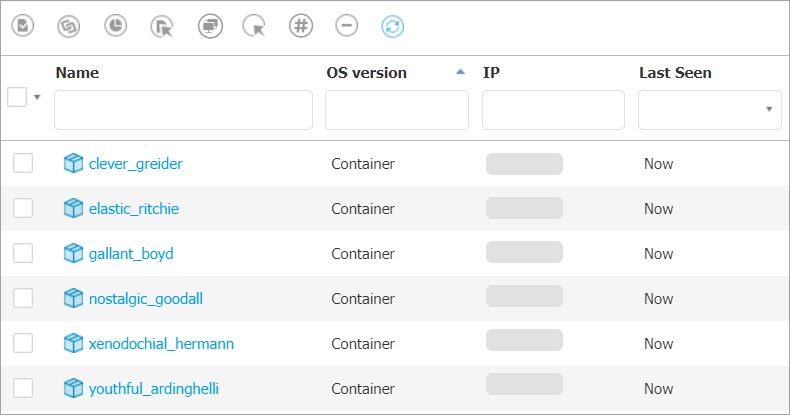
Check that the container is displayed on the page.
Test out On-Access protection
Log in to GravityZone with an account that has Manage Networks rights.
Go to the Policies page from the left side menu and open the previously created policy.
Go to the Antimalware > OnAccess and click on the Settings button on the upper right side of the On-access Scanning section.
Select the Advanced tab.
Make sure the On-Access Scanning for Linux setting is enabled and add the
/testpath in the box below.Click the Add button.
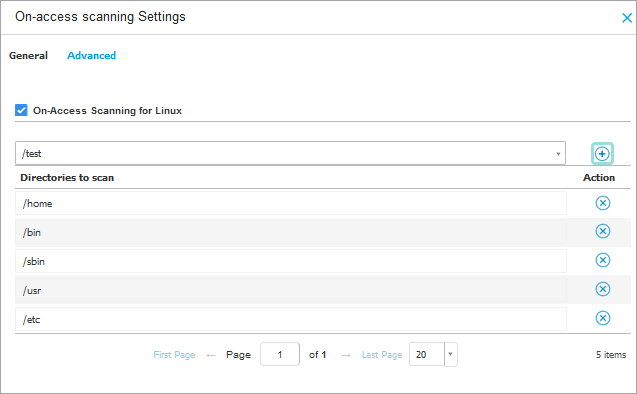
Go to the General tab and under the Scan Actions section, set the Default action for infected files setting to Delete.
Click Save.
Apply the policy on the previously created container. For more information refer to Assigning policies.
From the endpoint, open a shell in the previously created container:
root@ubuntu23-x64-tcor:~# docker exec -it 529c bash root@529ca9f8970c:/#
Create a test path:
mkdir /test
Write an Antimalware test file inside a protected path:
root@529ca9f8970c:/# echo 'X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*' > /test/test1.txt
The Antimalware On-Access protection feature will automatically detect the EICAR file and move it to quarantine.
Check reports for Antimalware activity
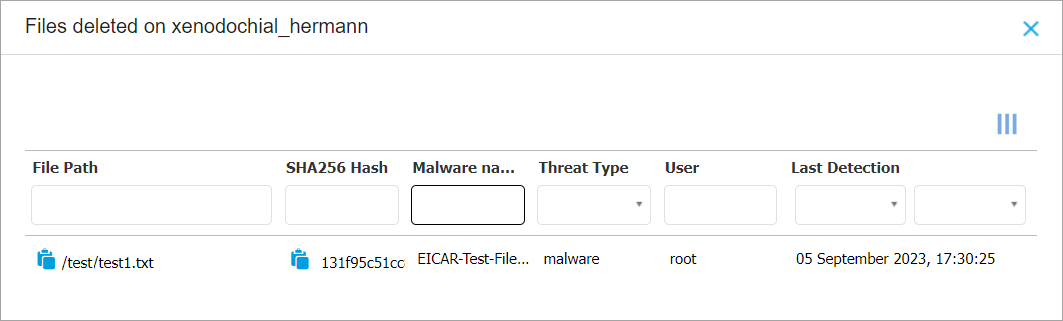
Check GravityZone reports for information regarding the deleted file:
Go to the Network page from the left side menu in GravityZone.
Click on the Reports button generate a Malware Status report.
Go to the Reports page from the left side menu and find the request.
Check that the report contains the previously deleted file:
Important
The file was deleted because the taken action for infected files from the policy was set to Delete.
Depending on the action selected in the policy, the file will be marked differently:
Take no action - Ignored
Deny - Unresolved
Move to Quarantine - Quarantined
Check the Incidents Sensor for an event corresponding to the detection of the EICAR file
Check that the Incidents Sensor works for files inside the container:
Log in to GravityZone Control Center.
Go to the Incidents page from the left side menu.
Select the Detected Threats tab.
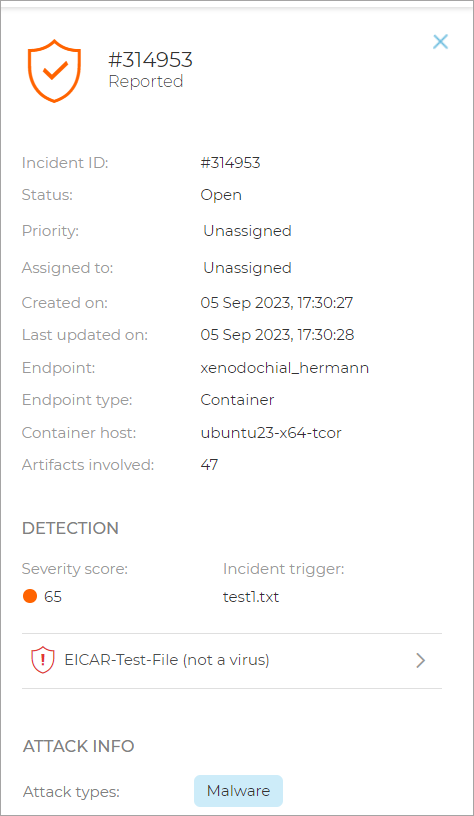
Locate an incident that mentions the hostname where the EICAR was generated:
Check that multiple containers can be created and protected
Create multiple containers (e.g. 5 more containers), from the endpoint:
root@ubuntu23-x64-tcor:~# for i in {1..5}; do docker run -dt ubuntu:latest bash; done 5b37d80408498340664f4c0b74043512a6af423734553c1b3802313b069e8e00 3356db2a2dbe2faea5589b520f81c4da71abc2561699a2ff6ab3f0a3e5bf9cc1 fb146eeab3c6db4cdccc281aa42e671118b7267e18e416baa2c21b84593ead0c cbfea815f32300564fcf1698df20ad4b820a545a2f38945540259dbc5fb5862b 028c3597646dba1b7adca79767a4674552cfd843d2012b05f81dd67ebf083eabIn GravityZone go to the Network page from the left side menu and check if the new containers are displayed and have no issues. For more information, refer to Viewing endpoint details.
Stop the trial
To stop the trial, follow the steps below:
Log in to GravityZone with your administrator account.
Click the
 button on the upper right side of the console to access the Products hub page.
button on the upper right side of the console to access the Products hub page. Select Learn more under the Security for Containers section.
Select Stop trial.
The product will be removed from your company and all additional features will be disabled.