PHASR
PHASR (Proactive Hardening and Attack Surface Reduction) analyzes user and system behavior to reduce an organization’s internal attack surface. Its learning phase lasts a minimum of 30 days and can extend up to 60 days depending on the rule, but recommendations may also be generated instantly if sufficient EDR historical data is available. Based on observed behavior per user-device pair, PHASR delivers targeted hardening recommendations to mitigate risks such as Living off the Land Binaries, Crypto miners, Piracy tools, Tampering tools, and Remote admin utilities based on observed behavior per user-device pair.
Note
Although PHASR uses the EDR historical data to reduce the learning period, it is not guaranteed that data for the past 30–60 days will be available, even if that period has already passed. The cache has a fixed size, and in some cases, data from fewer days may completely fill the available cache space
Components
For the PHASR feature to operate on an endpoint, the following prerequisites need to be met:
GravityZoneControl Center
Bitdefender Endpoint Security Tools installed on Windows endpoints
EDR module installed and enabled
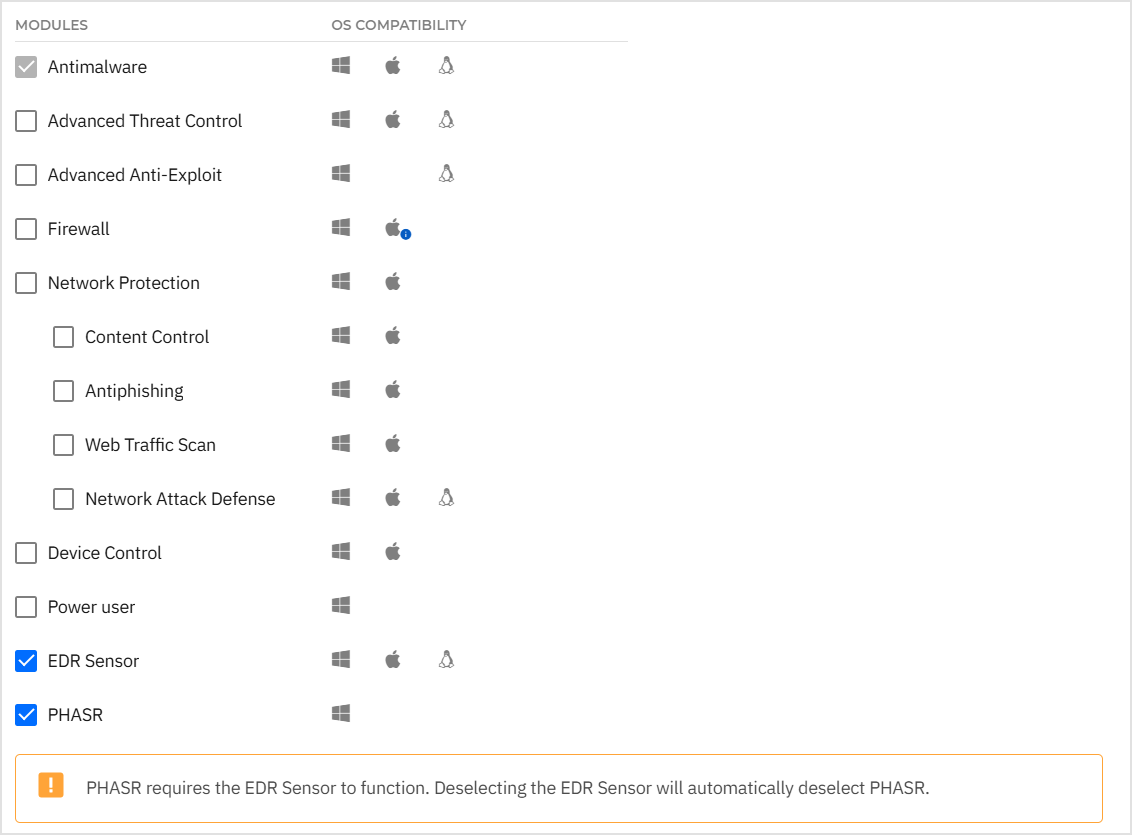
The following features are enabled in the policy: EDR and Risk Management
Feature compatibility
PHASR can be deployed only on Windows 10 and later versions.
Install and configure PHASR
There are three possible scenarios for installing this feature on your endpoints:
An endpoint does not have the BEST agent installed. In this case, use the Create an installation package procedure.
An endpoint has the BEST agent installed, but PHASR is not included in the modules list. In this case, use the Add PHASR using a Reconfigure agent task procedure.
An endpoint has the BEST agent installed, and the PHASR module is included. In this case, go directly to the Configure and enable PHASR section.
Configure and enable PHASR
Policies are used to enable and configure features both on endpoints and in terms of general functionality.
GravityZone comes with a default set of policy settings, that are custom tailored to meet the most common customer needs. These policies are applied, by default, to endpoints, after the BEST agent is installed. You cannot modify or delete the default GravityZone policy.
You can use these default policy settings and leave the configuration of the policy for a later date, or customize the feature using the steps below:
Log in to GravityZone Control Center.
Go to the Policies page from the left side menu.
Note
PHASR settings applied through assignment rules may override or remove existing device-level restrictions because the endpoint's control mode can switch between Autopilot and Direct Control. When this mode changes, device-level configurations may no longer apply and can be replaced automatically. Review your setup to prevent unintended overrides.
You can either:
Under Incidents Sensor, enable and configure the feature.
Important
The Incidents Sensor must be enabled for PHASR to function correctly. Disabling the Incidents Sensor will prevent PHASR from accessing historical EDR data required for risk analysis. To maintain PHASR functionality, ensure Incidents Sensor is active.
Under Risk Management, enable and configure the feature.
While on the same page, make sure the PHASR toggle is enabled, and enable each activity type you would like to monitor.
There are 3 available settings for each activity type:
Off - PHASR will not gather any related data, and the associated widget will not display any data in the PHASR Dashboard.
Autopilot - PHASR will gather the data of the selected type, based on which recommendations will be created and automatically applied.
Note
When Autopilot is selected, all PHASR recommendations are applied automatically by the Bitdefender Autopilot technology integrated with BEST. As a result, no individual recommendations will appear in the Recommendations grid, as Autopilot handles enforcement without requiring user intervention. You can review the restrictions applied to behavioral profiles by Autopilot, by opening the Restricted Behavioral Profiles panel from the PHASR monitored rules.
Direct control - PHASR will gather the data of the selected type, based on which recommendations will be created and presented in the console. The actions recommended will only be taken if manually approved.
Warning
When switching from Autopilot to Direct control mode, all rule restrictions enforced by Autopilot are reset. Changing the setting for a specific PHASR category to Off will disable restrictions, but will not remove them. They will still be available when the setting is changed again to the previous setting before turning it off.
Save your policy.
If you created a new policy, apply it on the endpoints where the feature is deployed:
Go to the Network page from the left side menu.
Select the endpoints you want to apply the policy to.
In the Actions menu, select Assign Policy.
Select the policy you want to apply.
Click Finish.
Note
For more information, refer to this kb article.
If you have edited an existing policy, make sure it is applied to all endpoints where the feature is deployed.
This will ensure that the feature is enabled and configured to best suit your company's needs.
You can check if the PHASR module has been enabled on your endpoints in the Bitdefender Endpoint Security Tools interface.
Managing PHASR recommendations
Recommendations in PHASR are security actions suggested based on observed user and device behavior. They indicate whether access to certain tool categories should be restricted or allowed, helping reduce attack surface while adapting dynamically if user behavior changes.
After PHASR is activated and the module is installed on endpoints, the learning phase begins. This phase lasts a minimum of 30 days and can extend up to 60 days, depending on rule severity. During this period, PHASR builds behavioral profiles by analyzing user and device activity, and gradually starts generating recommendations. When no usage is detected for certain tools, PHASR generates Restrict access recommendations to limit the attack surface.
Important
Behavioral profiles are unique pairs that are being created by combining user and device.
Examples of Behavioral profiles:
John Doe - Desktop
John Doe - Laptop
Kelly Doe - Laptop 1
Kelly Doe - Laptop 2
After the initial learning phase is completed and recommendations are generated, PHASR continues learning in the background, continually adapting to changes in user behavior.
Note
PHASR has the capability to leverage historical EDR data to reduce the duration of the learning phase, depending on the volume of the historical data at its disposal, meaning that the learning phase can be reduced to several days or get recommendations immediately.
When PHASR detects that user behavior has changed for a user which currently has access to certain assets, it will generate a Restrict access recommendation. Once this recommendation is generated you can review the behavioral profiles for which it was generated and allow the recommendation to be applied.
When PHASR blocks a tool, endpoint users can request access directly from the BEST interface, whether the restriction was applied automatically (Autopilot) or manually (Direct Control).
To view the generated recommendations and reduce the attack surface by applying them, go to the PHASR recommendations page.
Managing monitored rules
Monitored rules are mechanisms used by PHASR to identify possible attack vectors and allows the user to reduce the attack surface exposure. Each rule can produce multiple recommendations.
To view the rules that form the basis of recommendations, or to manually apply or remove restrictions, go to the PHASR monitored rules page.
Test out PHASR
To test out PHASR follow these steps:
In the GravityZone console go to the PHASR monitored rules.
Select a process that is available in one of the targeted activity type by PHASR, e.g.
teamviewer.exe.Click the process name under the Rule name column. The rule details side panel is displayed.
Select Edit access.
In the Edit access window, under the Behavioral profiles section, select the device for which you wish to restrict access.
Select Edit access to apply your changes.
On the selected device try to the access the earlier restricted process, e.g. teamviewer.exe.
When PHASR blocks a process on a specific endpoint, the restriction is visible in the Bitdefender Endpoint Security Tools interface. This information appears only if the process actually attempts to run or access resources, and it may take several seconds or even minutes for the change to synchronize.