Deploy Network Security Virtual Appliance
This section describes how to deploy Network Security Virtual Appliance, a Sandbox Analyzer component that captures network traffic (PCAP files) and submits suspicious samples for behavioral analysis.
Important
This virtual appliance, which provides the Network Sensor for Sandbox Analyzer On-Premises, should not be confused with the XDR component. For Network Sensor in Cloud XDR, refer to this topic.
To deploy the Network Security Virtual Appliance:
Log in to the GravityZone Control Center.
Go to the Network > Packages page.
Select the Network Security Virtual Appliance check box from the table.
Click the Download button at the upper-left side of the page and select the (VMware OVA) option.
Use your virtualization management tool (for example, vSphere Client) to import the downloaded OVA file into your virtual environment.
In the deployment wizard, select the network interface card (NIC) used for communication with GravityZone and the NIC used for capturing traffic.
Power on the appliance.
From your virtualization management tool, access the console interface of GravityZone SVE SVA Network Security Virtual Appliance.
When prompted for credentials, use
rootfor username andsvefor password.Access the configuration menu by running the following command:
/opt/bitdefender/bin/nsva-setup
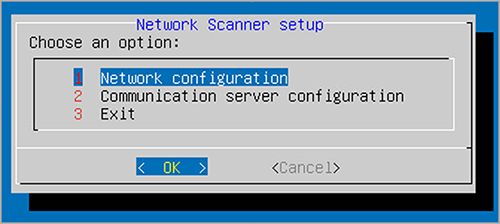
Go to Communication server configuration menu option.
Specify the IP address or hostname, and the port of a GravityZone Communication Server.
Use the following syntax:
http://<IP/Hostname>:<Port>. The default port is8443.Save the configuration.
Configure Network Sensor to detonate PCAP files
The Network Sensor can extract content from network capture files (PCAP) and automatically send it for detonation to the Sandbox Analyzer instance.
To detonate content from PCAP files:
Log in to Network Security virtual appliance.
When prompted for credentials, use
rootfor username andsvefor password.Run the following command:
/opt/bitdefender/bin/scan-pcap <local pcap path>
In the above command,
<local pcap path>represents the location where the PCAP file is uploaded in the Network Security Virtual Appliance.
The Network Sensor is configurable in the policy. For details, refer to this topic.
After detonation, the resulting reports are available in the Sandbox Analyzer section on the left-side main menu in GravityZone Control Center. For details on how to view and use them, refer to this topic.