Best Practices for Securing Your IoT Household

As smart devices evolve into staples of modern living, securing your IoT household is for your privacy, data, and peace of mind.
Why securing your smart home matters more than ever
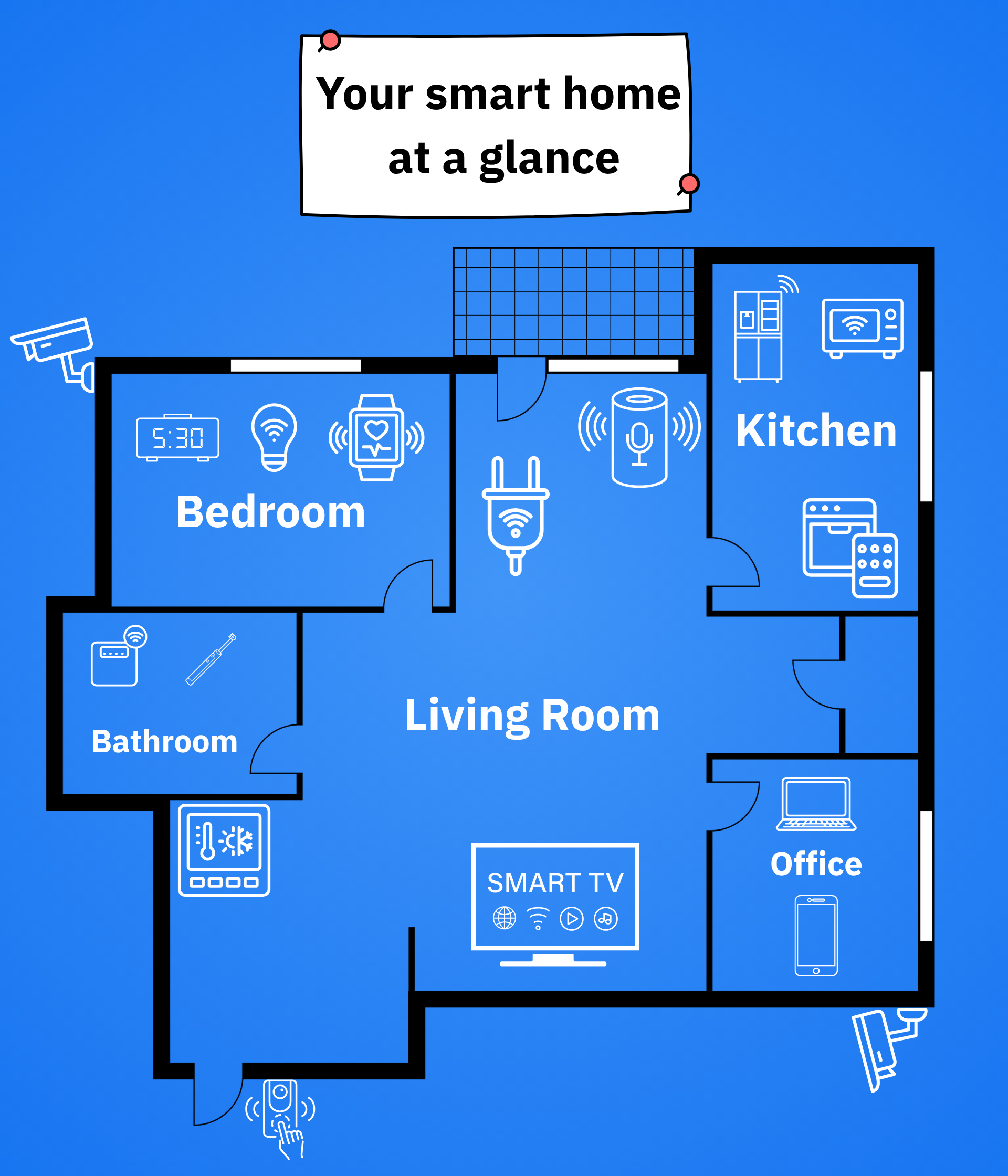
The Internet of Things (IoT) has revolutionized industry, modern homes, and our daily lives. An array of devices heralds great convenience, from baby monitors and connected thermostats to smart doorbells, voice assistants, robot vacuums and smart TVs. However, each new device you add to your IoT ecosystem expands your digital attack surface.
If not properly secured, each device in your household can serve as an entry point for a ruthless attacker. Consumers often assume that cybersecurity is a complicated matter only to be handled by IT professionals or enterprises. However, IoT security starts at home. Our comprehensive guide details the best practices for protecting your smart household from hackers, prying eyes, and digital eavesdroppers.
How to secure your smart home the right way
Before we dive into settings and router configurations, let’s take a step back. It’s important to understand that securing your IoT household isn’t a matter of panic; it should come as naturally as locking your doors before you go to sleep. Awareness, consistency and a few smart habits can go a long way in ensuring your protection. Below, you’ll find clear, practical cyber hygiene tips to help keep your connected devices safe from digital threats.
1. Understand what’s connected
The first step in securing your IoT ecosystem is often overlooked. The importance of understanding what qualifies as an IoT device cannot be overstated.
Many people believe only obvious devices like Alexa or smart cameras fall into this category.
In fact, the IoT ecosystem includes anything that connects to the internet and relays data, whether it’s your smart fridge, fitness tracker or even a children’s toy.
2. Change default settings immediately
One of the biggest mistakes consumers make is leaving default usernames and passwords unchanged after the device’s initial configuration. These credentials are often published online, easily guessed, or displayed in user manuals, making them low-hanging fruit for threat actors.
What you can do:
- Change default usernames and passwords during the initial setup
- Create strong, unique passwords for each device
- Avoid using common password patterns (e.g., Admin123 or SmartHome2025)
- Use a password manager like Bitdefender SecurePass to avoid password fatigue
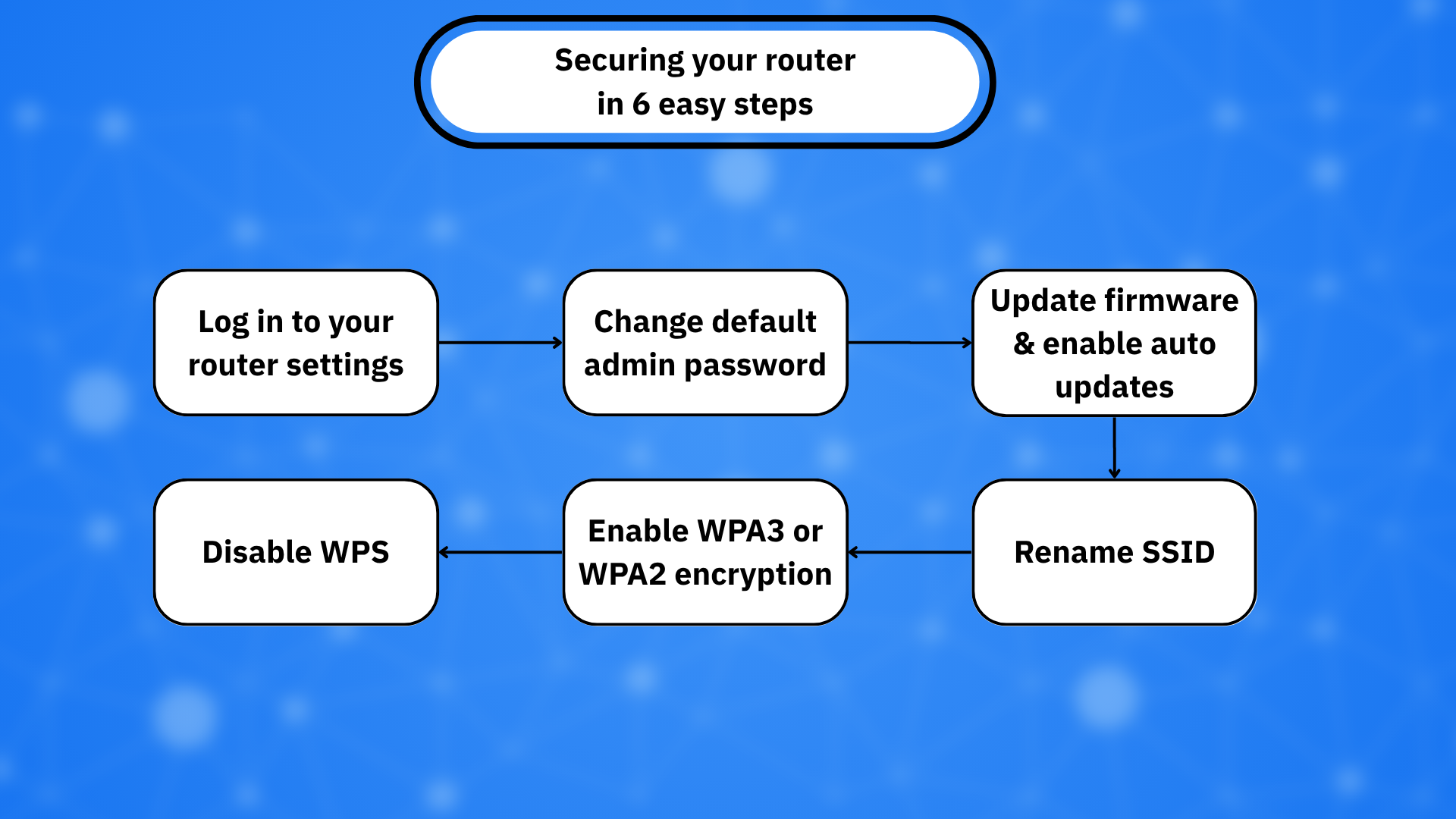
3. Secure your home network first
Your router is at the front line of your defenses, serving as the gateway to your smart home. If threat actors compromise it, every connected device becomes vulnerable. Think of it as a digital front door: keep it locked, monitor it, and don’t let just anyone in.
Best practices for routers:
- Use a strong WPA3 or WPA2 password
- Rename your SSID to something non-identifiable (e.g., not “JohnsonFamilyWiFi”)
- Disable WPS (Wi-Fi Protected Setup)
- Update your router firmware regularly and enable automatic updates
- Enable built-in firewall settings if possible
4. Set up a guest network for IoT devices
Most routers let you set up a separate guest network. This feature shouldn’t be limited to visitors, as it can be a powerful security tool if used right.
Placing IoT devices on a guest network isolates them from your main network, so if a device gets compromised, the attacker can’t jump directly to your computers or other devices that host sensitive data.
Advanced: If your router supports it and you have the know-how, you could try segmenting your network.
How this helps:
- Limits lateral movement if an IoT device is breached
- Reduces exposure of sensitive data on your main network
- Prevents IoT devices from communicating with each other unless absolutely necessary
5. Keep firmware and software updated
Every software or firmware update is another chance to patch security vulnerabilities. Unfortunately, many IoT devices don’t automatically update or even notify you about available updates, leaving you to handle this bit on your own.
Tips:
- Enable automatic updates whenever possible
- Set calendar reminders to manually check for updates monthly
- Buy from vendors with a proven record of issuing regular security patches
6. Limit device permissions and data collection
IoT devices often ask for more permissions than they need, typically under the pretense of improving their functionality. However, not every permission is justified. That smart speaker in your living room? Does it really need access to your contact list, camera, or location? Be intentional about the permissions you grant to your smart devices.
Review and restrict:
- Go through device settings and revoke unnecessary permissions
- Avoid linking too many third-party accounts (e.g., linking your doorbell to a social media account)
- Opt out of data sharing and analytics whenever possible
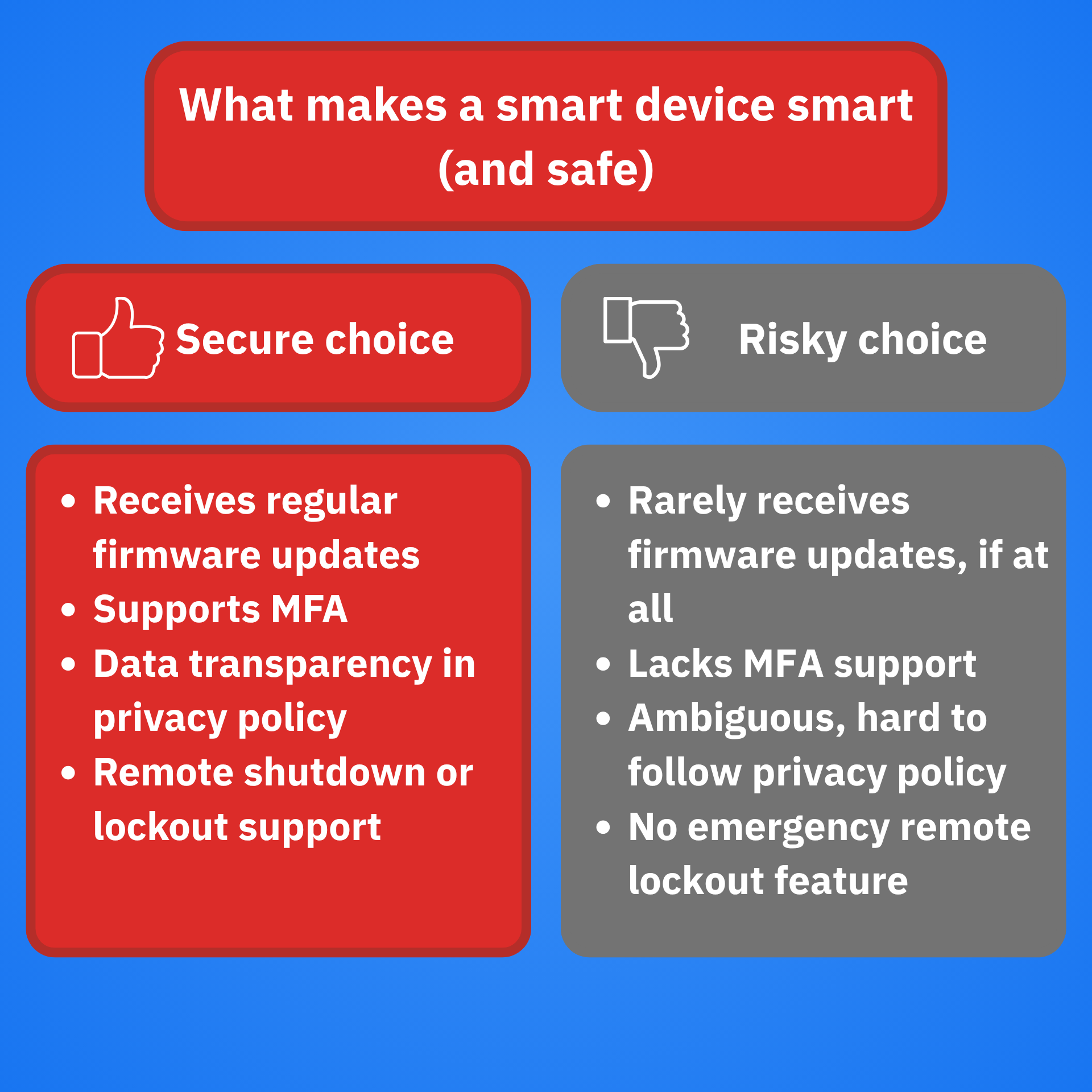
7. Choose security-focused devices
It goes without saying that not all IoT devices are created equal. Some offer far more security features than others, as these specifications entirely depend on their manufacturers.
Look for brands that are transparent about how they handle user data, issue updates and support long-term use. Cheaper devices typically lack advanced security features, and some are even tampered with (e.g., backdoors or malware intentionally planted).
Checklist when buying:
- Does the manufacturer provide regular firmware updates?
- Is multi-factor authentication (MFA) available?
- Can you control and limit your digital exposure?
- Are privacy policies transparent and easy to understand?
8. Use multi-factor authentication (MFA)
Whenever possible, enable MFA on your IoT device accounts. This adds an extra layer of protection to your devices, so even if someone steals your password, they will need a second factor to breach your account.
Best practices:
- Use app-based authenticators like Google Authenticator or Authy
- Avoid SMS MFA if stronger alternatives are available (SIM swapping could bypass SMS-based MFA)
- Enable MFA on your router admin panel, if supported
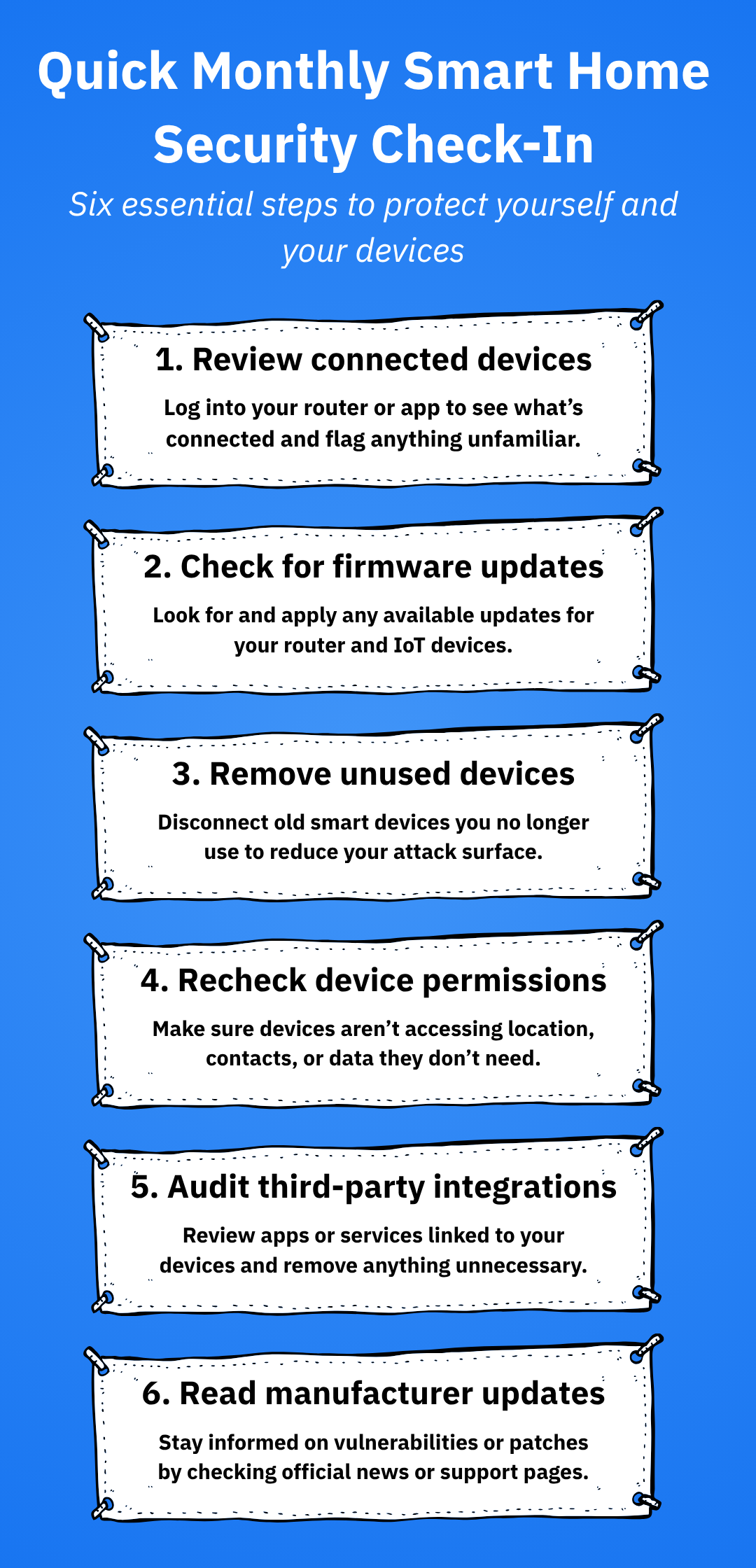
9. Monitor and audit regularly
Securing your IoT home shouldn’t be treated as a “set and forget” event, but turned into a regular activity. Much like a bedtime routine, securing your household’s digital security needs to be treated with the utmost importance. It’s worth noting that technology constantly evolves, and so do threats. A monthly audit of your IoT household can significantly boost your security.
Monthly maintenance checklist:
- Review devices connected to your network
- Check for unusual traffic or slowdowns
- Revoke access for unused or outdated devices
- Stay informed by reading security advisories from manufacturers or cybersecurity blogs
10. Use a dedicated security solution for smart homes
Although it can protect you against numerous digital threats, traditional antivirus software isn’t enough to monitor IoT vulnerabilities. Dedicated solutions like NETGEAR Armor can help you keep an eye on your IoT network, alert you to suspicious activity and provide device-level visibility.
Look for features like:
- Real-time device behavior analysis
- Intrusion detection and blocking
- Automatic threat alerts and remediation
Some advanced home routers even include built-in IoT security features. Investing in such a router might provide extra peace of mind.
Conclusion
Your home should feel like a sanctuary, not a security liability. With the surge of smart devices, taking matters of digital safety into your own hands is now mandatory. By applying these best practices, you can drastically reduce the chances of your household being exposed to cyber threats, and keep your smart home safe and private.
Frequently asked questions about securing your IoT household
How do you secure your IoT devices?
Changing their default username/password combination, updating their firmware regularly (or enabling automatic updates), enabling MFA, limiting their permissions and data collection, isolating them on a guest network and using dedicated solutions like NETGEAR Armor can boost the security of your IoT devices.
How is IoT helpful to secure a home?
IoT can offer a great deal of security to your smart home through devices like sensors, alarms, security cameras and intelligent locks. Advanced features like AI and ML can improve your odds of keeping your home safe with IoT technology.
What is a main security problem for IoT devices?
IoT devices come with default usernames and passwords that are often left unchanged after their initial configuration. Perpetrators can use unchanged credentials to breach your network. Seasoned criminals can also exploit outdated firmware on IoT devices for malicious purposes.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsYou might also like
Bookmarks


