Security management
In GravityZone, you can use security policies and perform tasks to protect your network inventory. On this page, you learn what are policies and tasks, and why they are important to you as GravityZone user.
Further, this documentation section covers the following topics:
Policy flow management in GravityZone (create, configure, assign policies etc,).
Major GravityZone features that you enable through policies, but you operate them mostly outside policies. Such features refer to EDR/XDR, Risk Management, Integrity Monitoring, and the quarantine.
Best practices and troubleshooting articles on GravityZone features enabled through policies.
See the list with specific topics at the end of this page.
Understanding security policies
The Bitdefender protection can be configured and managed from Control Center using security policies. A policy specifies the security settings to be applied on target network inventory objects (computers, virtual machines, containers, or mobile devices).
Immediately after installation, network inventory objects are assigned with the default policy, which is preconfigured with the recommended protection settings. Provided the NSX integration is enabled, another three default security policies for NSX are available, one for each security level: permissive, normal and aggressive. These policies are preconfigured with the recommended protection settings. You cannot modify or delete the default policies.
You can create as many policies as you need based on security requirements, for each type of managed network object.
This is what you need to know about policies:
Policies are created in the Policies page and assigned to network objects from the Network page.
Policies can inherit several modules settings from other policies.
Endpoints can have one active policy at a time.
Policies are pushed to target network objects immediately after creating or modifying them. Settings should be applied to network objects in less than a minute (provided they are online). If a network object is not online, settings will be applied as soon as it gets back online.
The policy applies only to the installed protection modules.
The Policies page displays only the following types of policies:
Policies created by you.
Other policies (such as default policy or templates created by other users) which are assigned to endpoints under your account.
You cannot edit policies created by other users (unless the policy owners allow it from the policy settings), but you can override them by assigning the target objects a different policy.
Warning
Only the supported policy modules will apply to target endpoints.
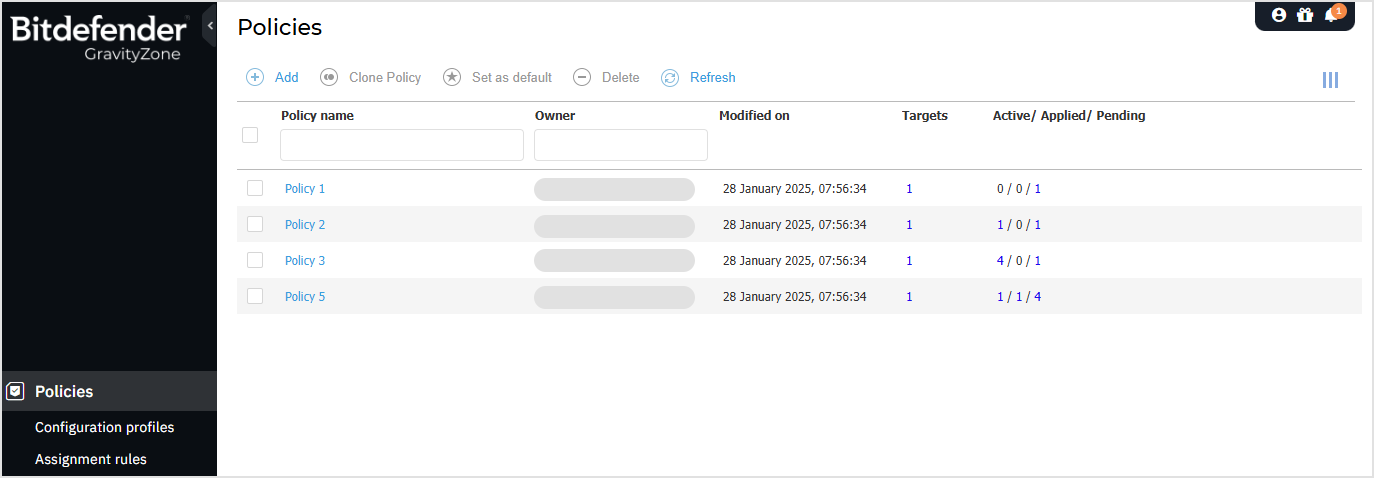
Policies page
You can view and manage policies in the Policies page.
Each type of endpoint has specific policy settings. To manage policies, you must first select the type of endpoint (Computers and Virtual Machines or Mobile Devices) from the views selector.
The table presents current policies, showcasing details such as:
Policy name.
Policy owner.
Date and time when the policy was last modified.
In the Targets column, the total number of endpoints and folders where the policy was directly applied.*
In the Active/Applied/Pending column, the number of endpoints where the policy is active, applied or pending. The policy can be directly applied or inherited.*
Note
* Clicking the number will redirect you to the Network page, where you can view the corresponding endpoints. You will be asked to choose the network view. This action will create a filter using policy criteria.
For policies with NSX module enabled, additional information is available:
The NSX policy name, used to identify the Bitdefender policy in VMware vSphere.
Policy visibility in the management consoles, allowing you to filter the policies for NSX. Thus, while Local policies are visible only in Bitdefender Control Center, Global policies are also visible in VMware NSX.
These details are hidden by default.
To customize the policy details displayed in the table:
Click the Columns button at the right side of the Action Toolbar.
Select the columns you want to view.
Click the Reset button to return to the default columns view.
You can sort the available policies and search for certain policies using the available criteria.
Understanding tasks
Besides security policies, you can use actions on the Network page to execute remote operations, or tasks, on endpoints. These tasks include:
For details on how you configure and perform tasks, refer to running tasks on computers, virtual machines, and mobile devices. Once created, you can monitor the tasks progress in the Network > Tasks page.