“Didn’t you say you had it under control?” Discover why smart security teams choose GravityZone — before the chaos hits. Learn More >>
The MITRE ATT&CK framework (usually pronounced "mitre attack" /ˈmaɪtɚ əˈtæk/) is a globally recognized knowledge base that categorizes adversary tactics, techniques, and procedures (TTPs) based on real-world cyber threats. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge, reflecting its purpose as a structured reference for understanding how cybercriminals operate throughout the attack lifecycle.
Unlike traditional security models that focus on indicators of compromise (IoCs), MITRE ATT&CK emphasizes how attacks unfold, helping organizations move beyond reactive defenses to proactive threat detection and mitigation.
The framework has reshaped cybersecurity strategies by providing a common language for security professionals, enhancing:
Beyond individual organizations, the framework influences industry-wide security evaluations, including MITRE Engenuity’s ATT&CK Evaluations, which assess how well security solutions detect adversarial techniques.
MITRE, a U.S.-based nonprofit that operates federally funded research and development centers (FFRDCs), developed ATT&CK in 2013 as part of a research initiative to improve threat detection. Initially focused on Windows enterprise environments, the framework has since expanded to cover macOS, Linux, mobile, cloud, and industrial control systems (ICS).
ATT&CK has evolved into a living framework that is continuously updated with emerging adversary behaviors and techniques observed in real-world attacks. This ensures security teams have the latest intelligence to strengthen their defenses.
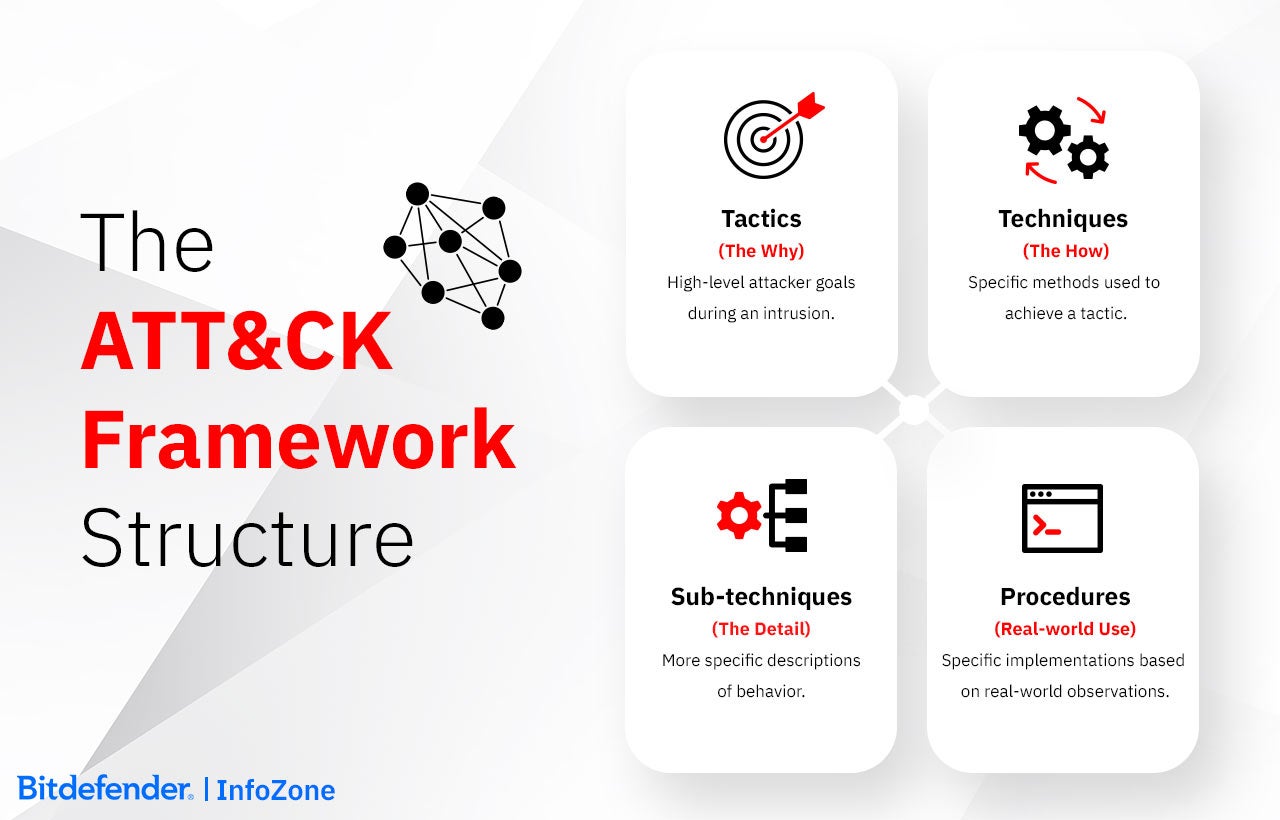
At its core, the MITRE ATT&CK framework is built around Tactics, Techniques, and Procedures (TTPs) and is organized into specialized matrices tailored to different environments.
Tactics: The Objectives of an Attack
Tactics define WHY an adversary takes a specific action at different stages of an attack in the form of high-level attack objectives, such as Initial Access, Privilege Escalation, Lateral Movement, and Exfiltration. Each tactic provides defenders with a structured way to anticipate adversary actions and align their security measures accordingly.
Techniques: How Adversaries Execute Their Attacks
Techniques describe HOW adversaries accomplish their objectives. Each technique outlines a specific method used to achieve a tactic. For example, within Credential Access, attackers may employ brute force attacks, credential dumping, or keylogging. The goal of this MITRE ATT&CK framework approach is to give organizations ways to improve their detection, mitigation, and response strategies against real-world threats.
Sub-techniques: Refining Attack Methods
Sub-techniques break down techniques into more specific implementations, providing a finer level of detail. For example, the phishing technique includes sub-techniques such as spear-phishing via email attachments, malicious links, or compromised services. This granularity allows security teams to develop precise defensive measures tailored to different variations of an attack method.
Procedures: Real-World Attack Implementation
Procedures document how specific adversary groups apply techniques and sub-techniques in actual cyberattacks. Unlike tactics and techniques, which provide general classifications, procedures detail real-world implementations observed in threat intelligence reports. For example, an APT (Advanced Persistent Threat) group may use PowerShell commands to extract credentials from memory. Understanding these real-world applications enables security teams to simulate attacks, refine response plans, and improve detection capabilities.
To provide a targeted view of adversary behaviors, the MITRE ATT&CK framework is divided into matrices that focus on different technology environments.
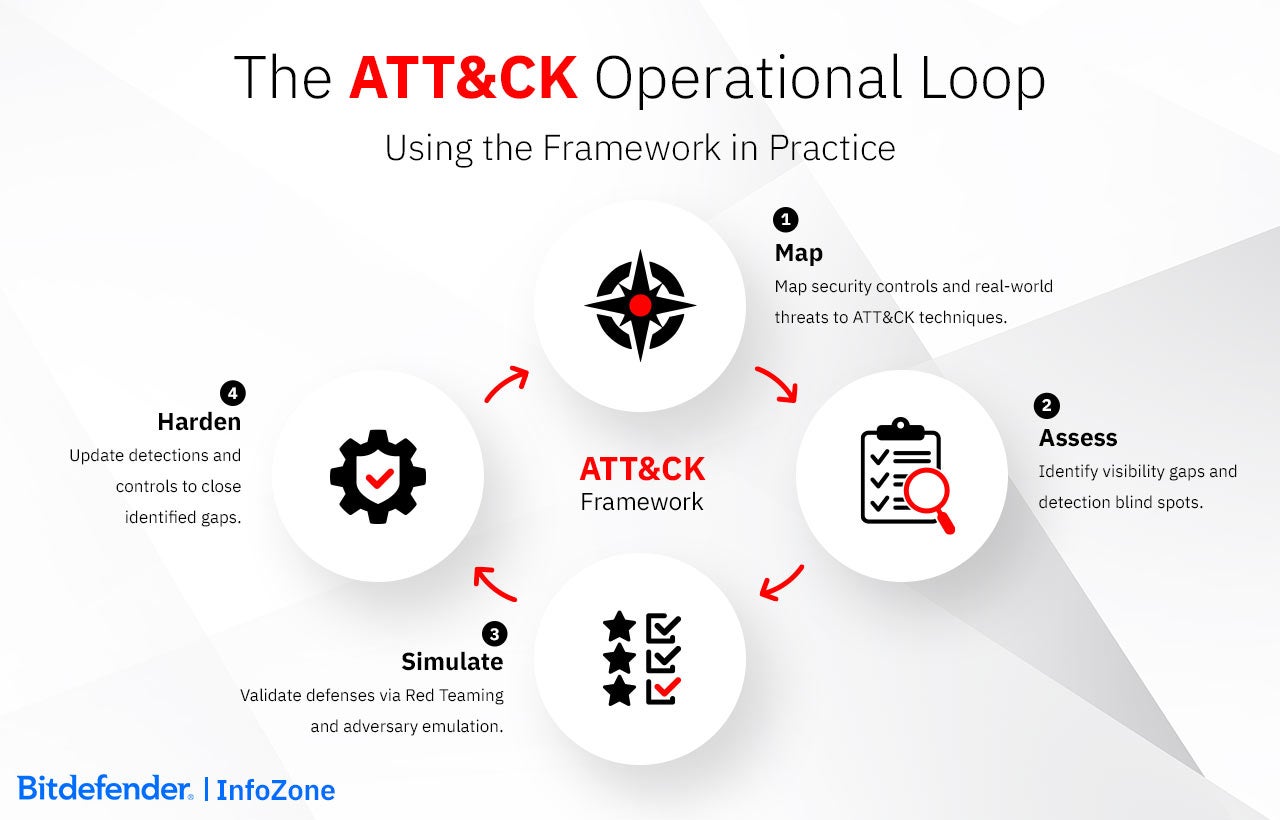
For security analysts, threat hunters, and SOC teams, the framework bridges the gap between threat intelligence and real-world defense strategies. Teams can map security events to known adversary behaviors, allowing for:
Integrating ATT&CK into security workflows allows organizations to reduce noise and accelerate investigation and remediation.
Enhancing Security Posture - The framework provides a data-driven approach to evaluating and improving cybersecurity defenses. Organizations can use it to:
By leveraging ATT&CK, organizations move from a reactive defense model to proactive threat management, ensuring they are prepared for real-world attacks rather than just meeting compliance checklists.
Strategic Advantages for Businesses - The MITRE ATT&CK framework is not just a technical tool - it provides strategic value by helping organizations make informed decisions on risk management, cybersecurity spending, and security operations. Industries that rely heavily on ATT&CK include:
When security efforts are aligned with real-world adversary tactics, businesses can reduce their attack surface, improve operational resilience, and ensure long-term cybersecurity readiness.
Facilitating Compliance with Regulatory Standards - The MITRE ATT&CK framework is widely recognized in regulatory and compliance landscapes, including NIST, ISO 27001, PCI DSS, and GDPR. It helps organizations:
By integrating ATT&CK into compliance efforts, organizations create security programs that are both effective and auditable, ensuring they meet regulatory standards while staying ahead of evolving threats.
Threat Detection and Hunting
Traditional signature-based detection methods often fail against sophisticated attacks. The MITRE ATT&CK framework shifts detection toward behavior-based analysis, allowing security teams to:
Integrating ATT&CK into security platforms allows teams to detect attacks earlier by focusing on behaviors rather than just signatures.
Security Control Validation and Gap Analysis
Organizations use the MITRE ATT&CK framework to assess how well their existing security controls detect and prevent adversary techniques. By mapping security tools and monitoring capabilities to ATT&CK, teams can:
Security Incident Response
During an attack, rapid response is critical. The MITRE ATT&CK framework improves incident response efficiency by:
Threat Modeling and Adversary Simulation
The framework serves as a foundation for threat modeling and adversary simulation, enabling security teams to:
Informing Risk Management Strategies
The framework helps organizations make data-driven decisions about cybersecurity risks by:
By incorporating ATT&CK into risk assessment frameworks, organizations can strategically reduce their attack surface and improve overall resilience.
Incident Response Teams use ATT&CK to build structured playbooks that map specific adversary techniques to response procedures, enabling faster containment during active incidents.
Threat Hunters leverage the framework to create hypothesis-driven searches based on techniques commonly used against their industry rather than relying solely on general threat feeds.
SOC Analysts integrate ATT&CK into SIEM dashboards by mapping alerts to specific techniques, significantly reducing alert fatigue and improving triage effectiveness.
Cloud Security Teams apply the framework to address unique challenges in multi-cloud environments, particularly focusing on identity management, privilege escalation, and account takeover techniques.
Implementing MITRE ATT&CK should be approached in phases. This way, organizations can gradually align their security controls, processes, and teams with the framework.
At a glance
|
Phase |
How |
|
1. Define Your Objectives |
Identify whether ATT&CK will be used for threat detection, incident response, security validation, or a combination of these functions. |
|
2. Start with High-Impact Techniques |
Focus on key attack techniques that are most relevant to your industry and risk profile before expanding coverage. |
|
3. Map ATT&CK to Security Tools |
Determine how SIEM, EDR, and threat intelligence platforms align with ATT&CK techniques to assess detection coverage. |
|
4. Embed ATT&CK into Workflows |
Integrate it into threat hunting, security monitoring, incident response, and red teaming exercises. |
|
5. Continuously Evaluate & Improve |
Update ATT&CK mappings, refine security strategies, and adapt to new adversary techniques as they emerge. |
Key tools for ATT&CK implementation include MITRE's own ATT&CK Navigator for mapping techniques to controls, CALDERA for adversary emulation, and open-source resources like Atomic Red Team for testing defenses.
Before implementing ATT&CK, organizations must assess their current security posture to determine where improvements are needed. This involves:
This assessment provides a clear roadmap for implementing the framework in a way that directly addresses security gaps.
To maximize its value, MITRE ATT&CK should be embedded into core cybersecurity operations rather than treated as a standalone reference. Customizing the framework to your specific threat landscape maximizes security effectiveness.
Key integration areas include:
Since cyber threats are constantly evolving, organizations should treat MITRE ATT&CK implementation as an ongoing process. Best practices include:
The MITRE ATT&CK framework is highly effective, but organizations may encounter challenges during implementation. Some of the most common pitfalls are:
While Lockheed Martin's Cyber Kill Chain maps attacks as linear progressions ideal for strategic planning, MITRE ATT&CK provides a detailed matrix of specific techniques better suited for tactical detection and response. The Cyber Kill Chain helps disrupt attacks at early stages, while ATT&CK enables real-time identification of adversary behaviors. Organizations achieve comprehensive security by implementing both frameworks together - combining high-level attack lifecycle visibility with granular technique detection.
Organizations use the framework to assess, validate, and optimize security controls by:
Bitdefender consistently ranks as a top performer in MITRE Engenuity ATT&CK Evaluations, demonstrating industry-leading detection, fast response times, and high-fidelity alerts that cut through the noise.
At the core of our MITRE-aligned approach is the Bitdefender GravityZone Platform and Services, a unified security and risk analytics solution that provides:
Bitdefender’s performance in MITRE ATT&CK Evaluations for Managed Services underscores its leadership in security effectiveness. With 100% detection coverage, one of the fastest mean times to detect (MTTD), and minimal alert noise, Bitdefender ensures security teams can focus on real threats, not distractions.
Yes, small businesses can and should use the MITRE ATT&CK framework, though they may need to adapt their implementation approach. Small businesses can start by focusing on high-risk techniques most relevant to their industry, prioritizing critical assets, and leveraging managed security services that incorporate ATT&CK. While enterprise-wide implementation may require significant resources, small businesses can adopt a targeted approach that addresses their most pressing security concerns while gradually expanding coverage as resources allow.
The MITRE ATT&CK framework, while powerful, has inherent limitations that organizations should understand:
Reactive by design - ATT&CK documents observe adversary techniques rather than predict new ones. This means there's always a gap between emerging attack methods and their documentation in the framework. Organizations need supplementary threat intelligence to stay ahead of evolving threats.
Focus on tactics rather than comprehensive prevention - While ATT&CK outlines what attackers do, it doesn't provide detailed prevention strategies. Organizations must integrate ATT&CK insights with other security frameworks and best practices to build holistic defense strategies.
Not a compliance solution on its own - Though ATT&CK enhances compliance efforts, it doesn't replace structured compliance frameworks. Organizations still need dedicated compliance programs that incorporate ATT&CK as one component.
Requires continuous context updates - ATT&CK techniques require contextual understanding specific to your environment. Without regularly updating this context to match your evolving infrastructure, the framework's value diminishes.
Limited visibility into attacker motivation - ATT&CK documents how attacks occur but provides less insight into why specific organizations are targeted. This limitation makes it difficult to fully predict which techniques are most relevant to your specific risk profile.
MITRE updates the ATT&CK framework approximately 2-3 times per year, with major updates typically released every six months. These updates include new techniques, sub-techniques, and refinements to existing content based on evolving threat landscape observations. Organizations should establish a regular review of these updates and incorporate relevant changes into their security operations.