“Didn’t you say you had it under control?” Discover why smart security teams choose GravityZone — before the chaos hits. Learn More >>
Ransomware as a Service (RaaS) is a method of distributing and deploying ransomware (a type of malicious software, blocks access to a computer system or encrypts files until a ransom is paid) using the Software as a Service (SaaS) business model, offering advanced tools on a subscription or profit-sharing basis.
Ransomware attacks used to be isolated incidents before RaaS platforms enabled widespread attacks, and today, even individuals lacking extensive technical knowledge can initiate devastating attacks, often with losses amounting to millions of US dollars.
RaaS platforms operate on the dark web and often offer facilities such as customer support and regular updates to streamline the process of executing attacks and maximize profits. Basically, RaaS democratizes access to ransomware, complicating the efforts to combat cybercrime, as it blurs jurisdictional boundaries and disperses accountability among a network of independent actors, including developers, operators, and affiliates. The spread of RaaS has become a major concern for businesses, governments, and cybersecurity professionals worldwide.
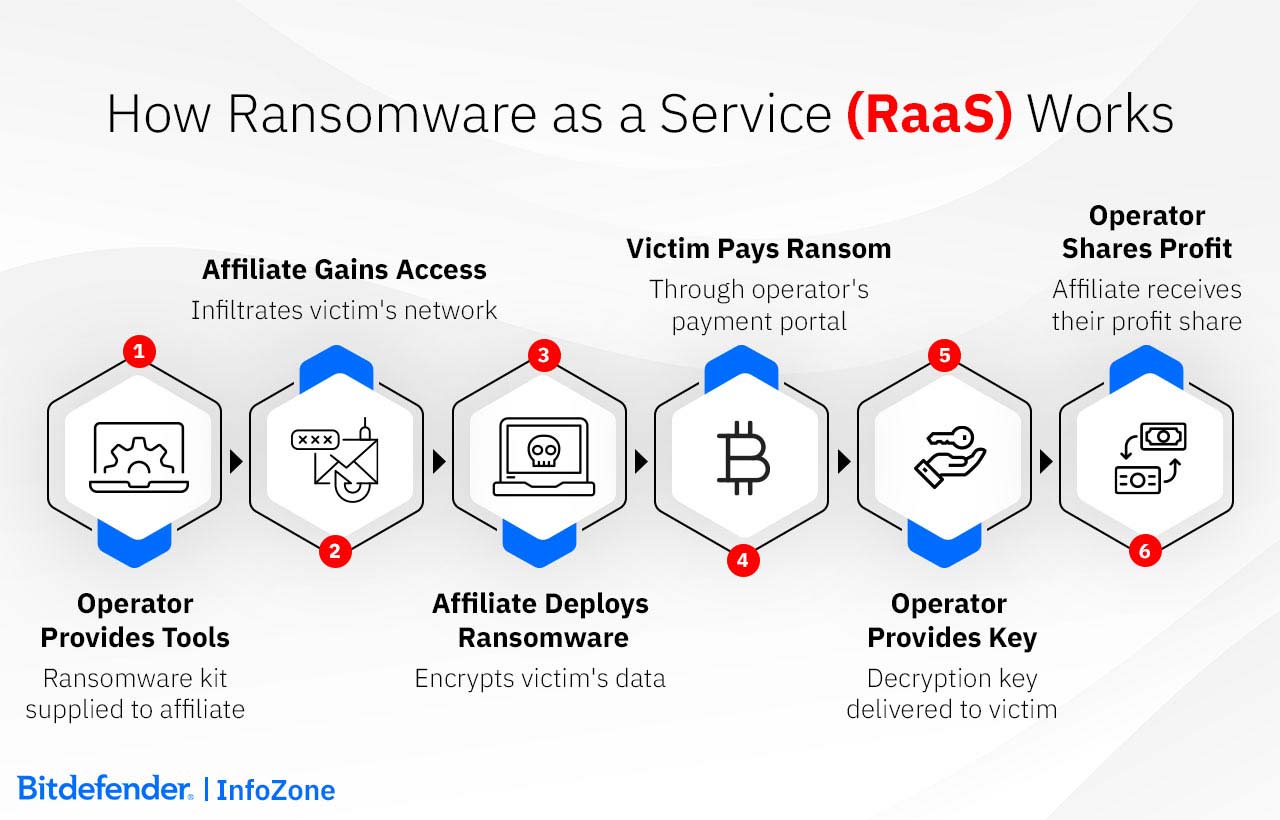
By adopting the Software as a Service (SaaS) model, Ransomware as a Service (RaaS) makes cyber extortion accessible to a broad audience, not only to a traditional cybercriminal profile. This illegal business model creates an ecosystem where ransomware developers, or RaaS operators, lease or sell their ransomware tools to affiliates under various arrangements.
RaaS platforms often feature user-friendly interfaces, offering tools and services such as customizable ransomware variants, command and control (C&C) dashboards for tracking attacks, and victim payment portals. Also common are support services, including assistance with victim negotiations and access to dedicated leak sites for data extortion. RaaS operations are often marketed with a level of professionalism and customer support that matches legitimate SaaS offerings. Operators actively recruit affiliates through forums and even complex marketing campaigns.
The competitive nature of the RaaS market encourages continuous innovation among providers, who enhance their offerings with new features like victim-specific ransomware attributes, which complicate decryption efforts. This adaptability makes RaaS a persistent and evolving challenge within cybersecurity.
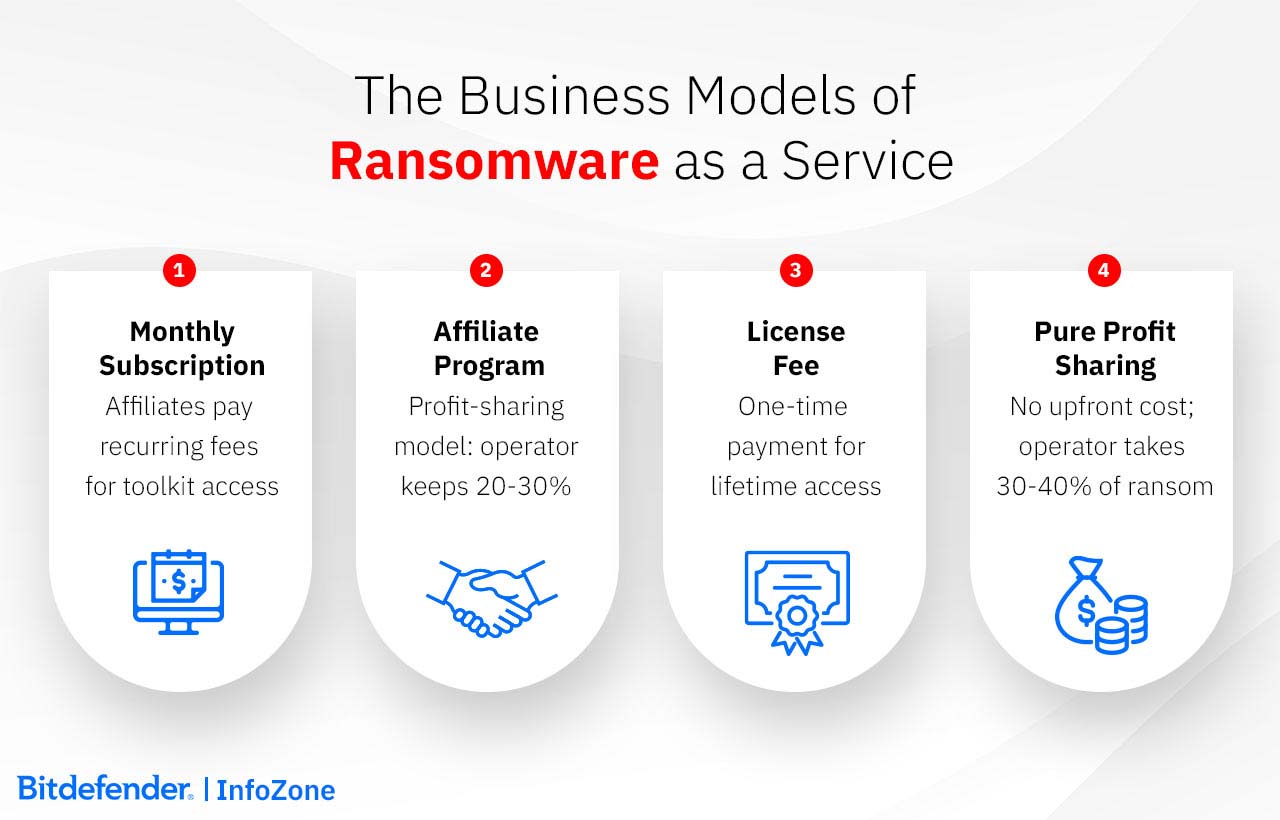
The RaaS framework includes several revenue models, appealing to a diverse range of possible customers:
RaaS attacks have evolved from the straightforward malware campaigns of the past into complex operations that exploit every available vulnerability. Below is a blueprint of how RaaS attacks are currently planned and executed. (Source)
RaaS attackers gain access to networks and systems through most common vectors that should be taken into consideration when deciding on the best defense strategy.
Early detection of a ransomware attack is crucial in stopping its progress or at least in minimizing its impact. Below are the most common red flags signaling a potential RaaS attack.
Direct Indicators
Indirect Indicators
Ransomware as a Service (RaaS) is escalating the risk and complexity of ransomware attacks globally as it brings the efficiency and adaptability of the gig economy to an old criminal practice. Ransomware as a Service has allowed the increase in financial demands: in 2023, ransomware payments skyrocketed, exceeding for the first time ever the $1 billion mark. The Cl0p's exploitation of the MOVEit zero-day vulnerability led to over $100 million in ransom payments and accounted for a significant portion of the total ransomware revenue in 2023.
Such meticulous and adaptive campaigns are indicative of the broader trends within RaaS, where cybercriminals exploit systemic vulnerabilities and network weaknesses. Law enforcement efforts, such as the FBI's infiltration into the Hive ransomware operation, which averted an estimated $130 million in ransom payments, highlight the tangible impact of strategic counter-ransomware operations. However, despite these successes, the sheer volume of new variants and the clever exploitation of vulnerabilities continue to pose serious challenges for cybersecurity defenses.
RaaS platforms have facilitated an increase in both double and multiple extortion attacks. Double extortion involves the encryption of a victim's data coupled with threats to release the information publicly if the ransom is not paid. Meanwhile, multiple extortion adds further pressure by introducing additional forms of attack, mostly Distributed Denial of Service (DDoS), to coerce victims into paying more promptly. The emergence of “pure extortion” tactics, where attackers threaten to leak stolen data without employing encryption, is another evolution of ransomware strategies within the RaaS ecosystem, as this approach represents a shift from traditional ransomware methods.
RaaS has made sophisticated tools more accessible, but this is not the only contributing factor to the growth in ransomware revenues. The surge can also be linked to the anonymity and security provided by cryptocurrency transactions, which offer cybercriminals a safer and untraceable method of receiving payments. Additionally, the fight against ransomware is often compromised by human-related vulnerabilities. Shortcomings in staff training, inadequate process oversight, and lapses in standard security practices provide fertile ground for RaaS exploits.
Ransomware gangs are facing heightened scrutiny and legal actions, as evidenced by the U.S. Department of Justice's seizure of $6 million from REvil or the recent international law enforcement action that disrupted the operations of the LockBit ransomware group.
Nevertheless, the highly competitive nature of RaaS platforms has made cybercriminal activities more calculated, making full use of technological advances and constantly shifting tactics to exploit vulnerabilities with precision. Opportunistic attacks weaponize zero-day exploits with amazing speed, as ransomware developers use modern programming languages like Rust to create harder-to-analyze code. Another noticeable trend is the growing specialization within ransomware groups, driven by a profit-sharing model.
In this context, staying ahead in cybersecurity is more than about adopting the latest tools, it is also about understanding and anticipating cybercriminal tactics and regulatory responses. Continuous education, policy adaptation, and technological vigilance are paramount in crafting a resilient defense against the sophisticated and evolving threat of RaaS. Bitdefender’s Business Insights blog offers valuable resources and analyses to help organizations stay one step ahead of ransomware and other cyber threats.
The layered structure of RaaS, with the developers, distributors, and end-users of ransomware often being distinct parties, complicates the process of investigating and prosecuting these crimes. Developers of ransomware might lease their products to affiliates in another country, who might target victims in yet another, which creates a tangled web of jurisdictional issues.
The Computer Fraud and Abuse Act is one legal framework under which RaaS actors can be prosecuted in the United States, but to address these crimes effectively often involves international cooperation. Law enforcement agencies such as the Interpol, FBI, or Europol may be hindered by borders, legal systems, and international relations, which can slow down the pace of investigation and prosecution.
Paying a ransom contravenes the advisory of law enforcement agencies such as the FBI, which recommends against such payments to discourage the perpetuation of these criminal activities. The legality of ransom payments falls into a grey area due to the challenges in identifying the recipient. The Office of Foreign Assets Control (OFAC), part of the U.S. Department of the Treasury, regulates transactions involving sanctioned parties, and ransom payments could inadvertently violate sanctions laws if the ransom is delivered to individuals or groups on the Specially Designated Nationals and Blocked Persons List, as well as to embargoed regions.
Organizations must carefully weigh the legal risks and potential penalties against the immediate operational needs. Legal repercussions can include substantial fines and, in some cases, criminal liability. As such, entities are encouraged to prioritize preventative measures, report incidents to authorities promptly, and implement robust cybersecurity protocols to mitigate the risk of RaaS attacks, rather than resorting to ransom payments, which may have far-reaching legal consequences.
For those exposed to a RaaS attack, the dilemma of whether to pay the ransom becomes a lot more complex than in theory. In reality, there will probably always be entities that opt to pay, often out of desperation or business necessity. The current landscape reveals that businesses, especially within the small and medium enterprise sector, are increasingly considering ransom payments. There is certainly a business aspect of this decision, as each organization weighs differently the pros and cons of paying, taking into consideration operational continuity, financial implications, and reputational impact.
To counter Ransomware as a Service threat, organizations should deploy a suite of tools and techniques able to preemptively identify and mitigate ransomware attacks. A robust RaaS prevention strategy includes:
In the continuous arms race against Ransomware as a Service, Bitdefender can act as a strong ally, offering comprehensive solutions that integrate seamlessly into any cybersecurity strategy. Bitdefender's cybersecurity solutions feature real-time protection and active scanning to thwart ransomware and other cyber threats, using:
Pinpointing the most popular Ransomware as a Service (RaaS) can be complex, given the rapidly changing nature of the cybersecurity threat landscape. LockBit stands out as one of the most pervasive variants in recent times, while other notorious RaaS variants include DarkSide (known for the 2021 attack on the U.S. Colonial Pipeline), REvil / Sodinokibi, Ryuk and its successor Conti, and Hive, which became prominent after an attack on Microsoft Exchange Server.
Tox, emerging in 2015, is widely recognized as a pioneering RaaS platform, marking a significant evolution in the monetization of ransomware. Some consider the Reveton ransomware, which appeared in 2012, to be the actual first instance of a RaaS operation.
Depending on the pricing model and the malware sophistication, subscription prices can range from as low as $40 for basic, off-the-shelf ransomware kits to several thousand dollars for more advanced, customizable solutions that include additional services like customer support, updates, and even tutorials on how to launch attacks.