How to Perform a Monthly IoT Security Audit for Your Smart Home

Simple monthly checkups can keep your smart home secure and your data out of the wrong hands.
Nowadays, smart devices are available in almost every house. Not so long ago, the IoT ecosystem encompassed only a few household staples, like thermostats and speakers. Today, refrigerators can reorder groceries and doorbells can stream live video to our phones.
The convenience of smart homes is undeniable. However, each connected voice assistant, smart plug, robot vacuum, or other gadget creates a potentially dangerous entry point that hackers could exploit.
Smart homes are exposed to various digital risks
The Internet of Things (IoT) has revolutionized the way we live, but it has also given cybercriminals an ever-expanding playground. Fortunately, you don’t need to be a cybersecurity expert to protect your home. A simple monthly security audit can go a long way toward keeping your devices and your data safe.
This guide aims to simplify the process by walking you through the steps required to perform a monthly IoT security audit tailored for everyday users, providing clear instructions, tools, and tips.
Whether you're tech-savvy or just starting your smart-home journey, this audit will help you gain control of your smart home ecosystem.
Why you need a monthly IoT security audit
IoT devices are low-hanging fruit for attackers. Unlike traditional computers or smartphones, many smart gadgets lack robust security features, rarely receive updates, and often use default passwords.
Threat actors often scan for weaknesses in these devices and exploit them to:
- Gain access to your home network
- Spy on you through connected cameras or microphones
- Zombify your devices by adding them to a botnet
- Weaponize your devices by using them to launch large-scale botnet attacks
- Steal login credentials, financial data or other sensitive information
These risks and others create a clear need for proactive and routine security checks. A monthly audit ensures you're not leaving open doors for hackers, even if it's unintentional.
What you’ll need
Before you begin, gather a few essentials:
- A list of your IoT devices (TVs, thermostats, smart speakers, cameras, etc.)
- Access to your home router’s admin interface
- A computer or smartphone
- Optional tools include network scanning apps or router companion apps for advanced diagnostics
Many users fear it will be too difficult to carry out periodic security audits on their networks.
The truth is that you don’t need expensive gear or deep technical knowledge, as most of the steps can be taken with minimal effort and free tools.
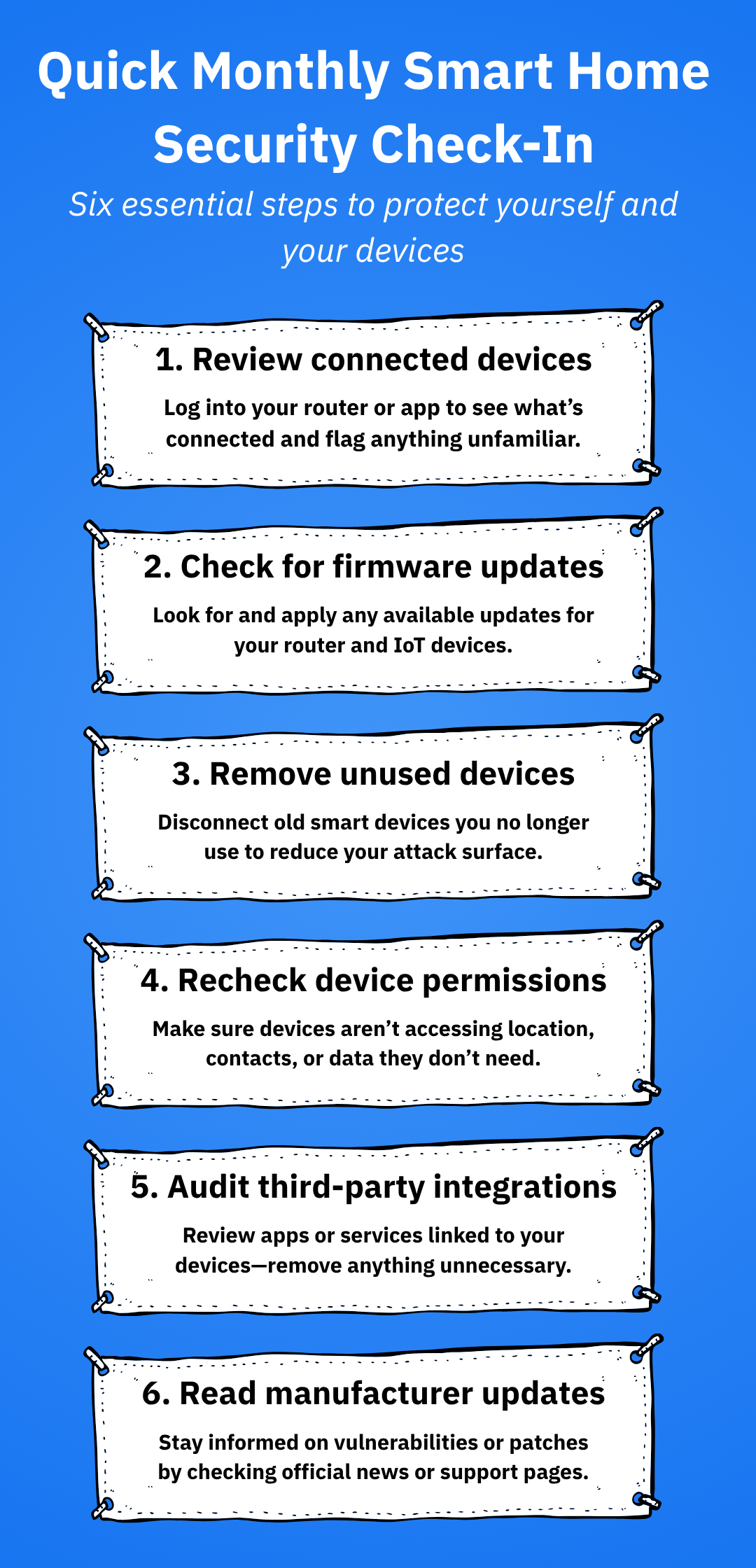
Step-by-step monthly IoT security audit
1. Inventory your devices
Often overlooked, the first step of running a successful security audit on your IoT household is making a full list of all connected devices on your network.
This list is vital to ensure that you don’t miss any device in your assessment.
How to do it:
Use a network scanning tool to scan your Wi-Fi and list every connected device, including the hidden ones.
If you’re not comfortable with dedicated tools, you can use your router’s management interface. However, it may be more tedious, as router administration interfaces lack the advanced features of a dedicated app (e.g. exporting a list of all connected devices).
What to check:
- Is the device recognized by name?
- Are there any devices you don’t recognize?
- Is anything connected that shouldn’t be?
Tip: Label unfamiliar devices as soon as you identify them so you can track them easily next time. Many IoT devices use codenames, which could make them difficult to recognize; labeling them could simplify the tracking process.
2. Check for firmware and software updates
Manufacturers often release patches to fix vulnerabilities. However, many IoT devices aren’t configured to automatically download and install updates.
How to do it:
Open the device's mobile app or web interface and look for a “Firmware Update” or “Software Update” option. If available, install the latest firmware or software versions as soon as possible.
Prioritize updates for:
- Cameras
- Door locks
- Routers
- Anything with access to microphones or video
Tip: Set calendar reminders or enable auto-updates where possible.
3. Change default or weak passwords
A shocking number of breaches occur because users never change default login credentials.
How to do it:
Access each device’s configuration section via its app or web interface. Change both the admin username and password, especially if they’re still “admin” and “password.”
Use strong passwords that follow solid rules, such as:
- At least 12 characters
- Include upper and lowercase letters, numbers, and symbols
- Use a password manager like Bitdefender SecurePass to manage and organize your passwords
Tip: Avoid reusing the same password across devices, as this practice can expose you to credential stuffing attacks.
4. Secure your Wi-Fi network
The router is the gateway to your entire smart home ecosystem. If compromised, all connected devices are at risk.
What to check on your router:
- Change default admin credentials
- Use WPA3 encryption (or at least WPA2)
- Hide the network SSID if you don't want it publicly visible
- Disable WPS (Wi-Fi Protected Setup), which is often vulnerable
Advanced tip:
Consider creating a guest network solely for IoT devices. This separates them from your main computers and smartphones, limiting exposure.
5. Review device permissions
Some IoT devices request more data or access than they need. A monthly review helps limit potential misuse.
Where to look:
Check the companion app’s permissions on your smartphone (camera access, microphone access, location, etc.)
Remove unnecessary access:
- Revoke permissions not essential to functionality
- Check third-party integrations (e.g., Alexa Skills) and remove those you don’t use
Tip: Most of the time, less is more, so consider disabling what you don’t use.
6. Scan for vulnerabilities
Network scanning tools can check for common misconfigurations and vulnerabilities.
Try these solutions:
- Router web interface diagnostics
- Bitdefender Box, NETGEAR Armor, or other dedicated IoT security tools
In doing so you can identify open ports, suspicious traffic, or outdated firmware. Dedicated tools can also help you with suggestions on patching weak spots in your network’s security.
Note: You don’t need to act on every alert immediately, but make sure to prioritize critical risks.
7. Audit physical access
Oftentimes, the easiest attack vector is physical access. Make sure no one can tamper with your devices or router.
What to do:
- Ensure smart locks, cameras, and hubs are in secure locations
- Keep your router out of sight
- Use tamper-proof hardware or locks for external devices
8. Review logs and alerts
Many smart devices and routers offer logs of access attempts or abnormal behavior. Make sure to check them for suspicious behavior. This can help you mitigate security incidents before they have a chance to cause real harm to your network.
What to look for:
- Unusual login attempts
- Multiple failed logins
- New or unknown devices connecting
Enable alerts:
Some devices or security platforms allow you to receive push notifications for suspicious activity. Turn these on.
9. Back up configurations
Before making major changes (like firmware updates), back up device configurations if possible. This allows for quick recovery if something goes wrong.
Tip: Store backup files in a secure, encrypted cloud storage service or external drive. If possible, opt for cold (offline) backups to avoid exposing your backups to online threats.
Pro tips for tech-savvy users
- Set up VLANs: Segmenting your network with virtual LANs can isolate IoT traffic from sensitive devices
- Use Pi-hole: A Raspberry Pi running Pi-hole can block ads and malicious domains across your network
- Monitor DNS traffic: Look for strange domain queries that could indicate a compromise
- Use a firewall: A home firewall can provide advanced logging and filtering
Conclusion
As smart homes become smarter, owners must keep pace, lest they turn smart devices into security liabilities.
Although a monthly IoT security audit sounds like a burden, it’s an essential routine that ensures your family’s privacy, data, and safety. Think of it like checking whether you locked your doors at night. It’s a basic step that goes a long way.
By dedicating just 30 minutes a month, you can significantly reduce the chances of your home network being compromised. Over time, it becomes second nature.
Frequently asked questions about monthly IoT security audits
What if I don’t recognize a device on my network?
First, check with family members or roommates. Sometimes, devices appear under unfamiliar names. If it remains unrecognized, disconnect it via your router settings and investigate further.
Can I automate this monthly audit?
Some tasks, like firmware updates and alerts, can be automated. However, it’s best to review your network and devices manually at least once a month.
Is a guest network really necessary for IoT devices?
It’s strongly recommended. Separating your IoT devices prevents potential intrusions from spreading to laptops, phones, and other personal devices.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsYou might also like
Bookmarks


