Design and refine your incident response approach with expert-led tabletop exercises that turn strategy into tested, actionable plans.
Simulate credible, threat-informed attack scenarios – informed by Bitdefender global research - to validate roles, processes, and team readiness in real time.
Engage with advisors through a modular, collaborative format that adapts to your organization’s structure, maturity, and evolving priorities.
|
Additional Available Services |
|
|
Information Security Policy Framework Development |
Establish clear, audit-ready security policies tailored to your business, regulatory needs, and technical environment |
|
Cybersecurity Strategy |
Define a practical, risk-based roadmap that aligns cybersecurity priorities with business objectives and resource realities |
|
Training and Awareness |
Equip teams with the knowledge to recognize threats, follow best practices, and meet compliance expectations without disrupting operations |
|
Reporting and Dashboarding |
Build executive-ready dashboards and reports that translate technical posture into business-level actionable insights |
|
Risk Assessments |
Identify and prioritize risks across your environment with expert-led evaluations to drive smart investment decisions |
|
Supply Chain/Third Party Risk Management |
Assess and manage vendor and partner security risks to protect your organization from external vulnerabilities and regulatory exposure |
|
Project Management for Security Transformation |
Keep security initiatives on track with structured project leadership from planning through execution and validation |
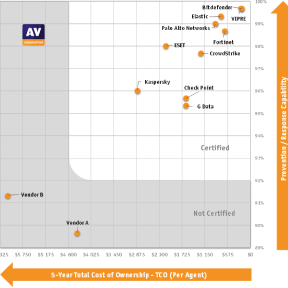
Bitdefender achieved top breach prevention and lowest TCO and was the only vendor to block 100% of attacks during the first stage.
Bitdefender GravityZone Endpoint Security received the AV-TEST Award 2023 for Best Protection and Best Performance in the business users category.

Bitdefender achieved 100% analytical coverage for both Linux and macOS, with zero False Positives (FPs) in both cases.

A Customers’ Choice in Gartner® Peer Insights™
Voice of the Customer for EPPs



The duration varies based on complexity and scope of participation. Typically, the active simulation session can range from a half-day to a full day, not including the preparation work and meetings by the CIRT members and reporting.
Bitdefender consultants will work closely with your organization to identify the documents and active participants required. The documents include existing incident response policies, network diagrams, and other business continuity plans. The Bitdefender team will develop tailored contextualized scenarios.
TTX aims to answer a specific requirement or challenge around preparedness in the event of an incident. Cybersecurity Advisory Retainer can include TTX as one of the projects delivered during the long-term engagement.
Each TTX engagement includes two scenarios tailored to your organization and based on real-world threat actor Tactics, Techniques, and Procedures (TTPs). Scenarios are designed to reflect the risks most relevant to your environment, such as ransomware, business email compromise, insider threats, or supply chain attacks, ensuring the simulation is both realistic and actionable.
Review and sharpen your decision-making, communication, and security policies.