Patch Management scan error 1627
Patch Scan tasks may fail with error code 1627 on Windows endpoints, after deploying Patch Management in your infrastructure.
This error code is related to missing certificates on the target machines.
The solution is to export the certificates from an endpoint where Patch Scan tasks works properly and to import them on the machines that are failing.
Locate the Certificates. The specific certificates are the following:
DigiCert Trusted Root G4 (found in Trusted Root Certification Authorities)
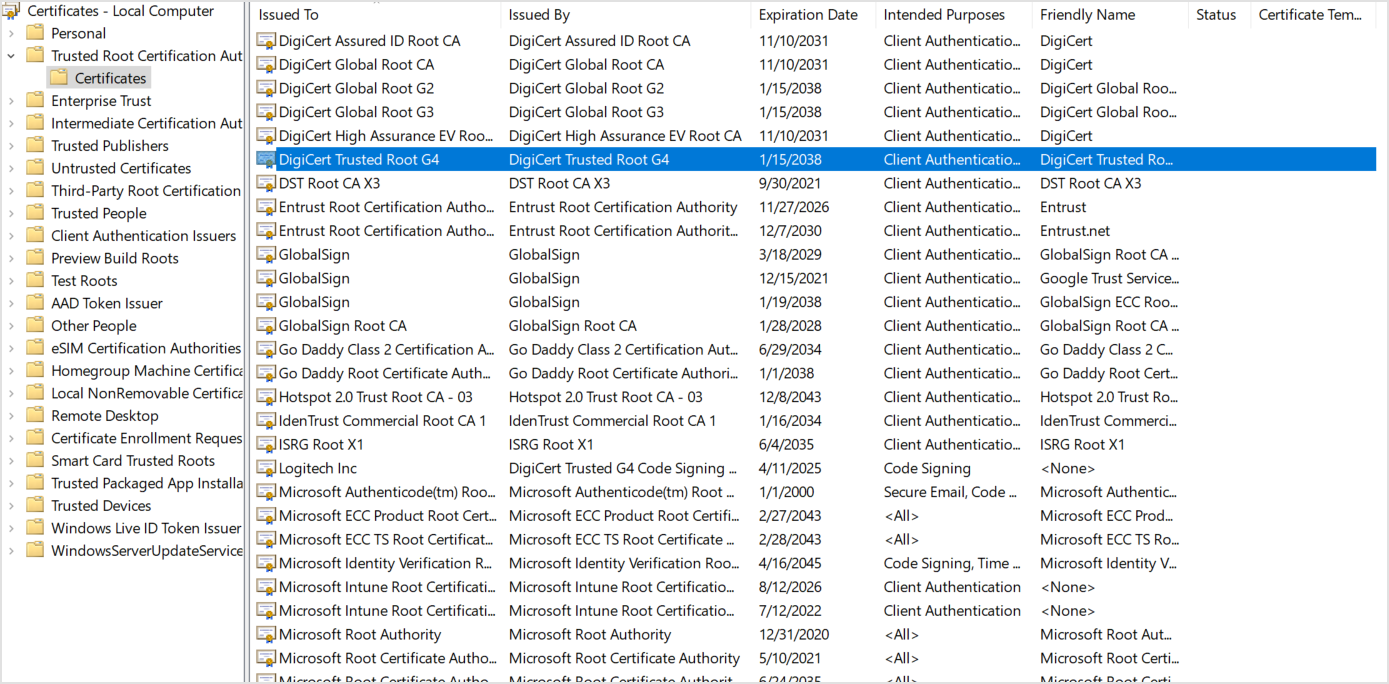
DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA1 (found in Intermediate Certification Authorities)
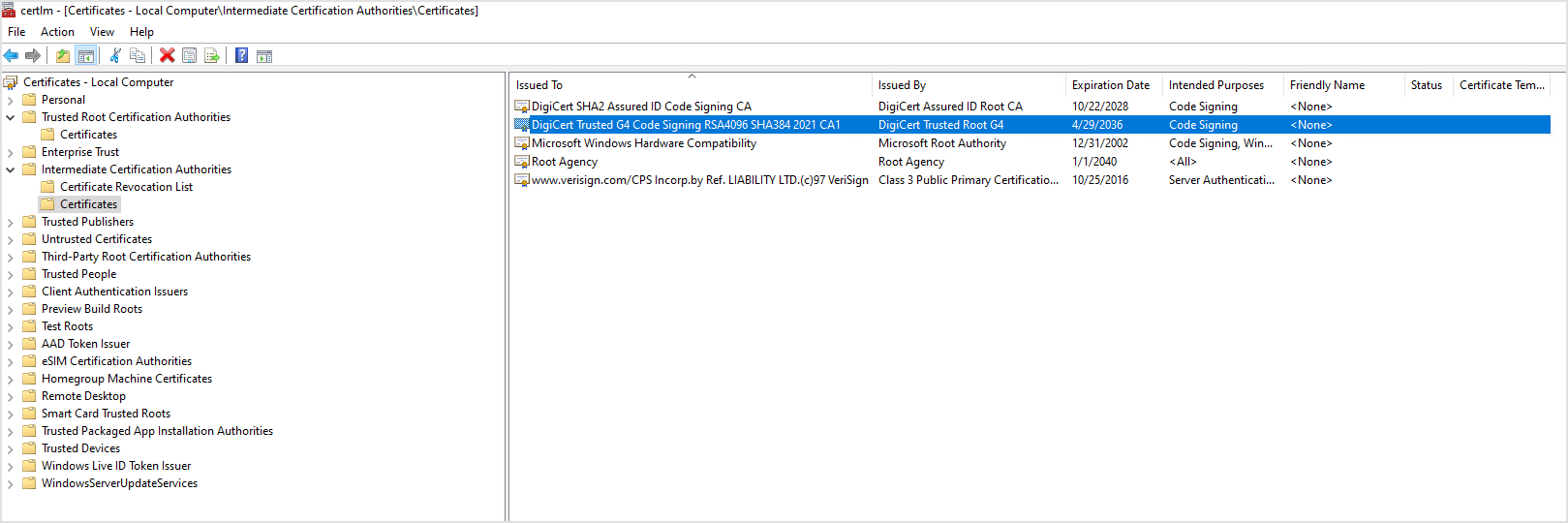
You can find the above certificates in the Local Machine Certificates Store, not in the Local User Certificates Store.
For Windows 8.1 and above, you may access this store by running the command
certlm.msc
For Windows 7, you will need to create a new snap-in as described below:
Start → Run:
mmc.exe
Menu: File → Add/Remove Snap-in…
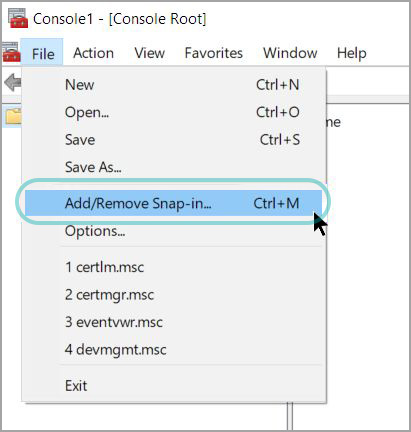
Under Available snap-ins, select Certificates and press Add.
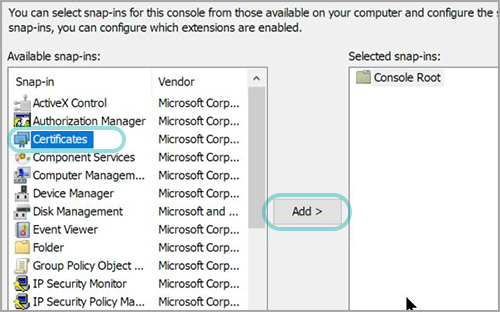
Select Computer Account for the certificates to manage. Press Next
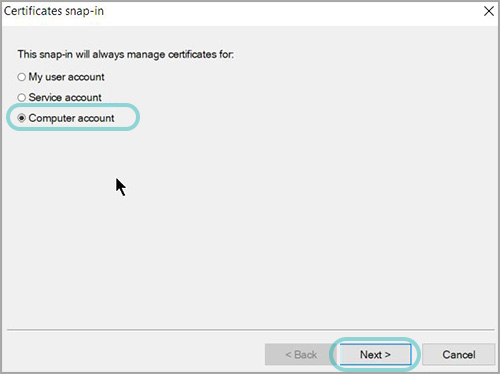
Select Local Computer and press Finish.
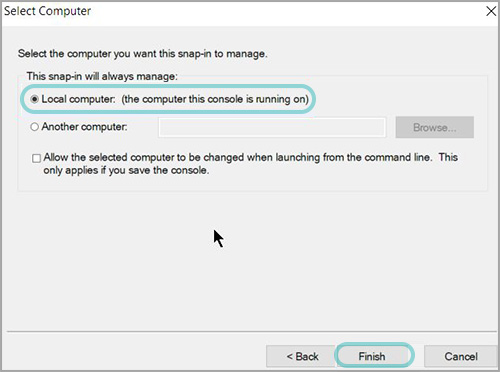
Press OK to return to the management console.
Once you locate the two certificates on one of the machines where Patch Scan is working properly, you will need to export them:
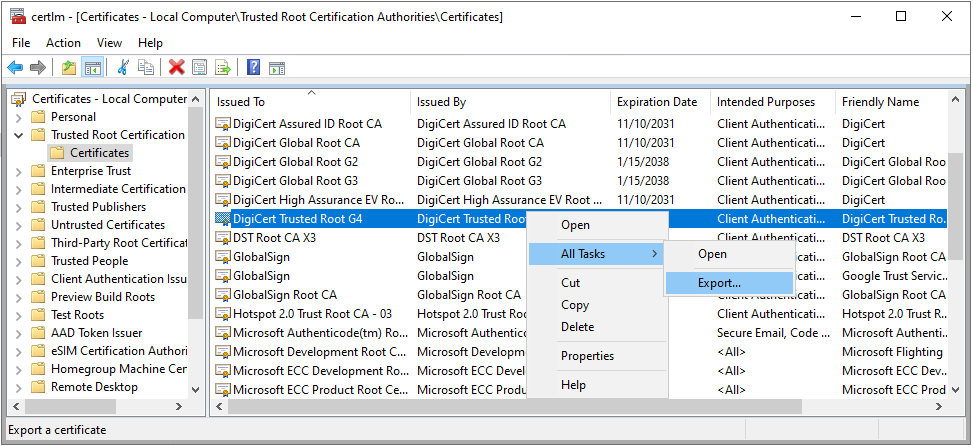
After exporting the two certificates and copying them over to the machine where the Patch Scan task is failing, you will need to import them.
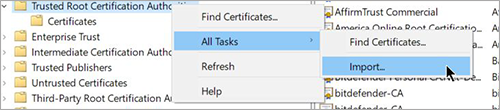
Note
Make sure to import the certificates in the Local Machine Certificates Store and in their proper locations:
DigiCert Trusted Root G4 → Trusted Root Certification Authorities
DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA1 → Intermediate Certification Authorities
Alternative methods to import certificates
If your endpoints are not connected to the internet, you can visit this webpage and download the certificates to use them later on the desired endpoints.
You can import the certificates by using the two commands below:
For DigiCert Trusted Root G4
certutil -addstore "Root" "< path_to_root_certificate >"For DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA1
certutil -addstore "CA" "< path_to_intermediate_certificate >"Note
This method is useful if you have multiple endpoints with the issue described and you need to automatically import certificates via script.
Make sure to run the commands above in Command Line with administrative rights.