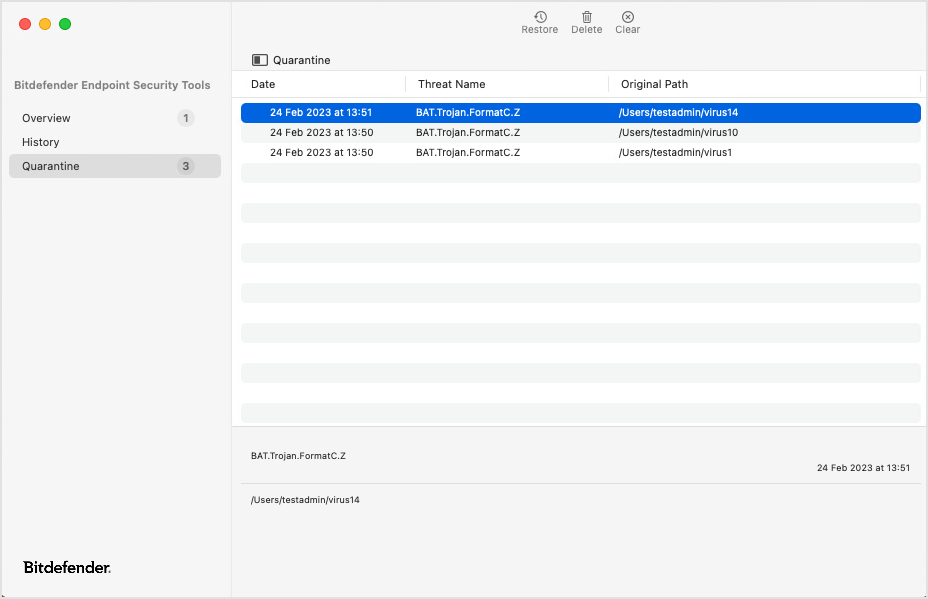
Application main window
In the Bitdefender Endpoint Security Tools main window you can view important information, such as your Mac security status, the list of security events and the list of quarantined items. If needed, you can resize to window to fit more data in.
In the upper left-corner of the window, click the  Expand icon next to the page name to access the following pages:
Expand icon next to the page name to access the following pages:
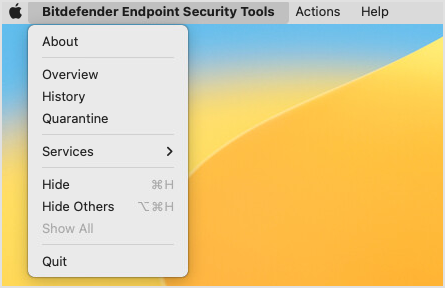
You can also access the Overview, History and Quarantine pages from the Bitdefender Endpoint Security Tools menu.
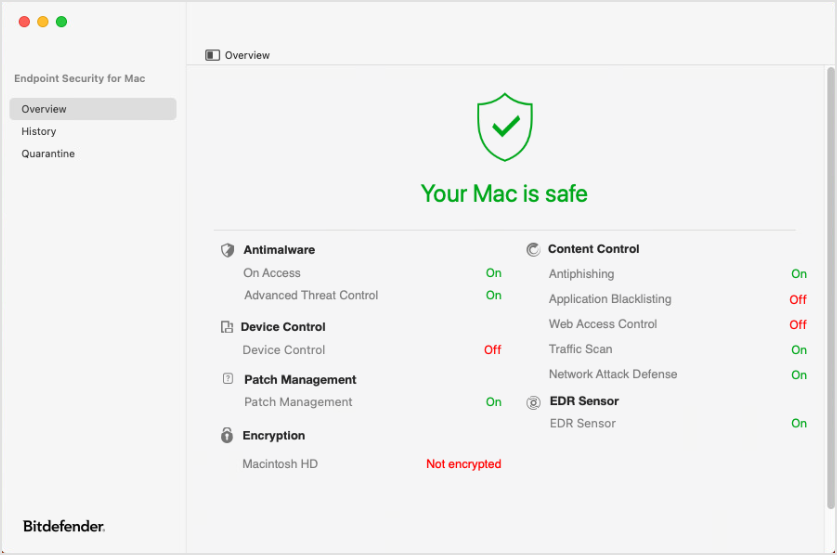
Overview
The Overview page contains two areas where you can monitor the status and the modules installed with Bitdefender Endpoint Security Tools.
Status
The status area at the top of the Overview page informs you about the system's security status using explicit messages and suggestive colors:
Green - if Bitdefender Endpoint Security Tools has no warnings.
Red - if an issue has been detected.
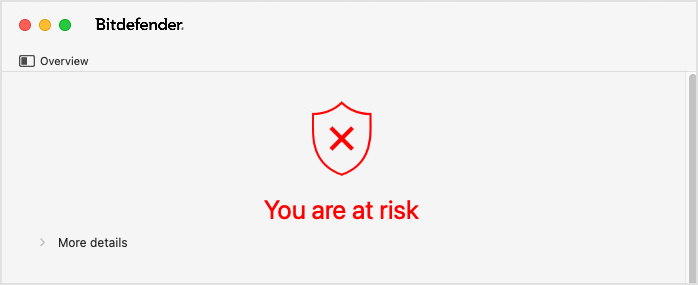
Click the More details option to view the issue and to take the appropriate action. For example, when an update is required, you can click the Update now button that appears in this area.
If the case, a number next to the Overview tab name indicates how many issues have been detected on your computer.
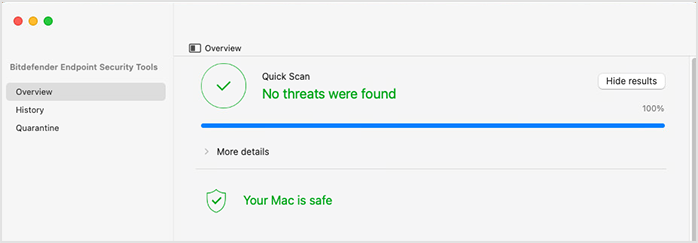
When performing actions such as scans and updates, their progress and status is displayed above the status area. In case of multiple actions, they are displayed in reverse chronological order, with the latest action at the top. For details on performing scans and updates, refer to Protecting against malware.
Modules
In the lower half of the main window, you can view the protection modules available with Bitdefender Endpoint Security Tools installed on Mac. Some of these modules may be disabled, depending on the security policy applied to the computer.
Modules include:
Antimalware. This module is the foundation of your security. Bitdefender Endpoint Security Tools protects you in real time and on demand against all sorts of malware, such as viruses, trojans, spyware, adware, etc.
On-access scanning. This component prevents new malware threats from entering the system by scanning local and network files when they are accessed (opened, moved, copied or executed), boot sectors and potentially unwanted applications (PUA).
Advanced Threat Control. This component is a proactive detection technology which uses advanced heuristic methods to detect new potential threats in real time.
Content Control. This module protects you while on the Internet against phishing attacks, fraud attempts, private data leaks, and inappropriate web content. It also includes a comprehensive set of user controls that help the network administrator enforce computer and Internet use policies.
Antiphishing. This component automatically blocks known phishing web pages to prevent users from inadvertently disclosing private or confidential information to online fraudsters.
Application Blacklisting. This component prevents access to unauthorized applications in your company. The administrator is responsible for creating rules for the allowed applications in the organization.
Web Access Control. This component protects you from accessing dangerous websites based on administrator-defined rules.
Traffic Scan. This component prevents malware from being downloaded to the endpoint by scanning and web traffic in real time.
Network Attack Defense. This component provides protection against network attacks designed to gain access on endpoints through specific techniques such as: brute-force attacks, network exploits and password stealers.
Content Control is available for Chrome, Firefox, Safari, and Edge (Traffic Scan).
Device Control. This module prevents sensitive data leakage and malware infections via external devices attached to endpoints, by applying blocking rules via policy to a vast range of device types. The administrator is responsible for managing permissions for the following types of devices:
Bluetooth devices
CDROM devices
Imaging devices
Modems
Windows Portable
Printers
Network adapters
Wireless network adapters
External storage
Patch Management. This module keeps the operating system and software applications up to date. This module includes several features, such as on-demand or scheduled patch scanning, automatic or manual patching, and reporting on missing patches.
When needed, the Patch Management module prompts endpoint users to restart running applications to complete updates. Users can postpone patches for up to 24 hours. After this interval, the installation task expires with "timeout" status and is reported as such to the GravityZone console.
Note
The module applies operating system patches only for minor versions, for example from version 13.5 (Ventura) to 13.6 (Ventura), but not from 13.9 (Ventura) to 14.0 (Sonoma).
EDR Sensor. This module collects, handles, and reports endpoint and application behavior data. Some of the information is processed locally, while a more complex set of data is reported to a backend component of GravityZone.
Encryption. This module allows you to provide full disk encryption by managing FileVault and diskutil tools on Mac.
In the main window you can view the encryption status for each disk (Encrypted, Encryption in progress, Decryption in progress, Not encrypted, Locked or Paused).
Risk Management. This module helps administrators identify and remediate a large number of network and operating system risks via scan tasks configured in the GravityZone policy.
Firewall. This module supports only the Network Connection functionality in the Blocklist feature.
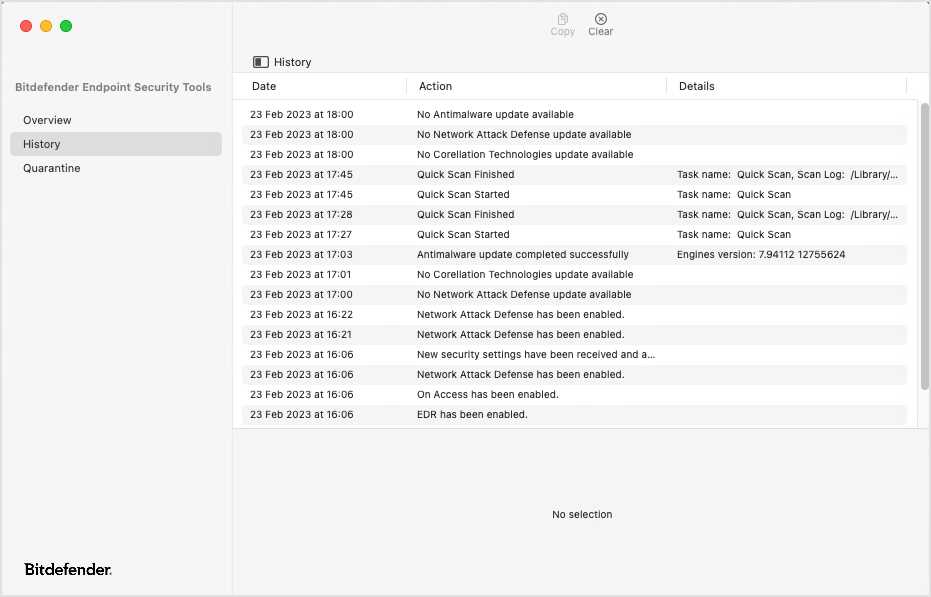
History
The History page lists all events occurred on your computer related to Bitdefender Endpoint Security Tools, such as enabling or disabling modules, updates, and scans. The list displays the most recent 3,000 events.
To sort events by date, action, and details, click the corresponding column headers. Click each event to view related information at the bottom of the page. Use the Copy and Clear buttons at the top of the page to copy events and to empty the entire list. For details, refer to Protecting against malware.
Quarantine
The Quarantine page lists all the infected or suspicious files that have been placed in isolation.
Click the column headers to sort files by date, name, and original path. Click each item to also view the related information at the bottom of the page. Use the Restore, Delete and Clear button at the top of the page to restore files, to delete selections of files, and to empty the entire list.
A number next to the Quarantine tab name indicates how many files are in the list.
For details on quarantine, refer to Protecting against malware.