Getting started
Bitdefender Endpoint Security Tools is a fully automated computer security program, managed remotely by your network administrator. After installation, it protects you against malware (such as viruses, spyware and Trojans), network attacks, phishing and data theft. It can also be used to enforce your organization's computer and internet use policies. Bitdefender Endpoint Security Tools makes most security-related decisions for you and displays pop-up alerts. Details of actions taken and information about program operation are available in the Events window.
Important
As of version 7.9.29.589, the new BEST UI is only supported on endpoints running Windows 10 version 1809 or later, or Windows Server 2019 version 1809 or later.
The System Tray icon
During the installation process, Bitdefender Endpoint Security Tools places an icon  in the system tray. If you double-click this icon, the main window is displayed. If you right-click the icon, a contextual menu provides the following options:
in the system tray. If you double-click this icon, the main window is displayed. If you right-click the icon, a contextual menu provides the following options:
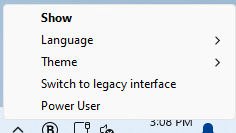
Show - opens the main window of Bitdefender Endpoint Security Tools.
Language - sets the language for the user interface.
Theme – allows you to switch between dark, light, and the system theme.
Switch to legacy interface – provides access to the legacy interface.
Power User - provides access to security settings, after you log in. Control Center is notified whenever an endpoint is in Power User mode and the Control Center administrator can always overwrite local security settings.
Important
This option is available only when a network administrator enables it through policy settings, and it is not available for Bitdefender Endpoint Security Tools for Windows Legacy.
The Bitdefender Endpoint Security Tools icon in the system tray informs you when issues affect your computer, by changing its design:
 Critical issues affect the security of the system.
Critical issues affect the security of the system. Non-critical issues affect the security of the system.
Non-critical issues affect the security of the system.
Note
The network administrator can choose to hide the system tray icon.
The system tray icon is not available when using the EDR standalone protection model.
The Overview window
The Overview window of Bitdefender Endpoint Security Tools is where you check the protection status and perform scan tasks. Everything is just a few clicks away. Protection configuration and management are performed remotely by your network administrator.
To access the main interface of Bitdefender Endpoint Security Tools, navigate from the Windows Start menu, through Start > All Programs > Bitdefender Endpoint Security Tools or double-click the Bitdefender Endpoint Security Tools  icon in the system tray.
icon in the system tray.
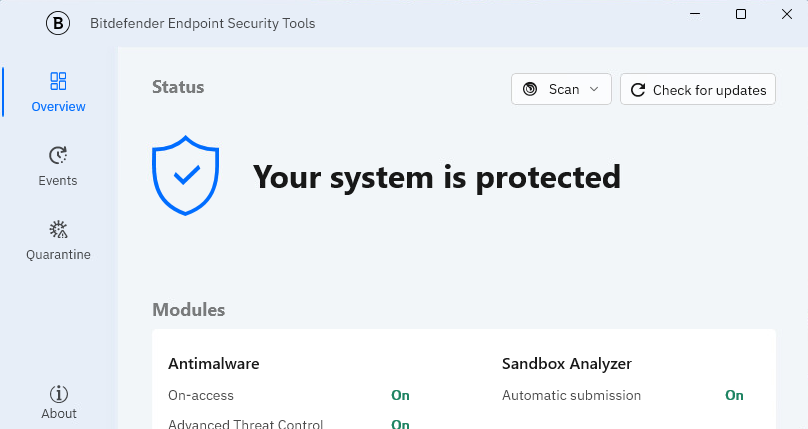
The window is organized into the following areas:
Actions
Status
Issues
Tasks
Policy name (if enabled by your system administrator)
Modules
Actions area
This area allows you to run a scan task or check for product updates.
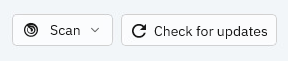
The following scan tasks are available:
Quick scan - checks the
%windir%\system32and%TEMP%folders to detect malware threatening the endpoint. A Quick scan is usually completed faster and uses fewer local system resources than a Full scan.Full scan - checks the entire endpoint for all types of malware threatening its security, such as viruses, spyware, adware, rootkits and others.
For more information on scan tasks, refer to Scanning for malware.
For more information about product updates, refer to Updating the security agent.
Status area
The Status area offers useful information regarding the security of the system.
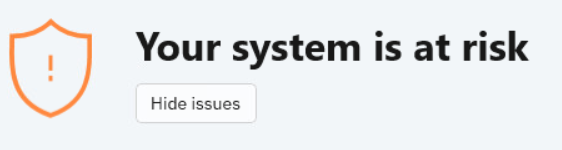
You can easily identify the current security status based on the status symbol displayed to the left of the status area:
Blue check mark. There are no issues to fix. Your computer and data are protected.
Orange exclamation mark. Non-critical issues that are affecting the security of your system.
Red X mark. Critical issues are affecting the security of your system.
In addition to the status symbol, a detailed security status message is displayed to the right of the status area. You can see the detected security issues by clicking inside the status area. Existing issues are fixed by your network administrator.
Issues area
The Issues area displays all the current issues found on your endpoint. If any critical issue is listed, the entire status set for the BEST agent is going to be critical, regardless of the number of additional non-critical issues.
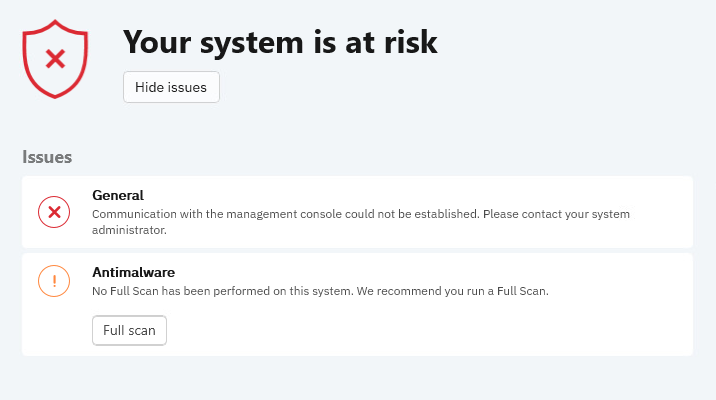
You can also hide the items in the Issues area, click Hide issues. The items remain hidden until you reopen the security agent.
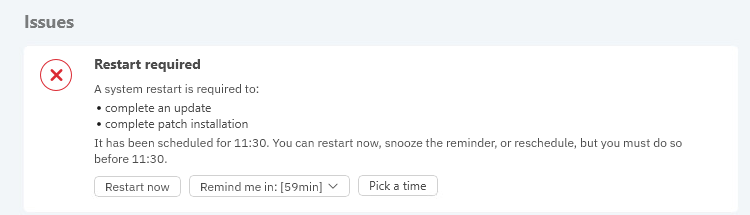
Some actions taken on your endpoint by the BEST agent will require a system restart. The restarts can be scheduled by administrators in Policies > Configuration profiles > Maintenance windows > Reboot preferences.
Based on the settings configured by the administrator, users can choose to restart now, set a reminder, or schedule the restart for a later time.
Tasks area
The Tasks area displays currently running tasks. When a task is completed, the Tasks area is no longer displayed in the Overview window.
Note
Tasks that have been generated by users are still going to be displayed in this area.
Policy name area
This area displays the policy that has been applied to your endpoint. This option is available only if granted by the network administrator through policy settings in GravityZone.
Modules area
The Modules area displays useful information about the status and activity of the installed protection modules.
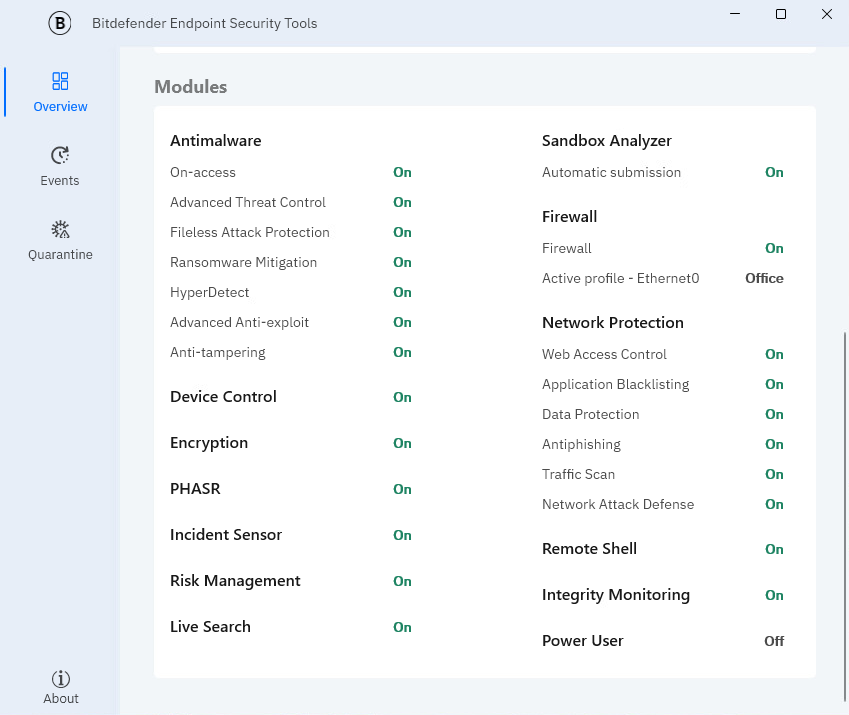
Antimalware
Antimalware protection is the foundation of your security. Bitdefender Endpoint Security Tools protects you in real time and on demand against malware, such as viruses, trojans, ransomware, exploits, etc.
On-access scanning prevents new malware threats from entering the system by scanning local and network files when they are accessed (opened, moved, copied or executed), boot sectors and potentially unwanted applications (PUA).
HyperDetect exposes advanced attacks and suspicious activities in the pre-execution stage. This layer of security contains machine learning models and stealth attack detection technology.
Advanced Threat Control continuously monitors applications running on the endpoint for malware-like actions. Advanced Threat Control automatically tries to clean detected files.
Fileless Attack Protection protects devices by detecting and blocking fileless malware before it can run. By default, it stops threats by analyzing memory, terminating malicious PowerShell activity, blocking harmful network traffic, and preventing code injection.
Ransomware Mitigation uses detection and remediation technologies to protect your data from both known and unknown ransomware. It blocks suspicious encryption activity and automatically restores affected files from a backup.
Advanced Anti-Exploit uses real-time, machine learning–based detection to block known and unknown exploits, including memory-based and fileless attacks.
Anti-tampering allows users to view when vulnerable drivers are detected on endpoints, and when advanced attack attempts are made to disable the security agent, leading to compromised product integrity.
Network Protection
Network Protection helps safeguard you on the internet against phishing attacks, fraud attempts, private data leaks, and inappropriate web content. It also includes a comprehensive set of user controls that help the network administrator enforce computer and internet use policies.
Traffic Scan prevents malware from being downloaded on the endpoint by scanning incoming emails and web traffic in real time. Outgoing emails are scanned to prevent malware from infecting other endpoints.
Application Blacklisting prevents access to unauthorized applications in your company. The administrator is responsible for creating rules for the allowed applications in the organization.
Web Access Control protects you from accessing dangerous websites based on administrator-defined rules.
Data Protection prevents unauthorized disclosure of sensitive data based on administrator-defined rules.
Antiphishing automatically blocks known phishing web pages to prevent users from inadvertently disclosing private or confidential information to online fraudsters.
Network Attack Defense detects network attack techniques used to gain access to specific endpoints, such as brute force attacks, network exploits, and password stealers.
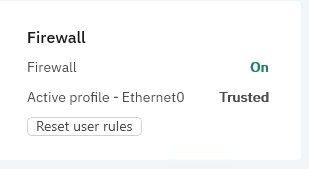
Firewall
The Firewall protects you while you are connected to networks and the internet by filtering connection attempts and blocking suspicious or risky connections.
If the Protection level in the policy is set to Ruleset and ask or Ruleset, known files and ask, you can choose to either Allow or Deny the connection when Firewall notifications are displayed. Selecting the notification opens the BEST UI, where you can view more details, such as the file path, command line, and IP address.
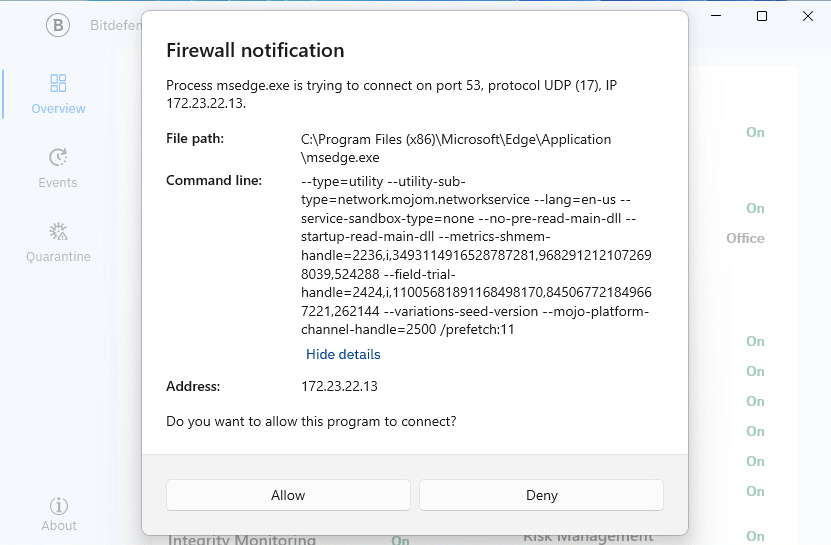
Note
If your operating system has notifications disabled, the connection is denied.
If you want to revert any connections that users have previously allowed or denied, click Reset user rules under Overview > Modules > Firewall. This action restores the Firewall to its default state.
Device Control
Device Control prevents sensitive data leakage and malware infections via external devices attached to endpoints. This is achieved through policy settings where you can configure blocking rules and exclusions, and then apply them to a vast range of device types. The administrator is responsible for managing permissions for the following types of devices:
Bluetooth Devices
CDROM Devices
Floppy Disk Drives
IEEE 1284.4
IEEE 1394
Imaging devices
Modems
Tape Drives
Windows Portable
COM/LPT Ports
SCSI Raid
Printers
Network Adapters
Wireless Network Adapters
Internal and External Storage
Application Control
The Application Control module blocks unauthorized applications and processes from running on the endpoint. Application Control decreases the frequency and impact of malware incidents, reducing the attack surface and vulnerabilities, by controlling the number of unwanted applications in your network.
Sandbox Analyzer
The Sandbox Analyzer module provides a powerful layer of protection against advanced threats by performing automatic, in-depth analysis of suspicious files which are not yet identified by Bitdefender antimalware engines. Sandbox Analyzer employs an extensive set of proprietary technologies that executes payloads in a contained virtual environment hosted by Bitdefender, analyzes their behavior and reports any subtle system changes that are indicative of malicious intent.
Encryption
The Encryption module provides full disk encryption, by managing BitLocker on Windows endpoints. You can encrypt and decrypt boot and non-boot volumes with minimal intervention from users, as GravityZone handles the entire process. Additionally, GravityZone stores the recovery keys needed to unlock volumes when the users forget their passwords.
EDR Sensor
The EDR (Endpoint Detection and Response) Sensor collects, handles, and reports endpoint and application behavior data. Part of the information is processed locally, while a more complex set of data is reported to a back-end component of GravityZone.
Patch Management
Patch Management keeps the operating system and software applications up to date. This module includes several features, such as on-demand or scheduled patch scanning, automatic or manual patching, and reporting on missing patches.
Risk Management
Risk Management helps you assess and harden your endpoints security configurations against industry best practices, to minimize the attack surface.
Live Search
Live Search uses Osquery to retrieve event data and system statistics in real time from online endpoints using SQL-based queries.
Remote Shell
This module provides interactive shell access, allowing you to remotely connect to an endpoint involved in an incident. You can run shell commands directly to mitigate threats or collect forensic data for analysis.
The Events window
Bitdefender Endpoint Security Tools keeps a detailed log of events on all the action made by the agent and all the security modules.
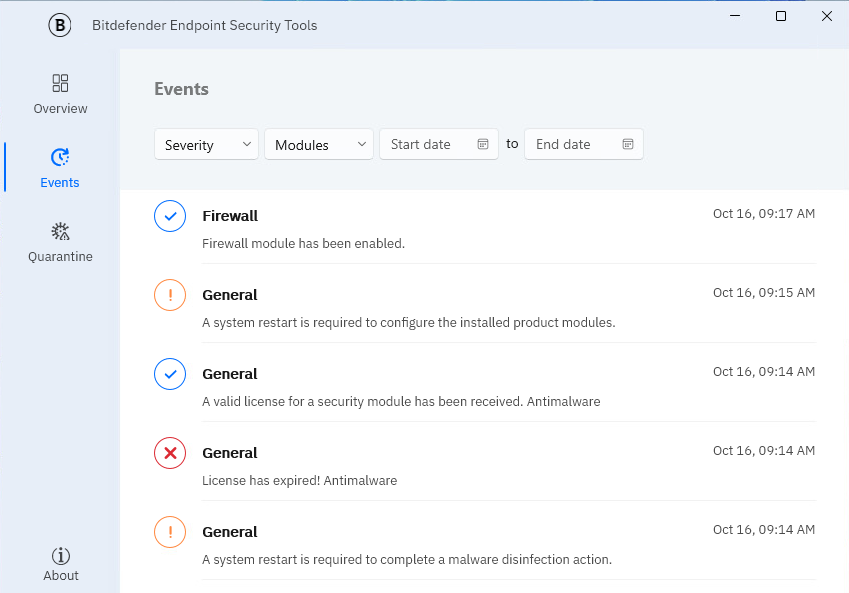
The Events window is an important tool in monitoring your Bitdefender protection. For instance, you can easily check if an update was successfully performed or if malware was found on your computer.
You can also sort the events by severity, modules, and date.
For more information, refer to Events.
The Quarantine window
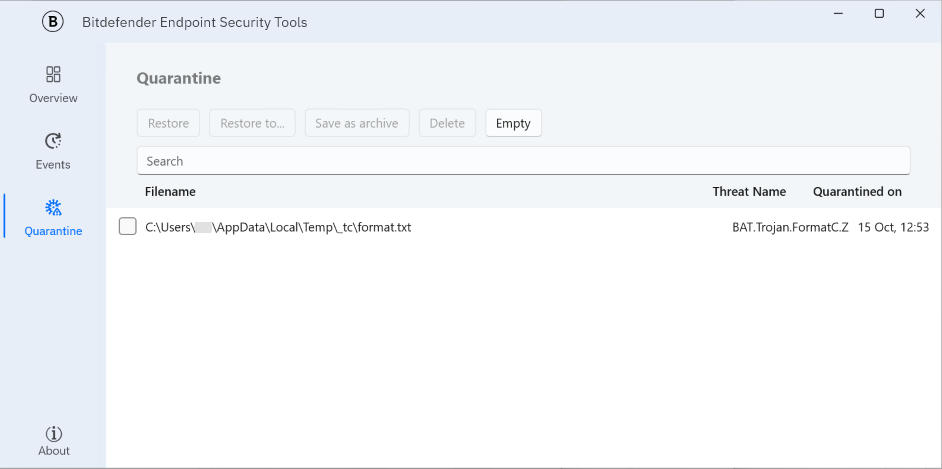
The Quarantine window lists all the infected or suspicious files that have been placed in isolation. Use the Restore, Restore to…, Save as archive, Delete and Empty buttons at the top of the page to restore files, restore them in a specific location, save the selected file as an archive, to delete selections of files, or to empty the entire list.
When you save a file as an archive, the following window is displayed and works as follows:
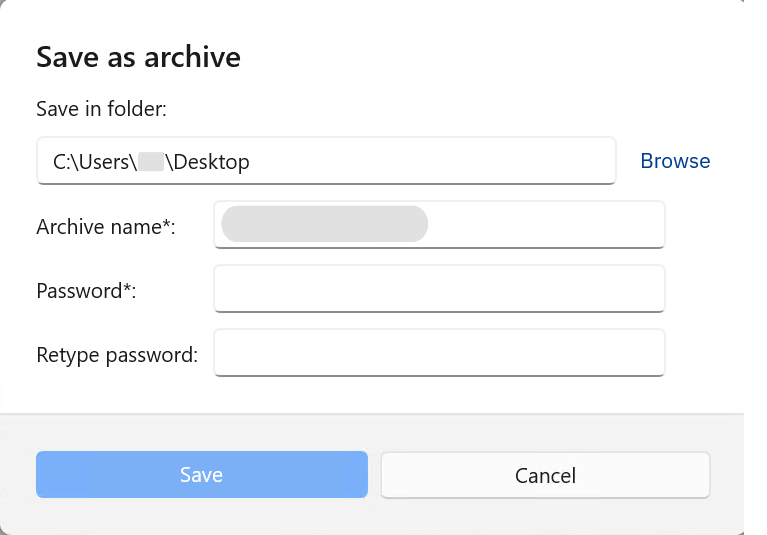
Save in folder: this field is set to the current user’s desktop by default. To change the location, click Browse.
If the name of the file already exists, you must choose a different one. You cannot overwrite an existing file or create new folders from this window.
Archive name: this field is pre-filled based on the quarantined file’s path. You can rename it, but the security agent always creates a ZIP archive regardless of the name or extension you choose.
The archive contains the original file with its original name, protected by the password you have selected.
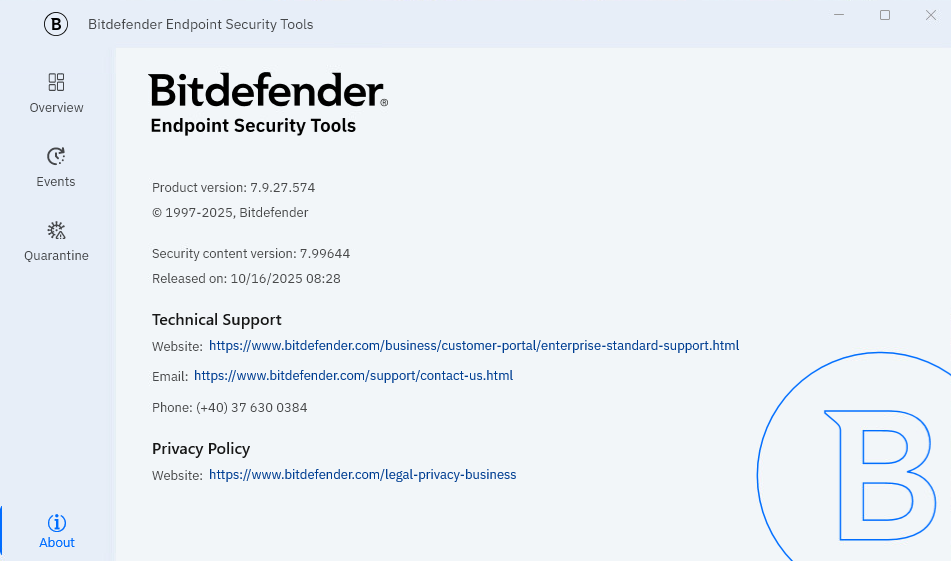
The About window
This section displays the product version and the security content version of Bitdefender Endpoint Security Tools for Windows, Technical Support details, and Privacy Policy information.
The information displayed in the Technical Support section can be customized by the system administrator in the policy.
Changing the display language of Bitdefender Endpoint Security Tools
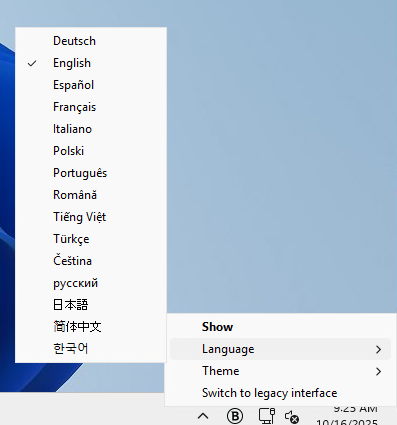
To change the language displayed and used by your locally installed BEST client, follow these steps:
Right-click the BEST icon in the system tray.
Go to Language.
Select your desired language.
Available languages:
English
Spanish
German
French
Romanian
Polish
Portuguese
Italian
Russian
Czech
Chinese
Vietnamese
Turkish
Korean
Japanese
Note
Changing the language will restart the BEST client interface.