Response Actions
Response Actions gives you a list of every action that a SOC Analyst has taken in your environment, based on data gathered from investigations or threat hunts.
On this page, you also have several filtering options and additional information for each action.
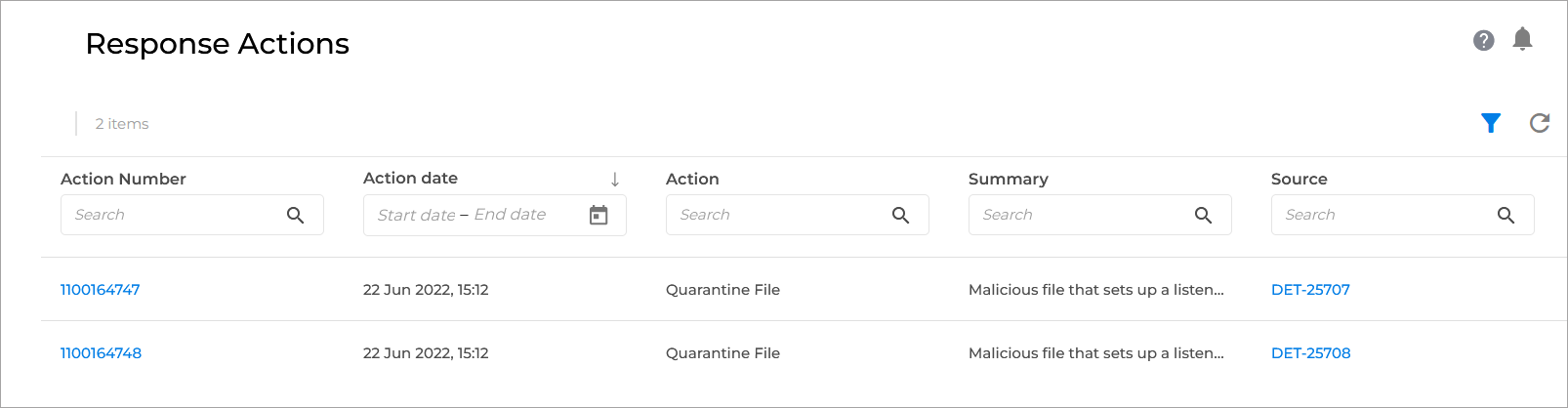
Action Number - the unique identifier of each action in this environment.
Note
Click any action number to display additional information.
Action date - timestamp of when the action was taken.
Action - indicates which action was taken by the SOC team.
Note
For a complete list of available actions, refer to Pre-approved Actions
Summary - displays the summary of the action, showing information such as which endpoint or which file was affected.
Source - the SOC effort (the investigation or the threat hunt) that resulted in this action. This item is linked back to the investigation or threat hunt for more information.