- ON PREMISES SOLUTIONS
- Getting started
- Feature specific deployment guides
- Advanced Threat Control
Advanced Threat Control
For threats that elude even the heuristic engine, another layer of protection is present in the form of Advanced Threat Control (ATC).
Advanced Threat Control continuously monitors running processes and grades suspicious behaviors such as attempts to: disguise the type of process, execute code in another process's space (hijack process memory for privilege escalation), replicate, drop files, hide from process enumeration applications, etc. Each suspicious behavior raises the process rating. When a threshold is reached, an alarm is triggered.
Components
Advanced Threat Control uses the following components:
GravityZone Virtual Appliance
Security agent (Bitdefender Endpoint Security Tools)
Security Server Multi-Platform
Security Server for NSX-T
Security Server for NSX-V
Install and configure Advanced Threat Control
There are three possible scenarios for installing this feature on your endpoints:
An endpoint does not have the BEST agent installed. In this case, use the Create an installation package procedure.
An endpoint has the BEST agent installed, but Advanced Threat Control is not included in the modules list. In this case, use the Add Advanced Threat Control using a Reconfigure agent task procedure.
An endpoint has the BEST agent installed, and the Advanced Threat Control module is included. In this case, go directly to the Configure and enable the Advanced Threat Control feature section.
Add the module using a Reconfigure agent task:
Log in to GravityZone Control Center.
Go to the Network page from the left side menu and select the endpoints you want to add the module on.
Click the Tasks button and select Reconfigure agent.
Under Modules select Add and enable Advanced Threat Control.
Note
For more information on using the Reconfigure agent task, refer to Reconfigure agent.
Click Save.
The task will now install the Advanced Threat Control module on all selected endpoints.
Create an installation package:
Log in to GravityZone Control Center.
Go to the Installation Packages page from the left side menu.
Click the Create button in the upper-right side of the screen.
Type in the Name and Description for the new installation package.
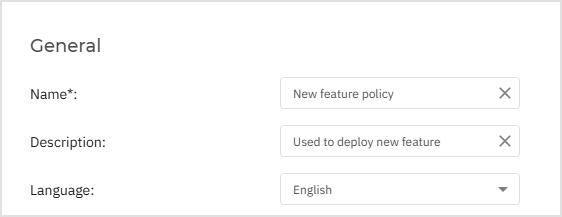
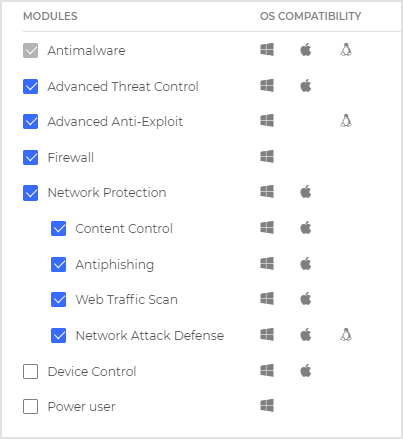
Select the modules you want to include.
Note
Make sure you include the Advanced Threat Control module.
Click Save.
Select the newly created package from the list of packages and click Send download links.
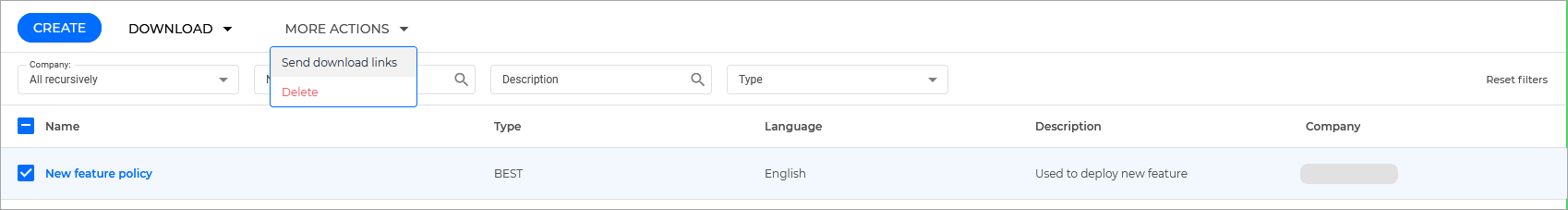
Enter the email addresses of the recipients and click Send.
Policies are used to enable and configure features both on endpoints and in terms of general functionality.
GravityZone comes with a default set of policy settings, that are custom tailored to meet the most common customer needs. These policies are applied, by default, to endpoints, after the BEST agent is installed. You cannot modify or delete the default GravityZone policy.
You can use these default policy settings and leave the configuration of the policy for a later date, or customize the feature using the steps below:
Log in to GravityZone Control Center.
Go to the Policies page from the left side menu.
You can either:
Under Antimalware > On-execute > Advanced Threat Control, enable and configure the module.
Save your policy.
If you created a new policy, apply it on the endpoints where the feature is installed.
Go to the Network page.
Select the endpoints you want to apply the policy to.
Click the
 Assign Policy button at the upper side of the table.
Assign Policy button at the upper side of the table.Select the policy you want to apply.
Click Finish.
Note
For more information, refer to Assigning device policies
If you have edited an existing policy, make sure it is applied to all endpoints where the feature is installed.
This will ensure that the feature is enabled and configured to best suit your company's needs.
Test out Advanced Threat Control
You can test ATC by following this procedure:
Go to the endpoint on which you want to test out ATC.
Click this link to download a tool that will simulate a malicious process.
Extract the contents of the
.zipfile, using the passwordinfected.Open the folder that matches your operating system.
Run the
AtcPocDetection.exefile with administrator privileges.
The application will trigger the ATC feature which will block it from launching.
The agent logs on the endpoint will show something similar to this:
Advanced Threat Control has started a disinfection action on a process detected as malicious. Process path: C:\Users\User\Downloads\x64\Release\AtcPocDetection.exe. Threat name: ATC.SuspiciousBehavior.558724252A537866.
You can also find records related to this detection by going to the GravityZone Control Center and running a report task.
Advanced Threat Control continuously monitors the applications running on the endpoint, looking for malware-like actions. Each of these actions is scored and an overall score is computed for each process. When the overall score for a process reaches a given threshold, the process is considered to be harmful. Advanced Threat Control will automatically try to disinfect the detected file. If the disinfection routine fails, Advanced Threat Control will delete the file.
Before applying the disinfect action, a copy of the file is sent to quarantine so as you can restore the file later, in the case of a false positive. This action can be configured using the Copy files to quarantine before applying the disinfect action option available in the Antimalware > Settings tab of the policy settings. This option is enabled by default in the policy templates.
You can find all the files that were sent into quarantine by going to the Quarantine page.
Log in to GravityZone Control Center.
Go to the Quarantine page from the left side menu.
Apply the filters required for the files and period you are looking for.
Explore the results.
You can also get information regarding the activity of the feature from the following reports:
Customer Status Overview
Endpoint Modules Status
Endpoint Protection Status
Executive Summary
Malware Status
Security Audit
Top 10 Detected Malware
Top 10 Infected Companies
Top 10 Infected Endpoints
Note
For more information refer to Report types.
Portlets provide you with security event information from your environment. You can customize the portlets and create your own, specifying the protection mechanism you would like the monitor and the time interval you would like to see in the data.
For information on how to create and manage portlets, refer to Dashboard.
Note
There is a portlet available for each report type provided by the console.