Identities
The Identities tab provides an overview of different identity types: users, roles, groups, and service accounts:
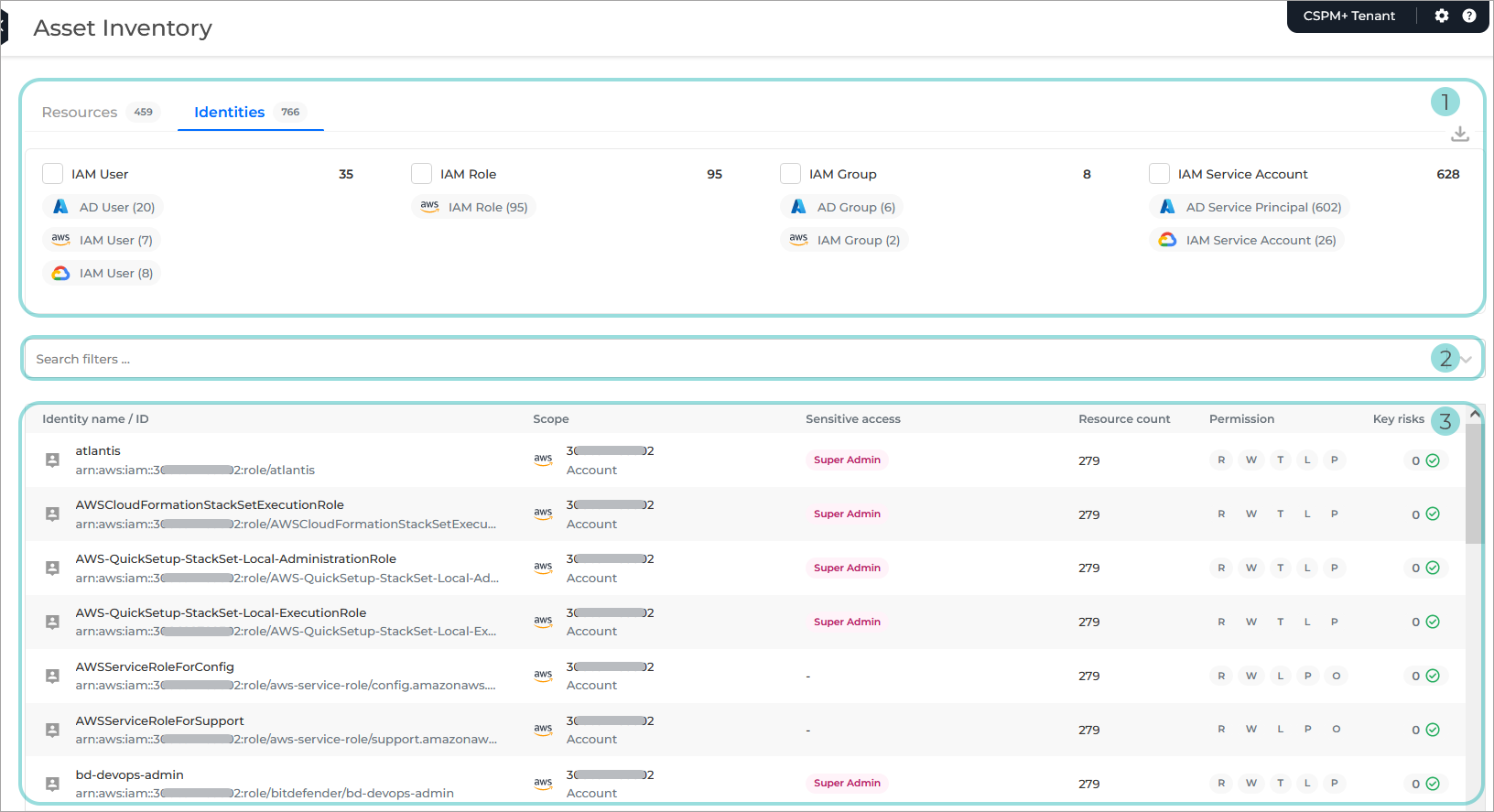
Identities overview. An aggregated count of identities grouped per identity type.
Note
Each column indicates the number of identities per identity type, and you can use the filter option to customize the information listed in the table below.
The following columns and filters are available:
IAM User
IAM Role
IAM Group
IAM Service Account
If you apply the filtering option to one or more columns, the data is automatically populated in the search filter and the identities list is automatically refreshed according to your selection. You can further customize and refine your search by removing some of the pre-selected options from each column.
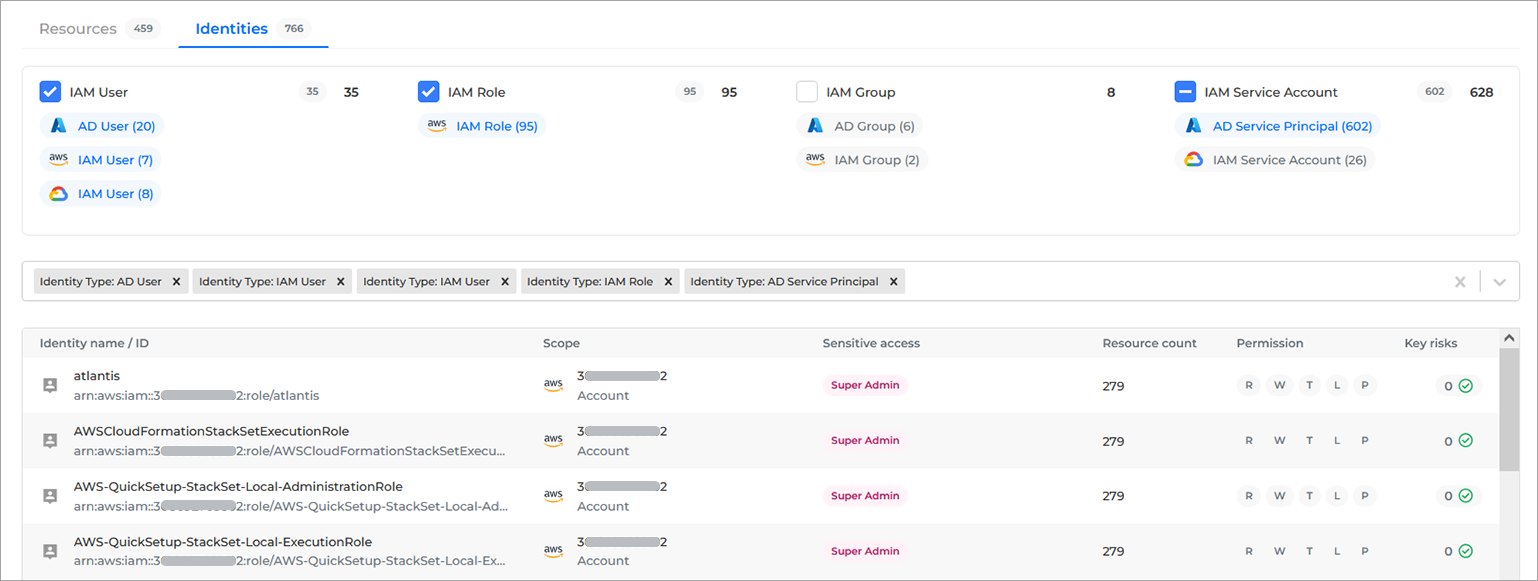
Search filter. With this filtering option, you can apply one or multiple filters to the identities list. The following options are available in the drop-down:
Identity ID
Identity name
Identity status
Identity type
Provider
Scan account
Scan group
Sensitive access
The search filter drop-down can be used as a standalone customization option or, in conjunction with the columns above the search filter.
Identities list. This section displays the current list of identities that have been detected across your cloud devices and used to gather data. It contains the following columns:
Identity name / ID
Scope
Sensitive access
Resource count
Permission
Risk findings
Identity Details
By clicking on any row from each column, you can display the Identity Details panel, where you have access to the following details:
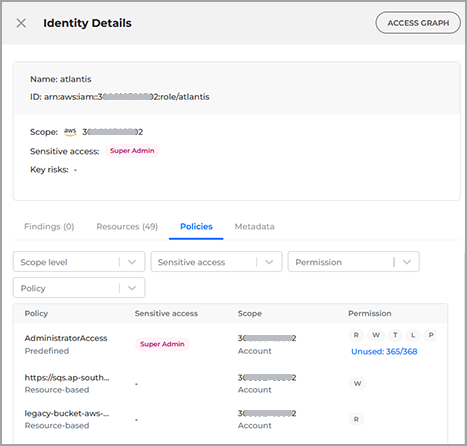
Access graph button
Name
ID
Scope
Sensitive access
Key risks
The Key risks you may see listed in the details panel are:
Key risk | Definition |
|---|---|
Access Key Found (AWS) | Access key found on an AWS root account. |
MFA Not Enabled (AWS, GCP, Azure) | MFA is not enabled for this identity (only for identity with console access). |
Unused Identity (AWS, GCP) | Identity has not been used at all since it was created. |
Inactive Identity (AWS, GCP) | Identity has not been used in over 90 days. |
Password Update Required (AWS, Azure) | Password was last updated over 90 days (only for identity with password assigned and able to log in to the cloud console). |
Key Rotation Required (AWS, Azure) | Access key last rotated over 90 days (only for identity with access key assigned). |
The lower half of the Identity Details panel, includes the following:
Findings
Resources
Resource type
Permission
Policies with the following columns and available filters:
Policy
Predefined
Custom
Identity-based
Resource-based
Sensitive access
Root User
Super Admin
IAM Admin
Scope
Organization
Folder
Project
Account
Subscription
Permission
Read (R)
Write (W)
Tagging (T)
List (L)
Permissions (P)
Others (O)
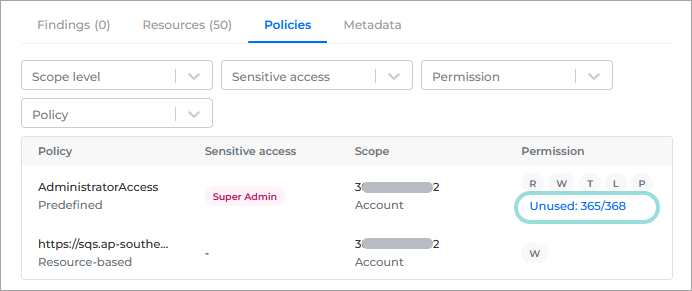
If there are any permissions that are assigned to the identity, but are not used, a link is displayed under the link of permissions.
The links displays the number of unused services and the total number of services assigned to the identity. Click the link to display the Unused permissions window.
Metadata
Access Graph
The Access Graph button offers a granular view of the access path from identities to resources for cloud infrastructure in your cloud environment. The graph is automatically updated with every scan. There are no additional setup steps required.
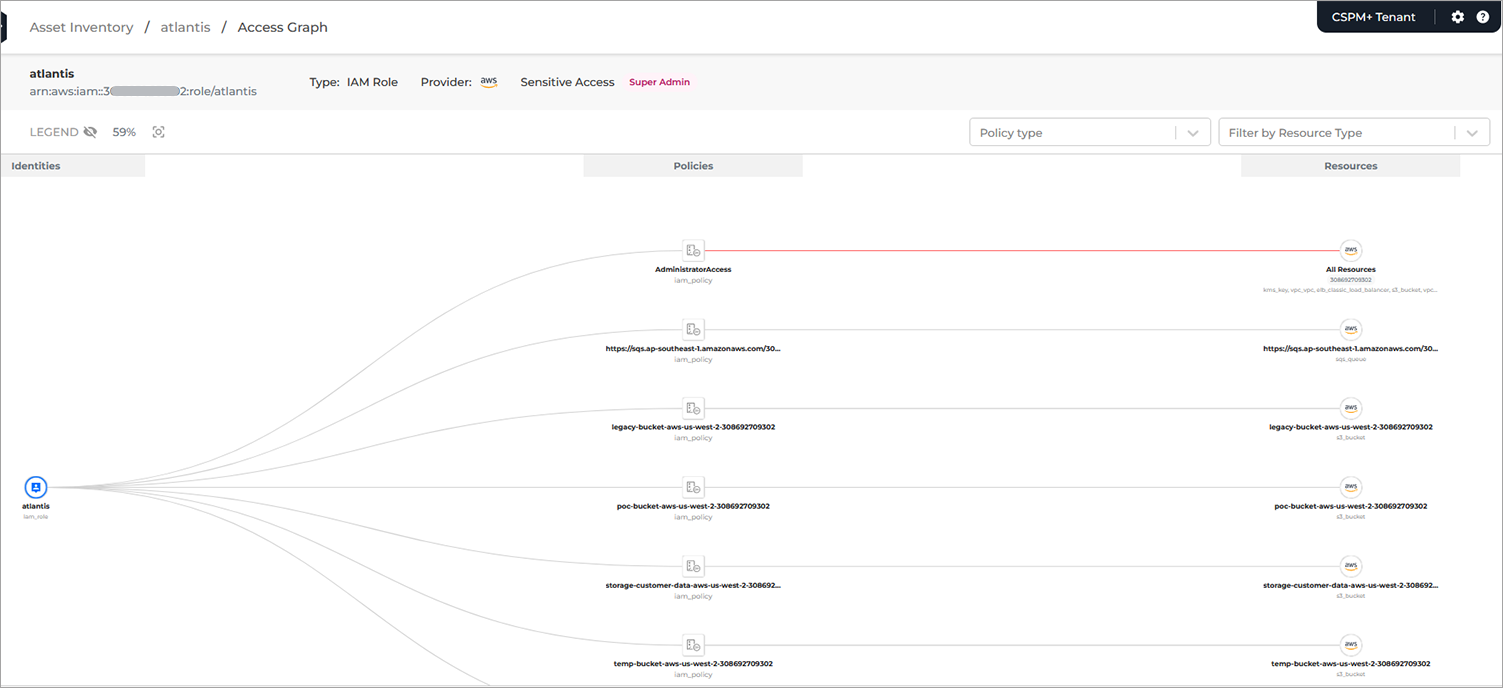
By default, the graph is zoomed out to show all resources and identities in the graph. The percentage to which it's zoomed out or in, can be found next to the legend which can also be viewed by clicking the eye icon next to it. Zooming in allows a closer inspection of the graph.
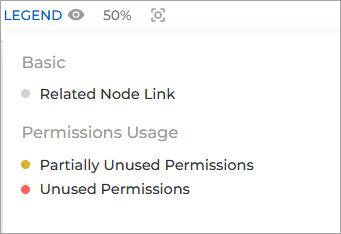
By clicking on each individual node you can display its details on the side panel. It will also highlight its connecting paths in the graph.
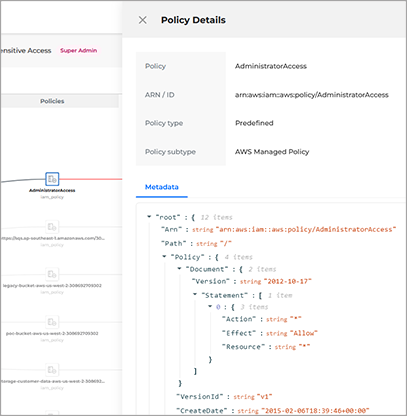
You can find a list of all Access Graph components here.
Unused permissions
Note
This feature is currently available only for AWS accounts.
To access and view the unused permissions, follow these steps:
Navigate to Asset Inventory > Identities.
Select an identity from the list and display the Identity Details panel.
From the Identity Details panel, click the Policies tab.
Under Permissions column, click the link associated to that row.
Note
The link is displayed only if there are unused permissions.
This new window provides you with additional information regarding the permissions assigned to a specific identity.
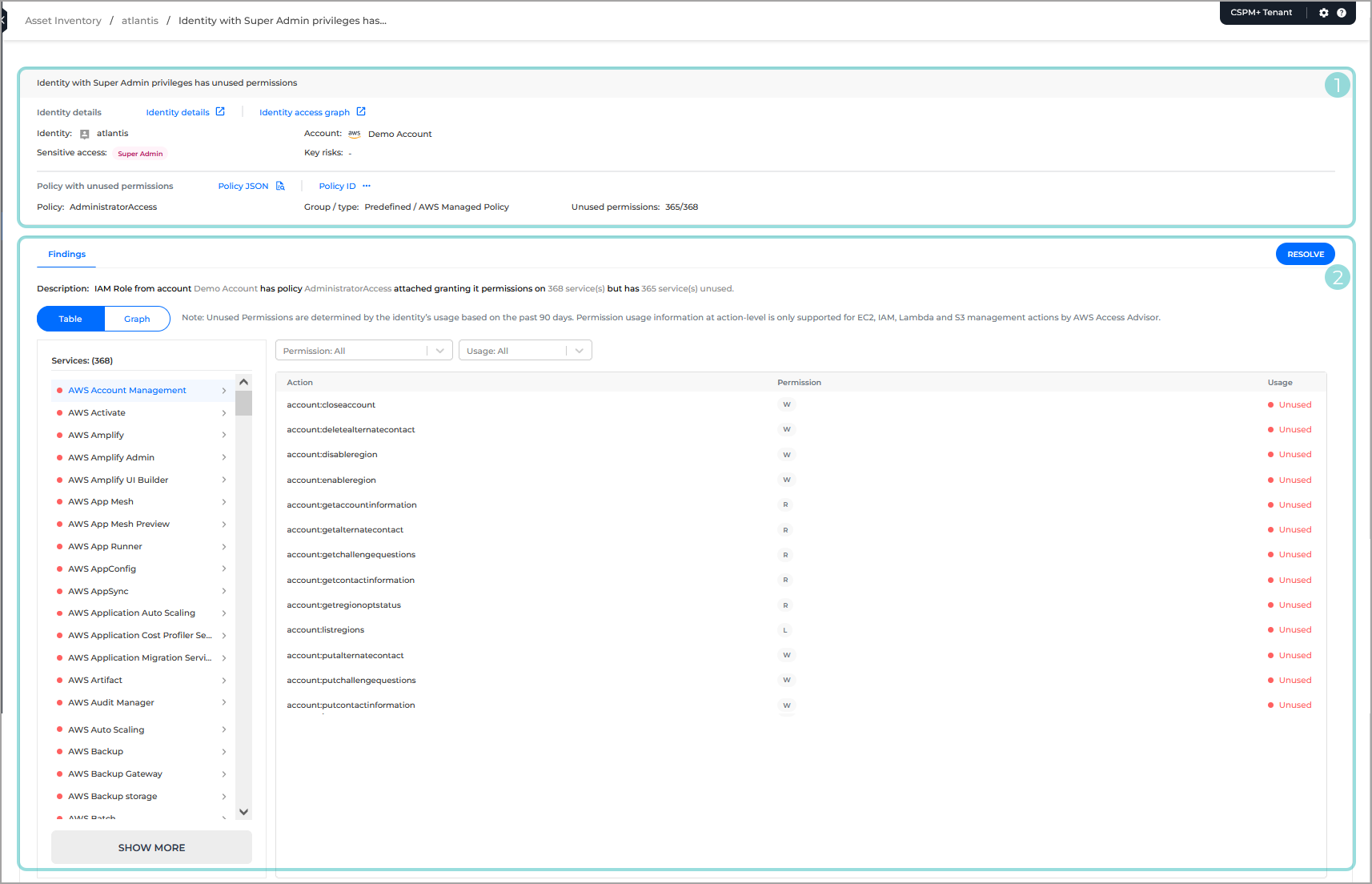
Identity information - this section provides general information regarding the identity, and is contains two subsections:
Identity details - this section provides you with the following information:
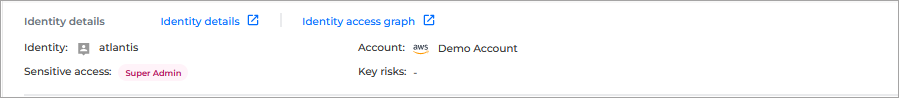
Identity - the name of the identity.
Sensitive access - highlights privileged access associated to the identity.
Super Admin - access to take any action to any resources/services
IAM Admin - permission to access control management
Root user - unrestricted access (cloud account's owner)
Account - the cloud account the identity belongs to.
Key risks - the key risks associated to the identity.
The section also provides links to the Identity Details and Access Graph pages.
Policy with unused permissions - this section provides you with the following information:
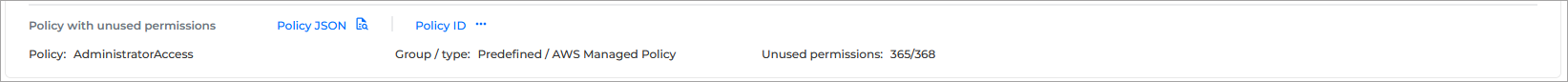
Policy - the name of the policy that the permissions are associated with.
Group / type - the group and type of the policy.
Unused permissions - the number of unused and total permissions.
This section also provides links to Policy JSON, which provides metadata information, and Policy ID, which displays the full ID of the policy.
Findings - this sections provides a list of findings that indicate what permissions have been found for this identity.
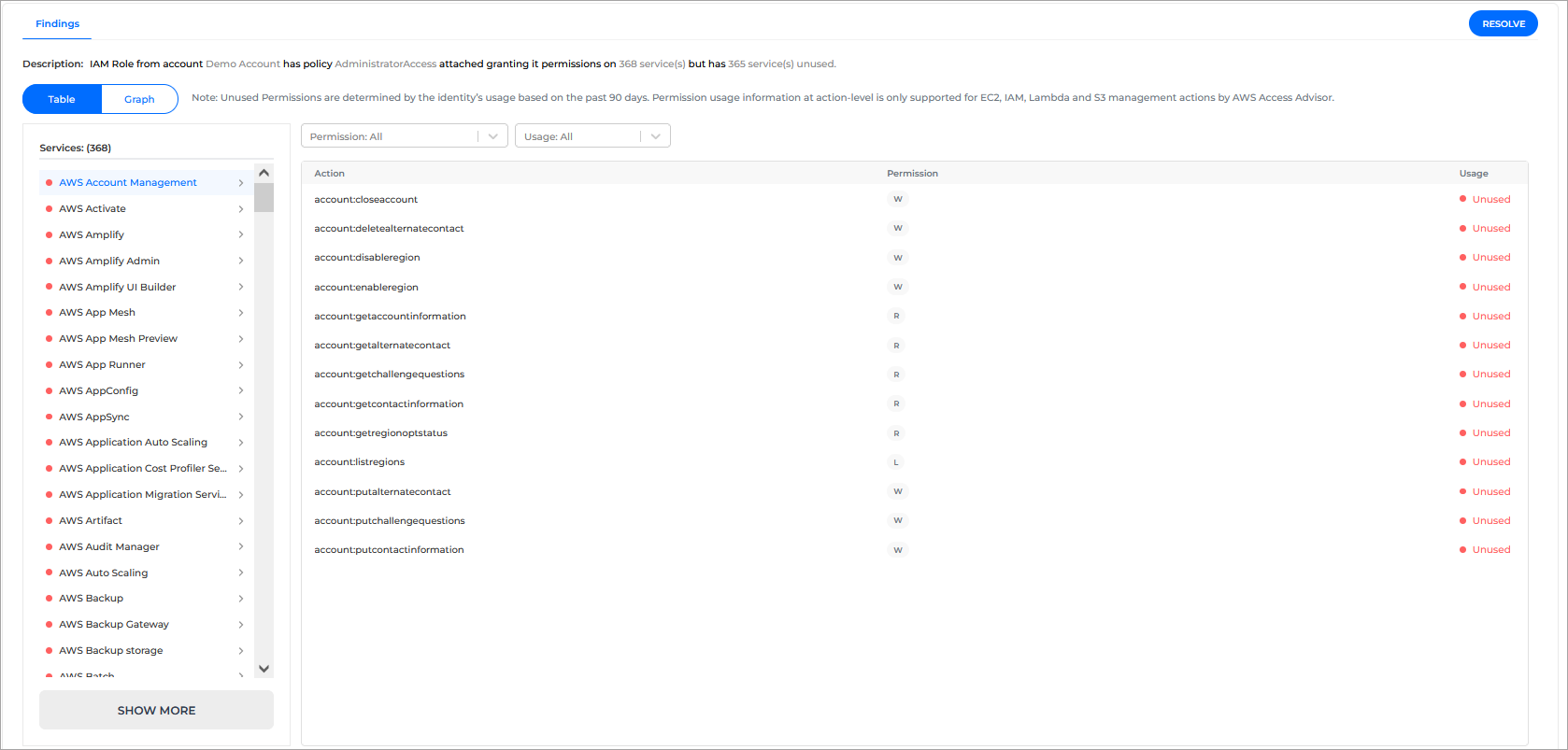
Description - this section provides a short description of the identity and the associated permissions.
Resolve button - this option displays the Resolve pane, which provide you with options on how to resolve the findings displayed on the page.
Table / Graph button - this toggle allows you to switch the findings view between a table or a graphical representation.
Services - this section provides a list of all services associated to the identity. Each one is marked with a color code:
Green - All permissions associated to the service have been used in the last 90 days.
Red - None of the permissions associated to the service have been used in the last 90 days.
Yellow - Some of the permissions associated to the service have been used in the last 90 days.
Clicking on a service provides information on all associated permissions in the Action section.
The grid next to the Services section provides information about the permissions associated to a specific service, and can be customized with the help of the two available filters:
Permissions
Usage
Export data
To export the data currently displayed in the Identities page, click the Export button on the top of the Identities overview section.
The information is downloaded in a .CSV file.