How to protect virtual machines in a XenDesktop with Provisioning Server infrastructure
Bitdefender GravityZone provides full visibility into organizations' overall security posture, global security threats, and control over its security services that protect virtual or physical desktops, servers and mobile devices. All Bitdefender's Enterprise Security solutions are managed within the GravityZone through a single console, Control Center, that provides control, reporting, and alerting services for various roles within the organization.
Security for Virtualized Environments is the component of GravityZone used to protect virtual environments. As opposed to legacy security, Bitdefender implements centralized scanning by offloading much of the antimalware functionality on a dedicated hardened virtual appliance called Security Server. This approach optimizes both on-access and on-demand scanning processes while de-duplicating critical computing resources on the host servers.
Citrix XenDesktop provides a complete virtual desktop delivery solution by integrating several components with advanced configuration tools that simplify the creation and real-time management of the virtual desktop infrastructure. The core components of XenDesktop are: Desktop Delivery Controller (DDC), Virtual Desktop Agent (VDA) and Desktop Receiver.
This article describes how to install and configure Security for Virtualized Environments on XenServer virtual machines with Provisioning Server infrastructure.
Overview
Provisioning Server's infrastructure is based on software-streaming technology. Using Provisioning Server, administrators prepare a device (Master Target Device) to be imaged, by installing an operating system and any required software on that device. A virtual disk (vDisk) image is then created from the Master Target Device's hard drive and saved to the network (on Provisioning Server or back-end storage device). Once the vDisk is available from the network, a target device no longer needs its local hard drive to operate, as it boots directly from the network. The Provisioning Server streams the contents of the vDisk to the target device on demand, in real time.
Solution
To protect virtual machines in a XenDesktop with Provisioning Server infrastructure using GravityZone Security for Virtualized Environments (SVE), you need to deploy a Security Server and have BEST installed on the vDisk. To do so, follow these steps:
- Deploy GravityZone in the virtual environment and configure its roles.
- Connect to GravityZone Control Center using an account with Manage Solution right.
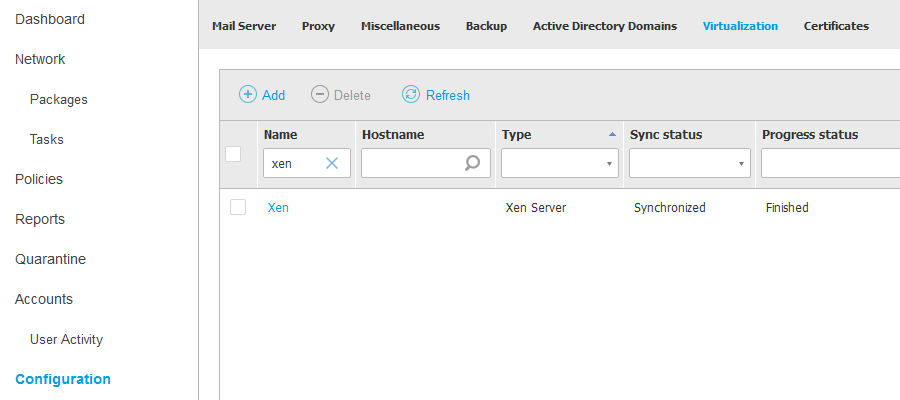
- Go to Configuration > Virtualization section and integrate GravityZone with Xen Server. When the process is finished, the Sync status will be Synchronized and the Progress status: Finished.
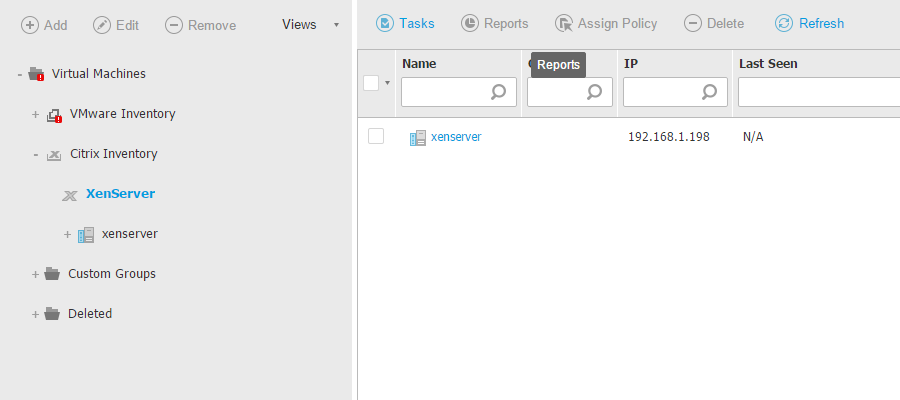
- To install the Security Server on the host, go to the Network page, select the host and run the Install Security Server task. The inventory will display the newly deployed virtual machine:
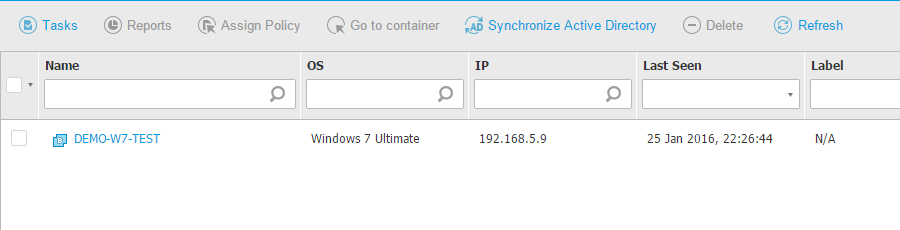
- Create a virtual machine with all programs that users need and install BEST to protect it against malware. To deploy BEST, select the VM in the inventory and run the Install Client task. After BEST is installed, the inventory will show the VM as being protected:
Also verify that the Master VM is protected by accessing it and opening the BEST user interface.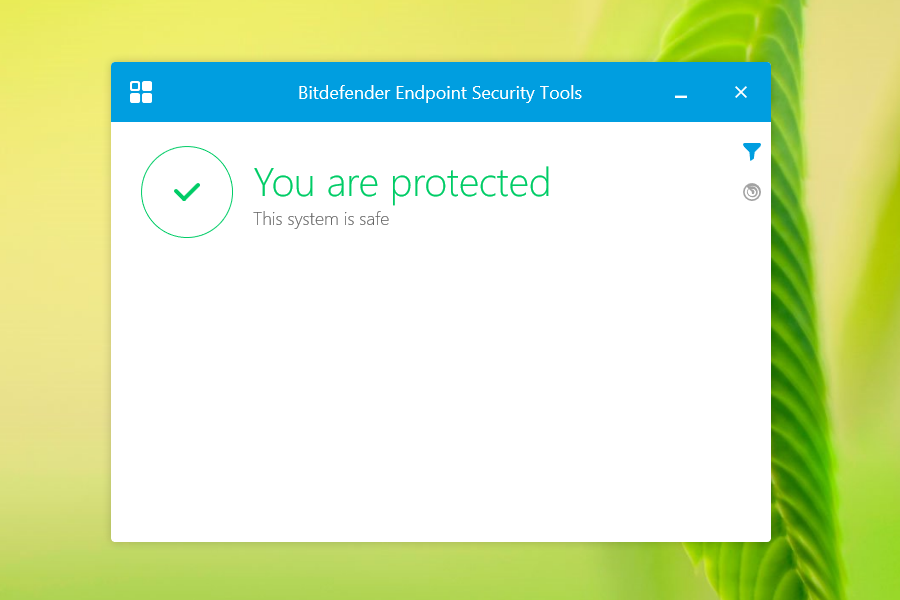
If you plan to use the BEST Firewall module, you need to add firewall rules to the BEST policy, to allow the appropriate ports used by Citrix components. For more details, check the following Citrix articles:• Communication Ports Used by Citrix Technologies
• Best Practices for Configuring Provisioning Services Server on a Network
It is especially important to allow the vDisk Streaming (Streaming Service) ports, otherwise the virtual desktops will not boot. For this purpose, you must add a Connection rule with the following configuration:• Local Address set to Any
• Remote Address set to the address of the server hosting the vDisk
• Remote Address port range set to PVS port range
• Protocol set to UDP
• Allow action
Whenever you plan to change the PVS ports or update/upgrade your Citrix software, be sure to check for Citrix port changes and update the BEST firewall rules accordingly. Please follow Citrix recommendations on how to update the ports, as indicated in the next step. - Prepare the target device by following the procedure described in this article.
- Start to deliver virtual desktops to users. The new VMs will appear in the network inventory as being protected by BEST.
Users will see their devices as protected when they access BEST user interface.
To test the protection, you can use an EICAR file. The file will be detected as a virus and it will be deleted. The interface will display the action taken to protect the virtual machine.



 Australia:
(+61) 1300 888 829, (+61) 385 956 732
Australia:
(+61) 1300 888 829, (+61) 385 956 732 Canada:
(+1) 647 977 5827, (+1) 647 367 1846
Canada:
(+1) 647 977 5827, (+1) 647 367 1846  Deutschland:
(+49) 2304 9993004
Deutschland:
(+49) 2304 9993004  España:
(+34) 937 370 223
España:
(+34) 937 370 223
 France:
+33(0)184070660
France:
+33(0)184070660  New
Zealand: (+64) 0800 451 786
New
Zealand: (+64) 0800 451 786  Osterreich:
(+49) 2304 9993004
Osterreich:
(+49) 2304 9993004  România:
(+40) 21 264 1777, (+40) 374 303 077
România:
(+40) 21 264 1777, (+40) 374 303 077  Schweiz:
(+49) 2304 9993004
Schweiz:
(+49) 2304 9993004  United
States: (+1) 954 414 9621, (+1) 954
281 4669
United
States: (+1) 954 414 9621, (+1) 954
281 4669  United
Kingdom: (+44) 2036 080 456, (+44) 2080 991 687
United
Kingdom: (+44) 2036 080 456, (+44) 2080 991 687  WorldWide: (+40) 31 620 4235,
(+40) 374 303 035
WorldWide: (+40) 31 620 4235,
(+40) 374 303 035