Splunk
To set up the link between Splunk and GravityZone follow the steps below.
1. Verify Prerequisites
The following software needs to be installed:
Splunk Common Interface Model app, only 4x versions.
The current Splunk version supports data from features provided by GravityZone version 6.27.1 or higher.
2. Install the Bitdefender Gravityzone for Splunk App
The Bitdefender Gravityzone for Splunk App provides a Dashboard where you can view all the information received from GravityZone, organized into multiple sections and widgets. Using the app you can also search for information or generate reports.
To install the app, follow these steps:
Download the Bitdefender Gravityzone for Splunk App installation package from here.
Log in to Splunk Enterprise.
From the home page, click the Manage Apps button on the upper left side of the screen:
Click the Install app from file button on the right side of the screen.
Click Browse....
Select the package downloaded from step 1.
Click Upload.
3. Install the Bitdefender Gravityzone Add-on for Splunk
The Bitdefender Gravityzone Add-on for Splunk supports the Bitdefender Gravityzone App for Splunk by providing source mapping, data extractions and transformations. It acts like a parser, converting all data gathered from various Bitdefender sources into a CIM format, which is compatible with Splunk.
To install the app, follow these steps:
Download the Bitdefender Gravityzone Add-on for Splunk installation package from here.
Log in to Splunk Enterprise.
From the home page, click the Manage Apps button on the upper left side of the screen:

Click the Install app from file button on the right side of the screen.
Click Browse....
Select the package downloaded from step 1.
Click Upload.
4. Configure GravityZone to send notifications to the Bitdefender Gravityzone for Splunk App instance using the Syslog protocol
Connect to the GravityZone Control Center.
Go to the Configuration page from the left side menu and click Miscellaneous.
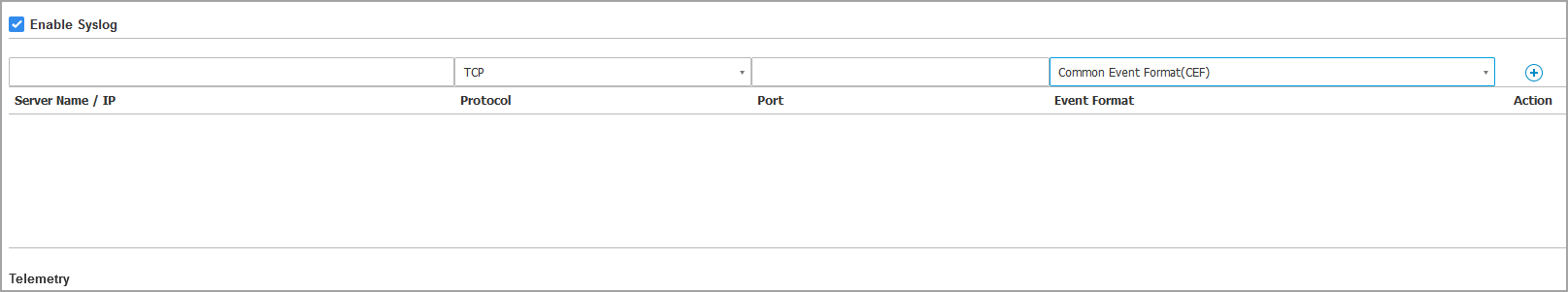
Select the Enable Syslog check box.
Enter the IP address of the Splunk instance, the preferred protocol and the port Syslog listens to.
Select the format json to send the data to the Syslog server.
Click the Add button from the Action column.
To select the events you want to receive on the Splunk instance:
Connect to the GravityZone Control Center.
Click the Notification button at the right side of the menu bar and then click the Settings icon.
Under Enable Notification section, choose the type of notifications you want to receive from GravityZone and select the Log to server checkbox.
5. Configure Splunk to accept data using the Syslog protocol
Log in to Splunk Enterprise.
On the upper right side of the screen click Settings and select Data Inputs.
Select TCP or UDP under the Local inputs section.
Click the New local TCP or the New local TCP button from the upper right side of the screen.
Select either a TCP or a UDP port.
Fill in the Port field and, optionally, the Source name overwrite and Only accept connection from fields.
Click Next.
Under Source type, click Select, and choose the
bitdefender:gzoption.Under App context, select
TA-bitdefender-gravityzone.Under Host, enter the appropriate IP, DNS or type in a custom host value.
Under Index, select the one where you want to store your data.
Click the Review button on the upper side of the screen and verify the information.
Click Submit.