“Didn’t you say you had it under control?” Discover why smart security teams choose GravityZone — before the chaos hits. Learn More >>
A honeypot is a deliberately exposed, isolated decoy system designed to look like a real computer network, server or system resource, used to observe attacker behavior. The honeypot meaning comes from how they function: honeypots attract cybercriminals and lure them into a controlled environment, serving as a research tool. These traps are carefully made so security teams can watch how attackers behave and collect information without putting important data or systems in danger. When hackers interact with these fake targets, they are said to have been honeypotted; in other words, they've fallen for the deception and exposed their tactics.
In cybersecurity, understanding how attackers operate, what tools they use, their methods, and their goals, is foundational. Honeypots are a key part of this strategy because they are a great way to gather first-hand key insights on threats that are constantly evolving: ransomware, phishing, zero-day attacks, etc. These insights help us design stronger defenses and reduce the likelihood of successful breaches.
Another advantage of honeypots is the uncertainty they create for attackers. When they are in play, adversaries are forced to second-guess whether their target is legitimate or just a well-placed trap. That hesitation can be a valuable tool in our defensive strategy.
ave come a long way. They've evolved from simple decoys into sophisticated systems that are fully integrated into larger security frameworks. They are also invaluable as training grounds, giving security professionals a controlled environment where they can study real-world threats and simulate attacks in a relatively controlled and safe manner.
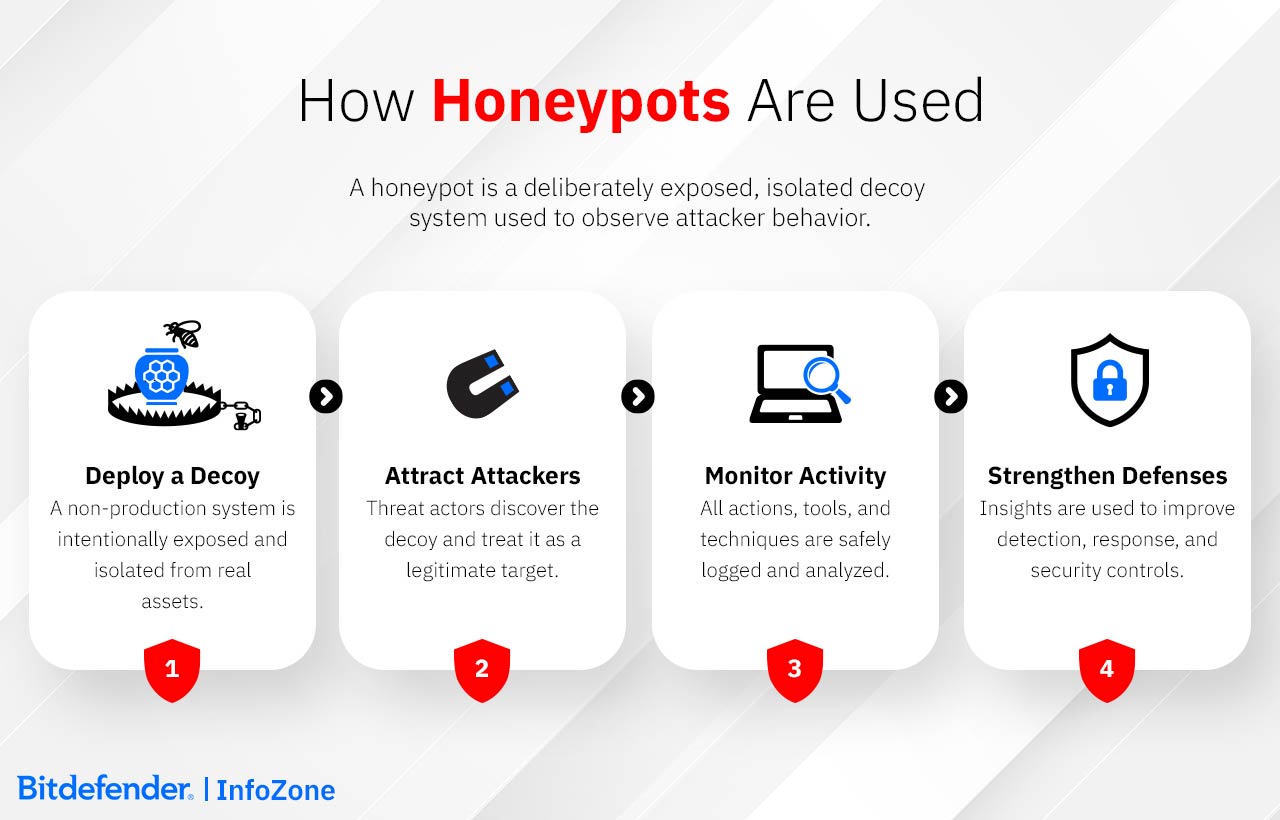
By intentionally adding vulnerabilities, e.g. outdated software or weak password, rotects real networks but also helps security teams learn about how attackers work. Honeypots operate through three key mechanisms: attraction, interaction, and monitoring.
1. Attraction: Drawing Attackers In
Honeypots are made to look like irresistible targets by incorporating deliberate flaws and decoy data. Examples include:
2. Interaction: Engaging Threat Actors
Once attackers engage, they allow security teams to observe their behavior in a controlled environment:
Some even make attackers overconfident by pretending to be easy targets, encouraging them to stay longer and reveal more information.
3. Monitoring: Learning From Attacks
Honeypots track everything attackers do and offer insights on:
Honeypots need protective barriers, such as honeywalls, to prevent attackers from using them to reach real systems. Playing with fire can become dangerous, a poorly configured trap can become a dangerous tool in attackers' hands. That is why it is wise to invest heavily in proper planning and skilled management.
The intelligence gathered from these tools plays a critical role in:
|
Type |
Main Purpose |
Key Features |
|
Production |
Active defense |
Protects real systems in real-time |
|
Research |
Intelligence Gathering |
Collects detailed attack data |
|
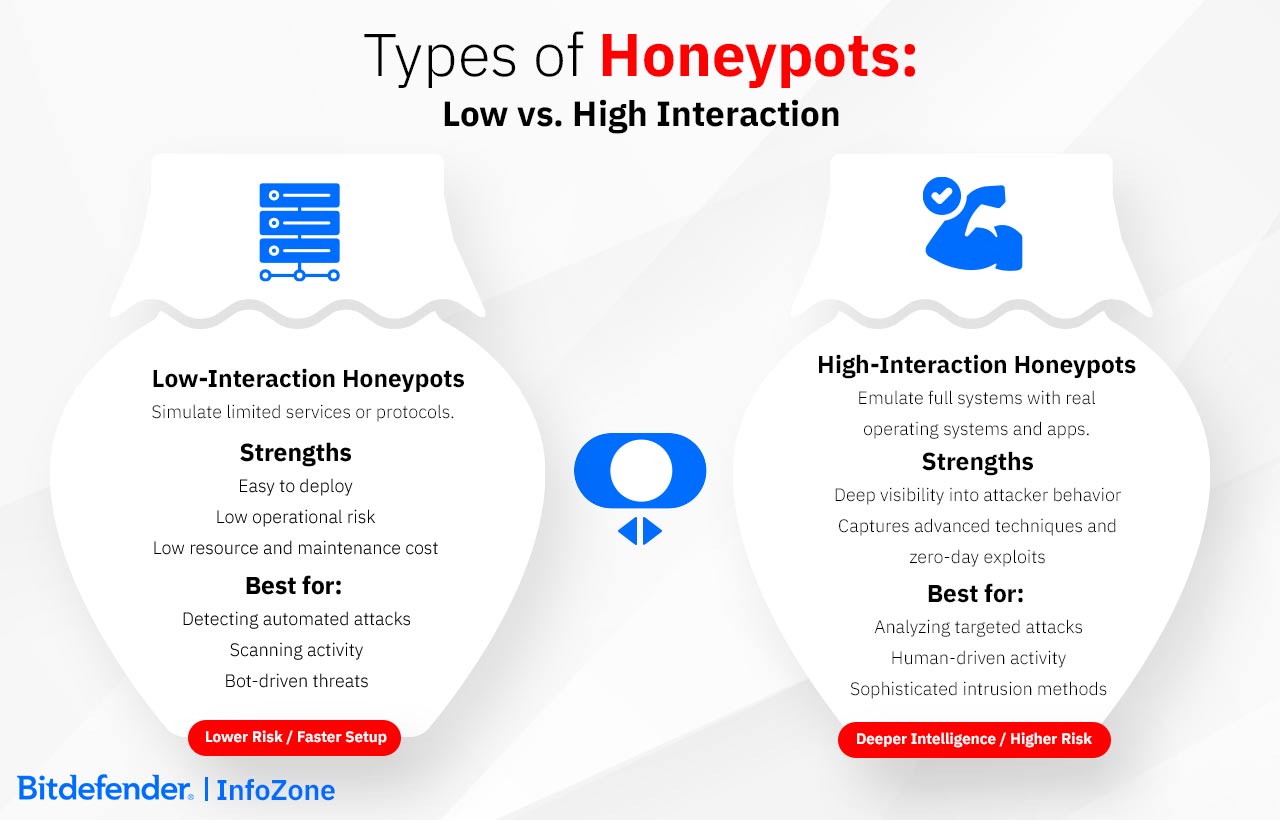
Low-interaction |
Basic Monitoring |
Easy to deploy, limited engagement |
|
High-interaction |
Deep Analysis |
Full system simulation, rich insights |
Production honeypots protect live systems by diverting attackers to fake targets. Deployed alongside legitimate systems, they safeguard valuable data, give security teams time to respond, and detect potential breaches early.
Governments and research institutions use research honeypots to study how attackers behave, collecting data on hacking techniques, tools, and strategies. This information helps cybersecurity experts build stronger defenses and prepare for threats.
Honeypots can be designed at different levels of complexity, depending on how much detail they simulate and the type of information they aim to collect:
Advanced deployments expand their capabilities:
Specialized honeypots tackle specific threats:
Honeypots are in essence decoys used by various entities, from enterprises and research institutions to government agencies and educational organizations, and their main benefit is improving the system's security. Using deception, predators become prey: attackers are diverted from critical systems, wasting their resources and exposing vulnerabilities that might otherwise remain hidden. Unlike traditional intrusion detection systems, honeypots produce low false positive rates, as any interaction is inherently suspicious.
Honeypots are also vital for early threat detection. They mimic real systems, so they can detect new (zero-day) threats and monitor how attack methods evolve. This helps security teams understand how attackers work, which makes it easier to improve defenses. For example, universities use them to protect sensitive research data and monitor cyber threats in real-time.
Honeypots support research into attacker behavior, which helps creating better security policies and stronger countermeasures. They're also great for training cybersecurity teams, as they offer a safe way to practice threat handling without risking live systems. This hands-on training is extremely useful in the context of the shortage of skilled cybersecurity professionals.
Cost-effective and flexible, honeypots can often be implemented using outdated hardware, which makes them affordable for even small businesses that can benefit from managed services.
In connected environments like IoT and 5G, honeypots have become indispensable in identifying and mitigating new threats.
Honeypots are clever and useful tools, but to really make the most of them, you've got to be aware of the potential traps they might bring along.
Legal Concerns
Yes, honeypots are usually legal - but the rules can vary depending on where you are in the world - for guidance on legal compliance, see the NIST Cybersecurity Framework guidelines on security tools. Some countries have strict privacy and cybersecurity laws that might limit how they can be deployed. Things get even trickier for international organizations, as there are different cyber laws across regions.
There are also ethical matters: tricking attackers into interacting with fake systems might sound like poetic justice, but it can spark debates about fairness.
Limitations and Vulnerabilities
A honeypot can be great at catching attackers who engage with them, but there's a catch: it only works if attackers take the bait. Advanced hackers might recognize it and either bypass it or use it to study your defenses.
If not properly secured, they can turn into a backdoor for attackers to access real systems. That's why tools like honeywalls (barriers that keep attackers locked in) and regular maintenance are non-negotiable.
Maintenance and Operational Demands
Setting up a honeypot isn't a “set it and forget it” tool, and high-interaction honeypots need constant attention to make sure that attackers don't misuse them. Even simpler types require regular updates to stay convincing. Another challenge is false positives. Sometimes, legitimate users might accidentally interact with a honeypot, causing unnecessary alerts.
Balancing Benefits with Risks
Honeypots are fantastic for gathering intelligence and distracting attackers, but they're not a one-stop solution. Think of them as a supporting actor in your cybersecurity cast, not the main star. To get the most out of them, it's crucial to:
Honeypots are generally considered legal as long as organizations follow local laws and privacy regulations. However, legal risks can arise if they are misused. For example, if it actively encourages or manipulates attackers into committing illegal actions, they might not have otherwise attempted, this could be viewed as entrapment. That is, deliberately provoking someone into breaking the law. Something that can lead to serious legal or ethical issues.
Additionally, they need to be carefully secured and kept completely separate from real systems. If attackers can use a poorly configured honeypot to access genuine networks, it not only defeats the purpose but could also expose the organization to liability.
Creating a honeypot begins with a clear goal: detecting cyberattacks, studying hacker behavior, testing security tools, or training security teams. Low-interaction honeypots monitor basic attack patterns, while high-interaction variants simulate full systems, gathering in-depth insights. Combining multiple honeypots into a honeynet makes it easier to study attackers' methods across a variety of scenarios.
For effectiveness, honeypots should be placed in an isolated network zone, such as a demilitarized zone (DMZ), to prevent attackers from accessing critical systems. Tools like honeywalls (e.g., Roo) and firewalls add extra layers of protection, ensuring attackers can't use the honeypot to cause further harm. Centralized logging systems help collect data for easy analysis, enabling teams to monitor and act on emerging threats.
Best Practices for Deployment
Tools and Frameworks
Numerous tools make honeypot creation straightforward:
Enterprise-grade solutions integrate honeypots into advanced threat intelligence systems. These networks help detect serious exploits, like Log4Shell, and provide insights for prioritizing security efforts.
Effectiveness Metrics
Organizations use a few key metrics to figure out how well a honeypot is doing its job. One of the main ones is engagement duration, which is basically how long attackers stick around and interact with the trap. The longer they're engaged, the more information security teams can gather about the tools and techniques the attackers are using, and even what they're trying to achieve.
Another important metric is the detection rate. This shows how good the honeypot is at catching real threats without generating too many false alarms. If the trap keeps flagging harmless activity as an attack, it wastes time and resources.
Teams also look at the data collected, not just how much they gather but also how useful it is. For example, does the honeypot uncover new attack methods, or does it just confirm stuff we already know? High-quality data helps organizations fine-tune their defenses and prepare for the next wave of threats.
Future Trends
Among the latest developments, we can mention AI-driven honeypots that adapt dynamically and are better at deceiving attackers. Another notable trend is the increasing use of IoT-specific honeypots, which are becoming essential for protecting smart devices like connected appliances and industrial systems.
Bitdefender enhances cybersecurity strategies with its innovative use of honeypots, integrated into a robust security framework that combines threat intelligence, advanced detection, and proactive defense.
Honeypots as a Core of Threat Intelligence
Bitdefender deploys an extensive global network of honeypots to attract and analyze malicious activity. They mimic likely attack targets, capturing real-world data that feeds into the Bitdefender Global Protective Network (GPN). This data enriches the intelligence powering Bitdefender solutions, enabling:
Honeypot-derived intelligence strengthens the capabilities of Bitdefender’s GravityZone Platform, particularly in key areas such as:
Operational Threat Intelligence: Honeypot data provides actionable insights into attacker behavior, improving the ability to detect and block sophisticated threats, including ransomware and advanced persistent threats (APTs).
Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR): By leveraging honeypot intelligence, these solutions identify and neutralize threats across endpoints, networks, and cloud environments. The enhanced context and accuracy reduce response times and increase the effectiveness of threat mitigation.
Machine Learning and AI Integration: Data collected from honeypots trains machine learning models, improving the detection of new attack patterns while minimizing false positives.
Practical Applications and Customer Benefits
Proactive Defense: Honeypots enable Bitdefender to detect emerging threats like cryptojacking and ransomware campaigns, offering customers early protection.
Threat Reports and Guidance: Insights from honeypot activities, featured in Bitdefender Threat Debrief reports, provide actionable intelligence to organizations.
A firewall and a honeypot are tools used in cybersecurity, but their purposes and methods are entirely different. A firewall protects a network by filtering traffic. It analyzes data that comes in and out of a system and enforces strict rules to allow only safe and authorized communication. If anything looks suspicious or unauthorized, the firewall blocks it before it can cause harm. A honeypot, by contrast, is meant to attract attention so that when attackers engage with it, the trap can record their methods, tools, and behavior. While a firewall is focused on prevention by keeping malicious activity away from real systems, a honeypot is used for observation and learning, allowing attacks to happen in a controlled environment. They are both important, but they solve different problems: one keeps your doors locked, while the other watches what happens when someone tries to break in.
Yes, especially if they're experienced or take the time to analyze the system. A honeypot might stand out if it doesn't fully mimic the behavior of a real system. For example, it might lack realistic data, normal user activity, or the connections a genuine server would have. Hackers may also test a system's responses with specific commands or patterns. If the honeypot doesn't behave as expected - like responding too generically or inconsistently - they might realize it's a decoy. To make detection harder, advanced types are designed to look and act as much like real systems as possible, often mimicking the specific vulnerabilities attackers are searching for. However, no matter how realistic they are, determined and skilled attackers can sometimes uncover them. This is why honeypots are used more as tools to observe and learn from attackers rather than as the sole line of defense in cybersecurity.
Honeypots are not always suitable and should be avoided in certain situations. With limited resources, such as insufficient IT staff or a constrained security budget, maintaining and monitoring a honeypot effectively may not be feasible. Another dangerous situation is protecting high-value assets or sensitive systems: the risk of a trap being exploited by attackers might outweigh its benefits.
If the goal is comprehensive protection, honeypots are not a good choice, as they do not block threats or secure systems - they are intelligence-gathering tools. Deploying a honeypot without clear objectives or in networks with heavy traffic can lead to wasted effort or difficulty identifying malicious activity. Compliance regulations in some industries may also restrict their use, especially where privacy or data collection limits are in place.
Finally, honeypots are less effective in small networks where they may be easily identified by attackers or when the primary concern is mitigating known threats, which are better handled by tools like firewalls or intrusion detection systems. Honeypots work best in specific, well-defined roles within a larger security strategy.