Settings
In the Antimalware > Settings section of the policy, you can configure the quarantine settings.
Note
Exclusions settings, which were previously displayed on this page, are available here.
Quarantine
You can configure the following options for the quarantined files from the target endpoints:
Delete files older than (days) - By default, quarantined files older than 30 days are automatically deleted. If you want to change this interval, choose a different option from the menu.
Submit quarantined files to Bitdefender Labs every (hours) - By default, quarantined files are automatically sent to Bitdefender Labs every hour.
You can edit the time interval between quarantined files are being sent (one hour by default). The sample files will be analyzed by the Bitdefender malware researchers. If malware presence is confirmed, a signature is released to allow removing the malware.
Rescan quarantine after security content updates - Keep this option selected to automatically scan locally quarantined files after each security content update. Clean files are automatically moved back to their original location.
Copy files to quarantine before applying the disinfect action - Select this option to prevent data loss in case of false positives and copy each file detected as infected to quarantine before applying the disinfect action. You can afterwards restore legitimate files from the Quarantine page.
Allow users to take actions on local quarantine - This option is controlling the actions that endpoint users can take on local quarantined files via the Bitdefender Endpoint Security Tools interface.
By default, local users can restore or delete quarantined files from their computer using the options available in Bitdefender Endpoint Security Tools.
By disabling this option, users will not have access anymore to the quarantined files action buttons from the Bitdefender Endpoint Security Tools interface.
Note
Availability and functioning of this feature may differ depending on the license included in your current plan.
Centralized quarantine
If you want to keep the quarantined files from your managed endpoints for further analysis, use the Centralized quarantine option, which sends an archived copy of each local quarantined file to a network share.
Note
This feature is available for:
Windows for workstations
Windows for servers
Linux
Availability and functionality of this feature depend on the license included in your current plan.
After enabling this option, each quarantined file from the managed endpoints is copied and packed in a password-protected ZIP archive to the specified network location. The archive name is the hash of the quarantined file.
Important
The archive size limit is 100 MB. If the archive exceeds 100 MB, it will not be saved on the network shared location.
To configure the centralized quarantine settings, fill in the following fields:
Click the Centralized quarantine checkbox to enable the section.
Archive password - Enter the password required for the quarantined files archive.
The password must contain at least one upper case character, at least one lower case character and at least one digit or special character.
Confirm the password in the following field.
Share path - Enter the network path where you want to store the archives (for example,
\\computer\folder).Username and password - They are required to connect to the network share. The supported formats for username are as follows:
username@domaindomain\usernameusername.
For the centralized quarantine to work properly, make sure the following conditions are met:
The shared location is accessible in the network.
The endpoints have connectivity to the network share.
The login credentials are valid and provide write access to the network share.
The network share has enough disk space.
Note
Centralized quarantine does not apply to mail servers quarantine.
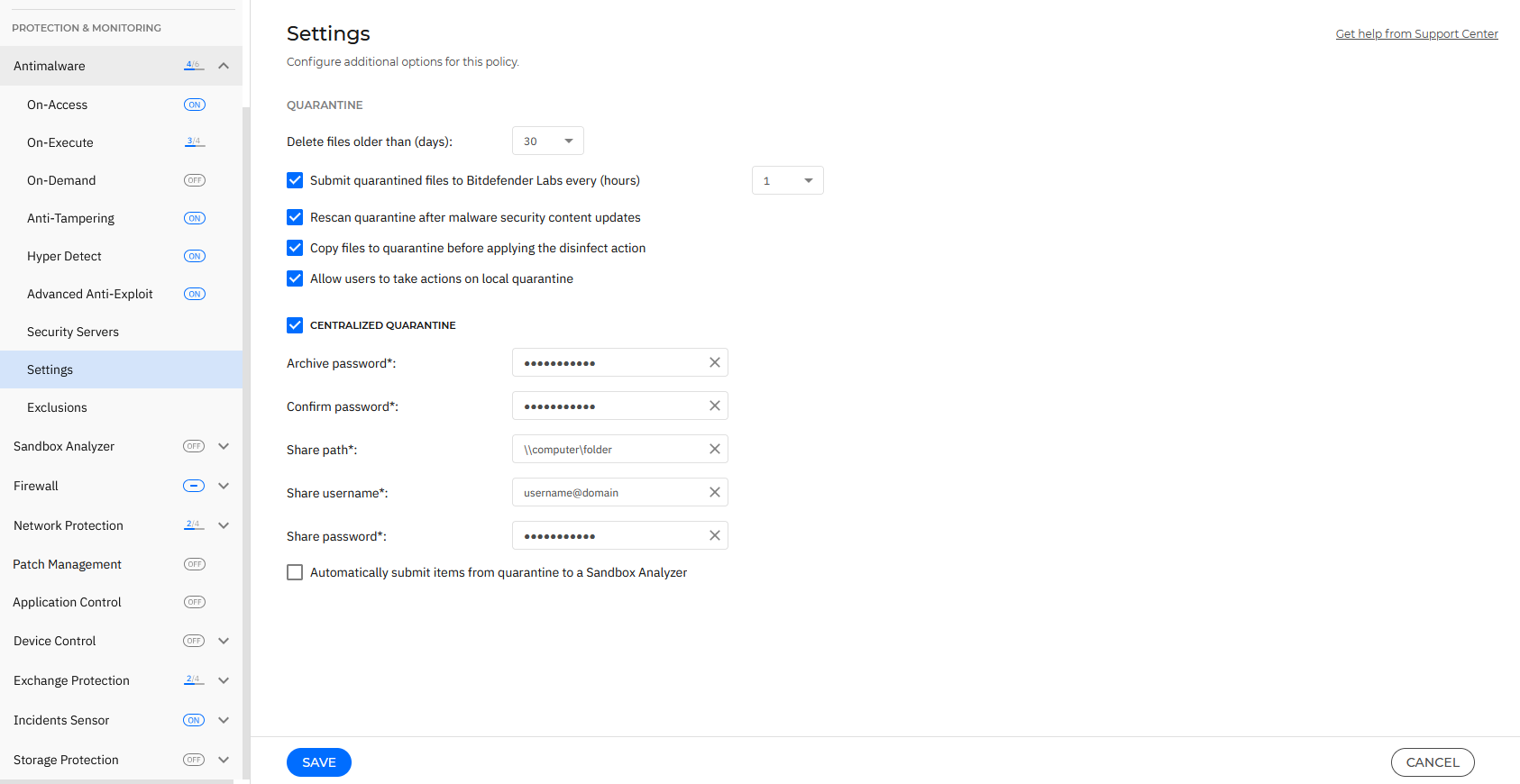
If you have a local Sandbox Analyzer instance configured in the Sandbox Analyzer > Endpoint Sensor section, you can select the check box Automatically submit items from quarantine to a Sandbox Analyzer.
Note
Depending on the license included in your current plan, the amount of submitted items may be capsized to a maximum size of 50 MB.