VMware NSX-V
GravityZone Security for Virtualized Environments integrates with the VMware vCenter through NSX-V manager.
Effective August 31, 2025, Bitdefender no longer supports or releases product updates for VMware NSX-T and NSX-V. For more information, refer to End-of-life and support for GravityZone Security for Virtualized Environments integrations with VMware NSX-T and VMware NSX-V.
Integrate with NSX-V Manager
For the integration to work, you will need to set up the integration for vCenter Servers associated with the NSX-V Manager. For more information, refer to Integrate with vCenter Server.
To setup integration with NSX-V Manager:
In Control Center, navigate to Configuration > Virtualization Providers > Management Platforms.
Click the
 Add button at the upper side of the table. A configuration window will appear.
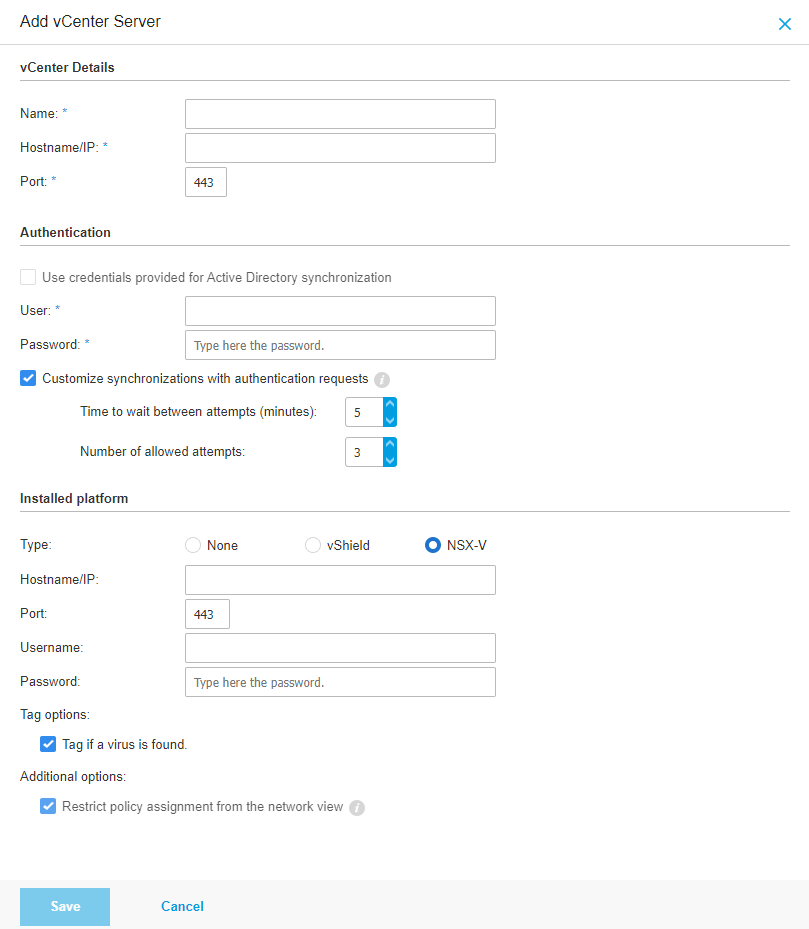
Add button at the upper side of the table. A configuration window will appear.Specify the NSX-V integration details:
Add the vCenter details.
Add Installed platform details, selecting NSX-V:
The hostname or the IP address of the associated vCenter Server system.
The NSX-V port. The default value is
433.The username.
The password.
Click Save.
After the integration is added, you must register by pressing the
 Register button.
Register button.This button requires the NSX-V Security Server to be published from: Control Center > Configuration > Update > Components.
After publishing the image, you can press the
 Register button.
Register button.
Content Control is now integrated with NSX-V.
Note
GravityZone can only be used to protect the associated vCenter server.
Manage endpoint protection in VMware NSX-V
In this section, you will learn how to configure Bitdefender GravityZone Security for Virtualized Environments integration with NSX-V Manager and apply endpoint protection to your guest virtual machines.
Integration overview
The NSX-V integration provides agentless endpoint protection capabilities through the Guest Introspection ecosystem. Bitdefender integrates with the NSX ecosystem to protect guest virtual machines by using a Security Server deployed at the hypervisor host level.
This section provides guidance for NSX-V Manager administrators on how to configure and apply endpoint protection to guest VMs, by implementing a Bitdefender GravityZone Guest Introspection policy.
Prerequisites
Software Prerequisites
For more information about compatibility with NSX-V Manager, refer to Version compatibility between Bitdefender GravityZone and VMware NSX-V.
NSX-V Manager configuration prerequisites
Before you start the Bitdefender GravityZone configuration and Security for Virtualized Environments service deployment, you need to meet the following conditions:
The NSX-V Manager is connected to all target Compute Manager (vCenter Servers) and all ESXi hosts target cluster members have NSX drivers installed. For more information, refer to the official NSX Installation Guide.
All target VMs are running a compatible version of VMware Tools with the NSX Guest Introspection driver installed. For more information, refer to Install the Guest Introspection Thin Agent on Windows Virtual Machines or Install the Guest Introspection Thin Agent on Linux Virtual Machines.
Process description
Deploy the Security Server installation as a partner service in NSX-V manager
To deploy the partner service (Bitdefender GravityZone) in NSX Manager and apply endpoint protection to VMs you must:
In vCenter, go to the Menu > Networking and Security.
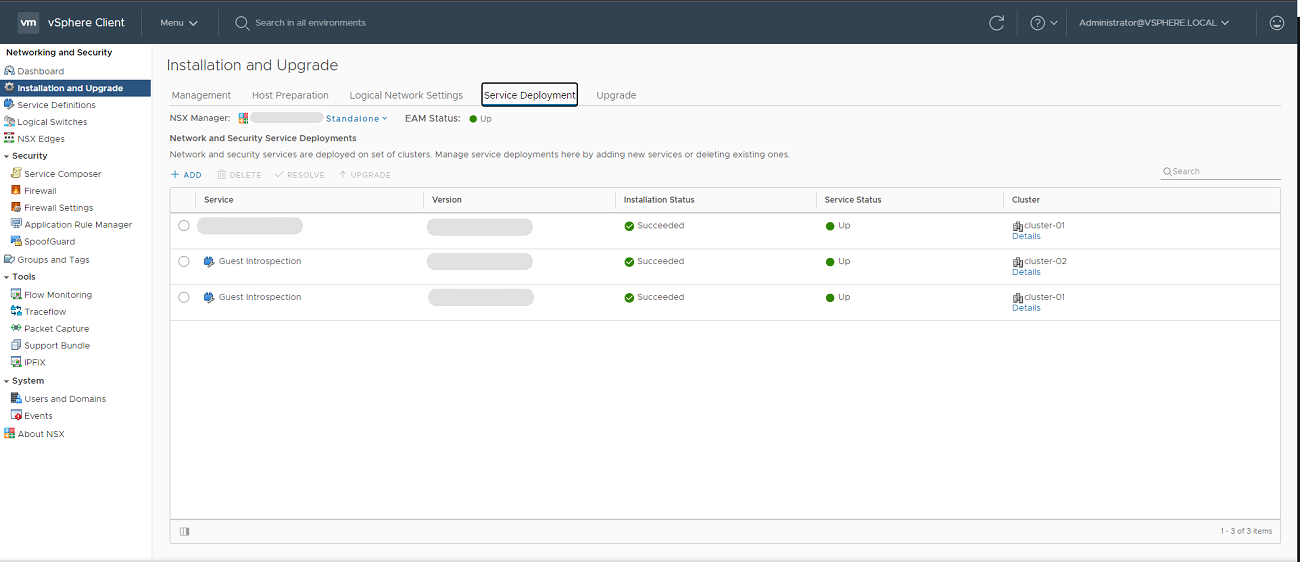
Go to Installation and Upgrade > Service Deployment.
Deploy Guest Introspection, using the plus button on the cluster that should be protected by the Bitdefender Security Server.
Wait until Guest introspection has displays the Succeded installation status and the service status is Up.
Select the Bitdefender service.
Click Deploy.
Specify the service deployment details:
In the Cluster field, select the cluster where the service needs to be deployed.
In the Data Store field, you can select a data store where the Security Server disk can be stored.
For more information, refer to the official VMware Documentation.
Under the Network column, you must configure the Management Network interface and the Assignation Mode.
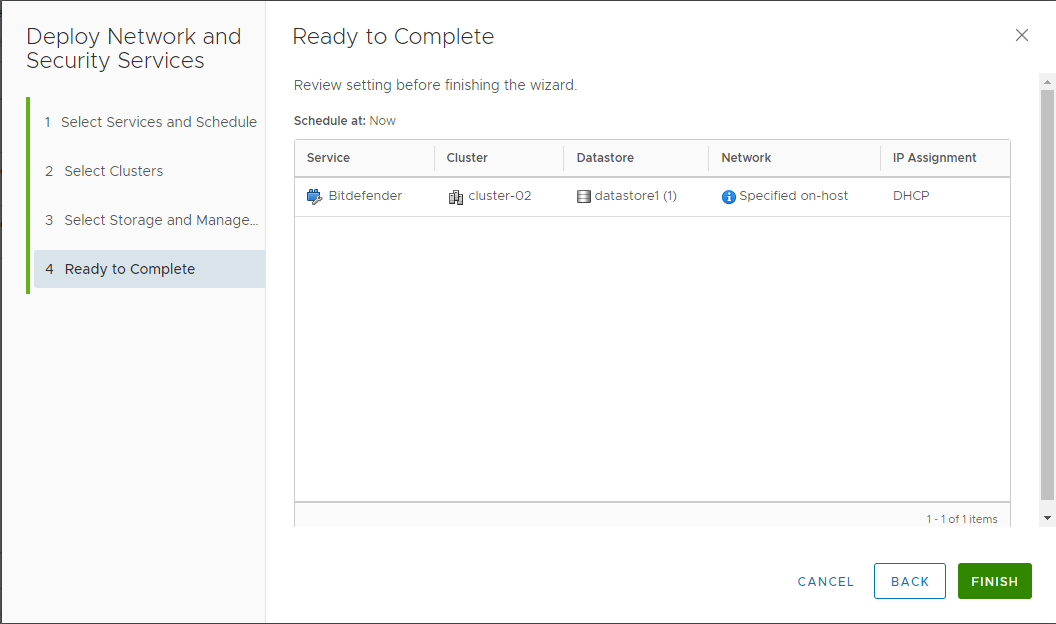
Click Finish.
Configure NSX groups
NSX uses groups to be used as source and destination field of a service profile. Create groups in NSX Manager for protected, unprotected VMs and affected (quarantined) VMs.
In this section, you will find out how to create and define group membership:
Protected VM Group
Create a group for protected VMs by following these steps:
In vCenter, go to the Networking and Security page.
Click Service Composer.
In the Security Group section, click Add.
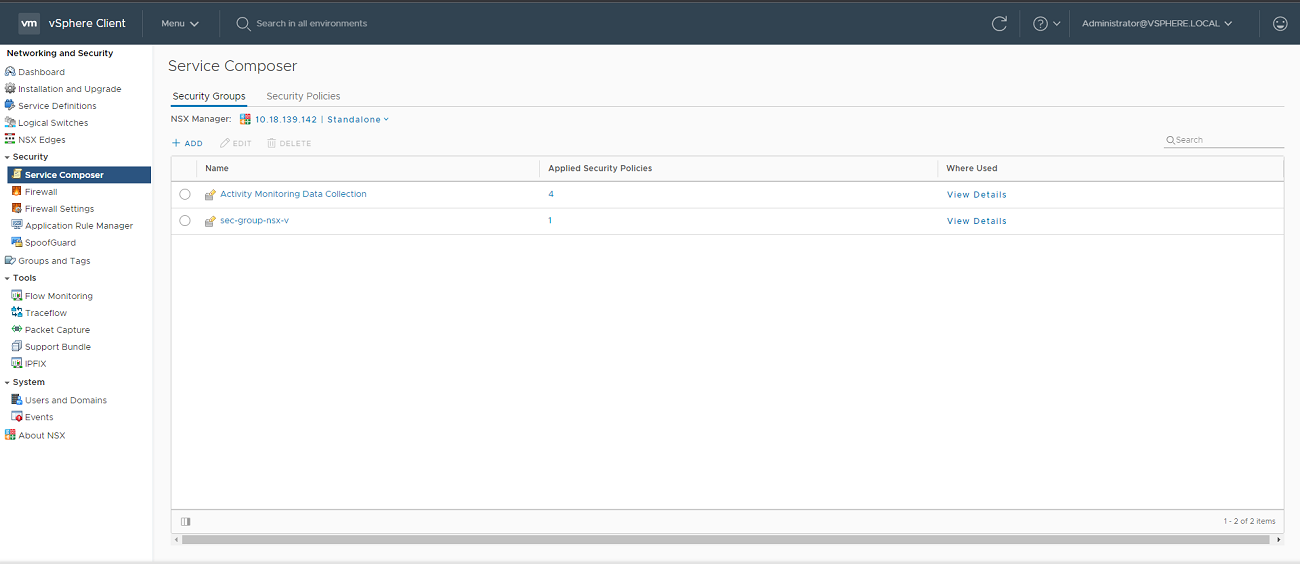
Specify the group details:
Enter the security group name and description. Under Compute Members, click Set Members to define membership of the group:
Go to the Membership Criteria tab and click Add criteria.
In the third column, click Contains.
In the Scope field, enter the following tag:
ANTI_VIRUSClick Apply.
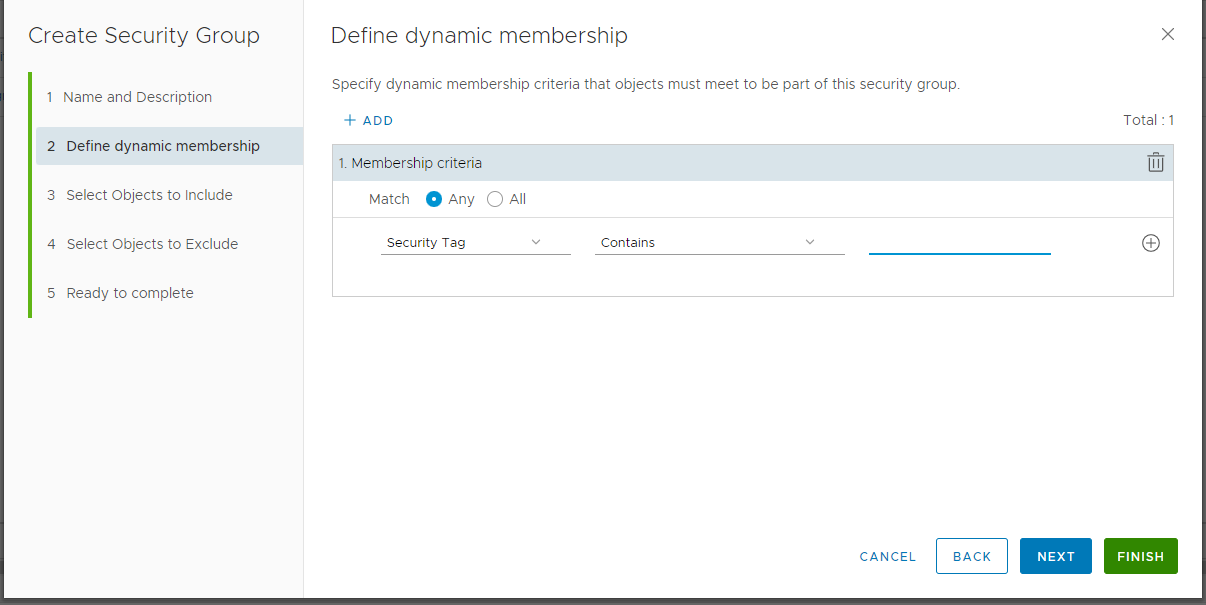
Define a dynamic membership using available criteria.
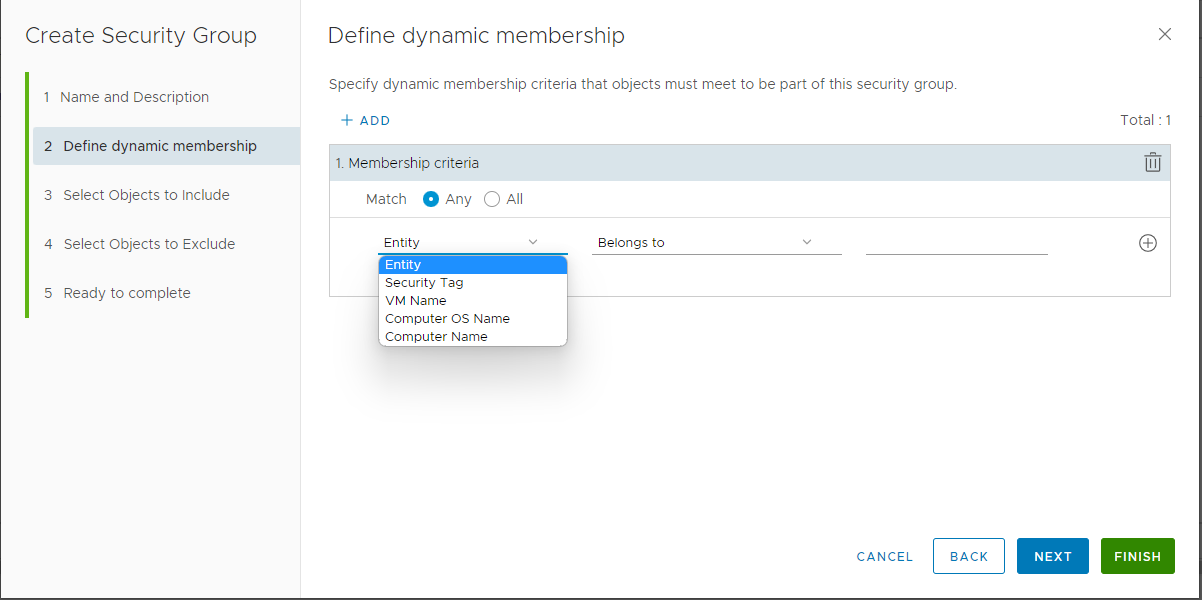
Include objects from Object type dropdown list.
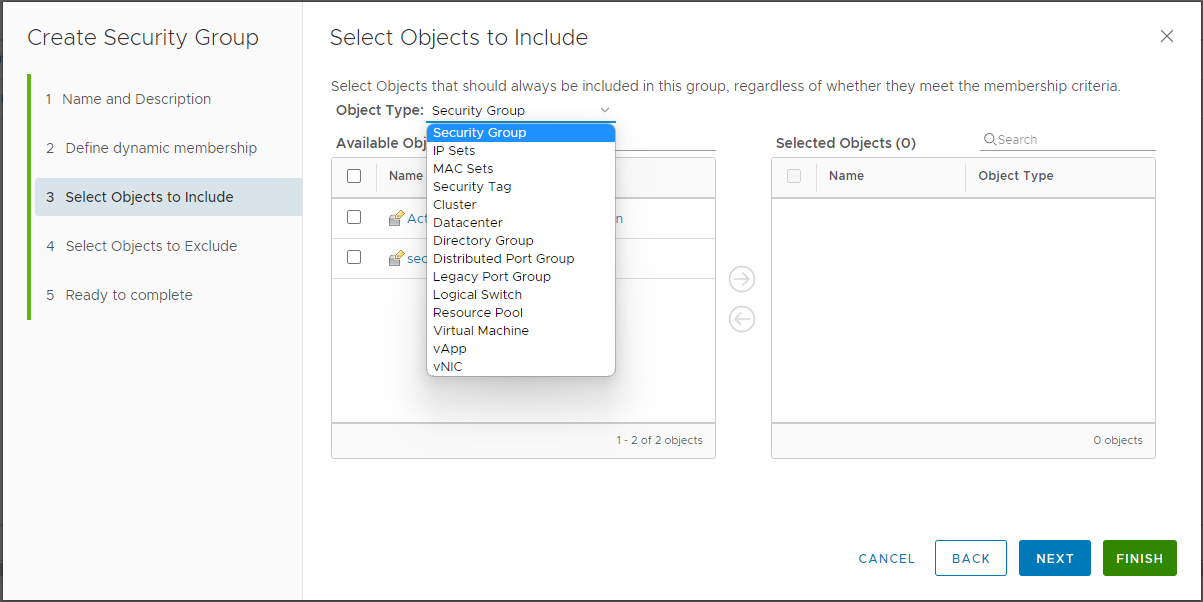
Note
Users can also exclude objects in this page.
Click Finish.
The group for the protected VMs is now added.
Create a GravityZone security policy
Create and configure security policy in Control Center.
In Control Center, go to the Policies > General > Antimalware page.
Click Add to configure a policy.
Enter a name for your policy.
Configure the policy settings as needed.
Note
Only Antimalware settings are applicable to NSX-V integrations.
Go to NSX and select the associated check box to set its visibility in NSX-V Manager.
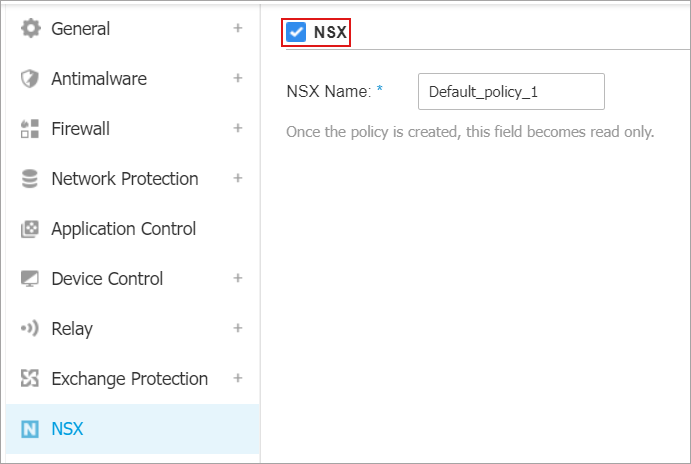
The GravityZone policy is visible in NSX-V Manager under the Vendor Template column, when you add a Service Profile.
Click Save.
Configure and apply endpoint protection to guest VMs
NSX enforces Guest Introspection policies (GravityZone security policy) when a Service Profile is available. To apply endpoint protection to guest VMs you need to create Service Profile and associate it to a VM group through policy rule.
Configure endpoint protection for guest VMs by following these steps:
Create a service profile
Add a Service Profile in NSX Manager:
In vCenter, go to the Networking and Security.
Click Service Composer.
In the Security Policies section, click Add.
Add your security policy name.
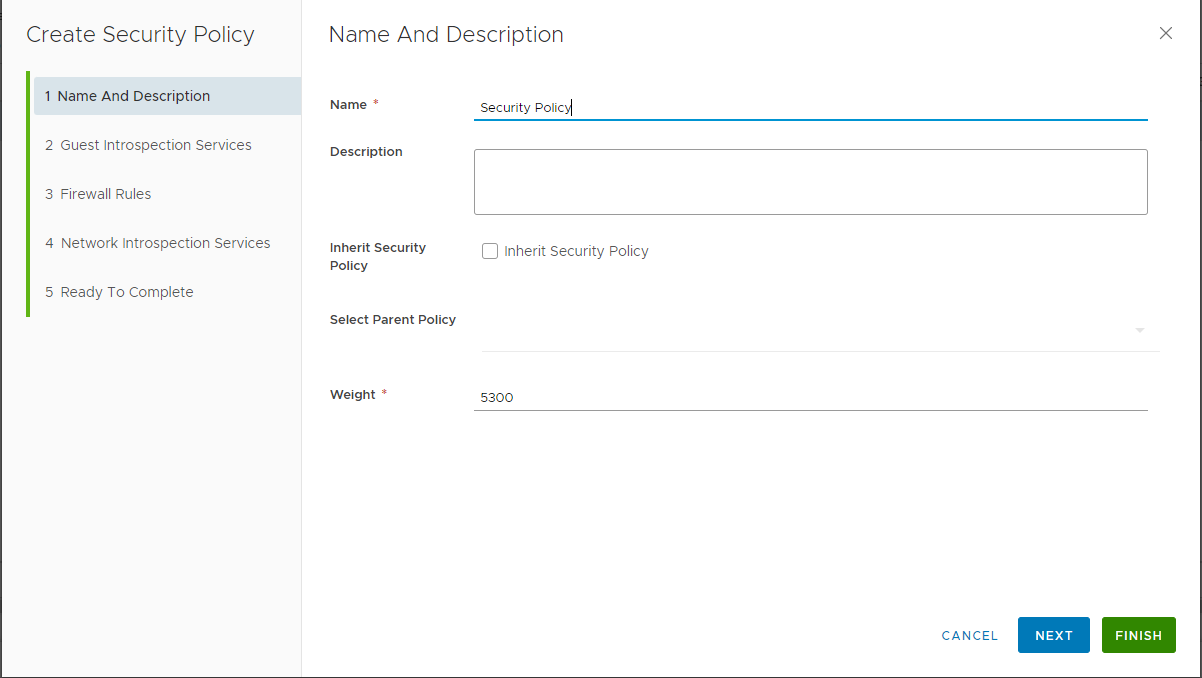
In the Guest Introspection Services page, click Add.
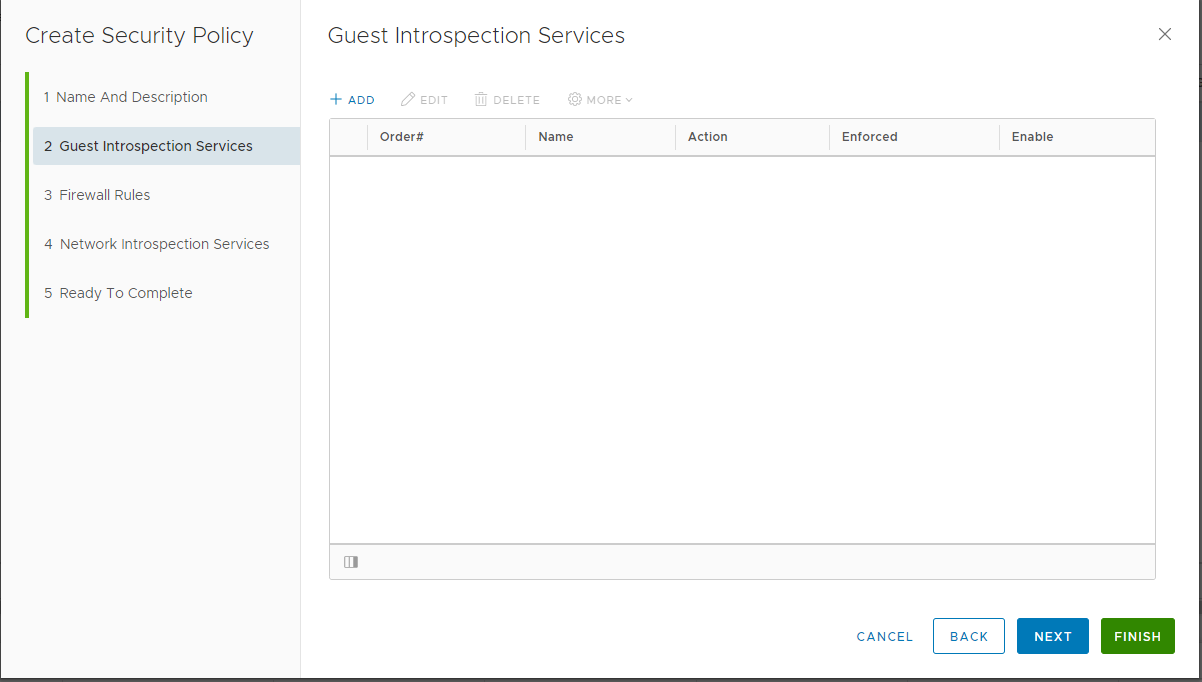
Specify the guest introspective service name.
Select the Bitdefender as the service name.
Select the service profile associated with the GravityZone policy settings.
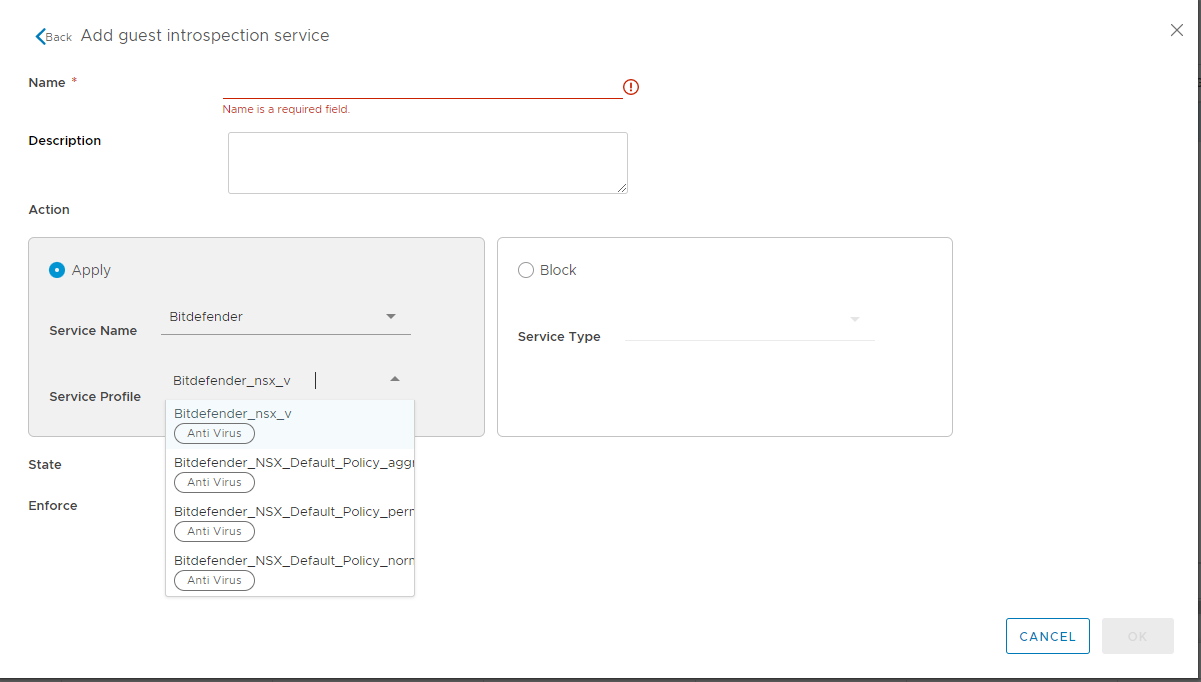
On the Ready to Complete page, click Finish.
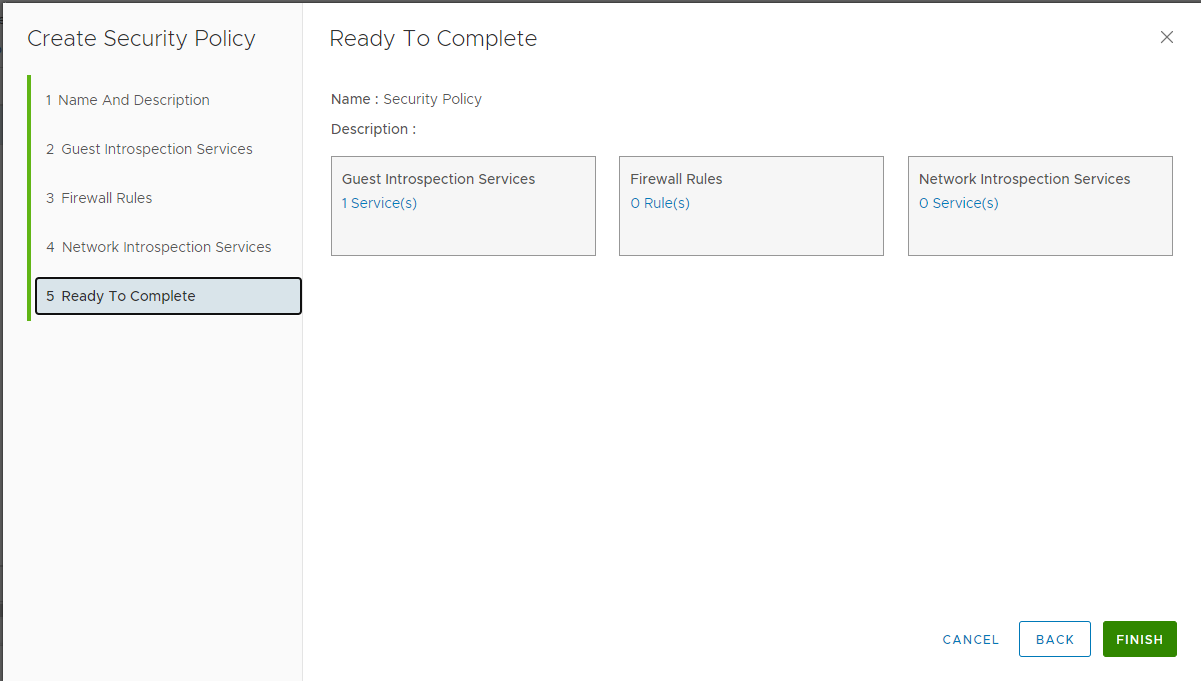
The service profile is now added.
To associate a security group that needs to be protected by a specific service profile, you need to apply the security policy to that group or groups.
You can apply the policy by following these steps:
In vCenter, go to the Networking and Security page.
Click Service Composer.
In Security Policies, select your policy.
Click Apply.
Select and include your security group or groups.
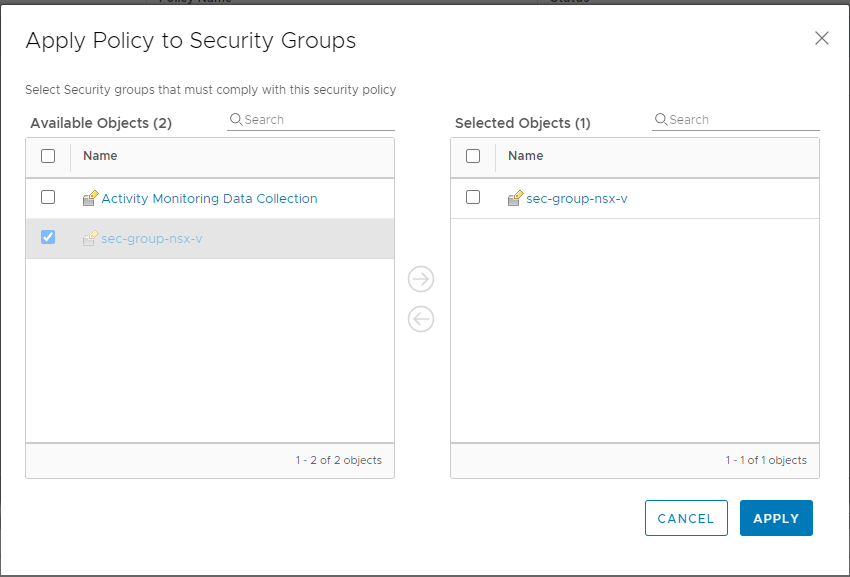
Click Apply.
Change the Security Server password
Once you have deployed the Security Server, you can change the password following these steps:
Using the local interface
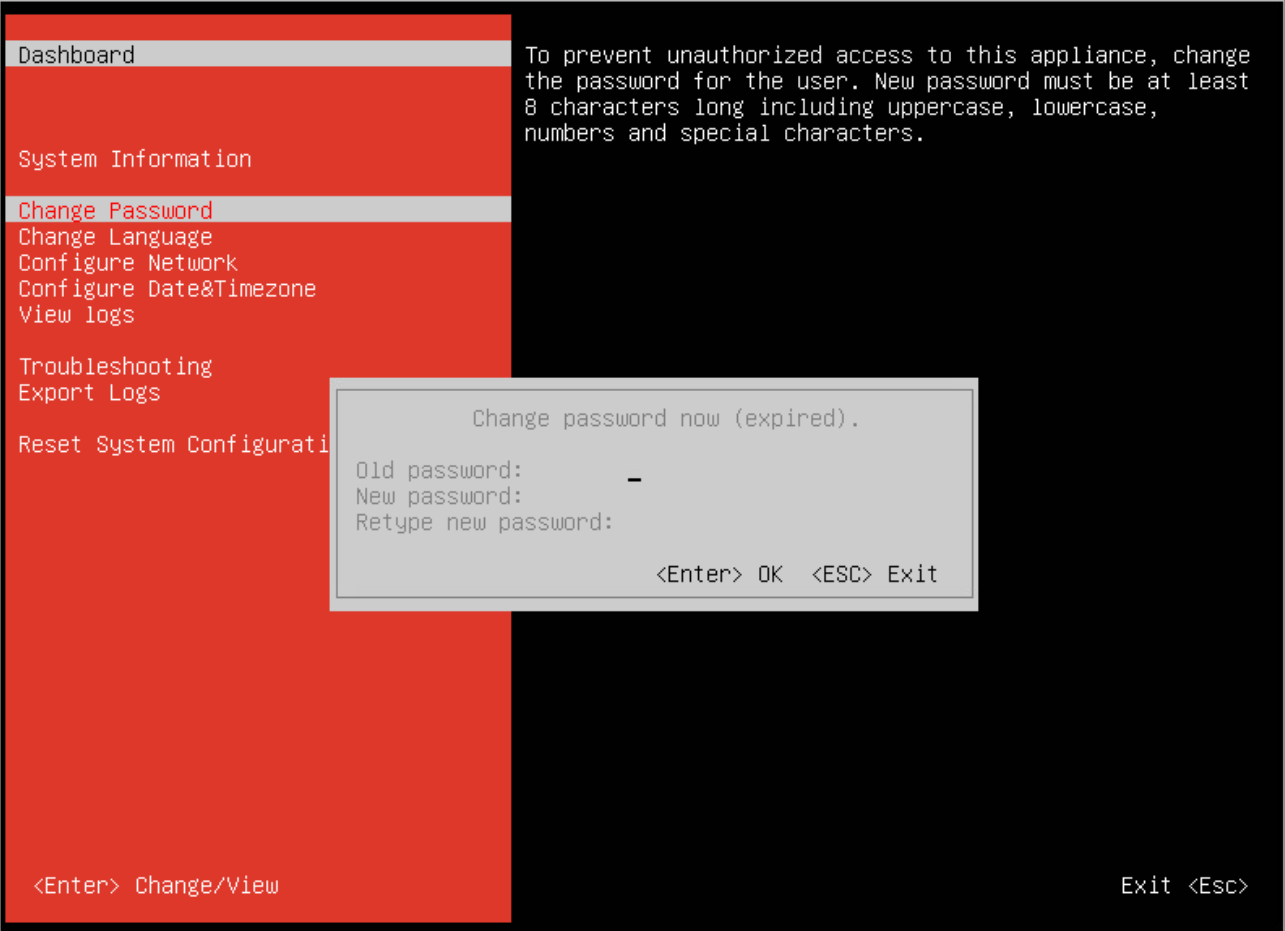
Open the Security Server console.
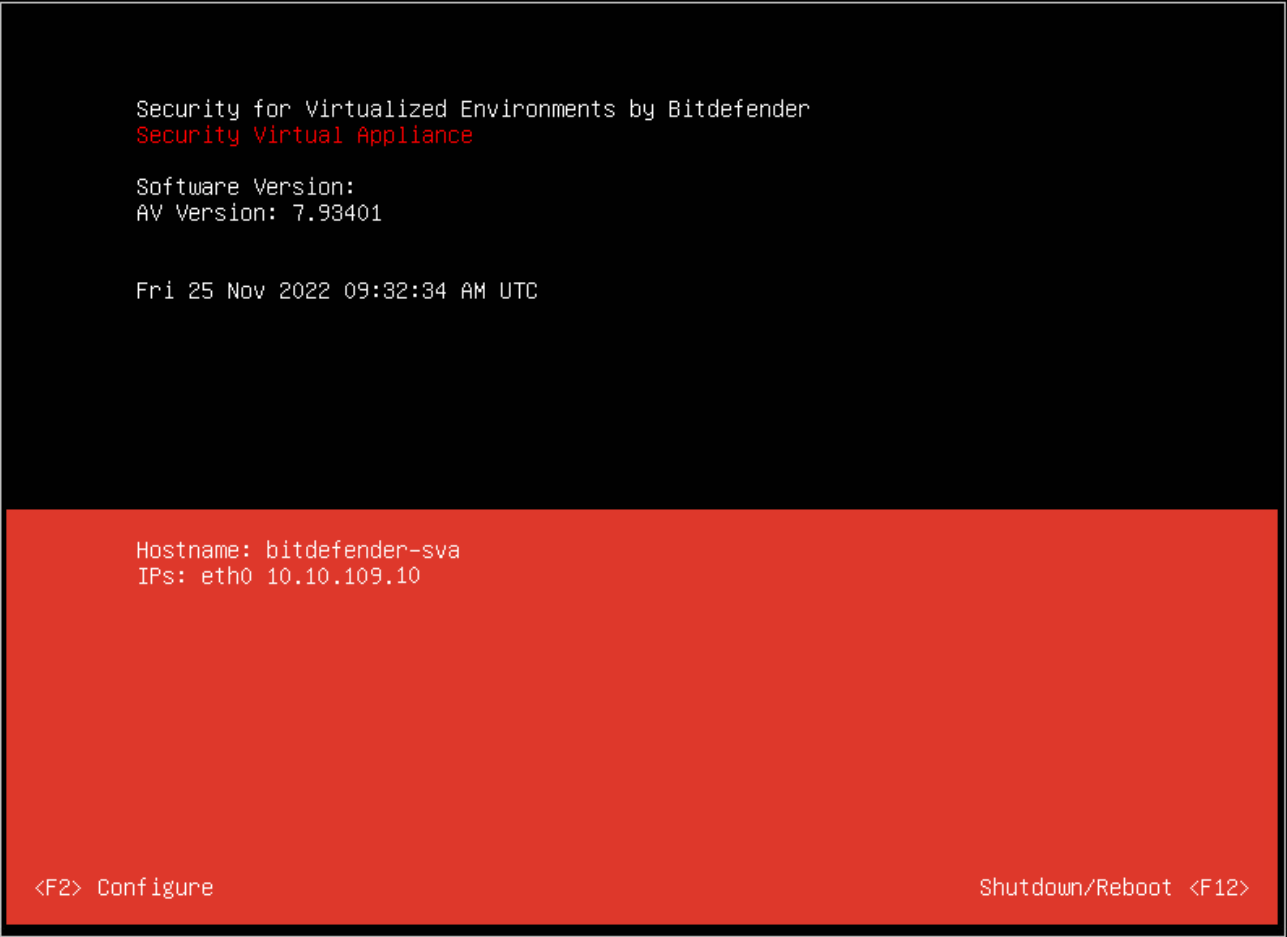
Press F2 to open the configuration screen.
Enter your password. The default password is:
sve.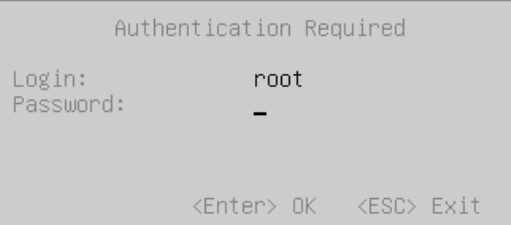
Change the password.
The default password does not meet the new security password requirements, so you have to change it. It must contain at least 8 characters, one digit, at least one upper case character, at least one lower case character, one special character and must be changed every 3 months.
Note
For more information about resetting the root password, refer to Reset root password for Security Server.
Using SSH
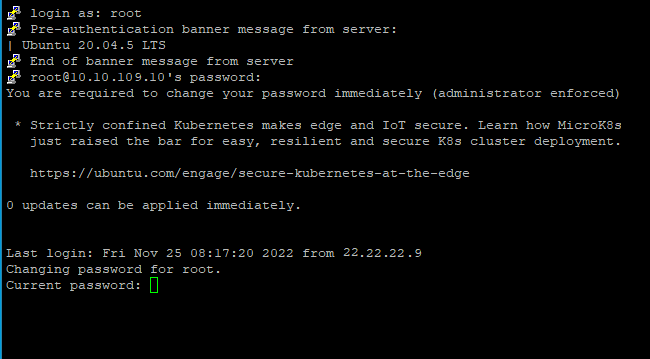
Connect to the appliance via SSH.
Log in using the default credentials.
User name:
rootPassword:
sve
Change the password.
The default password does not meet the new security password requirements, so you have to change it. It must contain at least 8 characters, one digit, at least one upper case character, at least one lower case character, one special character and must be changed every 3 months.
Note
For more information about resetting the root password, refer to Reset root password for Security Server.
Remove the NSX-V integration
To remove the NSX-V integration, follow these steps:
Log in to VMware vSphere Web.
Go to Networking & Security > Service Composers > Security Policies.
Select Security Policies with the Guest Introspection Services name set to Bitdefender and delete all Bitdefender policies.
Go to Networking & Security > Installation and Upgrade > Service Deployments.
Delete the Bitdefender Security Server and Guest introspection VMs.
In GravityZone Control Center, go to Configuration > Virtualization Providers.
In the Action column, go to the corresponding integration that you want removed and click Unregister.
Go to Edit > Installed platform.
Set the type to None.