Cybersecurity Predictions 2026: Understand how ransomware, AI control failures, and APT experimentation are converging in 2026. Register Now >>
Gain a comprehensive view of your current cybersecurity posture, aligned with leading frameworks and tailored to your organization’s specific risks, regulatory environment, and business context.
Focus your efforts with a business-aligned roadmap that helps you identify gaps, guide investment decisions, and take action where it matters most.
Turn expert insights into meaningful improvements by connecting people, policies, and controls to strengthen your long-term security and compliance program.
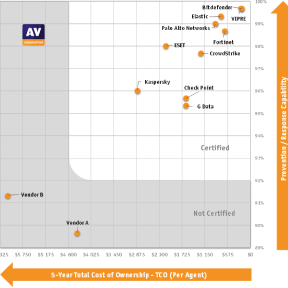
Bitdefender achieved top breach prevention and lowest TCO and was the only vendor to block 100% of attacks during the first stage.
Bitdefender GravityZone Endpoint Security received the AV-TEST Award 2023 for Best Protection and Best Performance in the business users category.

Bitdefender achieved 100% analytical coverage for both Linux and macOS, with zero False Positives (FPs) in both cases.

A Customers’ Choice in Gartner® Peer Insights™
Voice of the Customer for EPPs



Your team certainly can, but a third-party assessment is likely to be more accurate because external experts bring an objective perspective free from internal biases. This is also a time-consuming endeavor that can be off-loaded to our senior consultants.
Depending on the scope (based on the tier you pick ) and the size of your organization, this should range between 2 to 6 weeks. The only thing your team needs to do is to provide access to documents and systems and be part of interviews.
Bitdefender has consultants across the world, and we are experienced across sectors. We’re able to run an assessment against all major frameworks that are country or sector specific. This includes DORA, NIS 2, MAS TRM, PCI DSS, HIPAA, and IEC 62443. We can even run an assessment based on the internal framework that is specific to your organization or industry.
A penetration test is a targeted real-world simulated attack against a specific system or application to identify exploitable vulnerabilities. Our Cybersecurity Review is not a simulated attack, but a systematic and strategic assessment of your organization's security posture.
We’re here to help you gain visibility, plan cybersecurity investments, and accelerate the certification process for your desired cybersecurity framework.