Protecting against malware
Bitdefender Endpoint Security Tools informs you about existing security issues to help you easily protect your Mac against malware.
You can scan your Mac or specific files or folders only.
Infected files that cannot be cleaned are moved to quarantine automatically so that they can be restored and cleaned at a later time.
Regular updates allow Bitdefender Endpoint Security Tools to detect and remove the latest malware discovered.
Scanning your Mac
The On-Access module continuously monitors your computer, looking for malware-like actions and prevents new malware threats from entering your system. On-Access is controlled by your network administrator via security policies.
You can also scan your Mac or specific files anytime you want.
These scan types are available with Bitdefender Endpoint Security Tools:
Quick Scan - checks for malware the most vulnerable locations on your system (for example, the folders that contain the documents, downloads, mail downloads and temporary files of each user).
Full Scan - performs a comprehensive check for malware of the entire system.
All connected mounts will be scanned too.
Note
Depending on the size of your hard disk, scanning the entire system may take a while (up to an hour or even more).
For improved performance, it is recommended not to run this task while performing other resource-intensive tasks (such as video editing).
You can also run a quick scan or a full scan by using the productConfigurationTool interface. For details, refer to Using the command line tool.
Custom Scan - helps you check specific files, folders or volumes for malware.
By default, the application checks for update before starting the custom scan.
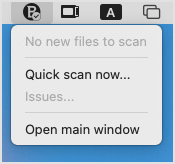
To start a quick scan, follow these steps:
Click the Bitdefender Endpoint Security Tools icon on the right-side of the menu bar.
In the menu, select Quick scan now...
The scan starts and you can view the progress the application's main window.
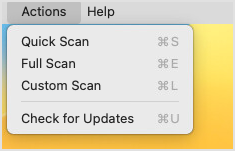
To start a more comprehensive scan, follow these steps:
Open Bitdefender Endpoint Security Tools.
Go to the Actions menu and select any option you want: Quick Scan, Full Scan, Custom Scan.
Alternately, use these shortcuts:
Command-S for Quick Scan.
Command-E for Full Scan
Command-L for Custom Scan.
The scan starts and you can view the progress the application's main window. You can cancel the scan at any time.
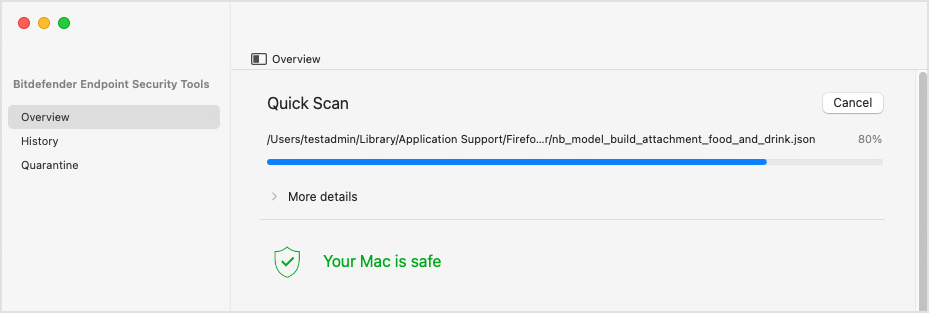
Wait for Bitdefender Endpoint Security Tools to finish scanning. The scan may take a while, depending on its complexity.
Checking scan logs
Scan logs provide useful information on the scan that is available in the History page.
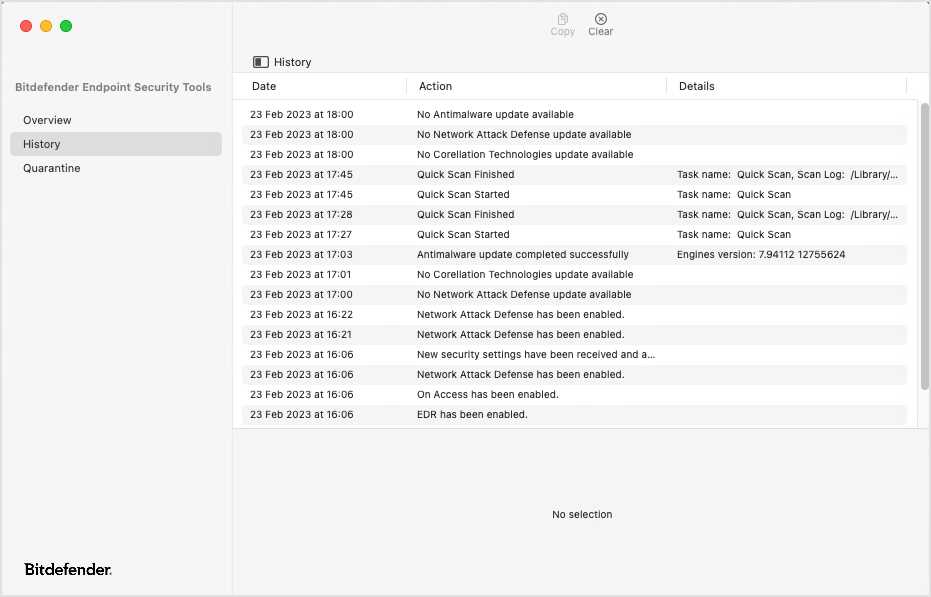
You can see the scan statistics, the resolved items and the action taken on them, and the unresolved items.
Click the column headers to sort items by date, actions, and details. Click each event to also view the related information at the bottom of the page.
Click the buttons at the top of the page to take the following actions:
Copy - select one or multiple items (using the
Shiftkey) and click to copy them to clipboard.Clear - click to delete all items in the list.
Fixing issues
Bitdefender Endpoint Security Tools for Mac automatically detects and informs you about a series of issues that can affect the security of your system and data.
The detected issues may refer to:
New security content and product updates have not been downloaded from Bitdefender servers.
Security threats have been detected on your system.
Certain modules are disabled.
System extensions are blocked.
BDLDaemon requires proxy configuration.
The application files require full disk access.
License has expired.
Fixing the issues indicated by Bitdefender Endpoint Security Tools is a quick and easy process. This way you can to fix security risks in a timely manner.
To check and fix detected issues:
Click the Bitdefender Endpoint Security Tools icon in the menu bar and select Issues... or Open main window.
If the Issues... option is disabled, it means no issues have been detected. No further action from you is required.

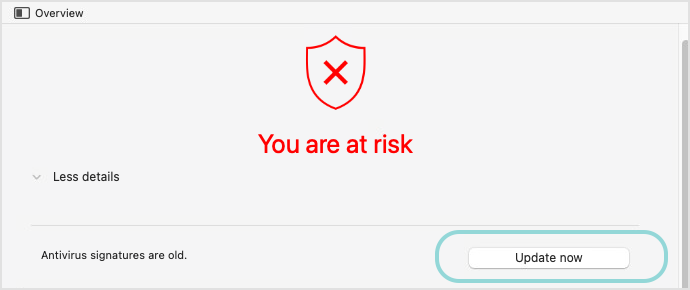
After opening the main window, check the color of the status area:
Green - Your Mac is safe.
Red - You are at risk. For further investigations, follow the next steps.
Click the More details option to check the description.
Depending on the number and type of the detected issues, a button may be available in the status area, such as Update now, if you need to download updates for Bitdefender Endpoint Security Tools.
When the application files require certain privileges, you are prompted by dialog windows to make the necessary changes in the system settings.
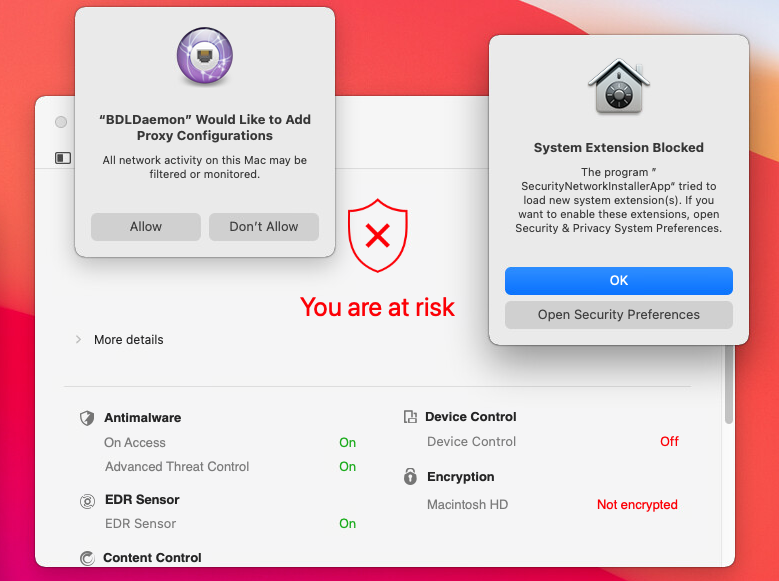
If malware has been detected, the application automatically attempts to remove it and to reconstruct the original file. This operation is referred to as disinfection. Files that cannot be disinfected are moved to quarantine to contain the infection.
If the file can neither be disinfected, nor quarantined, Bitdefender Endpoint Security Tools informs you about the issue and you can manually delete it.
Some issues may require your network administrator to solve them from the management console, such as:
Enabling the On-Access module via security policy.
Renewing the expired license.
Managing items in quarantine
Bitdefender Endpoint Security Tools allows isolating the infected or suspicious files in a secure area named quarantine.
When a malicious app is in quarantine it cannot do any harm because it cannot be executed or read.
To view and manage the quarantined files, go to the Quarantine page from the left side menu in the Bitdefender Endpoint Security Tools main window. To access the Quarantine, click the  Expand button in the main window, or click the Quarantine option in the Bitdefender Endpoint Security Tools menu in the Mac menu bar.
Expand button in the main window, or click the Quarantine option in the Bitdefender Endpoint Security Tools menu in the Mac menu bar.
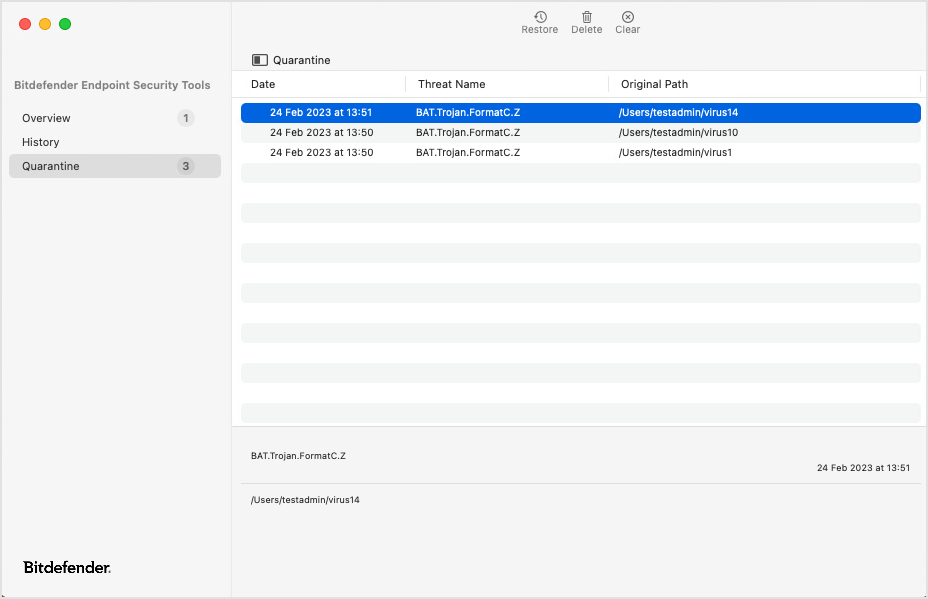
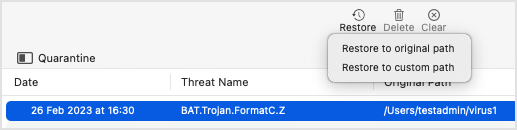
The Quarantine page displays all the files currently isolated in the Quarantine folder.
Click the column headers to sort items by date, threat name, and original path.
Click the buttons at the top of the page to take following actions:
Restore - select one or more items (using the Shift key) and click to restore them to the original path or to a custom path.
Delete - select one or more items (using the Shift key) and click to permanently remove them from the quarantine.
Clear - click to empty the entire quarantine.