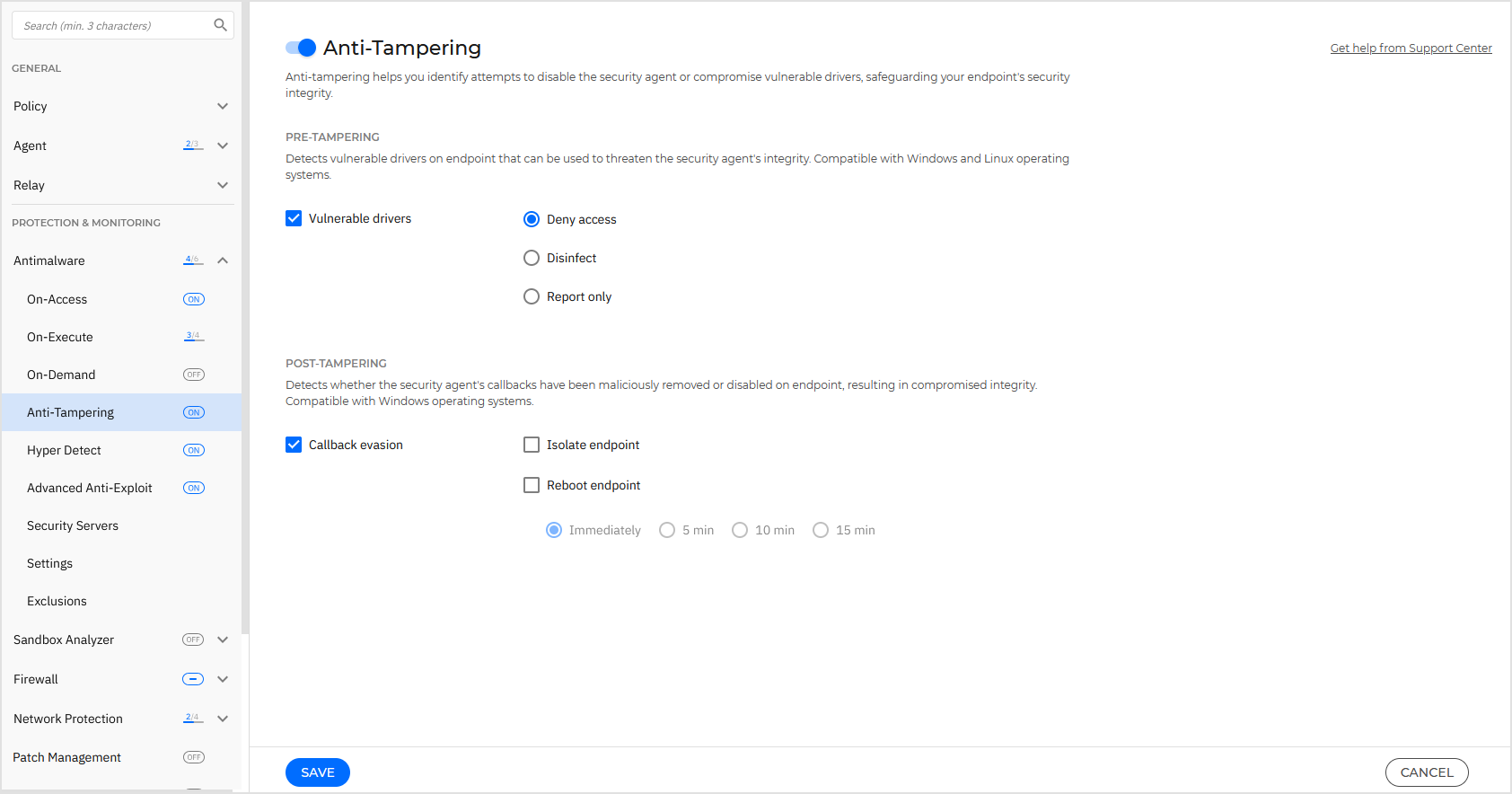
Anti-tampering
Anti-tampering enables you to view when vulnerable drivers are detected on endpoints and when advanced attack attempts are made to disable the security agent, leading to compromised product integrity.
The settings are available in the Antimalware > Anti-Tampering section of the policy.
The feature capabilities are divided in two main categories with distinct targets:
Vulnerable drivers
This pre-tampering technology detects vulnerable drivers on endpoints that can be exploited by attackers, posing threats to the integrity of the product. The technology is compatible with Windows operating systems.
Callback evasion
Callback functions generally trigger specific actions in response to security events or certain conditions. New threats or unintentional human error could be engineered to potentially allow unauthorized access to the kernel, leading to compromised product integrity. This post-tampering technology can detect when the security agent callback functions have been maliciously removed or disabled. The technology is compatible with Windows operating systems.
To enable and configure the module follow the steps below:
Click the toggle to enable the Anti-tampering module.
Callback evasion and Vulnerable drivers technologies are selected by default when enabling Anti-tampering, however, you can enable or disable them according to your needs.
Customize the remediation actions:
For Vulnerable drivers, you can select one action:
Deny access: This default action denies access to vulnerable drivers.
Remediate: Remediate the vulnerable drivers by disinfecting them.
Report only: Only report the vulnerable drivers.
For Callback evasion, you can select multiple actions:
The default action is Report only and is enabled when selecting the Callback evasion checkbox.
Isolate: Isolate endpoints to contain the spreading of potentially malicious activities.
Reboot: Reboot the endpoints to try and restore the security agent integrity. You can select a time interval after which the endpoints automatically reboot.
Save your changes.
You can view Anti-tampering events in the Threats Xplorer section using the dedicated module, technology, or threat type filters.