How to integrate GravityZone Cloud Platform with Splunk
This article explains how to integrate GravityZone Cloud Platform with Splunk by using HTTP Event Collector and GravityZone APIs.
- About the GravityZone integration with Splunk
- Prerequisites
- How to configure the GravityZone integration with Splunk
About the GravityZone integration with Splunk
As a Bitdefender partner, you can integrate GravityZone with Splunk by using GravityZone APIs and Splunk HTTP Event Collector. With this service, you are able to send data from GravityZone Control Center directly to Splunk Enterprise or Splunk Cloud.
Prerequisites
To integrate GravityZone with Splunk, you must have at hand:
- Credentials for your GravityZone Cloud account.
- Credentials for your Splunk account (cloud or on-premises).
Optionally, you can use a script to automatically enable the integration.
For Bitdefender Splunk App to correlate data coming from GravityZone, you must install Bitdefender Splunk Add-on.
How to configure GravityZone integration with Splunk
To use the GravityZone integration with Splunk you need to:
- A. Enable Event Push API in GravityZone Control Center.
- B. Enable a new token for HTTP Event Collector in Splunk.
- C. Enable the Splunk integration.
To integrate GravityZone with Splunk:
A. Enable Event Push API in GravityZone Control Center
- Log in to GravityZone Control Center.
- Go to My Account.
- Under API keys section, click Add.
- Select the Event Push Service API check box and click Save. The new key appears in the API Keys table.
.png)
- Click Save to preserve the changes made in My Account page.
B. Enable a new token for HTTP Event Collector in Splunk
- Log in to Splunk.
- Go to Settings > Data Inputs > HTTP Event Colector.
.png)
- Click New Token.
- In the Add Data screen, fill in the Name field, as suggested in the image below, and click Next.
.png)
- For Source type, click Select and choose
_json.
.png)
When using Bitdefender Splunk App, after installing Splunk Bitdefender Add-on, click Select and choose
bitdefender:gzas the source.
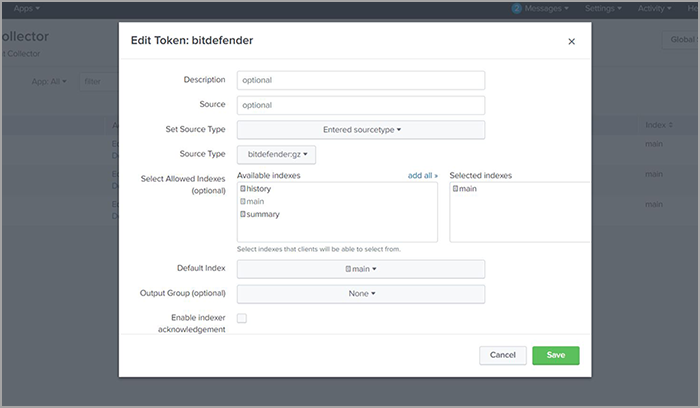
- At Index, select a default index or create a new one. The events received by HTTP Event Collector will be inserted in the selected index.
- Click Review.
- Verify the data you entered and click Submit.
The token has been created successfully. Copy the token value and save it. You will need it later to enable the integration.
.png)
- Go to Settings > Data Inputs > HTTP Event Collector and click Global Settings.
.png)
- In the new window, under All Tokens section, select Enabled.
.png)
- Click Save.
C. Enable the Splunk integration
After you created the Event Push Service key in GravityZone Control Center and enabled HTTP Event Collector in Splunk, you need to enable the integration. That means you have to start sending events from GravityZone to Splunk.
Enable the Splunk integration manually
To enable Splunk integration means you must configure Event Push Service settings from your favorite terminal emulator on Linux or Mac. These settings refer to:
Example:
- GravityZone API URL. You find it in MyAccount > Control Center API and it should be similar to
https://cloudgz.gravityzone.bitdefender.com/api. - The authorization header of the API key generated in GravityZone. The header value is Basic base64encode. To obtain the authorization header, run the
echocommand followed by API key with colon (":"). > echo –n '604821e87e4c7de3aa15d0e6a97f5ab362281dbf0763746671da2caf4b5cccd1:' | base64 –w 0The result should be something like this:
NjA0ODIxZTg3ZTRjN2RlM2FhMTVkMGU2YTk3ZjVhYjM2MjI4MWRiZjA3NjM3NDY2NzFkYTJjYWY0YjVjY2NkMTo=- Splunk URL. You find it in your Splunk Cloud platform and it should be something like this:
https://prd-p-xlpxkqpw84k2.cloud.splunk.com. If you use Splunk on-premises, the URL is already in place. - HTTP Event Collector token.
Once you have the above data, run this command (the settings you have to edit are underlined):
> curl -k -X POST \
https://cloudgz.gravityzone.bitdefender.com/api/v1.0/jsonrpc/push \
-H 'authorization: Basic NjA0ODIxZTg3ZTRjN2RlM2FhMTVkMGU2YTk3ZjVhYjM2MjI4MWRiZjA3NjM3NDY2NzFkYTJjYWY0YjVjY2NkMTo=' \
-H 'cache-control: no-cache' \
-H 'content-type: application/json' \
-d '{"params": {"status": 1, "serviceType": "splunk", "serviceSettings": {"url": "https://input-prd-p-r2rmnllpzv4n.cloud.splunk.com:8088/services/collector", "requireValidSslCertificate": false, "splunkAuthorization": "Splunk EA900DEB-22C8-402B-A7F9-A926C1633E7A"}, "subscribeToEventTypes": {"modules": true, "sva": true, "registration": true, "supa-update-status": true, "av": true, "aph": true, "fw": true, "avc": true, "uc": true, "dp": true, "sva-load": true, "task-status": true, "exchange-malware": true, "network-sandboxing": true, "adcloud": true, "exchange-user-credentials": true}}, "jsonrpc": "2.0", "method": "setPushEventSettings", "id": "1"}'
The result should be similar to:
{"id":"1","jsonrpc":"2.0","result":true}
GravityZone starts sending events to Splunk after the Event Push Service settings are reloaded. This happens every 10 minutes.
To start sending events immediately, run this command (the settings you have to edit are underlined):
> curl -k -X POST \
https://cloudgz.gravityzone.bitdefender.com/api/v1.0/jsonrpc/push \
-H 'authorization: Basic R2U5SENZcWRVN2pJRFI5MHdOMGVFMXpiQjVTbmM1SE46' \
-H 'cache-control: no-cache' \
-H 'content-type: application/json' \
-d '{"params": {}, "jsonrpc": "2.0", "method": "getPushEventSettings", "id": "2"}'
Test the Splunk integration
To test the integration, run this command (the settings you have to edit are underlined):
> curl -k -X POST \
https://cloudgz.gravityzone.bitdefender.com/api/v1.0/jsonrpc/push \
-H 'authorization: Basic R2U5SENZcWRVN2pJRFI5MHdOMGVFMXpiQjVTbmM1SE46' \
-H 'cache-control: no-cache' \
-H 'content-type: application/json' \
-d '{"params": {"eventType": "av"}, "jsonrpc": "2.0", "method": "sendTestPushEvent", "id": "3"}'
Enable the Splunk integration by running a script
You can also start sending events from GravityZone to Splunk by running a script created by Bitdefender. You can do this in your favorite terminal emulator on Linux or Mac.
- Download the script from here.
- Make the script executable by running the command:
chmod +x bdpusheventconfig.sh
- Run the script with the command:
./bdpusheventconfig.sh -g [console_url] -k [api_key] -t [service_type] -u [service_url] -a [splunk_auth_token] -v -c [events]
The script includes the following options:
| Option | Description |
-g [console url] |
Gravity Zone API url |
-k [api_key] |
Gravity Zone API key |
-t [service_type] |
Service type: splunk or jsonRPC |
-u [service_url] |
Splunk or RPC url |
-a [splunk_auth_token] |
Splunk authorization token |
-v |
Verify service SSL certificate |
-c |
Connect to Splunk Cloud. Adds 'input-' the the service url. |
-h, --help |
Help |
These options are similar to the ones used when enabling the integration manually.
The [events] list refers to one or more space-separated events that are to be sent from GravityZone to Splunk. These events are described in the table below:
| Event type identifier | Description |
modules |
Product Modules event |
sva |
Security Server Status event |
registration |
Product Registration event |
supa-update-status |
Outdated Update Server event (where the Update Server is a Relay) |
av |
Antimalware event |
aph |
Antiphishing event |
fw |
Firewall event |
avc |
ATC/IDS event |
uc |
User Control event |
dp |
Data Protection event |
hd |
Hyper Detect event |
sva-load |
Overloaded Security Server event |
task-status |
Task Status event |
exchange-malware |
Exchange Malware Detection event |
network-sandboxing |
Sandbox Analyzer Detection |
adcloud |
Active Directory Integration Issue |
exchange-user-credentials |
Exchange User Credentials |
To subscribe to all events, use the value all or specify each one of them. If the events list is empty (no event types specified) then the integration is disabled.
Examples
Enable the Splunk integration
./bdpusheventconfig.sh -g https://gz.example.com/api/v1.0/jsonrpc/push -k abcdefghijklmnopqrstuvwxyz123456 -t splunk -u https://splunk.example.com -a 11111111-2222-3333-4444-555555555555 -c modules sva registration supa-update-status av aph fw avc uc dp sva-load task-status exchange-malware network-sandboxing adcloud exchange-user-credentials
./bdpusheventconfig.sh -g https://gz.example.com/api/v1.0/jsonrpc/push -k abcdefghijklmnopqrstuvwxyz123456 -t splunk -u https://splunk.example.com -a 11111111-2222-3333-4444-555555555555 -c all
Configure a json RPC service
./bdpusheventconfig.sh -g https://gz.example.com/api/v1.0/jsonrpc/push -k abcdefghijklmnopqrstuvwxyz123456 -t jsonRPC -u https://rpc.example.com modules sva registration supa-update-status av aph fw avc uc dp sva-load task-status exchange-malware network-sandboxing adcloud exchange-user-credentials
Disable the Splunk integration
./bdpusheventconfig.sh -g https://gz.example.com/api/v1.0/jsonrpc/push -k abcdefghijklmnopqrstuvwxyz123456 -t splunk -u https://splunk.example.com -a 11111111-2222-3333-4444-555555555555 –c
For details about Push Events Service, refer to the GravityZone Cloud API Documentation guide, the chapter "Push".
For details about creating reports based on data from GravityZone in Splunk, refer to this KB article.



 Australia:
(+61) 1300 888 829, (+61) 385 956 732
Australia:
(+61) 1300 888 829, (+61) 385 956 732 Canada:
(+1) 647 977 5827, (+1) 647 367 1846
Canada:
(+1) 647 977 5827, (+1) 647 367 1846  Deutschland:
(+49) 2304 9993004
Deutschland:
(+49) 2304 9993004  España:
(+34) 937 370 223
España:
(+34) 937 370 223
 France:
+33(0)184070660
France:
+33(0)184070660  New
Zealand: (+64) 0800 451 786
New
Zealand: (+64) 0800 451 786  Osterreich:
(+49) 2304 9993004
Osterreich:
(+49) 2304 9993004  România:
(+40) 21 264 1777, (+40) 374 303 077
România:
(+40) 21 264 1777, (+40) 374 303 077  Schweiz:
(+49) 2304 9993004
Schweiz:
(+49) 2304 9993004  United
States: (+1) 954 414 9621, (+1) 954
281 4669
United
States: (+1) 954 414 9621, (+1) 954
281 4669  United
Kingdom: (+44) 2036 080 456, (+44) 2080 991 687
United
Kingdom: (+44) 2036 080 456, (+44) 2080 991 687  WorldWide: (+40) 31 620 4235,
(+40) 374 303 035
WorldWide: (+40) 31 620 4235,
(+40) 374 303 035