General
In the Firewall > General section of the policy, you can enable or disable the Bitdefender Firewall and configure the general settings.
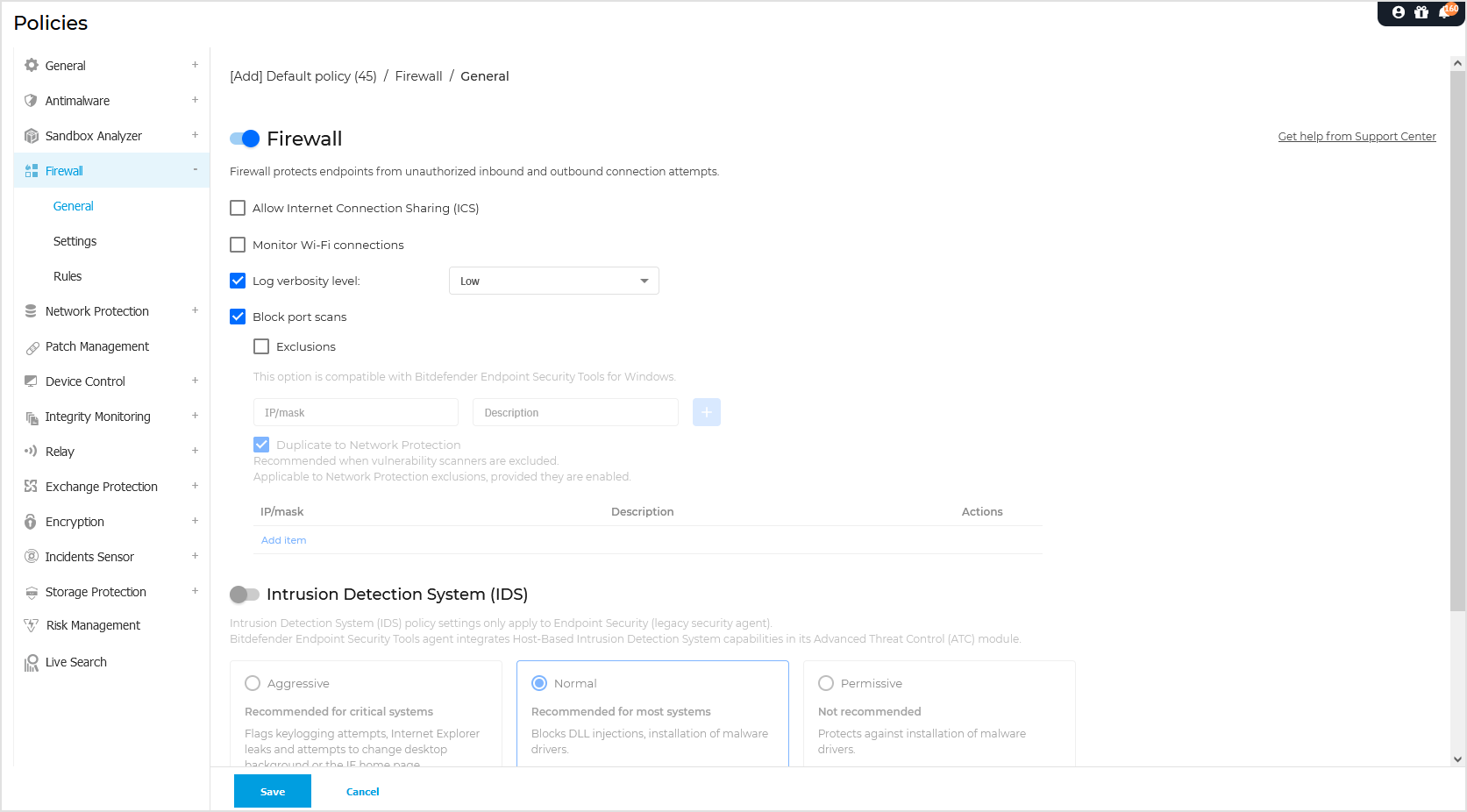
Firewall
Click the toggle to enable Firewall.
Warning
If you disable firewall protection, computers will be vulnerable to network and Internet attacks.
Allow Internet Connection Sharing (ICS)
Select this option to set the firewall to allow Internet Connection Sharing traffic.
When this feature is enabled, it permits the endpoint to utilize Internet Connection Sharing (ICS) or IP forwarding capabilities between its local adapters, thereby facilitating the sharing of network connections or routing of traffic between different network interfaces on the same device.
Note
This option does not automatically enable Internet Connection Sharing on the user's system.
Monitor Wi-Fi connections
Bitdefender security agent can inform users connected to a Wi-Fi network when a new computer joins the network.
To display such notifications on the user's screen, select this option.
Log verbosity level
Bitdefender security agent maintains a log of events regarding the Firewall module usage (enabling/disabling firewall, traffic blocking, modifying settings) or generated by the activities detected by this module (scanning ports, blocking connection attempts or traffic according to the rules). Choose an option from the Log verbosity level to specify how much information the log should include.
Note
The Log verbosity level feature is no longer supported on versions newer than BEST 6.x.
Port Scans Exclusions
Port scans are frequently used by hackers to find out which ports are open on a computer. They might then break into the computer if they find a less secure or vulnerable port.
Enable the Exclusions checkbox to specify IP addresses for such scenarios where you are using scanners to report and assess endpoint vulnerabilities. Port scan exclusions are compatible with Bitdefender Endpoint Security Tools for Windows.
To add a port scan exclusion rule:
Enter the IP address in the corresponding field. Example: 10.1.1.1
You can also use the IP/CIDR format. Example: 10.1.1.0/24
Provide a short description to easily identify the exclusion rule.
If needed and to save time, enable Duplicate to Network Protection to automatically create the same exclusion in the Network Protection section.
Click the
 button cu finish the process.
button cu finish the process.A new entry appears in the grid below.
If Duplicate to Network Protection is enabled, the same exclusion rule appears in the Network Protection section. However, to apply it there, make sure the Exclusions section in Network Protection is also enabled.
Note
The Duplicate to Network Protection option does not provide two-way synchronization between the Firewall and Network Protection modules. For example, if you delete a port scan exclusion in Firewall, its duplicate in Network Protection remains intact. The same is true if you delete an exclusion in Network Protection.
Bitdefender blocks a detected attacker IP address for a few minutes. The timer restarts with each detection made, even during this period. However, port scan exclusions get activated immediately, regardless an IP address was already blocked or they are applied during the blocking period.
Enabling Block port scans can lead to a decrease in download speed within the network. It is important to conduct thorough testing before implementing it on a large scale.
Intrusion Detection System (IDS)
Intrusion Detection System monitors the system for suspicious activities (for example, unauthorized attempts to alter the Bitdefender files, DLL injections, keylogging attempts etc.).
Note
Intrusion Detection System (IDS) policy settings only apply to Endpoint Security (legacy security agent). Bitdefender Endpoint Security Tools agent integrates Host-Based Intrusion Detection System capabilities in its Advanced Threat Control (ATC) module.
To configure Intrusion Detection System:
Click the toggle to enable Intrusion Detection System.
Click the security level that best suits your needs (Aggressive, Normal or Permissive).
Use the description on the right side of the scale to guide your choice.
To prevent a legitimate application from being detected by Intrusion Detection System, add an ATC/IDS process exclusion rule for that application in the Antimalware > Settings > In-policy exclusions section.
Note
The Intrusion Detection System is no longer supported on versions older than Bitdefender Endpoint Security Tools 6.x.
Important
Intrusion Detection System is only available for Endpoint Security clients.