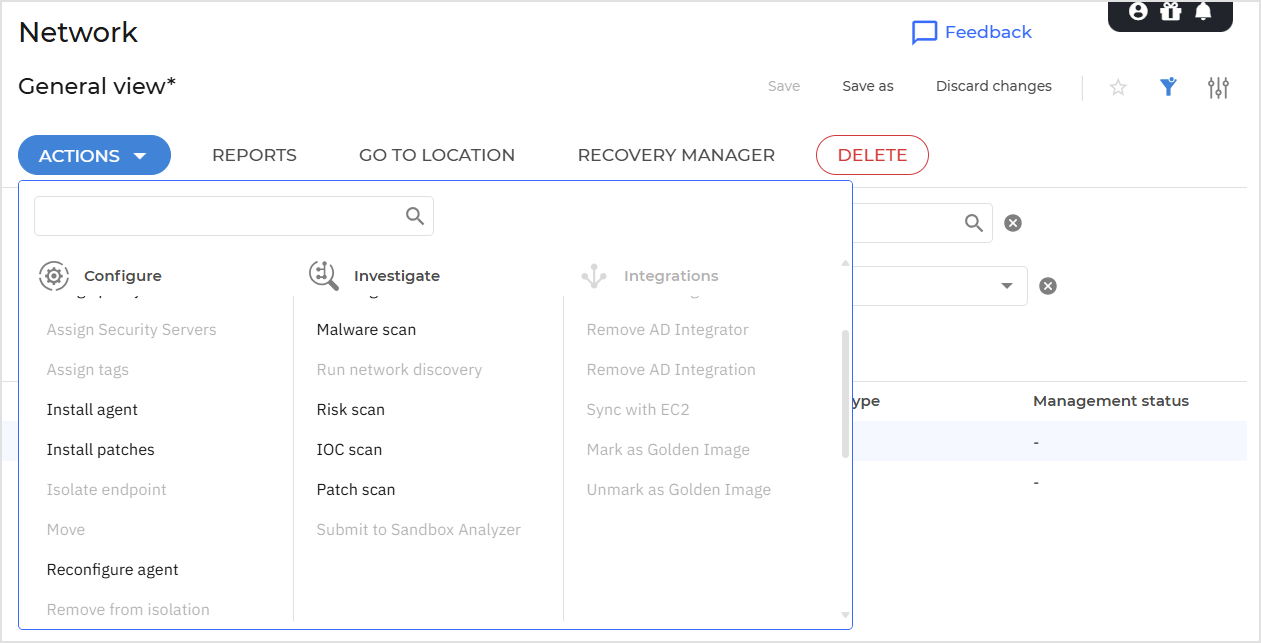
Using actions
Using actions
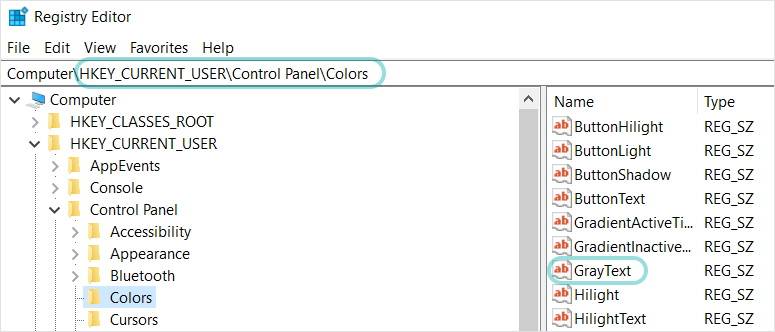
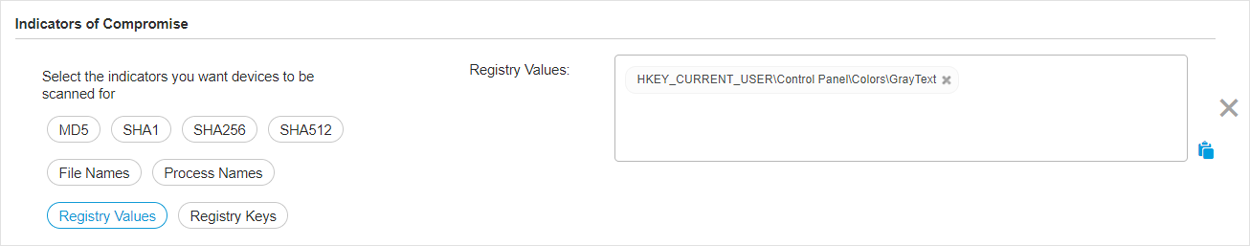
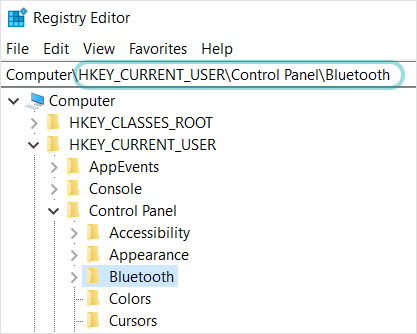
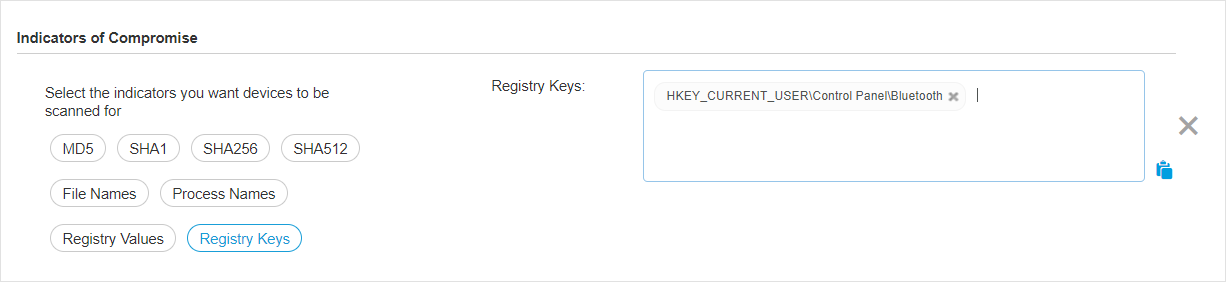
Malware scan
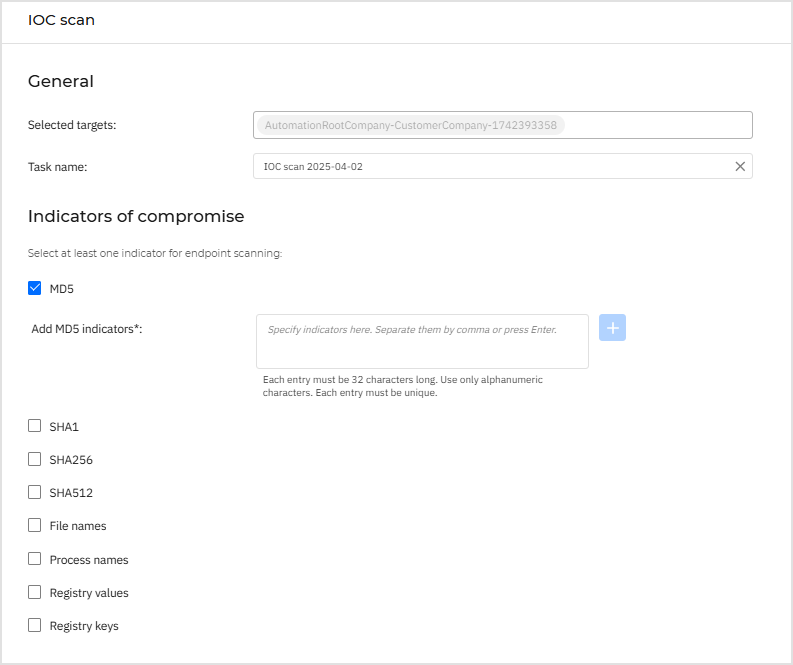
IOC scan
Risk scan
Exchange scan
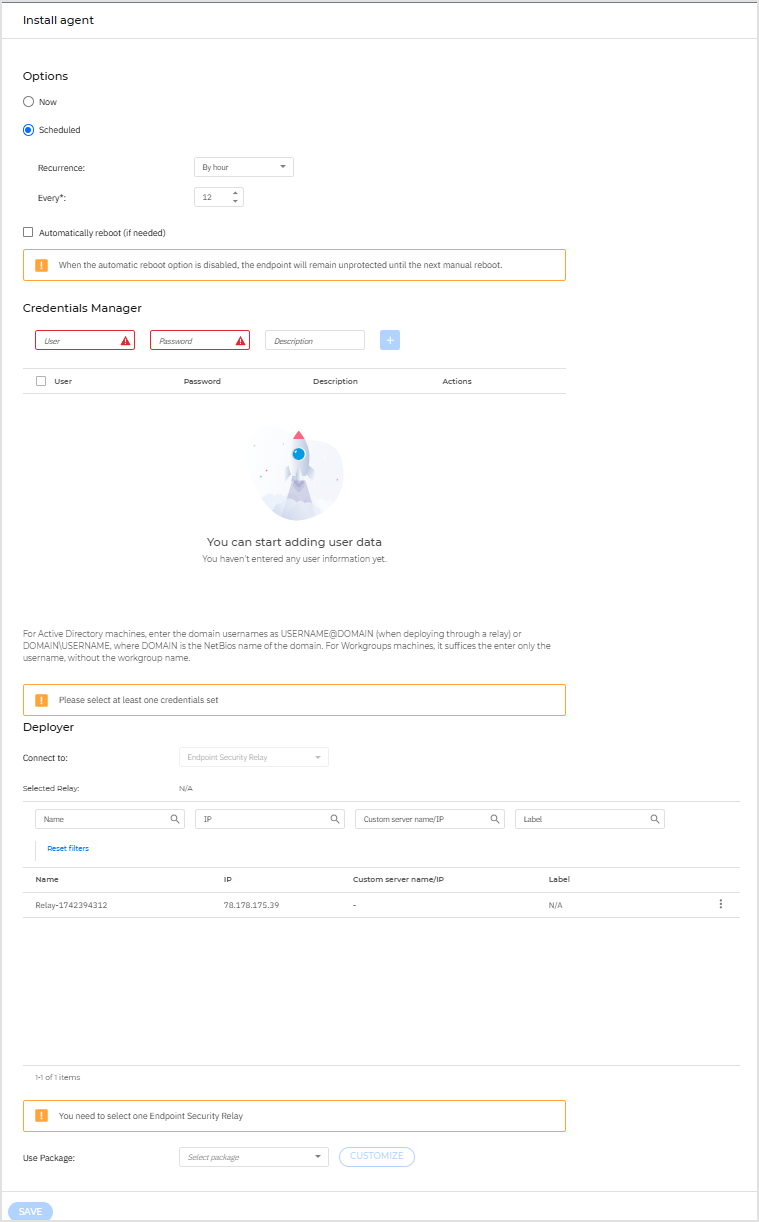
Install agent
Intermediary statuses
During execution, the Install agent task follows these steps:
Configure task - Read policy settings and configure the task.
Resolve hostnames to IP addresses - Convert hostnames to IP addresses for efficient network communication.
Determine target OS - Identify each target’s operating system to ensure compatibility with the required installation package.
Validate deployment targets - Verify that each target has the necessary attributes (for example: IP address, OS details). Targets missing mandatory data are excluded.
Initiate parallel task execution - Start a dedicated execution thread for each valid target to allow concurrent deployment.
Execute pre-tasks - Perform preliminary setup steps per target, such as synchronizing the deployment kit.
Download deployment kit - Retrieve the required installation package for each target.
Deploy software - Transfer installation files to the remote host, configure them, and execute the deployment.
Since deployment is time-consuming, the task must continuously report its current state to the GravityZone console to keep the network administrator informed.
Below are the defined intermediary status values:
Status | Code | Description |
|---|---|---|
| 101 | The task can run only five deployments simultaneously. To start additional deployments, it waits for the ongoing ones to complete. |
| 103 | The task starts configuration. |
| 104 | The task has completed configuration. |
| 105 | The task starts resolving target hostnames to IP addresses. |
| 106 | The task has completed resolving target hostnames to IP addresses. |
| 107 | The task starts OS detection. |
| 108 | The task has completed OS detection. |
| 109 | The task starts filtering valid targets. |
| 110 | The task has completed filtering valid targets. |
| 111 | The task starts dispatching deployment jobs on target. |
| 115 | The task starts running pre-tasks on a target. |
| 116 | The task has completed running pre-tasks on a target. |
| 117 | The task starts downloading the deployment kit. |
| 118 | The task has completed downloading the deployment kit. |
| 119 | The task starts agent installation on a target. |
| 198 | Deployment has stopped due to various reasons (for example: communication issues). |
| 199 | The task has finished execution, either successfully or with an error. |
Uninstall agent
Update agent
Upgrade agent
This task is available only when Endpoint Security agent is installed and detected in the network. Bitdefender recommends upgrading from Endpoint Security to Bitdefender Endpoint Security Tools Bitdefender Endpoint Security Tools, for a last-generation endpoint protection.
To easily find the security agents that are not upgraded, you can generate an upgrade status report. For details about how to create reports, refer to Creating reports.
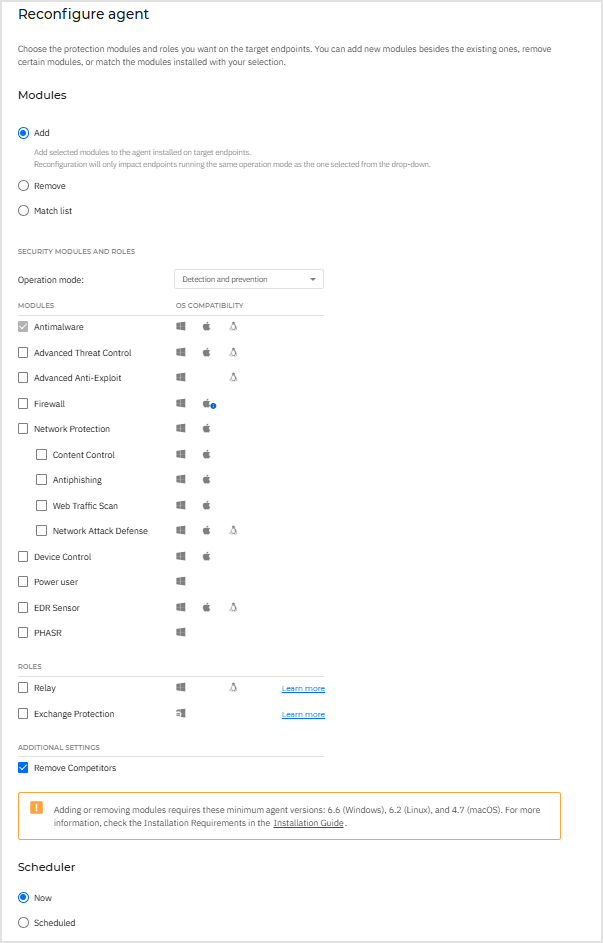
Reconfigure agent
Repair agent
Restart endpoint
Isolate endpoint
Remove from isolation
Suspend endpoint protection
In the Network section, you can manage endpoint security efficiently while maintaining full control over the suspension process.
Note
These actions are supported starting with Windows product version 7.9.20.x, macOS product version 7.20.x, and Linux product version 7.5.0.x.
To suspend endpoint protection follow these steps:
Locate the endpoint for which you want to suspend protection in the Network table.
Select the corresponding checkbox.
Open the Actions menu at the top of the table and select Suspend protection.
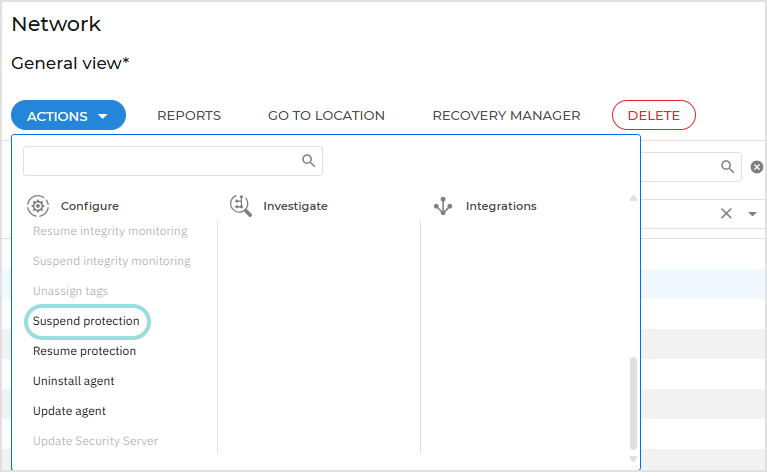
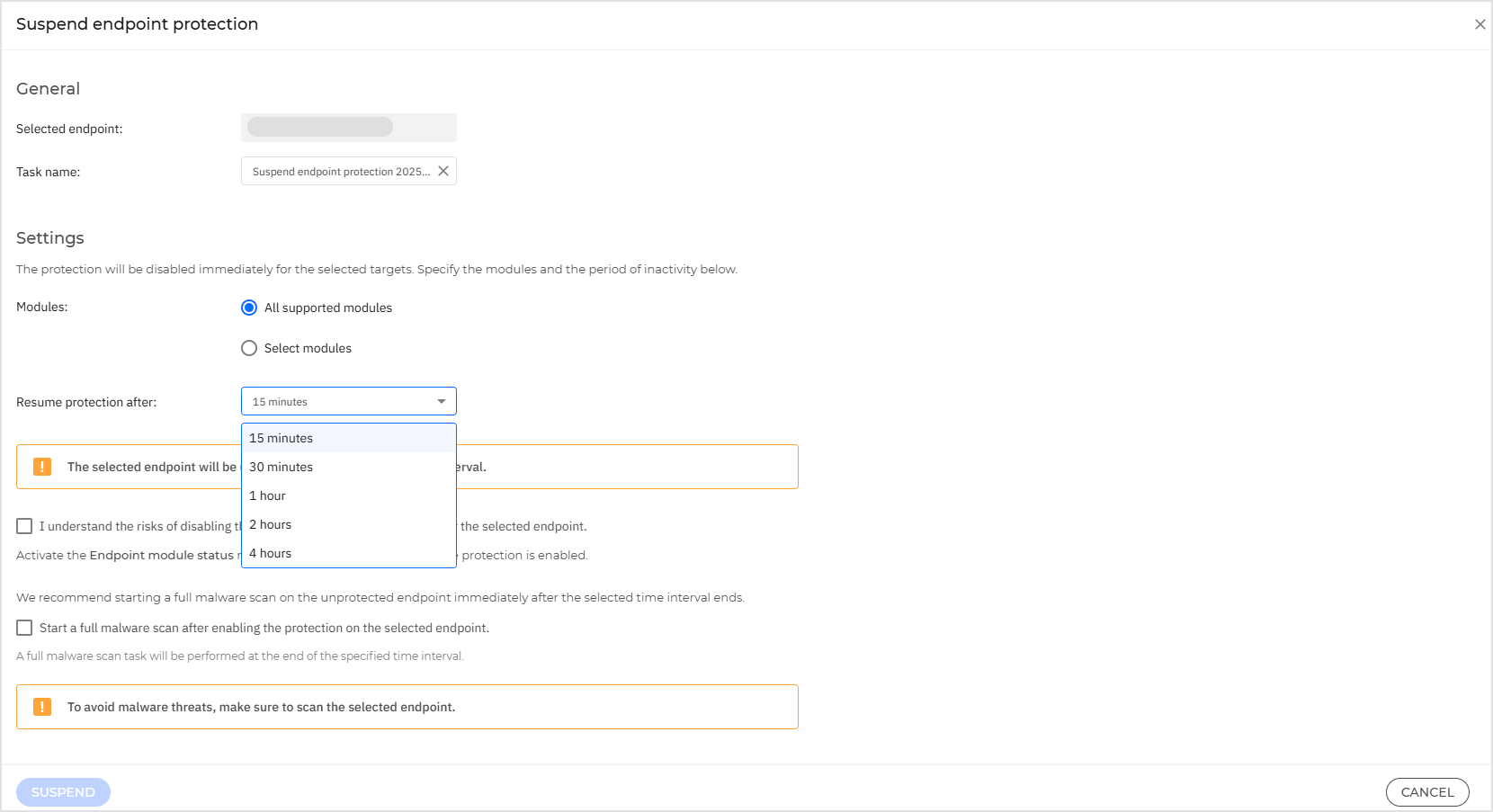
On the configuration page:
Create a task name.
Select the modules that will be suspended.
Select the time interval for the suspend action.
Click Suspend to initiate the task.
Important
The selected endpoint will be unprotected for the specified time interval, therefore we recommend starting a full malware scan on the unprotected endpoint immediately after the selected time interval ends.
On iOS devices, Web Traffic Scan relies on the Antimalware module to function. If Antimalware protection is suspended, Web Traffic Scan will also be disabled automatically until protection is resumed.
PHASR will not function properly, as it relies on the EDR module, which is suspended during this interval. As a result, behavioral data will not be collected during this time.
When troubleshooting, some protection modules cannot be deactivated. These modules are necessary for system integrity and security but do not affect user work.
The following modules are grayed out and cannot be disabled:
Device Control: manages access to external devices like USB drives and external storage. Since it does not interfere with regular operations, disabling it is unnecessary for troubleshooting.
Power User: ensures that only authorized administrators can modify security configurations. Disabling it would not aid in troubleshooting and could compromise security policies.
Full Disk Encryption: protects sensitive data at rest. Turning this off could lead to security risks, and it does not impact normal troubleshooting tasks.
Patch Management: ensures that critical security updates and patches are applied. Since patching runs in the background without disrupting user workflows, it remains enabled.
Resume endpoint protection
To resume endpoint protection follow these steps:
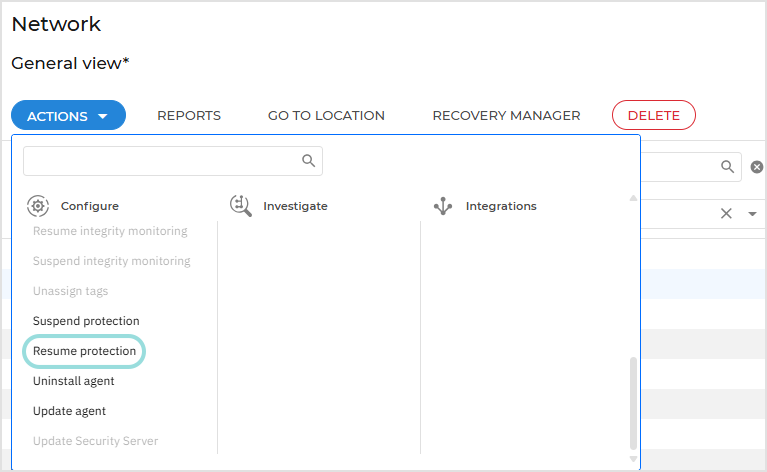
Locate the endpoint for which you want to resume protection in the Network table.
Select the corresponding checkbox.
Open the Actions menu at the top of the table and select Resume protection.
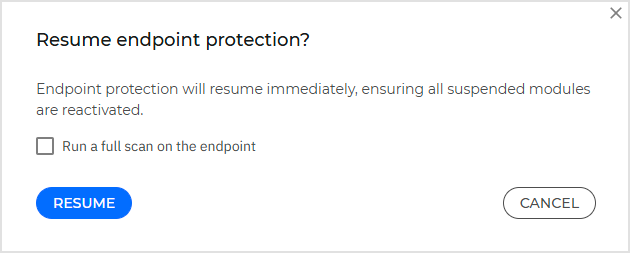
Click Resume to initiate the task.
Important
We recommend starting a full malware scan on the unprotected endpoint when resuming endpoint protection.
Submit to Sandbox Analyzer
At any time, you can remotely send samples to Sandbox Analyzer from any managed endpoint running Windows or Linux.
You can only submit samples from a single endpoint at once.
Note
To submit samples that you store locally on the machine where you access GravityZone Control Center, use the options on the Manual submission page.
Creating the task
To submit a sample from an endpoint in your network, follow these steps:
Log in to GravityZone Control Center.
Go to the Network page in the GravityZone main menu.
Browse your network and select the target endpoint.
Click the Actions menu and select Submit to Sandbox Analyzer.
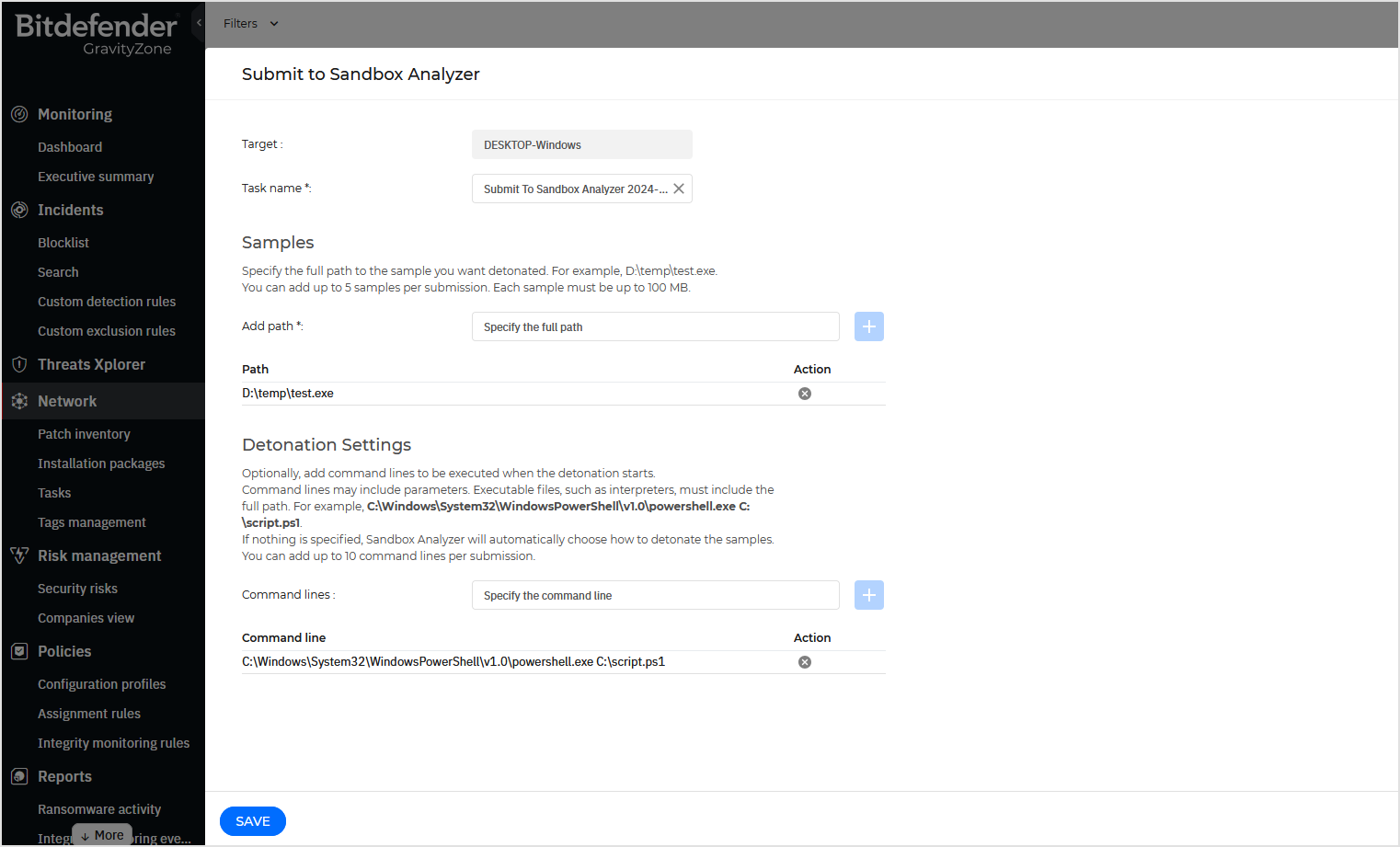
In the configuration window, fill in the following details:
Task name. By default, the task name is Submit to Sandbox Analyzer followed by date. If needed, you can change the name to find it easier on the Network > Tasks page.
The task name supports up to 512 characters.
Path. Specify the full path to the sample you want detonated.
Windows path example:
D:\temp\test.exeLinux path example:
/home/username/bin/scriptYou can add up to 5 samples per submission. Each sample must be up to 100 MB. After each path, click the
 Add button.
Add button.The path requires Windows or Linux format and supports up to 1024 characters.
Sandbox Analyzer supports archives with two levels of nesting.
Note
An easy way to get the full path is to access the Security tab in the Properties window of the sample, on the target endpoint, and copy it from there.
Command line. Optionally, add command lines to be executed when the detonation starts.
Command lines may include parameters. Executable files, such as interpreters, must include the full path.
Windows command line example:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe C:\script.ps1Linux command line example:
/usr/bin/bash /opt/scripts/test.shIf nothing is specified, Sandbox Analyzer will automatically choose how to detonate the samples.
You can add up to 10 command lines per submission. After each command line, click the
 Add button.
Add button.Each command line supports up to 4096 characters.
Click Save.
You can monitor the progress of the created task on the Network > Tasks page, under Submit to Sandbox Analyzer type.
Note
Sandbox Analyzer supports any Unicode characters.
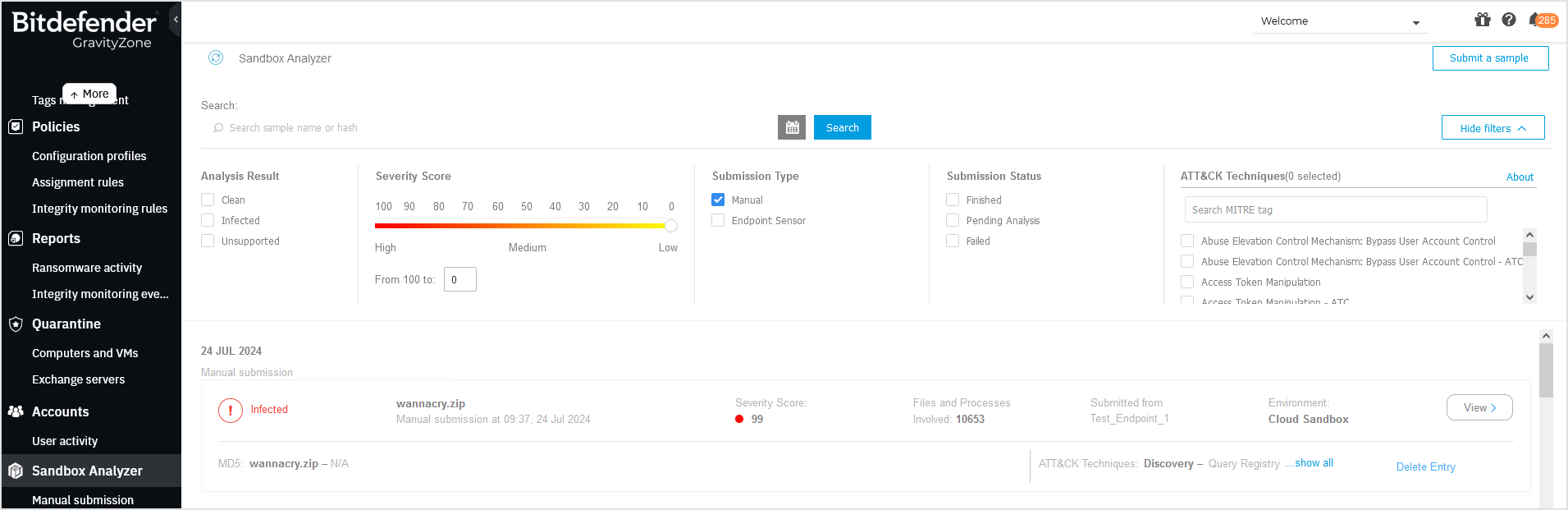
Viewing the results
Sample detonation may take several minutes. When done, you can view the results on the Sandbox Analyzer page in the GravityZone main menu.
Each detonation has dedicated submission card, with the following details:
Submission type: manual.
Verdict: clean, infected, unsupported.
Sample path, as you provided it when creating the task.
Severity score, which indicates the threat level posed by the sample.
Files and process involved, indicated by a number.
Endpoint name, as displayed in your network.
Environment where the detonation had taken place, which is identified as Cloud Sandbox.
MD5 hash.
ATT&CK techniques identified during detonation.
For a more detailed report, click the View button on the right side of the card.
Monitoring user activity
You can review the tasks on the Accounts > User activity page, under Area: Tasks.
Run network discovery
Update Security Server
Change Security Server password
When your Security Server password expires or as a precautionary measure, you can update it from the Network page using the Change Security Server password action.
You can update passwords for multiple Security Servers simultaneously, which is useful in large GravityZone inventories. Although the task will run on all selected Security Servers, it will finish successfully only on those instances that share the same current password. For Security Servers with different current passwords, you must run separate tasks.
Note
This action applies to Security Server Multi-Platform and to Network Sensor Virtual Appliance, available with the XDR feature.
Identify Security Servers requiring a password change
In GravityZone environments with multiple Security Server instances, you can identify those whose passwords have expired and require updating.
To identify Security Servers requiring a password change, follow these steps:
In the GravityZone Control Center left-side menu, go to the Network page.
In the list of smart views from the left-side panel, click Password change required.
This view already includes all necessary filters to show Security Servers with expired passwords.
Alternatively, on the Network page, you can manually set filters as follows:
Entity type - Select Physical machine and Virtual machine.
Pending activity - Select Password change required.
Ensure that the View data recursively option is active.
To view the password details for a specific Security Server:
In the Network table, click the Security Server name.
On the General tab of the details page, locate the Security Server password details section, which includes:
Last password change date
Current password expiry date
Maximum password age (in days)
Note
In environments with multiple Security Servers, they may share the same name or IP address, making them difficult to distinguish on the Network or Tasks pages. To prevent confusion, assign unique hostnames to each instance.
Change the password
After identifying the Security Servers that require updates, follow these steps:
Select the Security Servers in the table.
Click the Actions button at the top of the table and select Change Security Server password under the Configure category.
Alternatively, right-click the selected Security Servers, go to Configure, and then click Change Security Server password.
On the configuration page:
Enter your current Security Server password.
The default password at the installation time is
sve.Note
If you forgot the password, you can reset it. For details, refer to Reset root password for Security Server.
Enter your new password.
The password must be at least 8 characters long and contain at least one digit, one uppercase letter, one lowercase letter, and one special character.
Confirm the new password.
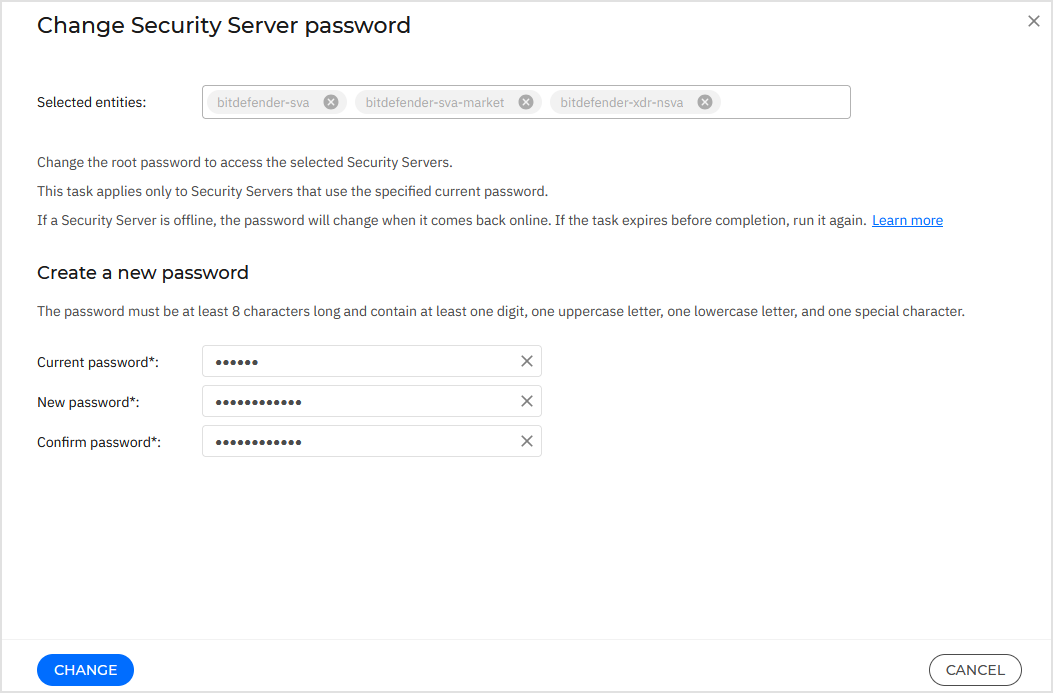
Note
The default password expiration period is 90 days. You can extend this duration or disable password expiration in the Configuration > Security Server settings section in GravityZone Control Center.
Click Change to create the task.
Note
This task applies only to Security Servers that use the specified current password. To update other Security Servers with different passwords, run the task again for those instances.
If a Security Server is offline, the password will change when it comes back online. If the task expires before completion, run it again.
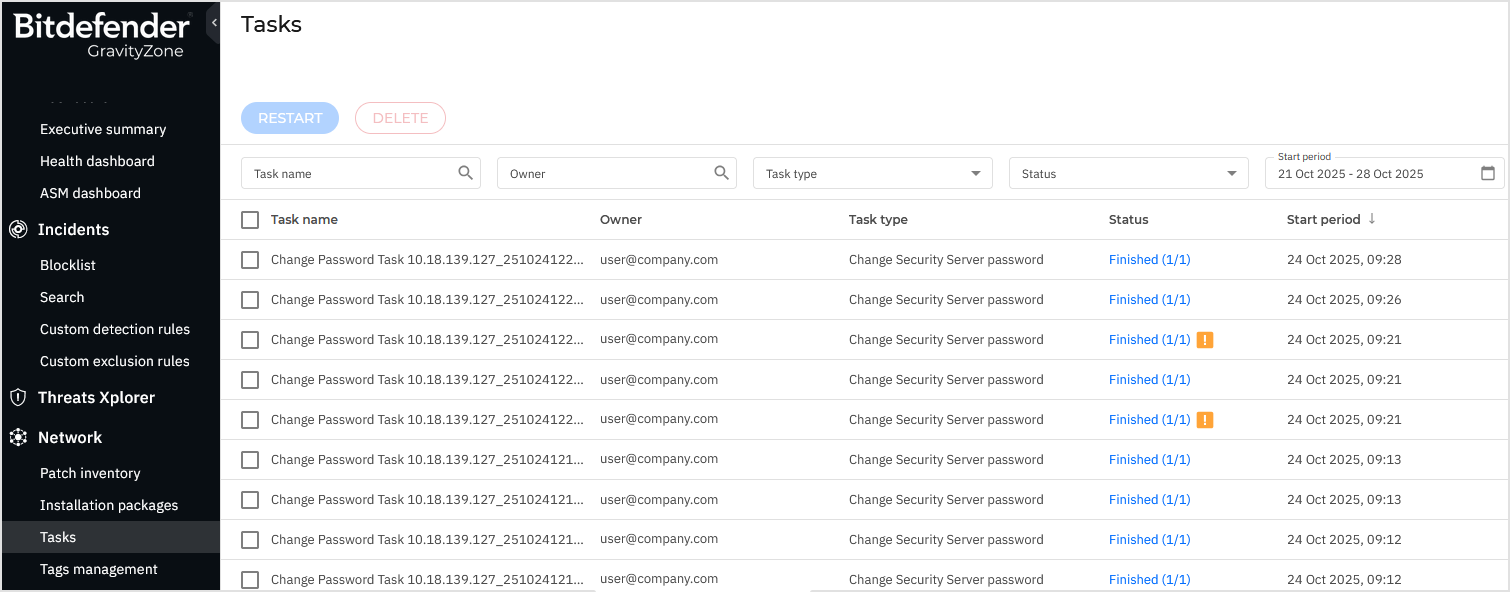
Monitor the task
You can view and manage password change tasks on the Network > Tasks page.
Depending on your environment, the task may take several minutes to complete, as it must communicate with the target Security Servers.
If a task fails, review the error messages and create a new task from the Actions menu on the Network page.
The task cannot be restarted from the Tasks page; instead, you must create a new one from Network.
Monitor user activity
All Security Server password changes are recorded on the User activity page.
To view them:
In the GravityZone Control Center left-side menu, go to the Accounts > User activity page.
Configure the filters as follows:
Action - Select Created.
Area - Select Tasks.
Click Search.
In the results list, click an entry to view details.