Managing two-factor authentication for user accounts
To view the two-authentication status for a specific account, follow the steps below:
Log in to the GravityZoneControl Center with an administrator account.
Go to the Accounts page from the left side menu.
A table is displayed, containing all the user accounts that have been created on your company.
You can view the two-authentication status for each account under the 2FA column.
Tip
You can only view and manage other user accounts from the Accounts page. To revoke browsers, and reset and disable 2FA for your own account, go to the Welcome, [username] > My Account page.
To reset 2FA for your account, contact your GravityZone administrator. You cannot reset 2FA for your account by yourself.
Contact your GravityZone administrator also when your device is lost, stolen, or replaced. After reset, you will be able to reconfigure 2FA with your new device.
Change 2FA settings for a specific account
To change 2FA settings for a specific user account, follow the steps below:
While still on the Accounts page, locate the user you wish to edit and click the link under the Username column.
Scroll down to the Login Security section.
The following actions are available for two-factor authentication:
Revoke trust for browsers
Use this option to revoke the trust of all browsers on all devices that skip the six-digit code when connecting to Control Center. Follow the steps below:
Enter your GravityZone password under Your GravityZone password*.
Note
This step is not required for users who use a single sign-on (SSO) to sign in.
Click the Revoke all browsers button.
Select Revoke.
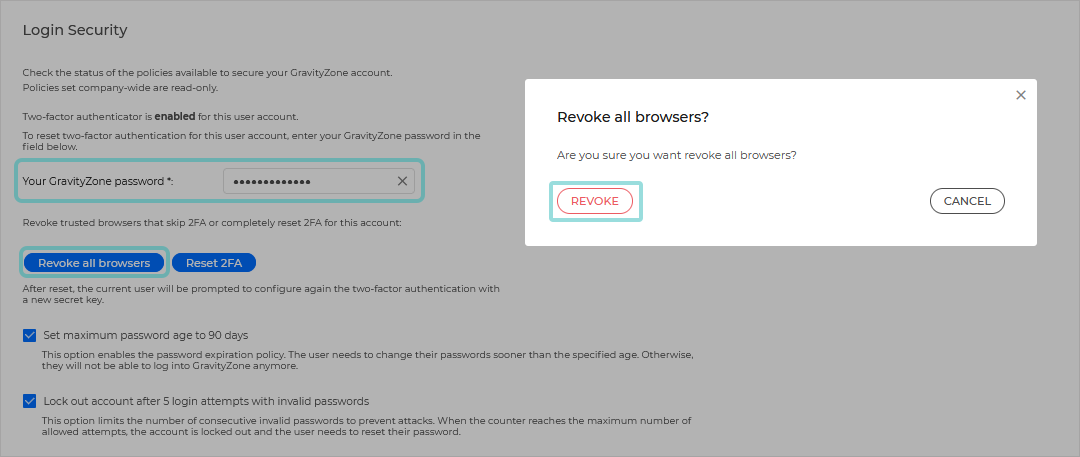
After revoking all browsers, the user need to enter the six-digit code again when connecting to Control Center. Users who previously enabled the Trust this browser option on the GravityZone login page have to enter the authentication code again.
Reset user's two-factor authentication
Use this option when users have changed or wiped the devices that hosted the authenticator, and they lost the secret key. Follow the steps below:
Enter your GravityZone password under Your GravityZone password*.
Note
This step is not required for users who use a single sign-on (SSO) to sign in.
Click the Reset 2FA button.
Select Reset.
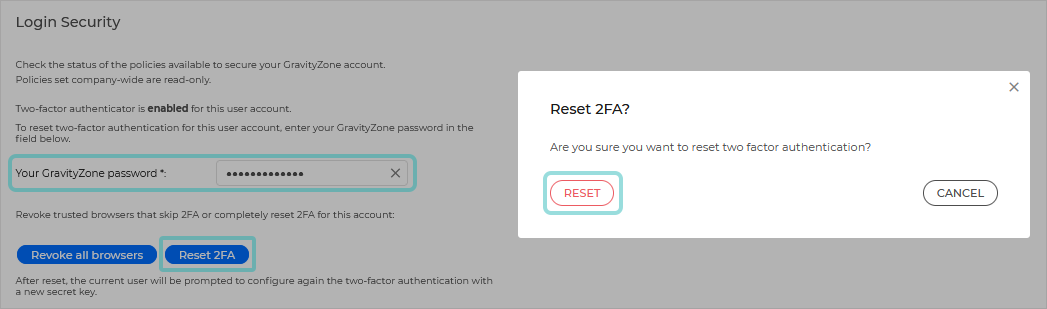
After resetting 2FA, a configuration window will prompt the user at login to configure again the two-factor authentication with a new secret key.
Check 2FA related user activity
To check the 2FA changes related to user accounts, access the Accounts > User Activity page and filter the activity logs using the following filters:
Area: Accounts/Company
Action: Edited
For information about 2FA on your account, refer to Your account.
Important
The authentication app of choice (Google Authenticator, Microsoft Authenticator, or any two-factor TOTP (Time-Based One-Time Password Algorithm) authenticator - compatible with the standard RFC6238 combines the secret key with the device’s current timestamp to generate the six-digit code.
Be aware that the time-stamps on both device and the GravityZone appliance have to match for the six-digit code to be valid. To avoid any time-stamps synchronization issue, we recommend enabling the automatic date and time setting on the device.
Video
Watch a full video tutorial on the topic here:
Enforce two-factor authentication for all accounts
Enable this option to make 2FA mandatory for all GravityZone accounts.
When logging in, users will be prompted to configure 2FA for their accounts and they will have to enter a six-digit code in addition to their credentials. Users can skip enabling 2FA only three times. At the fourth login attempt, they will not be able to connect to Control Center without two-factor authentication.
To enable this setting, follow the steps below:
Log in to GravityZone with an administrator account.
Go to the Configuration page from the left side menu and select the Miscellaneous tab.
Under the Two-factor Authentication section, enable the Enforce two-factor authentication for all accounts setting.
Click Save.
Allow users to set up trusted browsers
This option allows to trust the browsers used for connecting to Control Center. After enabling the Trust this browser check box on the login screen, users do not need to enter the six-digit code any longer until the interval expires.
To enable this setting, follow the steps below:
Log in to GravityZone with an administrator account.
Go to the Configuration page from the left side menu and select the Miscellaneous tab.
Under the Two-factor Authentication section, select an option under the Users trust their browsers setting.
The maximum interval you can select is 90 days. When the interval expires, users must enter the six-digit code in addition to their credentials. When selecting Never, browsers are not trusted and users cannot skip two-factor authentication.
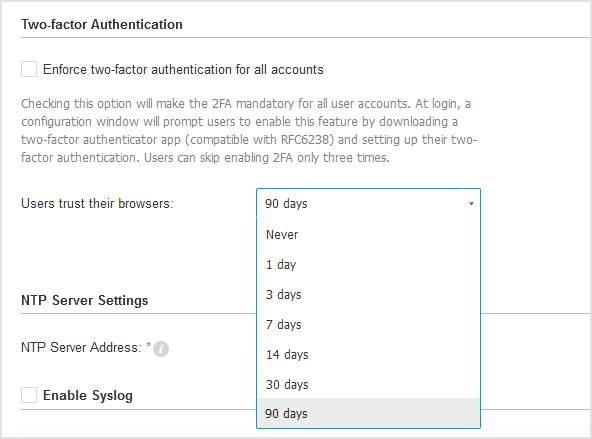
Click Save.
Disable 2FA
This option is only available if the Enforce two-factor authentication for all accounts option has not been enabled. Follow these steps:
Enter your GravityZone password under Your GravityZone password*.
Note
This step is not required for users who use a single sign-on (SSO) to sign in.
Click the Disable button.
Confirm the request.
A confirmation message will inform you that two-factor authentication has been disabled for the user.
Note
If the user has 2FA disabled and you want to activate it, you will need to ask the user to enable this feature from his account settings.
If you have a company administrator account, you may make two-factor authentication mandatory for all GravityZone accounts. For more information, refer to Configure Control Center settings.