Endpoint Sensor
Bitdefender Endpoint Security Tools can act as a feeding sensor for Sandbox Analyzer from Windows endpoints.
To configure automatic submission via endpoint sensor, go to the following sections:
Under Connection Settings, select one of the options:
Use Cloud Sandbox Analyzer - the endpoint sensor will submit samples to a Sandbox Analyzer instance hosted by Bitdefender, depending on your region.
Use local Sandbox Analyzer instance - the endpoint sensor will submit samples to a Sandbox Analyzer On-premises instance. Choose the preferred Sandbox Analyzer instance from the drop-down menu.
If you have your network behind a proxy server or a firewall, you can configure a proxy to connect to Sandbox Analyzer by selecting the Use proxy configuration check box.
You have to fill in the following fields:
Server - the IP of the proxy server.
Port - the port used to connect to the proxy server.
Username - a user name recognized by the proxy.
Password - the valid password for the specified user.
Sandbox Analyzer supports local file submission through endpoints with relay role, which are able to connect to different Sandbox Analyzer Portal addresses depending on your region. For details regarding the relay configuration settings, refer to Relay.
Note
A proxy configured in the Sandbox Analyzer connection settings will override any endpoints with relay role.
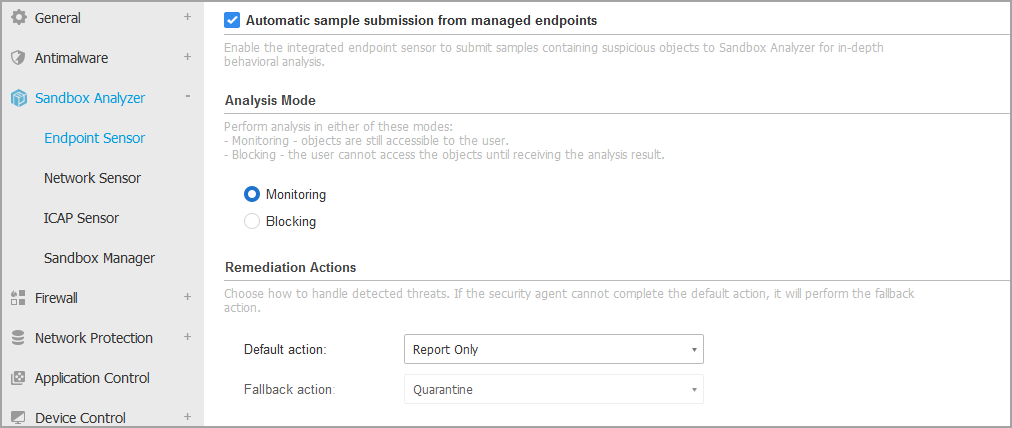
Select the Automatic sample submission from managed endpoints check box to enable automatic submission of suspicious files to Sandbox Analyzer. If you want to manually submit a sample, refer to Manual submission.
Important
Sandbox Analyzer requires on-access scanning. Make sure you have the Antimalware > On-Access module enabled.
Sandbox Analyzer uses the same targets and exclusions as defined in Antimalware > On-Access. Review carefully the On-Access scanning settings when configuring Sandbox Analyzer.
To prevent false positives (incorrect detection of legitimate applications), you can define exclusions by various criteria such as file name, extension, and path. For more information on exclusions, refer to Configuration profiles > Exclusions.
In addition to exclusions defined in the Antimalware section, you can specify them on this page as well, in the Exceptions field, as described further below.
The upload limit for any file or archive is 50 MB.
Choose the Analysis Mode. Two options are available:
Monitoring. The user can access the file during the sandbox analysis, but he is recommended not to execute it until receiving the analysis result.
Blocking. The user cannot execute the file until the analysis result is returned to endpoint from Sandbox Analyzer Cluster via Sandbox Analyzer Portal.
Specify the Remediation Actions. These are taken when Sandbox Analyzer detects a threat. For each analysis mode you are provided with a dual setup, consisting of one default action and one fallback action. Sandbox Analyzer initially performs the default action, then the fallback action, if the former cannot be completed.
When accessing this section for the first time, the following setups are available:
In the Monitoring mode, the default action is Report only, with the fallback action disabled.
In the Blocking mode, the default action is Quarantine, while the fallback action is Delete.
Note
As best practices, it is recommended to use remediation actions in this configuration.
Sandbox Analyzer provides you the following remediation actions:
Disinfect. It removes the malware code from the infected files.
Delete. It removes the entire detected file from the disk.
Quarantine. It moves detected files from their current location to the quarantine folder. Quarantined files cannot be executed or opened; therefore, the risk of getting infected disappears. You can manage quarantined files in the Quarantine page of Control Center.
Report only. Sandbox Analyzer only reports detected threats without taking any other action on them.
Note
Depending on the default action, a fallback action may be unavailable.
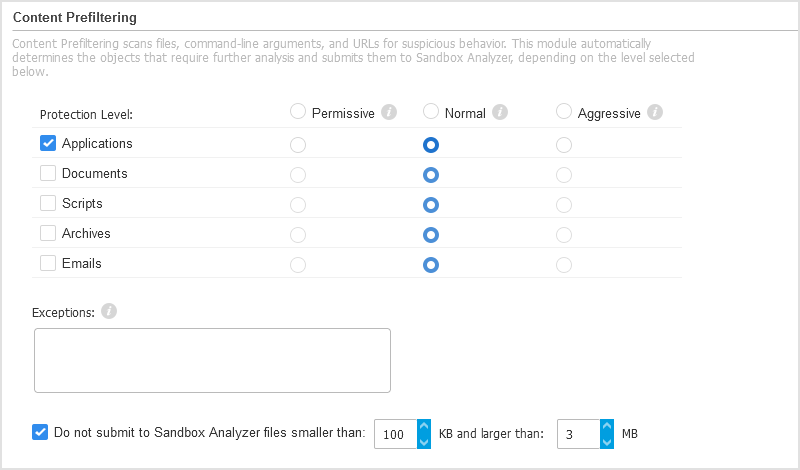
Under Content Prefiltering, customize the protection level against potential threats. The endpoint sensor has embedded a content filtering mechanism which determines whether a suspicious file needs to be detonated in Sandbox Analyzer.
The object types supported are: applications, documents, scripts, archives, emails. For more details on the supported object types, refer to File types supported by Content Prefiltering at automatic aubmission.
Use the master switch at the top of the threats list to choose a unique level of protection for all types of objects, or select individual levels to fine tune protection.
Setting the module at a certain level will result in a certain number of submitted samples:
Permissive. The endpoint sensor automatically submits to Sandbox Analyzer only the objects with the highest probability of being malicious and ignores the rest of the objects.
Normal. The endpoint sensor finds a balance between the submitted and ignored objects and sends to Sandbox Analyzer both objects with a higher and with a lower probability of being malicious.
Aggressive. The endpoint sensor submits to Sandbox Analyzer almost all objects, regardless of their potential risk.
Exceptions. In this field, you can define exceptions for the object types that you do not want to submit to Sandbox Analyzer.
File size. You can also define size limits of the submitted objects by selecting the corresponding check box and entering any desired values between 1 KB and 50 MB.
Under Detonation profile, adjust the complexity level of behavioral analysis, while affecting the Sandbox Analyzer throughput. For example, if set to High, Sandbox Analyzer would perform a more accurate analysis on fewer samples, in the same interval, than on Medium or Low.