General
In the Network Protection > General section of the policy,, you can configure options such as enabling or disabling functionalities and configure exclusions.
The settings are organized into the following sections:
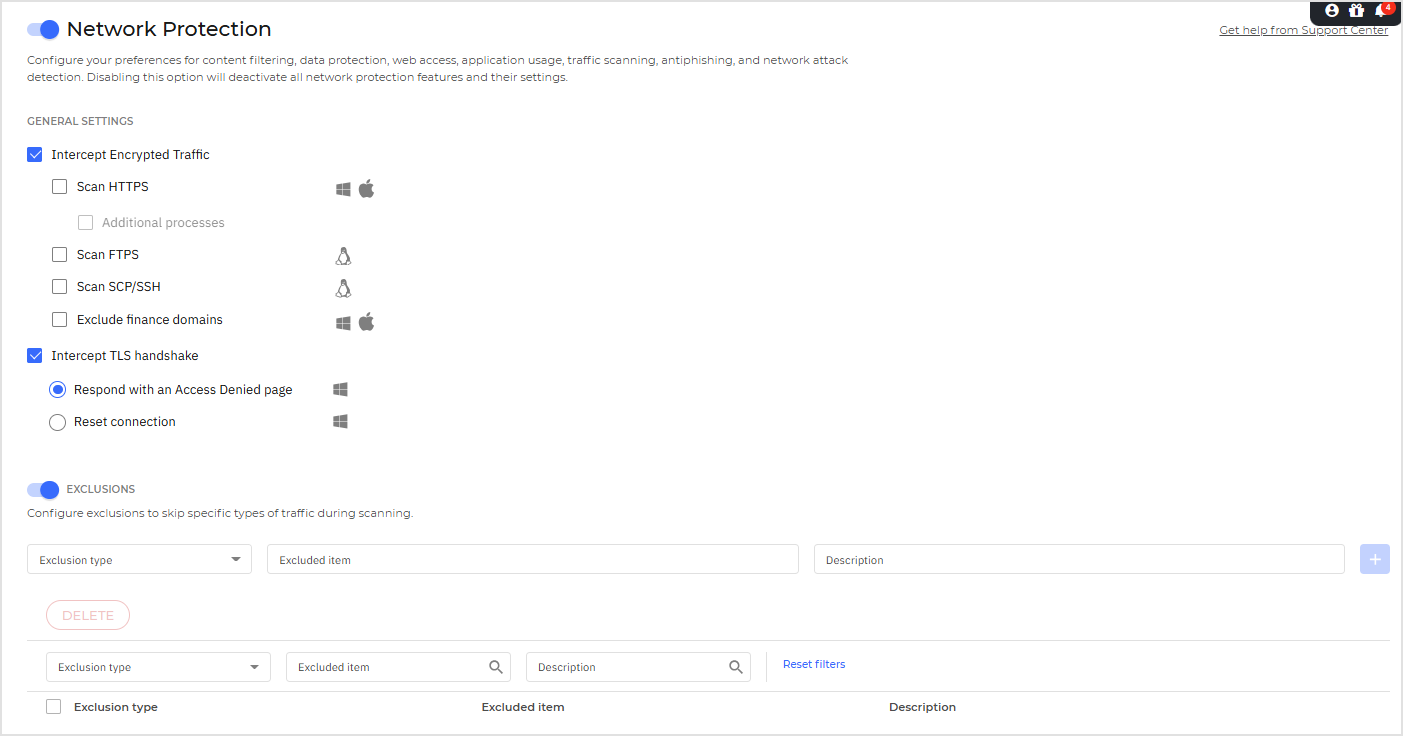
General settings
Intercept Encrypted Traffic - Select this option if you want the Secure Sockets Layer (SSL) web traffic to be inspected by the Bitdefender security agent's protection modules.
Scan HTTPS - Select this option if you want to extend SSL scanning to HTTP protocol.
The Bitdefender Endpoint Security Tools agent intercepts and scans HTTP/HTTPS on predefined processes on Windows and Mac. Additional processes for Scan HTTPS provides administrators flexibility in scanning custom applications and unsupported browsers.
Note
You can add process names separated by semicolons in the Additional processes field.
Scan FTPS - Select this option to enable outbound traffic monitoring over FTPS protocol on Linux machines.
Scan SCP/SSH - Select this option to enable outbound traffic monitoring over SCP and SSH protocols on Linux machines.
Scan IMAPS - Select this option to enable inbound traffic monitoring for encrypted email messages received via the IMAP protocol.
Scan MAPI - Select this option to enable outbound and inbound traffic monitoring for encrypted email messages received via MAPI protocol.
Scan POP3S - Select this option to enable inbound traffic monitoring for encrypted email messages received over the POP3S protocol.
Scan SMTPS - Select this option to enable outbound traffic monitoring for encrypted email messages received via the SMTPS protocol.
Exclude finance domains - Select this option to exclude any financial domains from scanning.
Note
Enabling Extended Protection on mail servers may lead to compatibility issues with certain email protocol scanning features. The following protocols may be affected: IMAPS, MAPI, POP3S, and SMTPS.
For details on the authentication procedures using SSH keys, refer to SSH PKI authentication on endpoint outbound connections.
The FTPS protocol defines at least two different ways to start this sequence: explicit (active) security and implicit (passive) security.
Warning
Network Attack Defense only works with implicit (passive) security.
Intercept TLS Handshake - Select this option if you want the security agent to intercept malicious domains during the TLS Handshake phase, detecting potential threats without decrypting traffic.
The feature scans outbound processes, excluding those defined in the HTTPS scan settings, and allows you to respond by either denying access to the page or resetting the connection.
Note
This feature is compatible only with Windows operating systems.
Respond with an Access Denied page - Select this option if you want to display an Access Denied page.
Reset connection - Select this option if you want to reset the user's connection. The user will receive an error explaining that the page cannot be accessed.
Exclusions
You can choose to skip certain traffic of being scanned for malware while the Network Protection options are enabled.
Note
These exclusions apply to Traffic Scan and Antiphishing, in the Web Protection section, and to Network Attack Defense, in the Network Attacks section. Data Protection exclusions are configurable separately, in the Content Control section.
On Linux systems, the exclusions are made at the application level, not at the iptables level.
To define an exclusion:
Select the exclusion type from the menu.
Depending on the exclusion type, define the traffic entity to be excluded from scanning as follows:
IP/mask - Enter the IP address or the IP mask for which you do not want to scan the incoming and outgoing traffic, which includes network attack techniques.
You can also exclude vulnerability scanners by adding their IP addresses in this section or by duplicating exclusions created in the Firewall section. For details on Firewall exclusions, refer to the "Block port scans" in Firewall Configuration.
URL - Excludes from scanning the specified web addresses. Take into account that URL-based scan exclusions apply differently for HTTP versus HTTPS connections, as explained hereinafter.
You can define a URL-based scan exclusion as follows:
Enter a specific URL, such as
www.example.com/example.htmlIn the case of HTTP connections, only the specific URL is excluded from scanning.
For HTTPS connections, adding a specific URL excludes the entire domain and any of its subdomains. Therefore, in this case, you can specify directly the domain to be excluded from scanning.
Use wildcards to define web address patterns.
You can use the following wildcards:
Asterisk (*) substitutes for zero or more characters.
Question mark (
?) substitutes for exactly one character. You can use several question marks to define any combination of a specific number of characters. For example,???substitutes for any combination of exactly three characters.
In the following table, you can find several syntax samples for specifying web addresses (URLs).
Syntax
Exception Applicability
www.example*Any URL starting with
www.example(regardless of the domain extension).The exclusion will not apply to the subdomains of the specified website, such as
subdomain.example.com.*example.comAny URL ending in
example.com, including subdomains thereof.*example.com*Any URL that contains the specified string.
*.comAny website having the
.comdomain extension, including subdomains thereof. Use this syntax to exclude from scanning the entire top-level domains.www.example?.comAny web address starting with
www.example?.com, where?can be replaced with any single character.Such websites might include:
www.example1.comorwww.exampleA.com.
Note
You can use protocol-relative URLs.
Application - Excludes from scanning the specified process or application. To define an application scan exclusion:
Enter the name of the executable file of the application to be excluded.
For example, enter
calendarto exclude the Calendar application,firefoxto exclude the Mozilla Firefox browser, orelectronto exclude the Visual Studio Code application.Use wildcards to specify any applications matching a certain name pattern.
For example:
c*.exematches all applications starting with "c" (chrome.exe).??????.exematches all applications with a name that contains six characters (chrome.exe, safari.exe, etc.).[^c]*.exematches all application except for those starting with "c".[^ci]*.exematches all application except for those starting with "c" or "i".
Note
You do not need to enter a path and the executable file does not have an extension. This is different from exclusions in Antimalware, where you need to specify the entire path.
If needed, add a comment in the Description field to make it easier to identify the exclusion later.
Click the
 Add button to add the exclusion.
Add button to add the exclusion.
To edit an exclusion:
Click the
 More icon in the table.
More icon in the table.In the menu, click Edit.
Make the necessary changes.
Click the confirmation button to save the changes.
Alternatively, click the cancel button to exit the editing mode without any changes.
To remove an exclusion from the list:
In the table, go to the exclusion you want to delete.
Open the
 More menu.
More menu.In the menu, click Delete.
The exclusion is removed from the table.
To remove multiple exclusions at the same time:
Select the checkboxes corresponding to the exclusions you want to delete.
Click the Delete button at the upper side of the table.
The target exclusions are removed from the table.
You cannot restored deleted exclusions.