Joining an endpoint to Active Directory
With Active Directory, each user is set up as a unique object in a central database, and only one set of credentials is used for that user. A separate object is also made for each computer system. With the same set of credentials, every user can automatically get into every workstation. Any changes to an account are made only once at the central database. Using groups and organizational units, access to different resources can be set up and kept up to date.
This section provides guidance on how to join Linux and macOS systems to Active Directory.
Joining Linux endpoints:
Note
For Linux endpoints, make sure to first check the prerequisites page before starting the Active Directory joining process.
If you encounter any issues refer to the Troubleshooting section for further details.
Linux
Prerequisites for joining Linux systems to Active Directory
To join a Linux computer to an Active Directory (AD) domain, there are a few prerequisites that must be met.
The following section details the necessary prerequisites.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
The date and time must be the same as the one in Active Directory.
Make sure the Computer is in sync with the Active Directory. Many authenticating errors appear due to time differences.
The VM must use the Active Directory server as DNS.
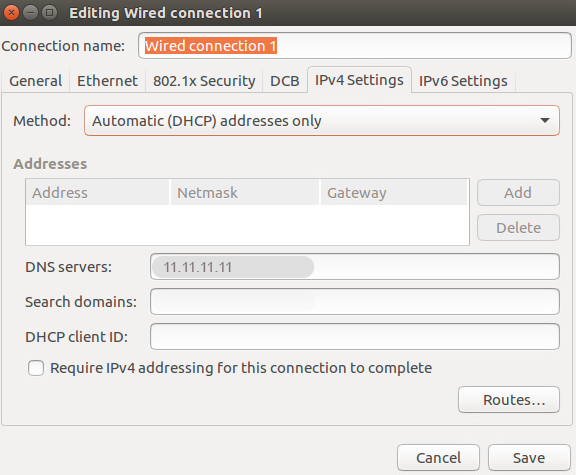
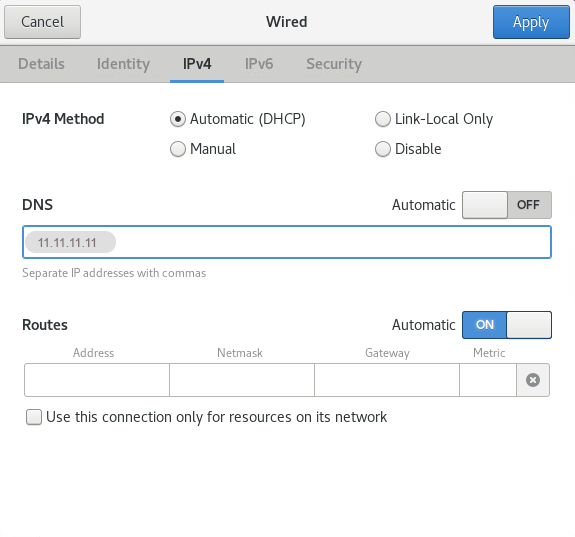
You can change the DNS settings from Applications > Network > Options > IPv4 Settings.
Method: Automatic (DHCP) address only
Automatic: OFF
DNS servers: 11.11.11.11
DNS: 11.11.11.11
Note
Alternatively you can add the following lines to
/etc/resolv.conf:search example.local nameserver 11.11.11.11
Make sure the ports used by Active Directory & Kerberos are open through the network and firewalls. You can find the necessary ports in the below table:
Port
Direction
Destination
Description
22, 445 (SSH & SMB)
OUTGOING
Any
Detects computers in the local network
135 (RPC)
INCOMING
Any
Deployment through Relay Agent
137, 138, 139 (NetBIOS)
INCOMING
Any
Deployment through Relay Agent
53 (DNS)
OUTGOING
DNS Server
Internal use for DNS queries
88 (Kerberos)
OUTGOING
Active Directory Domain Controller
Active Directory integration for Linux computers
389, 636 (LDAP & LDAPS)
OUTGOING
Active Directory Domain Controller
Active Directory integration
Make sure that the OS hostname is unique and has maximum 15 characters.
Change the hostname by running the following command:
# hostnamectl set-hostname <NAME>
Delete the old name from
/etc/hostnameand replace with the new one.Note
On CentOS 6 you need to replace the old HOSTNAME value with the new one:
# vi /etc/sysconfig/network NETWORKING=yes HOSTNAME=<NAME>
Reboot the computer
Note
The endpoint's hostname must not contain the FQDN part.
Disable Selinux.
Change the value of SELINUX variable in configuration file:
/etc/selinux/configto disable it.SELINUX=disabled
Modify
/etc/nsswitch.conffile.Change the search order in
hostsdatabase by addingdnsafterfiles:hosts: files dns mdns4_minimal [NOTFOUND=return]
Joining a Linux endpoint to Active Directory using PBIS
To join a Linux endpoint to an Active Directory (AD) domain using PBIS you need to follow the steps described below and also comply with the General Prerequisites.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Important
Some OSs (Fedora31, CentOS8) require to have the libsnsl package installed.
How to Install PBIS-Open offline
Download the latest
.shfile from here and execute the following commands:For Ubuntu, Debian.
For x64
# wget https://github.com/BeyondTrust/pbis-open/releases/download/9.1.0/pbis-open-9.1.0.551.linux.x86_64.deb.sh # chmod +x pbis-open-9.1.0.551.linux.x86_64.deb.sh # sudo ./pbis-open-9.1.0.551.linux.x86_64.deb.sh # apt-get install ssh # sudo apt-get remove avahi-daemon
For x86
# wget https://github.com/BeyondTrust/pbis-open/releases/download/9.1.0/pbis-open-9.1.0.551.linux.x86.deb.sh # chmod +x pbis-open-9.1.0.551.linux.x86.deb.sh # sudo ./pbis-open-9.1.0.551.linux.x86.deb.sh # apt-get install ssh # sudo apt-get remove avahi-daemon
For CentOS, Fedora, OracleLinux7, RHEL, SUSE.
For x64
# wget https://github.com/BeyondTrust/pbis-open/releases/download/9.1.0/pbis-open-9.1.0.551.linux.x86_64.rpm.sh # chmod +x pbis-open-9.1.0.551.linux.x86_64.rpm.sh # sudo ./pbis-open-9.1.0.551.linux.x86_64.rpm.sh
For x86
# wget https://github.com/BeyondTrust/pbis-open/releases/download/9.1.0/pbis-open-9.1.0.551.linux.x86.rpm.sh # chmod +x pbis-open-9.1.0.551.linux.x86.rpm.sh # sudo ./pbis-open-9.1.0.551.linux.x86.rpm.sh
Join the Active Directory domain.
# cd /opt/pbis/bin/ # sudo domainjoin-cli join example.local administrator
Note
Verify the output of
./pbis-open*.shand check for possible errors.Check domain connectivity.
# sudo domainjoin-cli query
Joining a Linux endpoint to Active Directory using SSSD
This section covers instructions for the following operating systems:
Joining a Linux endpoint to Active Directory using SSSD for CentOS6
To join a Linux endpoint to an Active Directory (AD) domain using SSSD you need to follow the steps described below and also comply with the General Prerequisites.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
To successfully join CentOS6 to an Active Directory you need to install the necessary packages:
# yum install adcli krb5-workstation sssd pam_krb5
Change the authentication provider by running the following command:
# authconfig \ --enablekrb5 \ --krb5kdc=example.local \ --krb5adminserver=example.local \ --krb5realm=EXAMPLE.LOCAL \ --enablesssd \ --enablesssdauth \ --update
Join the Active Directory by running the following command:
adcli join example.local -v
Configure the
sssd.confby creating a backup of the old/etc/sssd/sssd.confand override its contents with:[sssd] domains = example.local config_file_version = 2 services = nss, pam [domain/example.local] ad_domain = example.local krb5_realm = EXAMPLE.LOCAL realmd_tags = manages-system joined-with-samba cache_credentials = True id_provider = ad krb5_store_password_if_offline = True default_shell = /bin/bash ldap_id_mapping = True use_fully_qualified_names = False fallback_homedir = /home/%d/%u access_provider = ad
Set the file permissions to
600.# chmod 600 /etc/sssd/sssd.conf # service sssd start # chkconfig sssd on
Configure the
krb5.conffile by creating a backup of the old/etc/krb5.confand override its content with:[libdefaults] default_realm = EXAMPLE.LOCAL dns_lookup_kdc = true forwardable = true default_ccache_name = FILE:/tmp/krb5cc_%{uid} [realms] EXAMPLE.LOCAL = { admin_server = EXAMPLE.LOCAL #kdc = dc1.EXAMPLE.LOCAL #kdc = dc2.EXAMPLE.LOCAL } [logging] kdc = FILE:/var/log/krb5/krb5kdc.log admin_server = FILE:/var/log/krb5/kadmind.log default = SYSLOG:NOTICE:DAEMON [domain_realm] .EXAMPLE.LOCAL = EXAMPLE.LOCAL EXAMPLE.LOCAL = EXAMPLE.LOCALCheck the domain connectivity and make sure that everything works by running the following commands:
# dig -t SRV _ldap._tcp.example.local
# dig -t SRV _ldap._tcp.dc._msdcs.example.local
# adcli info example.local
# id administrator
Joining a Linux endpoint to Active Directory using SSSD for CentOS7/8, Fedora31, RHEL7/8, OracleLinux7
To join a Linux endpoint to an Active Directory (AD) domain using SSSD you need to follow the steps described below and also comply with the General Prerequisites.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Install the necessary packages:
Centos7/8, Fedora31 and RHEL8 require the following packages:
# yum install adcli krb5-workstation realmd sssd
Oracle Linux7 and RHEL7 require the following packages:
# yum install samba-common-tools realmd oddjob oddjob-mkhomedir sssd adcli krb5-workstation
Join the Active Directory domain by running the following command.
# realm join example.local -U administrator
Check the domain connectivity by running the following commands.
# dig -t SRV _ldap._tcp.example.local
# dig -t SRV _ldap._tcp.dc._msdcs.example.local
# realm discover example.local
# realm list
Joining a Linux endpoint to Active Directory using SSSD for Ubuntu, Debian
To join a Linux endpoint to an Active Directory (AD) domain using SSSD you need to follow the steps described below and also comply with the General Prerequisites.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Install the necessary packages.
# sudo apt install sssd-ad sssd-tools realmd adcli
Note
For Ubuntu14 you'll need to install an additional package.
# sudo apt-get install packagekit
Join the Active Directory domain by running the following command.
# sudo realm -v join example.local
Check the domain connectivity by running the following commands.
# dig -t SRV _ldap._tcp.example.local # dig -t SRV _ldap._tcp.dc._msdcs.example.local # sudo realm -v discover example.local # realm list
Joining a Linux endpoint to Active Directory using SSSD for SUSE Linux Enterprise 12, 15
To join a Linux endpoint to an Active Directory (AD) domain using SSSD for SUSE you need to follow the steps described below and also comply with the General Prerequisites.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Install the necessary packages.
Install
krb5-client.# zypper in krb5-client
Install the following packages.
# zypper in adcli sssd sssd-ldap sssd-ad sssd-tools
Make a backup of the old
/etc/krb5.confand override its content with:[libdefaults] default_realm = EXAMPLE.LOCAL dns_lookup_kdc = true forwardable = true default_ccache_name = FILE:/tmp/krb5cc_%{uid} [realms] EXAMPLE.LOCAL = { admin_server = EXAMPLE.LOCAL #kdc = dc1.EXAMPLE.LOCAL #kdc = dc2.EXAMPLE.LOCAL } [logging] kdc = FILE:/var/log/krb5/krb5kdc.log admin_server = FILE:/var/log/krb5/kadmind.log default = SYSLOG:NOTICE:DAEMON [domain_realm] .EXAMPLE.LOCAL = EXAMPLE.LOCAL EXAMPLE.LOCAL = EXAMPLE.LOCALConfigure the
sssd.conffile by making a backup of the old/etc/sssd/sssd.confand override its content with:[sssd] config_file_version = 2 services = nss,pam domains = example.local [nss] filter_users = root filter_groups = root [pam] [domain/example.local] id_provider = ad auth_provider = ad ad_domain = example.local cache_credentials = true enumerate = false override_homedir = /home/%d/%u ldap_id_mapping = true ldap_referrals = false ldap_schema = ad
Set the permissions of the file to
600.# chmod 600 /etc/sssd/sssd.conf
Configure
nsswitch.conffilepasswd: compat sss group: compat sss
Join the Active Directory domain by running the following command:
# adcli join -D example.local
Enable and start the
sssddaemon.# systemctl enable sssd # systemctl start sssd
Configure LDAP client
Install the necessary packages.
# zypper in openldap2-client cyrus-sasl-gssapi
Add the following lines to
/etc/openldap/ldap.conf.URI ldap://example.local BASE dc=example,dc=local REFERRALS OFF
Check the domain connectivity by running the following commands:
# ldapsearch -Y GSSAPI cn=Administrator # adcli info example.local # id administrator # getent passwd administrator
Joining a Linux endpoint to Active Directory using Winbind
This section covers instructions for the following operating systems:
Joining a Linux endpoint to Active Directory using Winbind on CentOS6, RHEL7
To join a Linux endpoint to an Active Directory (AD) domain using Winbind you need to follow the steps described below and also comply with the General Prerequisites.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Install the necessary packages.
# yum -y install samba4-winbind samba4-winbind-clients pam_krb5 krb5-libs
Change the authentication provider by running the following command:
# authconfig \ --enablekrb5 \ --krb5kdc=example.local \ --krb5adminserver=example.local \ --krb5realm=EXAMPLE.LOCAL \ --enablewinbind \ --enablewinbindauth \ --smbsecurity=ads \ --smbrealm=EXAMPLE.LOCAL \ --smbservers=example.local \ --smbworkgroup=example\ --winbindtemplatehomedir=/home/%U \ --winbindtemplateshell=/bin/bash \ --enablemkhomedir \ --enablewinbindusedefaultdomain \ --update
Configure
nsswitch.conffile by enabling the parameters in/etc/nsswitch.conffile:passwd: compat winbind group: compat winbind
Join the Active Directory domain.
Create a Kerberos keytab file:
# sudo net ads keytab create -U administrator
Start Winbind service
# service winbind start # chkconfig winbind on
Run the following command
# net ads join -U administrator -v Enter administrator's password: Using short domain name -- EXAMPLE Joined 'Ubuntu20-VM' to dns domain 'example.local' No DNS domain configured for Ubuntu20-VM. Unable to perform DNS Update. DNS update failed!
Important
Even if the above message mentions that the DNS update has failed, please note that DNS was correctly updated and you should ignore this error message.
Check the domain connectivity by running the following command:
# wbinfo -u
Joining a Linux endpoint to Active Directory using Winbind for CentOS7/8,Fedora31,RHEL8,OracleLinux7
To join a Linux endpoint to an Active Directory (AD) domain using Winbind you need to follow the steps described below and also comply with the General Prerequisites.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Install the necessary packages.
# yum install samba samba-client samba-winbind samba-winbind-client
Configure the
smb.conffile.Make a backup of the old
/etc/samba/smb.confand override it's content with:[global] workgroup = EXAMPLE realm = EXAMPLE.LOCAL security = ads idmap config * : backend = autorid idmap config * : range = 100000-19999999 idmap config * : rangesize = 1000000 template homedir = /home/%D/%U template shell = /bin/bash winbind use default domain = false winbind offline logon = true log file = /var/log/samba/log.%m max log size = 50 log level = 0 kerberos method = secrets and keytabJoin the Active Directory domain.
Create a Kerberos
krb5.keytabfile:# sudo net ads keytab create -U administrator
Enable the Winbind service.
# systemctl enable winbind --now
Run the following command.
# net ads join -U Administrator --no-dns-updates example.local
Check the domain connectivity by running the following commands.
# host -t SRV _kerberos._udp.example.local # host -t SRV _kerberos._tcp.example.local # testparm # wbinfo -u # wbinfo -g
Joining a Linux endpoint to Active Directory using Winbind for SUSE Linux Enterprise 12,15
To join a Linux endpoint to an Active Directory (AD) domain using Winbind for SUSE you need to follow the steps described below and also comply with the General Prerequisites.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Install the necessary packages.
Install
krb5client.# zypper in krb5-client
Configure the Kerberos client.
Make a backup of the old
/etc/krb5.confand override its content with:[libdefaults] default_realm = EXAMPLE.LOCAL dns_lookup_kdc = true forwardable = true default_ccache_name = FILE:/tmp/krb5cc_%{uid} [realms] EXAMPLE.LOCAL = { admin_server = EXAMPLE.LOCAL #kdc = dc1.EXAMPLE.LOCAL #kdc = dc2.EXAMPLE.LOCAL } [logging] kdc = FILE:/var/log/krb5/krb5kdc.log admin_server = FILE:/var/log/krb5/kadmind.log default = SYSLOG:NOTICE:DAEMON [domain_realm] .EXAMPLE.LOCAL = EXAMPLE.LOCAL EXAMPLE.LOCAL = EXAMPLE.LOCALInstall the following packages:
# zypper in samba-client samba-libs samba-winbind
Configure the
smb.conffile.Make a backup of the old
/etc/samba/smb.confand override its content with:[global] workgroup = EXAMPLE kerberos method = secrets and keytab realm = EXAMPLE.LOCAL security = ADS winbind refresh tickets = yes winbind use default domain = yes template shell = /bin/bash template homedir = /home/%D/%U idmap config * : backend = tdb idmap config * : range = 10000-19999 idmap config EXAMPLE: backend = rid idmap config EXAMPLE: range = 20000-29999Set the permissions of the file to
600.# chmod 600 /etc/samba/smb.conf
Configure the
nsswitch.conffile.Enable parameters in
/etc/nsswitch.conffile:passwd: compat winbind group: compat winbind
Establish connection with Kerberos by running the following command.
# kinit Administrator
Join the Active Directory domain by running the following command.
#net ads join -U Administrator
Enable and start the Winbind daemon by running the following commands.
# systemctl enable winbind # systemctl start winbind
Configure LDAP client.
Install the necessary packages.
zypper in openldap2-client cyrus-sasl-gssapi
Add the following lines to
/etc/openldap/ldap.conf.URI ldap://example.local BASE dc=example,dc=local REFERRALS OFF
Check the domain connectivity by running the following commands.
# ldapsearch -Y GSSAPI cn=Administrator # net ads info # id administrator # getent passwd administrator
Joining a Linux endpoint to Active Directory using Winbind for Ubuntu, Debian
To join a Linux endpoint to an Active Directory (AD) domain using Winbind you need to follow the steps described below and also comply with the General Prerequisites.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Install the following packages.
# sudo apt install samba krb5-config krb5-user winbind libpam-winbind libnss-winbind
Enter the domain name using only capital letters:
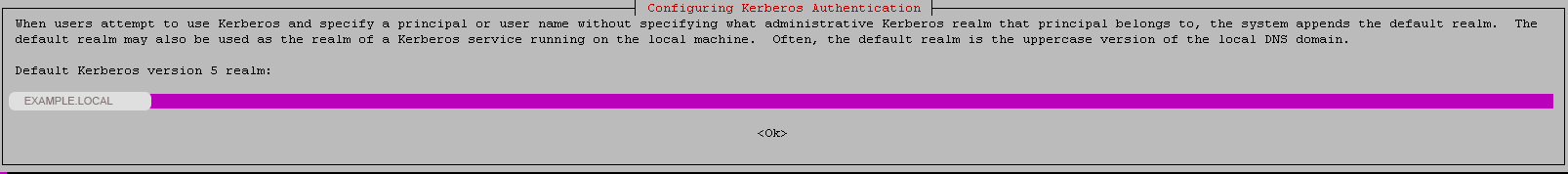
Leave blank the Kerberos server for your realm.
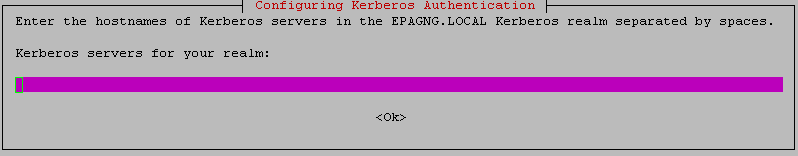
Leave blank the administrative server for your Kerberos realm.
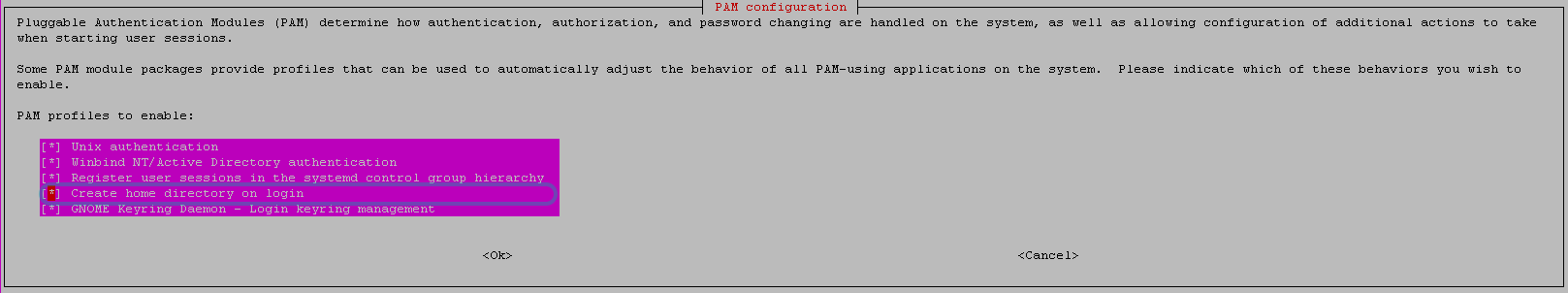
Configure PAM by running the following command and enable “Create home directory on login”.
# sudo pam-auth-update
Important
This command is not applicable for Debian and Ubuntu14.
Configure
nsswitch.conffile and enable parameters in/etc/nsswitch.conffile.passwd: compat winbind group: compat winbind
Configure the
smb.conffile.Make a backup of the old
/etc/samba/smb.confand override it's content with:[global] workgroup = EXAMPLE security = ads realm = EXAMPLE.LOCAL encrypt passwords = yes winbind use default domain = yes winbind refresh tickets = true template homedir = /home/%D/%U template shell = /bin/bash kerberos method = secrets and keytab
Restart samba service.
# systemctl restart smbd.service
Configure
krb5.conffile. Make a backup of theold /etc/krb5.confand override it's content with:[libdefaults] default_realm = EXAMPLE.LOCAL dns_lookup_realm = true dns_lookup_kdc = true dns_fallback = yes [realms] EXAMPLE.LOCAL = { kdc = example.local default_domain = example.local } [domain_realm] .EXAMPLE.LOCAL = EXAMPLE.LOCAL EXAMPLE.LOCAL = EXAMPLE.LOCALJoin the Active Directory domain.
Initiate a Kerberos ticket and verify it.
# sudo kinit administrator
Create a Kerberos keytab file.
# sudo net ads keytab create -U administrator
Join the computer to Active Directory:
# sudo net ads join -U administrator
Restart samba service.
# systemctl restart smbd.service
Check the domain connectivity by running the following commands:
# wbinfo -u # wbinfo -g # getent passwd # getent group # wbinfo -i administrator
Note
DNS update failed: NT_STATUS_INVALID_PARAMETER is not an error.
The computer joined the Active Directory successfully.
Troubleshooting
This section covers instructions for the following:
Troubleshooting the PBIS Active Directory Domain Join Procedure
This section contains a list of errors that might be encountered during the PBIS Active Directory domain join procedure.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Error: ERROR_GEN_FAILURE [code 0x0000001f]
The domainjoin-cli command may fail due to the presence of avahi-daemon package.
# domainjoin-cli join example.local administrator Joining to AD Domain: example.local With Computer DNS Name: user.example.local administrator@EXAMPLE.LOCAL's password: Error: ERROR_GEN_FAILURE [code 0x0000001f]
Resolution
Remove the
avahi-daemonpackage# sudo apt-get remove avahi-daemon
Error: Invalid hostname [code 0x000004ba]
The domainjoin-cli command may fail due to incorrect configuration of the hostname.
# cd /opt/pbis/bin/ # sudo domainjoin-cli join example.local administrator Error: Invalid hostname [code 0x000004ba] The hostname may not be 'linux' or 'localhost'.
Resolution
Change the hostname by running the following command:
# hostnamectl set-hostname <NAME>
Delete the old name from
/etc/hostnameand replace with the new one.Replace any occurrence of the endpoint name from
/etc/hosts.Reboot the endpoint.
Error: Module not configured [code 0x000003eb]
The domainjoin-cli command may fail due to incorrect configuration of the hostname.
# cd /opt/pbis/bin/ # sudo domainjoin-cli join example.local administrator Joining to AD Domain: example.local With Computer DNS Name: bdvm-c6x64.example.local administrator@EXAMPLE.LOCAL's password: Error: Module not configured [code 0x000003eb] Even though the configuration of 'hostname' was executed, the configuration is not complete. Please contact support.
Resolution
Change the hostname by running the following command:
# hostnamectl set-hostname <NAME>
Delete the old name from
etc/hostnameand replace with the new one.Replace any occurrence of the endpoint name from
/etc/hosts.Reboot the endpoint.
Error: BeyondTrust AD Bridge Open requires library libnsl.so.1; please install libnsl.so.1 before installing AD Bridge.
Executing the .sh file may fail due to missing libnsl.so.1 library.
# ./pbis-open-9.1.0.551.linux.x86_64.rpm.sh Creating directory pbis-open-9.1.0.551.linux.x86_64.rpm Verifying archive integrity... All good. Uncompressing pbis-open-9.1.0.551.linux.x86_64.rpm.......... Installing packages and old packages will be removed warning: /home/pbis-open-9.1.0.551.linux.x86_64.rpm/./packages/pbis-open-upgrade-9.1.0-551.x86_64.rpm: Header V3 DSA/SHA1 Signature, key ID c9ceecef: NOKEY Verifying... ################################# [100%] Preparing... ################################# [100%] Updating / installing... 1:pbis-open-upgrade-9.1.0-551 ################################# [100%] warning: /home/pbis-open-9.1.0.551.linux.x86_64.rpm/./packages/pbis-open-9.1.0-551.x86_64.rpm: Header V3 DSA/SHA1 Signature, key ID c9ceecef: NOKEY Verifying... ################################# [100%] Preparing... ################################# [100%] BeyondTrust AD Bridge Open requires library libnsl.so.1; please install libnsl.so.1 before installing AD Bridge. error: %prein(pbis-open-9.1.0-551.x86_64) scriptlet failed, exit status 1 error: pbis-open-9.1.0-551.x86_64: install failed Error installing /home/pbis-open-9.1.0.551.linux.x86_64.rpm/./packages/pbis-open-9.1.0-551.x86_64.rpm The install has not completed. Correct any errors and reinstall by running /home/pbis-open-9.1.0.551.linux.x86_64.rpm/install.sh install
Resolution
Install
libnslpackage# yum install libnsl
Error: Failed to download metadata for repo 'appstream': Cannot prepare internal mirrorlist: No URLs in mirrorlist
Cannot install package due to internal mirrorlist.
# yum install libnsl CentOS Linux 8 - AppStream 118 B/s | 38 B 00:00 Error: Failed to download metadata for repo 'appstream': Cannot prepare internal mirrorlist: No URLs in mirrorlist [root@bdvm-c8x64 home]# yum install libnsl CentOS Linux 8 - AppStream 512 B/s | 38 B 00:00 Error: Failed to download metadata for repo 'appstream': Cannot prepare internal mirrorlist: No URLs in mirrorlist [root@bdvm-c8x64 home]# yum update CentOS Linux 8 - AppStream 437 B/s | 38 B 00:00 Error: Failed to download metadata for repo 'appstream': Cannot prepare internal mirrorlist: No URLs in mirrorlist
Resolution
Run the following commands:
# cd /etc/yum.repos.d/ # sed -i 's/mirrorlist/#mirrorlist/g' /etc/yum.repos.d/CentOS-* # sed -i 's|#baseurl=http://mirror.centos.org|baseurl=http://vault.centos.org|g' /etc/yum.repos.d/CentOS-* # yum update -y
Re-install the package
Error: Received error while querying lwsmd. [code 0x00000002]
Cannot join to domain due to error code 0x00000002.
# sudo domainjoin-cli join example.local administrator Error: Received error while querying lwsmd. [code 0x00000002] Received error while querying lwsmd.
Resolution
Check the output of
pbis-open*.shfile for mentions related to SELinux.# ./pbis-open-9.1.0.551.linux.x86_64.rpm.sh Creating directory pbis-open-9.1.0.551.linux.x86_64.rpm Verifying archive integrity... All good. Uncompressing pbis-open-9.1.0.551.linux.x86_64.rpm.......... Installing packages and old packages will be removed ... SELinux Mode: Enforcing An appropriate SELinux policy [/opt/pbis/share/rhel/unknown/pbis.pp] was not included in this package. You may provide a policy at /opt/pbis/share/pbis.pp SELinux found to be present, enabled, and enforcing. You may either provide a policy at /opt/pbis/share/pbis.pp --OR-- SELinux must be disabled or set to permissive mode by editing the file /etc/selinux/config and rebooting. For instructions on how to edit the file to disable SELinux, see the SELinux man page. BeyondTrust AD Bridge will not install without an appropriate policy for SELinux. warning: %post(pbis-open-9.1.0-551.x86_64) scriptlet failed, exit status 1 ...
Check the SELinux status by running the following command:
# sestatus SELinux status: enabled SELinuxfs mount: /sys/fs/selinux SELinux root directory: /etc/selinux Loaded policy name: targeted Current mode: enforcing Mode from config file: enforcing Policy MLS status: enabled Policy deny_unknown status: allowed Memory protection checking: actual (secure) Max kernel policy version: 31
Change the value of SELINUX variable in configuration file
/etc/selinux/configto disable it.SELINUX=disabled
Re-run the
pbis-open*.shcommand.
Error: ERROR_BAD_COMMAND [code 0x00000016]
This is not an error, the endpoint was joined successfully.
# /opt/pbis/bin/domainjoin-cli join example.local administrator Joining to AD Domain: example.local With Computer DNS Name: bdvm-c8x64.example.local administrator@EXAMPLE.LOCAL's password: Warning: A resumable error occurred while processing the 'hostname' module ERROR_BAD_COMMAND [code 0x00000016] Warning: System restart required Your system has been configured to authenticate to Active Directory for the first time. It is recommended that you restart your system to ensure that all applications recognize the new settings. SUCCESS
Error: DNS_ERROR_BAD_PACKET [code 0x0000251e]
# /opt/pbis/bin/domainjoin-cli join example.local administrator Joining to AD Domain: example.local With Computer DNS Name: o7x64tl.example.local administrator@EXAMPLE.LOCAL's password: Error: DNS_ERROR_BAD_PACKET [code 0x0000251e] A bad packet was received from a DNS server. Potentially the requested address does not exist.
Resolution
Check if DC responds to ping.
# ping example.local
Check if DNS of
Computeris set to IP of the Domain Controller.Check if the search order for
hostsdatabase isfiles, thendnsin/etc/nsswitch.conf.Add to
/etc/resolv.conf.search example.local nameserver 11.11.11.11
Troubleshooting the Domain Join Procedure for SSSD
This section contains a list of errors that might be encountered during the SSSD Active Directory domain join procedure.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Error: Failed to join domain: failed to lookup DC info for domain 'example.local' over rpc: The attempted logon is invalid. This is either due to a bad username or authentication information.
The error code appears due to incorrect user or password.
# realm join example.local -U administrator -v * Resolving: _ldap._tcp.example.local * Performing LDAP DSE lookup on: 11.11.11.11 * Successfully discovered: example.local Password for administrator: * Required files: /usr/sbin/oddjobd, /usr/libexec/oddjob/mkhomedir, /usr/sbin/sssd, /usr/bin/net * LANG=C LOGNAME=root /usr/bin/net -s /var/cache/realmd/realmd-smb-conf.0HT7S1 -U administrator ads join example.local Enter administrator's password: Failed to join domain: failed to lookup DC info for domain 'example.local' over rpc: The attempted logon is invalid. This is either due to a bad username or authentication information. ! Joining the domain example.local failed realm: Couldn't join realm: Joining the domain example.local failed
Resolution
Re-run the command and enter the correct credentials.
Error: ! Failed to enroll machine in realm: GDBus.Error:org.freedesktop.systemd1.UnitMasked: Unit is masked.
The error code appears due to missing packages.
# realm join example.local -U administrator -v * Resolving: _ldap._tcp.example.local * Performing LDAP DSE lookup on: 11.11.11.11 * Successfully discovered: example.local Password for administrator: * Couldn't find file: /usr/bin/net * Required files: /usr/sbin/oddjobd, /usr/libexec/oddjob/mkhomedir, /usr/sbin/sssd, /usr/bin/net * Resolving required packages ! Failed to enroll machine in realm: GDBus.Error:org.freedesktop.systemd1.UnitMasked: Unit is masked. realm: Couldn't join realm: Failed to enroll machine in realm. See diagnostics.
Resolution
Run the following command:
# yum install samba-common-tools realmd oddjob oddjob-mkhomedir sssd adcli krb5-workstation
Error: No results: example.local
When running discover to an Active Directory (AD), the realm discover command resolves the realm but produces no result.
# sudo realm -v discover example.local sudo: unable to resolve host user-market-2: Connection timed out * Resolving: _ldap._tcp.example.local * Resolving: example.local * No results: example.local example.local type: kerberos realm-name: EXAMPLE.LOCAL domain-name: example.local configured: no
Resolution
To solve the problem:
Check that the VM has the date & time synchronized with the Active Directory.
Set the same time zone, date & time as the Active Directory.
Check if DC responds to ping.
# ping example.local
Check if DNS of
Computeris set to IP of the Domain Controller.Check if the search order for
hostsdatabase isfiles, thendnsin/etc/nsswitch.conf.hosts: files dns mdns4_minimal [NOTFOUND=return]
Error: realm: No such realm found: example.local
When running discover to an Active Directory (AD), the realm discover command cannot resolve the realm.
# sudo realm -v discover example.local sudo: unable to resolve host user-market-2: No such file or directory * Resolving: _ldap._tcp.example.local * Resolving: example.local * No results: example.local realm: No such realm found: example.local
Resolution
Add to
/etc/resolv.conf.search example.local nameserver 11.11.11.11
Verify in
/etc/nsswitch.confthat the database hosts: has dns after files.hosts: files dns myhostname
Run ping command.
# ping example.local
Error: Couldn't authenticate as: Administrator@EXAMPLE.LOCAL: Preauthentication failed
# sudo realm -v join example.local sudo: unable to resolve host user-market-2: Connection timed out * Resolving: _ldap._tcp.example.local * Performing LDAP DSE lookup on: 11.11.11.11 * Successfully discovered: example.local Password for Administrator: * Unconditionally checking packages * Resolving required packages * LANG=C /usr/sbin/adcli join --verbose --domain example.local --domain-realm EXAMPLE.LOCAL --domain-controller 11.11.11.--login-type user --login-user Administrator --stdin-password * Using domain name: example.local * Calculated computer account name from fqdn: USER-MARKET-2 * Using domain realm: example.local * Sending netlogon pings to domain controller: cldap://11.11.11.11 * Received NetLogon info from: DC.example.local * Wrote out krb5.conf snippet to /var/cache/realmd/adcli-krb5-2lGxqJ/krb5.d/adcli-krb5-conf-ophiP9 ! Couldn't authenticate as: Administrator@EXAMPLE.LOCAL: Preauthentication failed adcli: couldn't connect to example.local domain: Couldn't authenticate as: Administrator@EXAMPLE.LOCAL: Preauthentication failed ! Failed to join the domain realm: Couldn't join realm: Failed to join the domain
Resolution
Check that you entered the correct password for administrator account and run the command again.
Error: Failed to enroll machine in realm: The following packages have unmet dependencies:
# sudo realm -v join example.local
* Resolving: _ldap._tcp.example.local
* Performing LDAP DSE lookup on: 11.11.11.11
* Successfully discovered: example.local
* Unconditionally checking packages
* Resolving required packages
* Installing necessary packages: sssd-tools, sssd, libnss-sss, libpam-sss
! Failed to enroll machine in realm: The following packages have unmet dependencies:
sssd-tools: Depends: libc6 (>= 2.12) but 2.19-0ubuntu6.15 is to be installed
Depends: libpopt0 (>= 1.14) but 1.16-8ubuntu1 is to be installed
Depends: libselinux1 (>= 1.32) but 2.2.2-1ubuntu0.1 is to be installed
Depends: libsemanage1 (>= 2.0.3) but 2.2-1 is to be installed
Depends: libtalloc2 (>= 2.0.4~git20101213) but 2.1.5-0ubuntu0.14.04.1 is to be installed
Depends: sssd-common (= 1.11.5-1ubuntu3) but 1.11.8-0ubuntu0.7 is to be installed
realm: Couldn't join realm: Failed to enroll machine in realm. See diagnostics.Resolution
Update the packages by running the commands.
# apt update # sudo apt install sssd-ad sssd-tools realmd adcli
Error: KDC or realm is unreachable or can't resolve address
This problem appears when trying to join Centos6 to Active Directory using SSSD
"errors": [
{
"description": "failed to generate credentials cache file for keytab file: default",
"message": "KDC or realm is unreachable or can't resolve address"
}
],Resolution
Run the following command:
# authconfig \ --enablekrb5 \ --krb5kdc=example.local \ --krb5adminserver=example.local \ --krb5realm=EXAMPLE.LOCAL \ --enablesssd \ --enablesssdauth \ --update
Check
krb5.conffile. It should have the following format:[libdefaults] default_realm = EXAMPLE.LOCAL dns_lookup_kdc = true forwardable = true default_ccache_name = FILE:/tmp/krb5cc_%{uid} [realms] EXAMPLE.LOCAL = { admin_server = EXAMPLE.LOCAL #kdc = dc1.EXAMPLE.LOCAL #kdc = dc2.EXAMPLE.LOCAL } [logging] kdc = FILE:/var/log/krb5/krb5kdc.log admin_server = FILE:/var/log/krb5/kadmind.log default = SYSLOG:NOTICE:DAEMON [domain_realm] .EXAMPLE.LOCAL = EXAMPLE.LOCAL EXAMPLE.LOCAL = EXAMPLE.LOCAL
Error: Cannot find a valid baseurl for repo: base
The problem appears on CentOS 6 due to the fact that OS is approaching end of life
# yum install adcli krb5-workstation sssd Loaded plugins: fastestmirror, refresh-packagekit, security Setting up Install Process Loading mirror speeds from cached hostfile YumRepo Error: All mirror URLs are not using ftp, http[s] or file. Eg. Invalid release/repo/arch combination/ removing mirrorlist with no valid mirrors: /var/cache/yum/x86_64/6/base/mirrorlist.txt Error: Cannot find a valid baseurl for repo: base
Resolution
Create a new repo in
/etc/yum.repos.d/and add the following:[C6.10-base] name=CentOS-6.10 - Base baseurl=http://vault.epel.cloud/6.10/os/$basearch/ gpgcheck=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-6 enabled=1 metadata_expire=never [C6.10-updates] name=CentOS-6.10 - Updates baseurl=http://vault.epel.cloud/6.10/updates/$basearch/ gpgcheck=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-6 enabled=1 metadata_expire=never [C6.10-extras] name=CentOS-6.10 - Extras baseurl=http://vault.epel.cloud/6.10/extras/$basearch/ gpgcheck=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-6 enabled=1 metadata_expire=never [C6.10-contrib] name=CentOS-6.10 - Contrib baseurl=http://vault.epel.cloud/6.10/contrib/$basearch/ gpgcheck=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-6 enabled=0 metadata_expire=never [C6.10-centosplus] name=CentOS-6.10 - CentOSPlus baseurl=http://vault.epel.cloud/6.10/centosplus/$basearch/ gpgcheck=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-6 enabled=0 metadata_expire=never
Update the packages and re-run the command:
# yum update # yum install adcli krb5-workstation sssd
Error: adcli: couldn't connect to domain: Couldn't get kerberos ticket ... Clock skew too great
The problem appears when the endpoint has a different date & time than Active Directory.
# adcli join example.local Password for Administrator@EXAMPLE.LOCAL: adcli: couldn't connect to example.local domain: Couldn't get kerberos ticket for: Administrator@EXAMPLE.LOCAL: Clock skew too great
Resolution
Set the same time zone, date & time on the endpoint as Active Directory.
Error: gss_init_sec_context failed with [ Miscellaneous failure (see text): Clock skew too great]
The problem appears when the endpoint has a different date & time than Active Directory.
# sudo realm -v join example.local * Resolving: _ldap._tcp.example.local * Performing LDAP DSE lookup on: 11.11.11.11 * Successfully discovered: example.local * Unconditionally checking packages * Resolving required packages * LANG=C /usr/sbin/adcli join --verbose --domain example.local --domain-realm EXAMPLE.LOCAL --domain-controller 11.11.11.11 --login-type computer --no-password * Using domain name: example.local * Calculated computer account name from fqdn: BDVMU14X86 * Using domain realm: example.local * Sending netlogon pings to domain controller: cldap://11.11.11.11 * Received NetLogon info from: DC.example.local * Wrote out krb5.conf snippet to /var/cache/realmd/adcli-krb5-ffDXAr/krb5.d/adcli-krb5-conf-YCJvaP ! Couldn't authenticate as machine account: BDVMU14X86: Client 'BDVMU14X86$@EXAMPLE.LOCAL' not found in Kerberos database adcli: couldn't connect to example.local domain: Couldn't authenticate as machine account: BDVMU14X86: Client 'BDVMU14X86$@EXAMPLE.LOCAL' not found in Kerberos database ! Unable to automatically join the domain Password for Administrator: * Unconditionally checking packages * Resolving required packages * LANG=C LOGNAME=root /usr/bin/net -s /var/cache/realmd/realmd-smb-conf.PF1JS1 -U Administrator ads join example.local Enter Administrator's password:gss_init_sec_context failed with [ Miscellaneous failure (see text): Clock skew too great] kinit succeeded but ads_sasl_spnego_gensec_bind(KRB5) failed: An internal error occurred. Failed to join domain: failed to connect to AD: An internal error occurred. ! Joining the domain example.local failed realm: Couldn't join realm: Joining the domain example.local failed
Resolution
Set the same time zone, date & time on the endpoint as the Active Directory.
Error: Failed to enroll machine in realm: GDBus.Error:org.freedesktop.systemd1.UnitMasked: Unit is masked.
The error appears due to missing packages.
# realm join example.local -U administrator -v * Resolving: _ldap._tcp.example.local * Performing LDAP DSE lookup on: 11.11.11.11 * Successfully discovered: example.local Password for administrator: * Couldn't find file: /usr/bin/net * Required files: /usr/sbin/oddjobd, /usr/libexec/oddjob/mkhomedir, /usr/sbin/sssd, /usr/bin/net * Resolving required packages ! Failed to enroll machine in realm: GDBus.Error:org.freedesktop.systemd1.UnitMasked: Unit is masked. realm: Couldn't join realm: Failed to enroll machine in realm. See diagnostics.
Resolution
Install missing packages by running:
# yum install samba-common-tools realmd oddjob oddjob-mkhomedir sssd adcli krb5-workstation
Error: Failed to start System Security Services Daemon status=4 /NOPERMISSION
sssd service cannot be started due to the incorrect permissions set on /etc/sssd/sssd.conf file.
# systemctl start sssd
Job for sssd.service failed because the control process exited with error code.
See "systemctl status sssd.service" and "journalctl -xe" for details.
# systemctl status sssd.service
● sssd.service - System Security Services Daemon
Loaded: loaded (/usr/lib/systemd/system/sssd.service; enabled; vendor preset: disabled)
Active: failed (Result: exit-code) since Wed 2022-09-21 22:08:34 EEST; 5s ago
Process: 9457 ExecStart=/usr/sbin/sssd -i ${DEBUG_LOGGER} (code=exited, status=4)
Main PID: 9457 (code=exited, status=4)
Sep 21 22:08:34 slesl15gia systemd[1]: Starting System Security Services Daemon...
Sep 21 22:08:34 slesl15gia sssd[9457]: Cannot read config file /etc/sssd/sssd.conf. Please chec
k that the file is accessible only by the owner and owned by root.root.
Sep 21 22:08:34 slesl15gia systemd[1]: sssd.service: Main process exited, code=exited, status=4
/NOPERMISSION
Sep 21 22:08:34 slesl15gia systemd[1]: Failed to start System Security Services Daemon.
Sep 21 22:08:34 slesl15gia systemd[1]: sssd.service: Unit entered failed state.
Sep 21 22:08:34 slesl15gia systemd[1]: sssd.service: Failed with result 'exit-code'.Resolution
Add
600permissions to/etc/sssd/sssd.conffile and re-run the start command.# chmod 600 /etc/sssd/sssd.conf # systemctl start sssd
Error: adcli: joining domain example.local failed: Couldn't lookup computer account. Can't contact LDAP server
The endpoint cannot contact LDAP server.
# adcli join -D example.local -U administrator Password for administrator@EXAMPLE.LOCAL: adcli: joining domain example.local failed: Couldn't lookup computer account: SGIA12$: Can't contact LDAP server
Resolution
Configure the LDAP client.
# zypper in openldap2-client cyrus-sasl-gssapi
Add the following lines to
/etc/openldap/ldap.conf.URI ldap://example.local BASE dc=example,dc=local REFERRALS OFF
Error: authconfig: Authentication module /usr/lib64/security/pam_krb5.so is missing. Authentication process might not work correctly.
authconfig command fails to run due to missing so.
# authconfig \ --enablekrb5 \ --krb5kdc=example.local \ --krb5adminserver=example.local \ --krb5realm=EXAMPLE.LOCAL \ --enablesssd \ --enablesssdauth \ --update authconfig: Authentication module /usr/lib64/security/pam_krb5.so is missing. Authentication process might not work correctly.
Resolution
Install missing package:
# yum install pam5_krb
Error: Warning: user would have been denied GPO-based logon access if the ad_gpo_access_control option were set to enforcing mode.
The error appears due to the incomplete configuration of the krb5.conf file.
● sssd.service - System Security Services Daemon
Loaded: loaded (/usr/lib/systemd/system/sssd.service; enabled; vendor preset: disabled)
Active: active (running) since Mon 2022-09-26 12:15:44 EDT; 2 weeks 0 days ago
Main PID: 25700 (sssd)
Tasks: 4
CGroup: /system.slice/sssd.service
├─25700 /usr/sbin/sssd -i --logger=files
├─25701 /usr/libexec/sssd/sssd_be --domain yyz.local --uid 0 --gid 0 --logger=files
├─25702 /usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --logger=files
└─25703 /usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --logger=files
Oct 11 10:32:59 10-10-192-49.yyz.local sssd[be[yyz.local]][25701]: Group Policy Container with DN [cn={8F655C32-3704-42C7-9BAD-5CC2C1A3AE55},cn=policies,cn=system,DC=yyz,DC=local] is unreadable or has unreadable or missing attributes. In order to fix this make sure that this AD object has following attributes readable: nTSecurityDescriptor, cn, gPCFileSysPath, gPCMachineExtensionNames, gPCFunctionalityVersion, flags. Alternatively if you do not have access to the server or can not change permissions on this object, you can use option ad_gpo_ignore_unreadable = True which will skip this GPO.See 'man ad_gpo_ignore_unreadable for details.'
Oct 11 10:32:59 10-10-192-49.yyz.local sssd[be[yyz.local]][25701]: Warning: user would have been denied GPO-based logon access if the ad_gpo_access_control option were set to enforcing mode.
Oct 11 10:36:35 10-10-192-49.yyz.local sssd_be[25701]: GSSAPI client step 1
Oct 11 10:36:35 10-10-192-49.yyz.local sssd_be[25701]: GSSAPI client step 1
Oct 11 10:36:35 10-10-192-49.yyz.local sssd_be[25701]: GSSAPI client step 1
Oct 11 10:36:35 10-10-192-49.yyz.local sssd_be[25701]: GSSAPI client step 2
Oct 11 10:40:31 10-10-192-49.yyz.local sssd[be[yyz.local]][25701]: Group Policy Container with DN [cn={8F655C32-3704-42C7-9BAD-5CC2C1A3AE55},cn=policies,cn=system,DC=yyz,DC=local] is unreadable or has unreadable or missing attributes. In order to fix this make sure that this AD object has following attributes readable: nTSecurityDescriptor, cn, gPCFileSysPath, gPCMachineExtensionNames, gPCFunctionalityVersion, flags. Alternatively if you do not have access to the server or can not change permissions on this object, you can use option ad_gpo_ignore_unreadable = True which will skip this GPO.See 'man ad_gpo_ignore_unreadable for details.'
Oct 11 10:40:31 10-10-192-49.yyz.local sssd[be[yyz.local]][25701]: Warning: user would have been denied GPO-based logon access if the ad_gpo_access_control option were set to enforcing mode.
Oct 11 10:40:54 10-10-192-49.yyz.local sssd[be[yyz.local]][25701]: Group Policy Container with DN [cn={8F655C32-3704-42C7-9BAD-5CC2C1A3AE55},cn=policies,cn=system,DC=yyz,DC=local] is unreadable or has unreadable or missing attributes. In order to fix this make sure that this AD object has following attributes readable: nTSecurityDescriptor, cn, gPCFileSysPath, gPCMachineExtensionNames, gPCFunctionalityVersion, flags. Alternatively if you do not have access to the server or can not change permissions on this object, you can use option ad_gpo_ignore_unreadable = True which will skip this GPO.See 'man ad_gpo_ignore_unreadable for details.'
Oct 11 10:40:54 10-10-192-49.yyz.local sssd[be[yyz.local]][25701]: Warning: user would have been denied GPO-based logon access if the ad_gpo_access_control option were set to enforcing mode.
Resolution
Check that
krb5.confhas the[realms]configured as follows:[libdefaults] default_realm = EXAMPLE.LOCAL dns_lookup_realm = true dns_lookup_kdc = true dns_fallback = yes [realms] EXAMPLE.LOCAL = { kdc = example.local default_domain = example.local } [domain_realm] .EXAMPLE.LOCAL = EXAMPLE.LOCAL EXAMPLE.LOCAL = EXAMPLE.LOCAL
Error: kadmin: Missing parameters in krb5.conf required for kadmin client while initializing kadmin interface
The error appears due to the incomplete configuration of the krb5.conf file.
# kadmin list_principals kadmin: Missing parameters in krb5.conf required for kadmin client while initializing kadmin interface
Resolution
Check that
krb5.confhas the[realms]configured as follows:[libdefaults] default_realm = EXAMPLE.LOCAL dns_lookup_realm = true dns_lookup_kdc = true dns_fallback = yes [realms] EXAMPLE.LOCAL = { kdc = example.local default_domain = example.local } [domain_realm] .EXAMPLE.LOCAL = EXAMPLE.LOCAL EXAMPLE.LOCAL = EXAMPLE.LOCALCheck if hostname is already in use.
Check if the endpoint is disabled in Active Directory.
Error: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Server not found in Kerberos database)
The error appears due to missing rdns parameter form krb5.conf.
------------------------ldapsearch -Y GSSAPI cn=Administrator---------------------------------
● sssd.service - System Security Services Daemon
Loaded: loaded (/usr/lib/systemd/system/sssd.service; enabled; vendor preset: disabled)
Active: active (running) since Tue 2022-10-11 16:43:20 EDT; 1min 30s ago
Main PID: 1923 (sssd)
Tasks: 4
CGroup: /system.slice/sssd.service
├─1923 /usr/sbin/sssd -i --logger=files
├─1963 /usr/libexec/sssd/sssd_be --domain yyz.local --uid 0 --gid 0 --logger=files
├─1967 /usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --logger=files
└─1968 /usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --logger=files
Oct 11 16:43:32 10-10-192-49.yyz.local sssd_be[1963]: GSSAPI client step 1
Oct 11 16:43:32 10-10-192-49.yyz.local sssd_be[1963]: GSSAPI client step 1
Oct 11 16:43:32 10-10-192-49.yyz.local sssd[be[yyz.local]][1963]: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Server not found in Kerberos database)
Oct 11 16:43:32 10-10-192-49.yyz.local sssd[nss][1967]: Enumeration requested but not enabled
Oct 11 16:43:36 10-10-192-49.yyz.local sssd_be[1963]: GSSAPI client step 1
Oct 11 16:43:36 10-10-192-49.yyz.local sssd_be[1963]: GSSAPI client step 1
Oct 11 16:43:36 10-10-192-49.yyz.local sssd[be[yyz.local]][1963]: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Server not found in Kerberos database)
Oct 11 16:43:36 10-10-192-49.yyz.local sssd_be[1963]: GSSAPI client step 1
Oct 11 16:43:36 10-10-192-49.yyz.local sssd_be[1963]: GSSAPI client step 1
Oct 11 16:43:36 10-10-192-49.yyz.local sssd[be[yyz.local]][1963]: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Server not found in Kerberos database)
Resolution
Add
rnds=falsetokrb5.conffile[libdefaults] default_realm = EXAMPLE.LOCAL dns_lookup_realm = true dns_lookup_kdc = true dns_fallback = yes rdns = false [realms] EXAMPLE.LOCAL = { kdc = example.local default_domain = example.local } [domain_realm] .EXAMPLE.LOCAL = EXAMPLE.LOCAL EXAMPLE.LOCAL = EXAMPLE.LOCAL
Troubleshooting the Domain Join Procedure for Winbind
This section contains a list of errors that might be encountered during the Winbind Active Directory domain join procedure.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Error: failed to generate credentials cache file for keytab file: default
The hostname of the endpoint can be at most 15 characters.
# net ads join -U administrator Our netbios name can be at most 15 chars long, "MAC-00-50-56-A9-06-E1" is 21 chars long Invalid configuration. Exiting.... Failed to join domain: The format of the specified computer name is invalid.
Resolution
Change the hostname.
Error: No DNS domain configured for suse15-user. Unable to perform DNS Update.
When joining to an Active Directory sometimes the net command fails to update the DNS.
# net ads join -U administrator Enter administrator's password: Using short domain name -- EXAMPLE Joined 'SUSE15-USER' to dns domain 'example.local' No DNS domain configured for suse15-user. Unable to perform DNS Update. DNS update failed: NT_STATUS_INVALID_PARAMETER
Resolution
Add the IP & FQDN of the machine to
etc/hostsfile.12.12.12.12 suse15-name.example.local suse15-name
Run the command again.
Alternatively you can run the command with
--no-dns-updateparameter.
Error: The format of the specified computer name is invalid.
The problem appears when the hostname is greater than 15 characters.
# net ads join -U administrator Our netbios name can be at most 15 chars long, "MAC-XX-XX-XX-XX-XX-XX" is 21 chars long Invalid configuration. Exiting.... Failed to join domain: The format of the specified computer name is invalid.
Resolution
Change the hostname by running.
# systemctl set-hostname <NAME>
Delete the old name from
/etc/hostnameand replace with the new one.Replace any occurrence of the endpoint name from
/etc/hosts.Reboot the endpoint.
Error: No DNS domain configured. Unable to perform DNS Update
When joining to an Active Directory sometimes the net command fails to update the DNS.
# net ads join -U administrator Enter administrator's password: Using short domain name -- SAMDOM Joined 'AD-Member' to dns domain 'samdom.example.com' No DNS domain configured for AD-Member. Unable to perform DNS Update. DNS update failed: NT_STATUS_INVALID_PARAMETER
Resolution
Add the IP & FQDN of the machine to
/etc/hostsfile.12.12.12.12 AD-Member.samdom.example.com AD-Member
Run the command again.
Alternatively you can run the command with
--no-dns-updateparameter.
Error: E: Package 'krb5-config' has no installation candidate
The krb5-config package cannot be installed.
# sudo apt install samba krb5-config krb5-user winbind libpam-winbind libnss-winbind
Reading package lists... Done
Building dependency tree
Reading state information... Done
Package krb5-config is not available, but is referred to by another package.
This may mean that the package is missing, has been obsoleted, or
is only available from another source
E: Package 'krb5-config' has no installation candidate
# sudo apt install samba krb5-user winbind libpam-winbind libnss-winbind
Reading package lists... Done
Building dependency tree
Reading state information... Done
Some packages could not be installed. This may mean that you have
requested an impossible situation or if you are using the unstable
distribution that some required packages have not yet been created
or been moved out of Incoming.
The following information may help to resolve the situation:
The following packages have unmet dependencies:
krb5-user : Depends: krb5-config but it is not installable
samba : Depends: python-dnspython but it is not installable
Depends: python-samba but it is not going to be installed
Depends: samba-common-bin (= 2:4.5.16+dfsg-1+deb9u4) but it is not going to be installed
Depends: tdb-tools but it is not installable
Recommends: attr but it is not installable
Recommends: samba-dsdb-modules but it is not going to be installed
Recommends: samba-vfs-modules but it is not going to be installed
winbind : Depends: samba-common-bin (= 2:4.5.16+dfsg-1+deb9u4) but it is not going to be installed
E: Unable to correct problems, you have held broken packages.Resolution
Uncomment lines starting with
#debin/etc/apt/sources.listfile.Update the repo and re-run the command.
# apt update # sudo apt install samba krb5-config krb5-user winbind libpam-winbind libnss-winbind
Error: ads_keytab_open: Invalid kerberos method set (0)
The problem appears due to missing section from smb.conf file.
# sudo net ads keytab create -U administrator Warning: "kerberos method" must be set to a keytab method to use keytab functions. Enter administrator's password: ads_keytab_open: Invalid kerberos method set (0)
Resolution
Add the following line to
/etc/samba/smb.conffile:kerberos method = secrets and keytab
Re-run the command again.
Error: could not obtain winbind interface details: WBC_ERR_WINBIND_NOT_AVAILABLE
Testing commands fails.
# wbinfo -t could not obtain winbind interface details: WBC_ERR_WINBIND_NOT_AVAILABLE could not obtain winbind domain name! checking the trust secret for domain (null) via RPC calls failed failed to call wbcCheckTrustCredentials: WBC_ERR_WINBIND_NOT_AVAILABLE Could not check secret [root@fedgia samba]# wbinfo -u could not obtain winbind interface details: WBC_ERR_WINBIND_NOT_AVAILABLE could not obtain winbind domain name! Error looking up domain users [root@fedgia samba]# wbinfo -g could not obtain winbind interface details: WBC_ERR_WINBIND_NOT_AVAILABLE could not obtain winbind domain name! failed to call wbcListGroups: WBC_ERR_WINBIND_NOT_AVAILABLE Error looking up domain groups
Resolution
Run the following command.
# systemctl enable winbind --now
Re-run the commands again.
Error: Failed to join domain: failed to lookup DC info for domain 'EXAMPLE.LOCAL' over rpc: NT_STATUS_CONNECTION_RESET
Join command fails with error NT_STATUS_CONNECTION_RESET.
# net ads join -U Administrator Enter Administrator's password: Failed to join domain: failed to lookup DC info for domain 'EXAMPLE.LOCAL' over rpc: NT_STATUS_CONNECTION_RESET
Resolution
Install SMBv1 on the Active Directory. Go to Server Manager → Dashboard → Start the Remove Roles and Features → Features → SMB 1.0/CIFS Files Sharing Support.
Re-run the command.
Error: DNS update failed!
This is not a problem. The endpoint has been joined to Active Directory with success.
# net ads join -U Administrator Enter Administrator's password: Using short domain name -- EXAMPLE Joined '|USER-USER3' to dns domain 'example.local' No DNS domain configured for user-user3. Unable to perform DNS Update. DNS update failed!
Error: The net Command Fails to Connect to the 127.0.0.1 IP Address
Using the default settings, the net command connects to the 127.0.0.1 IP address. If Samba is not listening on the loopback interface, the connection fails. For example:
# net rpc rights list -U administrator Enter administrator's password: Could not connect to server 127.0.0.1 Connection failed: NT_STATUS_CONNECTION_REFUSED
Resolution
Add the following parameters to the [global] section in
/etc/samba/smb.conffile:bind interfaces only = yes interfaces = lo eth0
Restart the Samba service(s).
Pass the
-IIP_address or the -S host_nameparameter to the net command.
Error: getent not Finding Domain Users and Groups
Sometimes getent passwd or getent group don't display anything.
# getent passwd # getent group
Resolution
Add the following parameters to the
[global]section in/etc/samba/smb.conffile:
winbind enum users = yes winbind enum groups = yes
Note
These lines slow things down therefore they should be added only for testing.
Error: DNS Update failed: ERROR_DNS_GSS_ERROR
When joining to an Active Directory sometimes the net command fails with ERROR_DNS_GSS_ERROR due to an incorrect Kerberos setup on the Active Directory.
# net ads join -U administrator Enter administrator's password: Using short domain name -- SAMDOM Joined 'AD-Member' to dns domain 'samdom.example.com' DNS Update for AD-Member.samdom.example.com failed: ERROR_DNS_GSS_ERROR DNS update failed: NT_STATUS_UNSUCCESSFUL
Resolution
Run the auto-reconfiguration:
# samba_upgradedns --dns-backend=BIND9_DLZ Reading domain information DNS accounts already exist No zone file /usr/local/samba/private/dns/SAMDOM.EXAMPLE.COM.zone DNS records will be automatically created DNS partitions already exist dns-DC1 account already exists See /usr/local/samba/private/named.conf for an example configuration include file for BIND and /usr/local/samba/private/named.txt for further documentation required for secure DNS updates Finished upgrading DNS
Restart the BIND service.
Error: Failed to join domain: Invalid configuration ("workgroup" set to 'EXAMPLE.LOCAL', should be 'EXAMPLE') and configuration modification was not requested
Join command fails due to the fact that authconfig was run incorrectly.
# net ads join -U Administrator
Enter Administrator's password:
Failed to join domain: Invalid configuration ("workgroup" set to 'EXAMPLE.LOCAL', should be 'EXAMPLE') and configuration modification was not requestedResolution
Run the following command correctly.
# authconfig \ --enablekrb5 \ --krb5kdc=example.local \ --krb5adminserver=example.local \ --krb5realm=EXAMPLE.LOCAL \ --enablewinbind \ --enablewinbindauth \ --smbsecurity=ads \ --smbrealm=EXAMPLE.LOCAL \ --smbservers=example.local \ --smbworkgroup=example\ --winbindtemplatehomedir=/home/%U \ --winbindtemplateshell=/bin/bash \ --enablemkhomedir \ --enablewinbindusedefaultdomain \ --update
Error: winbind.service: main process exited, code=exited, status=1/FAILURE
Failed to start Winbind service.
# service winbind status
Redirecting to /bin/systemctl status winbind.service
● winbind.service - Samba Winbind Daemon
Loaded: loaded (/usr/lib/systemd/system/winbind.service; enabled; vendor preset: disabled)
Active: failed (Result: exit-code) since Mon 2022-09-26 10:15:35 EDT; 56s ago
Docs: man:winbindd(8)
man:samba(7)
man:smb.conf(5)
Process: 12649 ExecStart=/usr/sbin/winbindd --foreground --no-process-group $WINBINDOPTIONS (code=exited, status=1/FAILURE)
Main PID: 12649 (code=exited, status=1/FAILURE)
Status: "Starting process..."
Sep 26 10:15:35 rhel7x64tl winbindd[12649]: [2022/09/26 10:15:35.316642, 0] ../../source3/winbindd/winbindd_cache.c:3166(initialize_winbindd_cache)
Sep 26 10:15:35 rhel7x64tl winbindd[12649]: initialize_winbindd_cache: clearing cache and re-creating with version number 2
Sep 26 10:15:35 rhel7x64tl winbindd[12649]: [2022/09/26 10:15:35.319950, 0] ../../source3/winbindd/winbindd_util.c:1279(init_domain_list)
Sep 26 10:15:35 rhel7x64tl winbindd[12649]: Could not fetch our SID - did we join?
Sep 26 10:15:35 rhel7x64tl winbindd[12649]: [2022/09/26 10:15:35.319999, 0] ../../source3/winbindd/winbindd.c:1462(winbindd_register_handlers)
Sep 26 10:15:35 rhel7x64tl winbindd[12649]: unable to initialize domain list
Sep 26 10:15:35 rhel7x64tl systemd[1]: winbind.service: main process exited, code=exited, status=1/FAILURE
Sep 26 10:15:35 rhel7x64tl systemd[1]: Failed to start Samba Winbind Daemon.
Sep 26 10:15:35 rhel7x64tl systemd[1]: Unit winbind.service entered failed state.
Sep 26 10:15:35 rhel7x64tl systemd[1]: winbind.service failed.Resolution
Join the endpoint to Active Directory using the steps from How to join Centos6, RHEL7.
macOS
Joining a macOS endpoint to Active Directory
To join a macOS Ventura endpoint to an Active Directory (AD) domain follow these steps.
Example:
Realm: example.local Domain User: administrator Domain IP: 11.11.11.11
Go to System Preferences > Network.
Under the Ethernet section, click Advanced.
Under DNS , enter the IP address of the Active Directory.
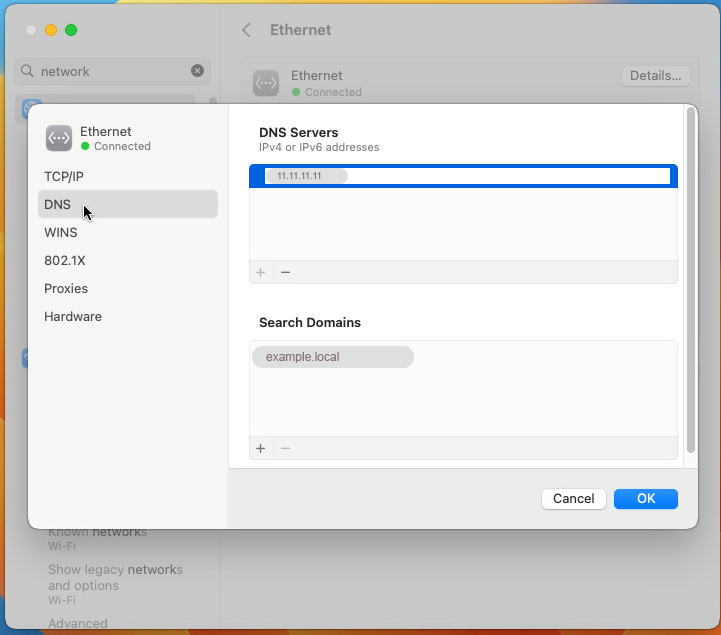
Click OK to save changes.
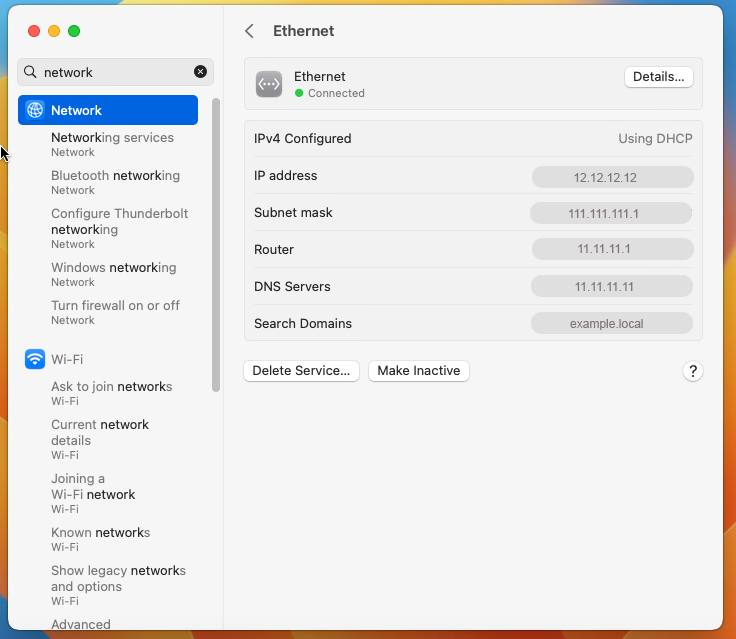
Back in the Network page you can see the fields completed with the data.
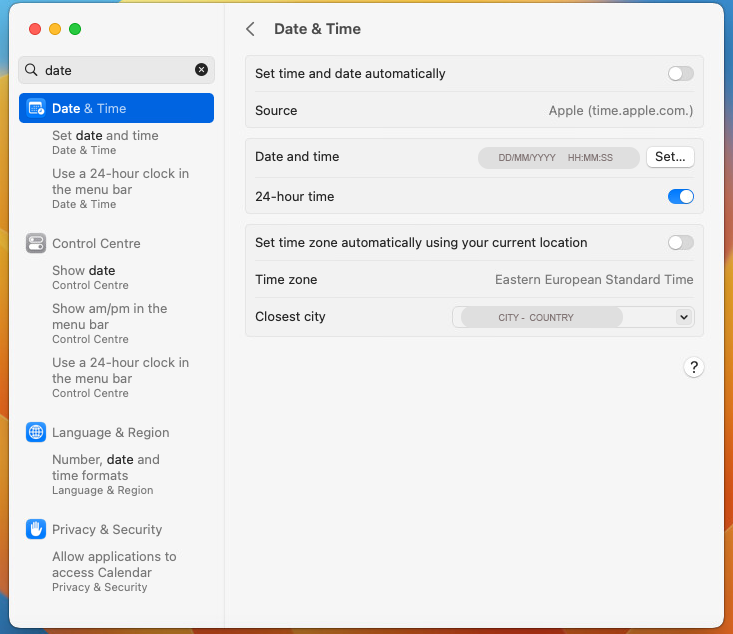
Set the Date &Time as well as the Time Zone to be the same as in Active Directory.
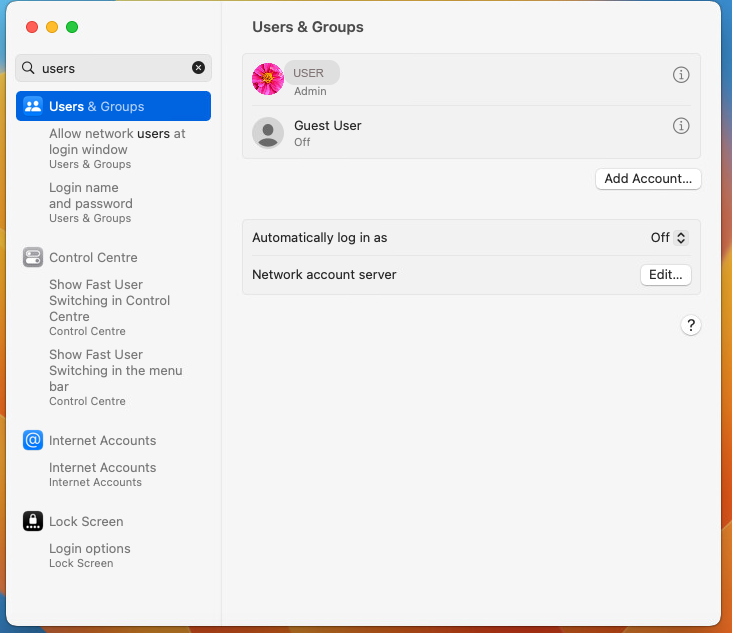
Go to System Preferences > Users & Groups > Network account server.
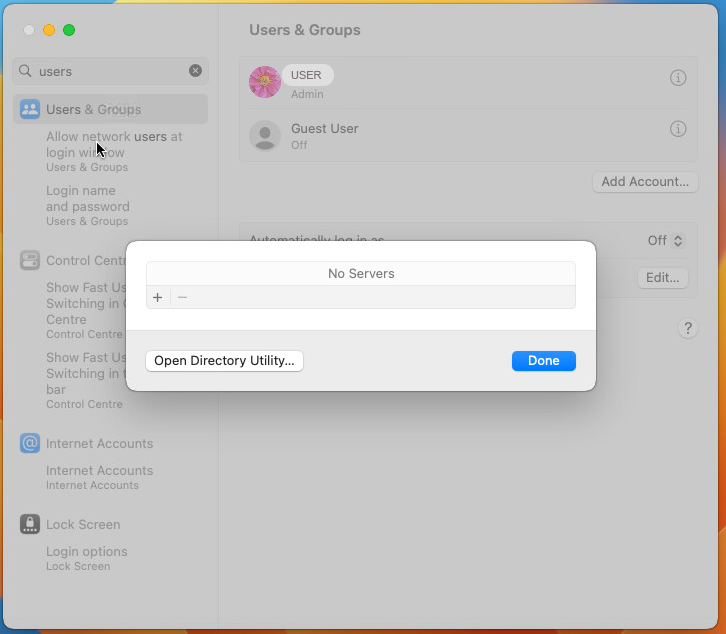
Click Edit > Open Directory Utility.
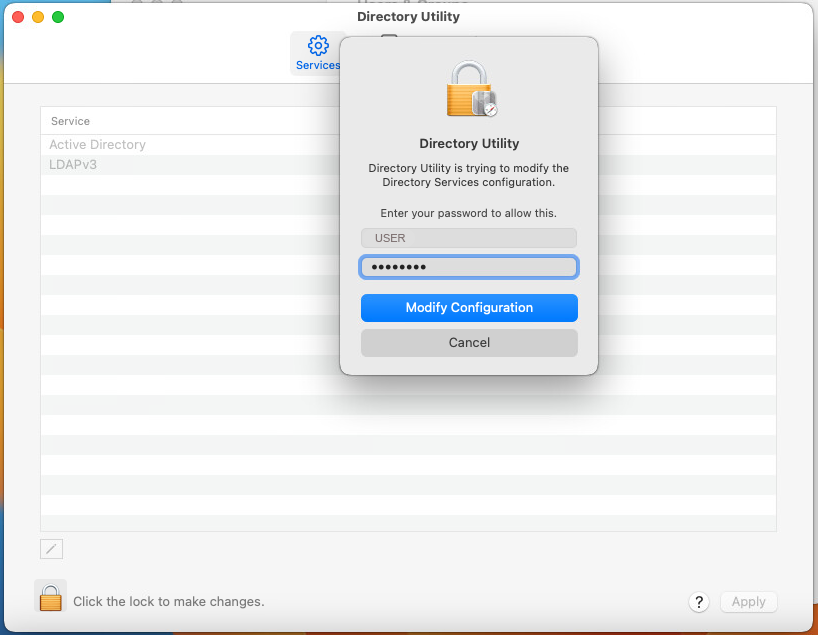
In the Directory Utility enter your local Username and Password.
Insert the Active Directory Domain name and click on Bind.
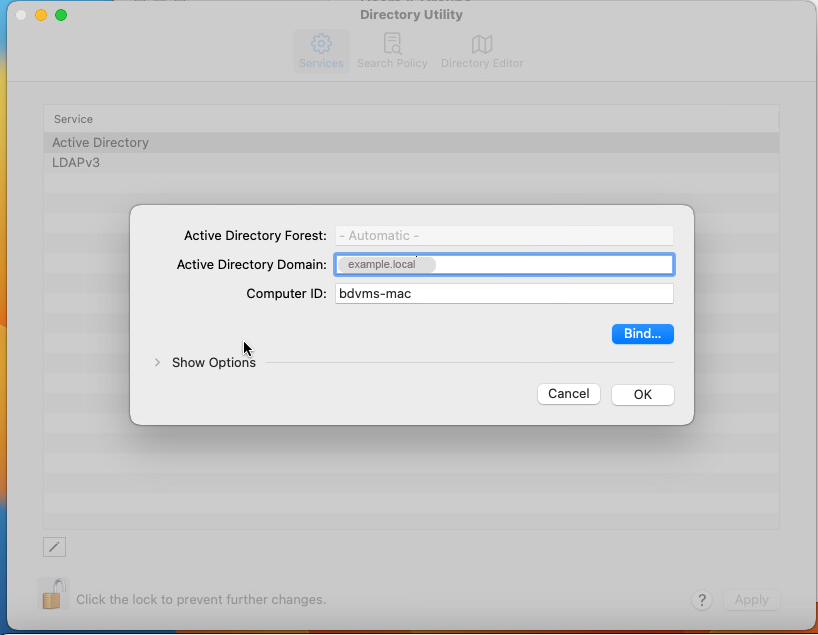
In the Directory Utility re-enter your local Username and Password.
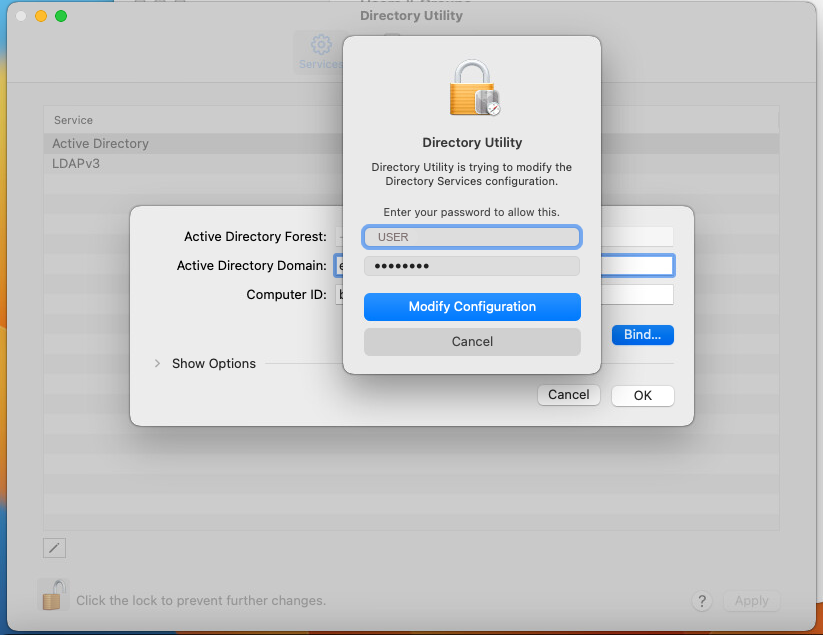
Insert your domain Username and Password.
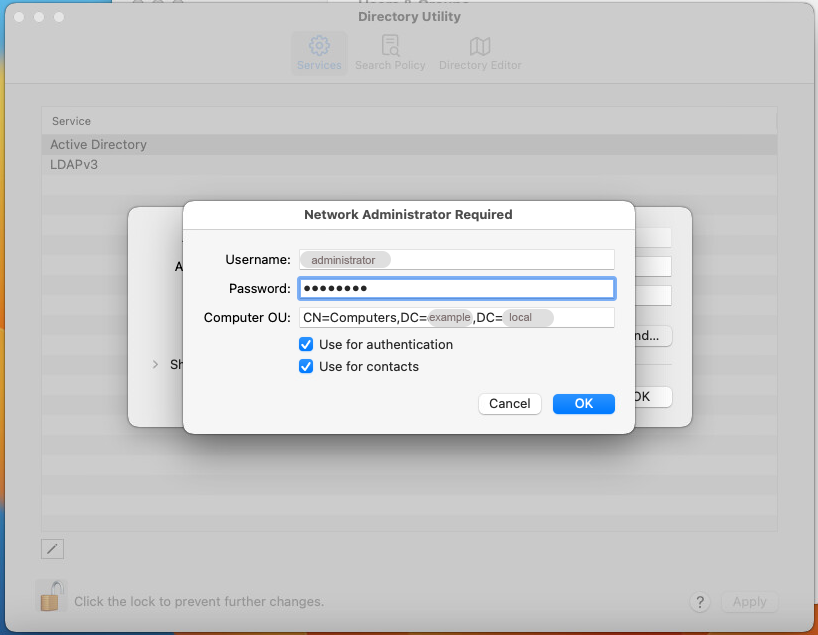
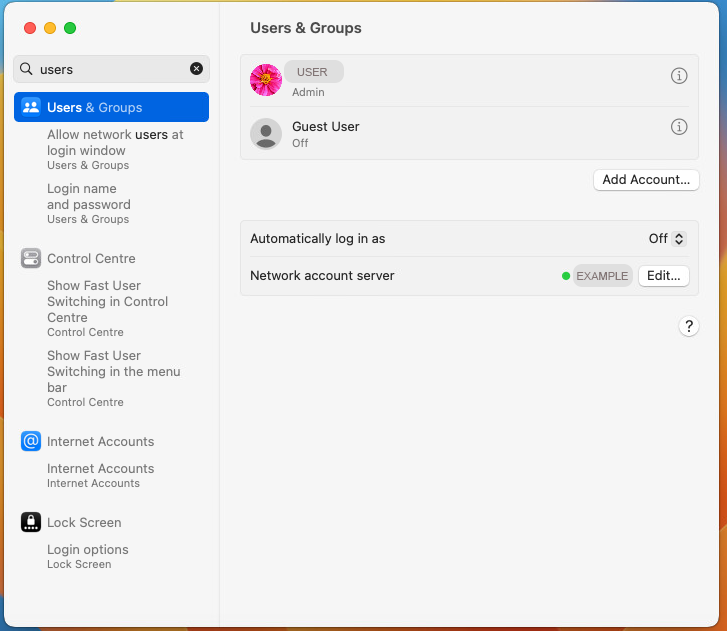
Back in Users & Groups you'll be able to check if your endpoint has successfully joined the Active Directory.
Important
If your endpoint name contains a hyphen, you might not be able to bind to a directory domain such as LDAP or Active Directory.
To establish binding, use a endpoint name that does not contain a hyphen.