Vulnerabilities
The Vulnerabilities page displays all vulnerable applications discovered on resources in your environment during scanning. It provides detailed information of their severity level, number of known CVEs per application, and number of affected resources.
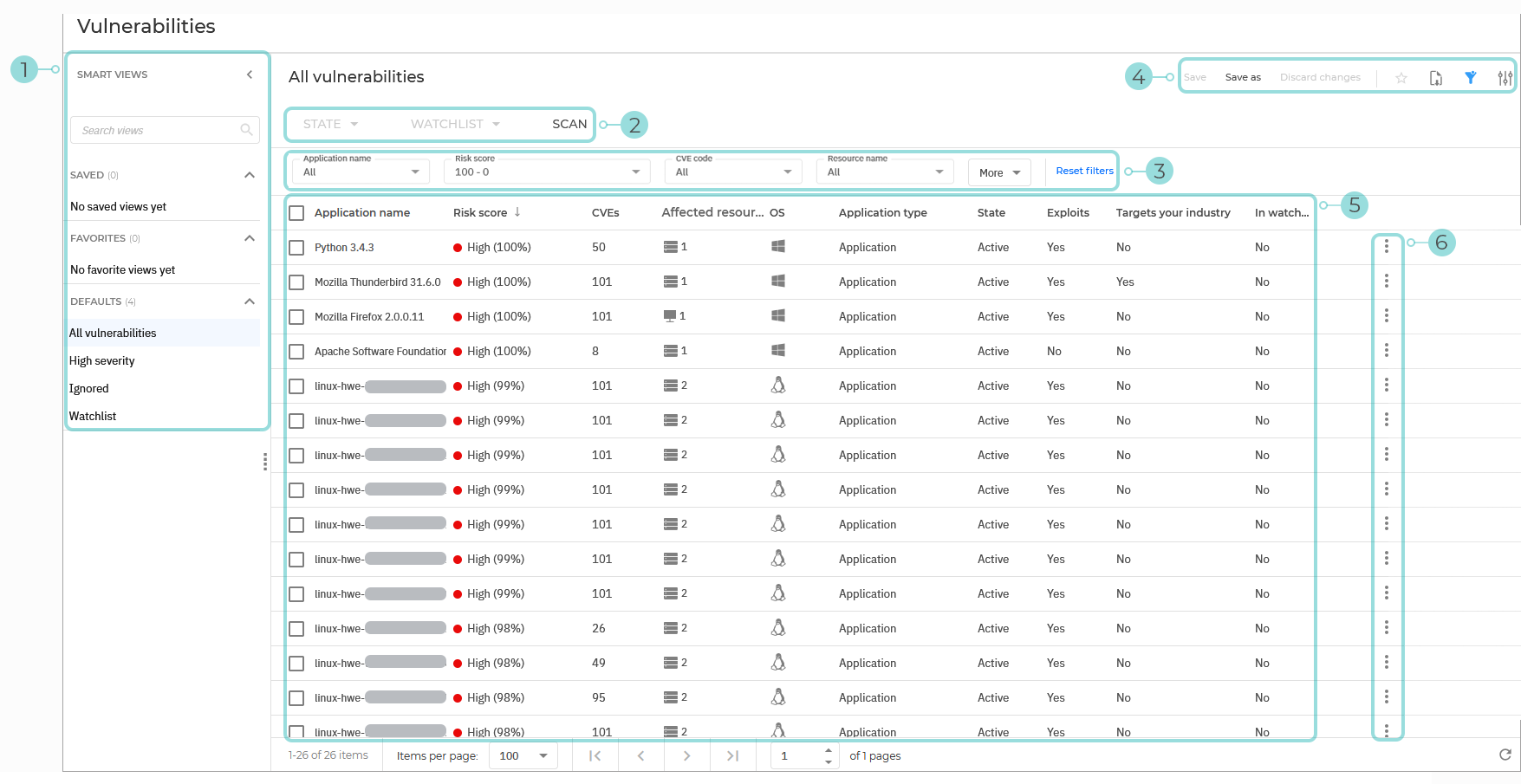
The Smart views panel. This feature allows you to customize, save, and switch between different loadouts of the Vulnerabilities page.
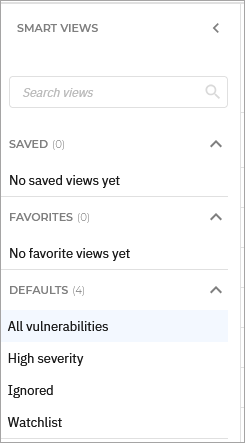
The panel has the following sections:
Search views - Use this search field to filter out the views displayed in the sections below, by name.
Saved - This section displays a list of all your saved views that have not been marked as favorites.
Favorites - All views marked as favorites are displayed under this section.
Defaults - This section displays the views that are available by default:
All vulnerabilities
High risk score
Ignored
Watchlist
For any view in the Saved or Favorites category, you can click the vertical ellipses
to Rename or Delete the view.
The Vulnerability actions. This section contains the buttons to all the available actions you can take on the risks displayed on the page:
State - Change the state of the selected risks. The following options are available:
Ignore applications
Restore ignored applications
Watchlist - Add or remove the selected risks from your watchlist. The following options are available:
Add to watchlist
Remove from watchlist
Scan - Perform a scan to check for new risks or updates on known risks.
The Filters section. You can use these options to customize the risks that are displayed in the grid.
The following filters are currently available:
Filtering option
Details
Application name
Use the searchable drop-down menu to filter the list of vulnerable applications by name. Select the applications you want to display and click Apply.
Only the selected applications are displayed.
Risk score
Select a risk score range between 1 and 100.
Only vulnerable applications with a risk score between these values are displayed.
CVE code
Use the searchable drop-down menu to filter the list vulnerable apps based on the CVE codes assigned to their associated vulnerabilities. Select the CVEs you want and click Apply.
Only applications affected by the selected CVEs are displayed.
Resource name
Use the searchable drop-down menu to filter the list by the name of the resource containing vulnerable apps.. Select the resources you want and click Apply.
Only vulnerable applications that have been detected on the selected resources are displayed.
Platform
Use the searchable drop-down menu to filter the list of vulnerable apps by the platform on which they were detected. Select the operating systems you want and click Apply. Possible platforms:
Unknown
Windows
Linux
macOS
Only vulnerable applications that are present on the selected operating systems are displayed.
Application type
Select the type of applications you want to display. Possible options:
OS
Application
Service
Only applications of the type you select are displayed.
State
This column allows you to filter the list of vulnerable apps by their state, Active or Ignored.
Use the searchable drop-down menu to filter the list of resources by state. Select the states you want and click Apply. Possible states:
Active
Ignored
Only Vulnerabilities with the states you selected are displayed.
Exploits
Use this filter to display applications with vulnerabilities that have existing exploits, no exploits, or both.
Targets your industry
Use this filter to display applications with vulnerabilities that are actively exploited in your industry, not exploited, or both.
Affected resource
Use the searchable drop-down menu to filter the list of vulnerable apps by the type of the resource that these affect. Select the resources you want and click Apply.
The following options are available:
Workstation
Server
Container image
Container
Not affected
Only vulnerable applications affecting the selected resource types are displayed.
In watchlist
Use this filter to display vulnerable applications based on them currently being included in a watchlist.
Detection source
Use this filter to display vulnerabilities based on the source of detection. The following options are available:
Endpoint scanner
Network scanner
The View options menu. This section provides you with multiple functions for working with views:
Save - Save changes you make to a saved view.
Save as - Save a modified view under a different name.
Discard changes - Revert the saved view to its original state.
 Add to favorites - Add the view to the Favorites category.
Add to favorites - Add the view to the Favorites category. Export view - Download the information in a
Export view - Download the information in a .csvfile, which can contain up to 1500 rows. When exporting the information, you are prompted with a choice between two export types, as follows:Overview - Contains company-wide information on vulnerable applications. The downloaded
.csvfile contains the following columns:Application name
Risk score
CVEs
Affected resources
Platform
Application type
State
Exploits
Targets your industry
Vulnerabilities
Detection source
Breakdown by resource - Contains information on vulnerabilities identified for each resource. The export contains a separate row for each resource and its respective vulnerability. The downloaded
.csvfile contains the following columns:Application name
Resource name
Resource type
First seen on (UTC)
Last scanned (UTC)
Risk score
Exploits
State
CVEs 1 ... CVEs N (there can be multiple CVE columns depending on the number of identified CVEs)
Resource info
 Show or hide filters - Hide or display the filters menu.
Show or hide filters - Hide or display the filters menu. Open settings - Display the Settings panel. You can use this panel to customize what columns are displayed in the view and enable or disable the Compact view.
Open settings - Display the Settings panel. You can use this panel to customize what columns are displayed in the view and enable or disable the Compact view.
The Vulnerabilities grid. The grid displays all detected vulnerable applications in your company, based on your last scan.
The information available for each application displayed under the following columns:
Application name - The name of the application affected by vulnerabilities.
Risk score - The risk score of the vulnerable application. Hovering over the score displays a breakdown of how it was calculated.
CVEs - The number of CVEs that that were detected in the scanned application
Affected resources - The number of resources where the vulnerable application is found on.
Platform - The type of operating system where the vulnerable application was detected.
Application type - The type of the application.
State - The state of the application.
Exploits - Indicates if there are any existing exploits for any of the vulnerabilities detected on the application.
Targets your industry - Indicates if any of the vulnerabilities detected for the application is actively exploited in your industry.
In watchlist - Indicates if the application is currently in the watchlist.
Note
More details regarding the information in each column are available in the Filters section.
Actions button - The
Actions button at the right of each application row, enables you to take the necessary actions:
Ignore application
Restore ignored application
Add to watchlist
Remove from watchlist
View additional information
Selecting an entry opens a side panel with additional details about a specific finding. Depending on where you click, a different panel is available.
Main side panel
The main side panel opens when clicking anywhere on a vulnerability row, except the checkbox and the Affected resources value.
The panel displays specific information that varies based on the type of risk and the related data available.
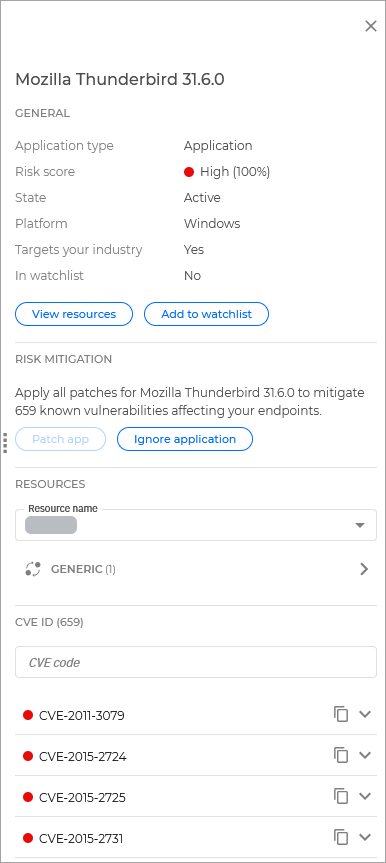
General
This section contains general information regarding the risk:
Application type - The type of the vulnerable application.
Risk score - The risk score of the vulnerable application.
State - The state of the vulnerable application.
Platform - The type of operating system that is affected by the vulnerable application.
Targets your industry - Indicates if any of the vulnerabilities detected for the selected application targets your industry.
In watchlist - Indicates if the vulnerable application is currently in the watchlist.
Additionally, the following actions are available:
View resources - This link redirects you to the Devices page, where you can view all the resources affected by this vulnerable application.
Add to watchlist - Add the vulnerable application to your watchlist.
Risk mitigation
This section provides information on the steps required to fix the risk.
Additionally, the following options are available:
Patch app - This option automatically updates the app to the latest available version that fixes the vulnerability.
Ignore application - Ignore the selected vulnerable application.
Resources
This section provides you with a list of resources where this risk has been detected.
Selecting any of the resources displays a list of associated vulnerabilities.
CVE ID
This section lists all CVEs related to this application.
Click the title of the CVE to display a description and the following links:
View CVE database - Opens a link in a new browser tab to the official page of the CVE.
View resources - Open the Resources page in a new tab, searching for all the resources where the CVE applies.
Affected resources panel
Clicking the Affected resources value of a vulnerability opens a side panel that lists all resources affected by the risk.
In this panel, clicking the More options button next to any resource will provide you with the available actions you can take further:
View resource - This option opens the Resources page in a new tab, where filters will be automatically configured to display only the selected resource.
View incidents - This option opens the Incidents page in a new tab, where filters will be automatically configured to display all incidents where this resource was involved.