Cyber-Hygiene for Non-Tech Family Members

Technology keeps surging forward, but not everyone moves with it. This guide helps bridge the gap by teaching essential cyber hygiene to people who didn’t grow up online.
Protecting your loved ones in the digital world
Thanks to technological advancements, convenience has increased significantly in the last few years. However, our digital-forward existence has made cyber safety a necessity.
While tech-savvy users may have an advantage due to their ability to grasp the nuances of password managers, multi-factor authentication, and phishing scams, many of our loved ones may not.
That’s where cyber hygiene comes in: the practice of maintaining good cybersecurity habits to prevent scams, identity theft and even data breaches.
Our guide aims to break down cybersecurity into manageable steps, making it easier for non-technical family members to understand and apply basic digital safety principles in their daily lives.
What is cyber hygiene?
Cyber hygiene is to your devices what personal hygiene is to your health. It’s a series of regular habits and practices that helps keep your digital footprint clean, safe, and secure. While you may already follow many of these practices yourself, your family members may be more vulnerable if they aren’t aware of common cyber risks.
The most common examples of poor cyber hygiene include:
- Using the same password for multiple accounts (password recycling)
- Ignoring or postponing software or firmware updates
- Interacting with suspicious links, especially those from unknown senders
- Leaving devices unlocked in public places
- Carrying sensitive operations on public, unsecured Wi-Fi networks

Why non-tech users are prime targets
It’s a common misconception that threat actors “favor” the wealthy or tech-savvy. In fact, they often go after those they believe are easier to exploit. Scammers combine social engineering and persuasion tactics to trick people into giving up sensitive information, making fraudulent payments, or installing malware.
Common reasons why non-tech users are vulnerable
Another misconception is that it’s a matter of intelligence. It actually depends more on non-tech users’ lack of training to spot online threats. The most common factors in the elevated risk of non-tech users include:
- Lack of awareness of fake websites and scams
- A trusting nature exposes them to seemingly legitimate emails, texts or phone calls
- Reluctance to ask for help due to embarrassment
- Unfamiliarity with verifying website URLs or spotting phishing attempts
These reasons are precisely why training to spot red flags from afar can help keep non-tech users safe online. Just like teaching a child to look both ways before crossing the street, teaching cyber hygiene is crucial in building healthy habits and raising awareness.
The core pillars of cyber hygiene
If you want to explain essential cybersecurity concepts to your family in simple, relatable steps, here’s how you can do it:
1. Passwords are like toothbrushes
- You never share them
- You have to change them regularly
- You shouldn’t use the same one for everything
Tip: Encourage them to use passphrases instead of passwords, as they are more difficult to crack. For instance, “IloveDogs2025!” can be significantly harder to crack than “password123.”
Pro tip: Memorizing many passwords can lead to something called “password fatigue,” which is precisely what it sounds like. A password manager like Bitdefender Password Manager can significantly simplify things.
2. Updating software is like getting a flu shot
You can use a comparison with seasonal vaccinations to teach them about the importance of keeping software up to date. More often than not, updates aren’t just about adding new features to apps or devices; they patch vulnerabilities that hackers can exploit.
Tip: If possible, enable automatic updates for the following:
- Operating systems (Windows, macOS, Android, iOS)
- Antivirus (Bitdefender Ultimate Security, Bitdefender Mobile Security for Android & iOS)
- Browsers and apps
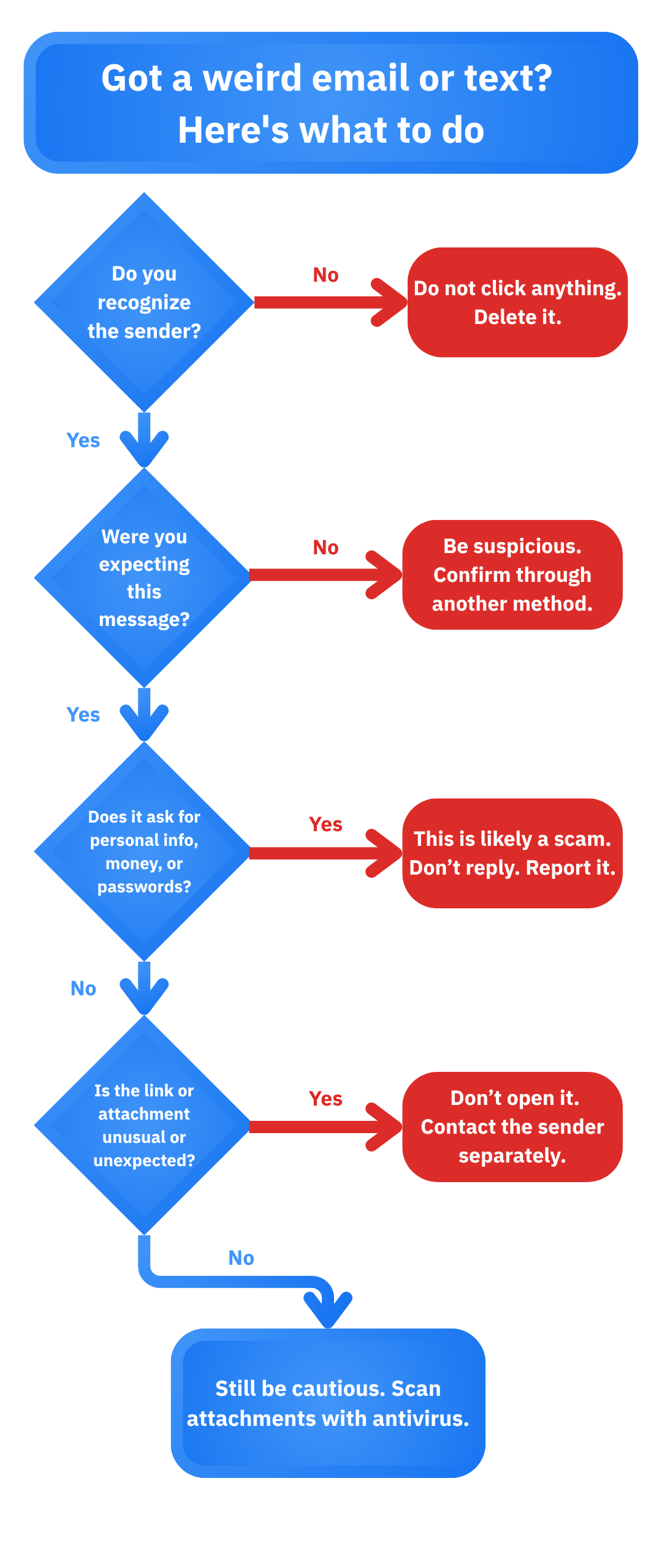
3. Think twice before you click
Phishing attacks typically exploit lack of attention and people’s trusting nature. Teach non-tech-savvy users in your household how phishing works. Show them real (but safe) examples of scam emails or texts. Discuss the most common scenarios, such as the “account verification,” “Nigerian prince,” “fake invoice,” “bank alert” or “tax refund” scams. Encourage a “when in doubt, don’t click” approach.
Key red flags to highlight include:
- A sense of urgency instilled by the sender (“Act now or lose access!”)
- Unknown senders or strange email addresses
- Attachments they weren’t expecting
- Strange requests from seemingly legitimate entities (such as bank representatives asking for credit card details, police officers asking for personal data)
4. Encourage multi-factor authentication (MFA) usage
You should discuss the importance of implementing MFA wherever possible. MFA is like an additional lock underneath the main lock – and you hold the only key (ideally). Even if a threat actor obtains the key to the main lock (your account password), they will still need the MFA confirmation to gain access.
Tip: If the concept still sounds foreign, try explaining it like this: “It’s like needing both a key and a secret handshake to get in.”
Teaching tech-averse family members
It’s essential to remember that not everyone learns in the same way, or even perceives technological advancements in the same manner. While some may be indifferent, others may even dislike or oppose them; you will need to find common ground, try a different approach and keep your guidance simple, empathetic and interactive.
Ways to help
- Start with real-life scenarios: “What would you do if someone emailed you to say your bank account was locked?”
- Use analogies: Relate digital threats to physical ones (e.g., “Would you give your house keys to a stranger?”)
- Create routines: Schedule a “Digital Safety Sunday” each month to check devices together
- Avoid jargon: Instead of “phishing,” say “a scam message trying to trick you.”
- Encourage the use of dedicated tools: Bitdefender’s Scamio can help you spot scams in texts, emails, images, QR codes and links before they do harm
Devices need protection too
However, cyber hygiene is not just about your behavior online. Devices themselves also require some basic security settings to be enabled. Internet of Things (IoT) devices, also known as smart home devices, are incredibly convenient, but they’re also often overlooked in family cybersecurity plans.
Connected cameras, Wi-Fi doorbells, thermostats, smart speakers, and even smart refrigerators are part of the attack surface if left unsecured.
These devices may seem harmless, but they are often shipped with weak default settings and may lack robust built-in security features.
Risks for non-tech IoT users
- Default passwords: Many devices come with weak predefined credentials like “admin/admin” that are rarely changed, if ever
- Outdated firmware: Unlike phones or computers, IoT devices rarely prompt users to update their firmware
- Poor app security: Control apps for smart devices may have weak default safeguards
- Excessive data collection: Devices may violate privacy by recording audio, video, or behavioral data without users fully understanding or consenting
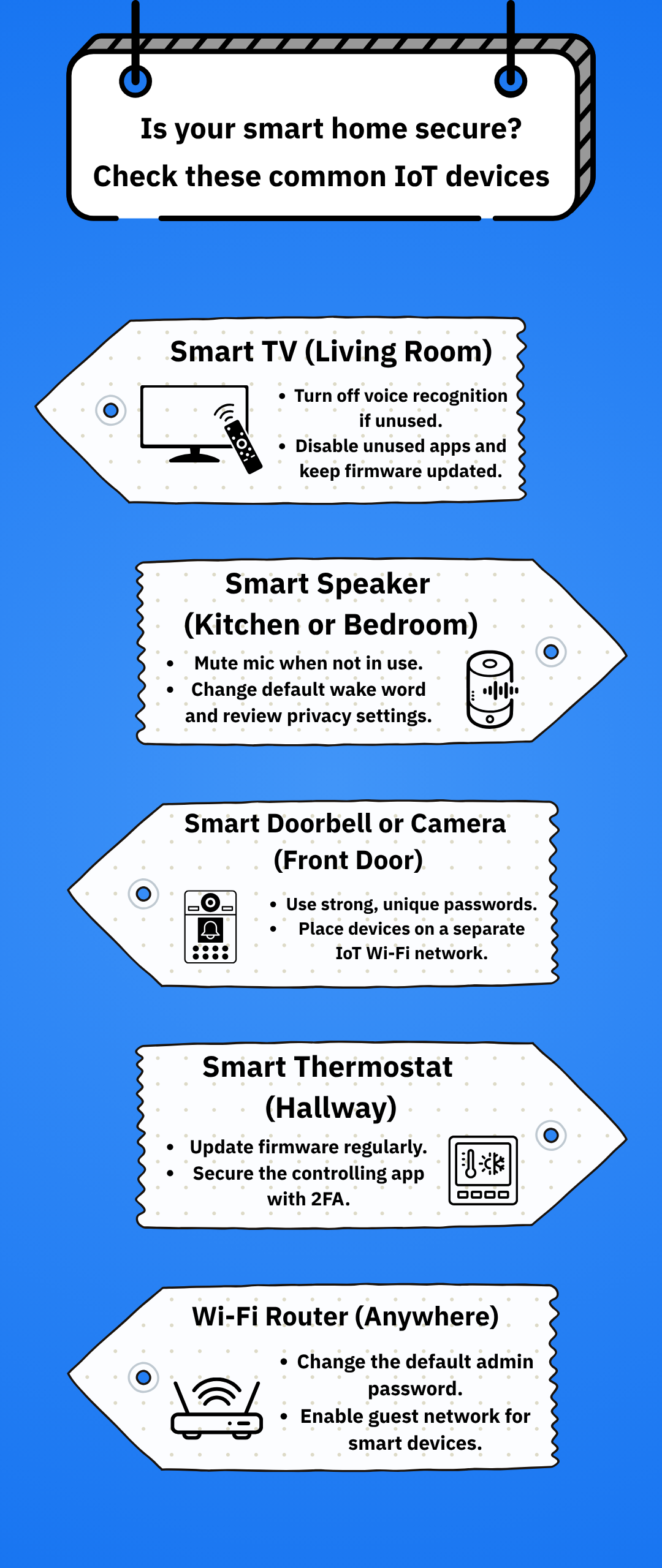
How to keep smart devices safe
Although many IoT devices are shipped with weak built-in security, there are several steps you can take to enhance their security:
- Change default passwords immediately after setting them up, and use strong, unique passwords
- Disable features you don’t need like remote access or voice recognition if you never plan to use them
- Check for firmware updates through the device app or manufacturer’s website every few months
- Segment your network or place smart devices on a separate “guest” or IoT network if your router allows it
- Enable encryption and multi-factor authentication (MFA) in the device app if possible
- Run monthly security audits on your IoT devices to catch potential issues early
- Use dedicated security software like NETGEAR Armor to protect devices connected to your smart home ecosystem
Tip: Encourage family members to think of smart devices like windows; they are highly useful, but need to be closed when not in use and properly secured to prevent unwanted access.
Creating a family cyber safety plan
Last but not least, it’s worth noting that security works best when it’s not perceived as a burden, but a shared responsibility. Consider creating an easy-to-follow cyber hygiene plan for your family.
If you don’t know where to begin, feel free to use the infographic below as a starting point –you can even download and print it for an easy and accessible starter plan. Make sure you encourage your family to:
- Share their concerns and suspicions if they ever feel something is off
- Use a group chat for flagging potential scams and sharing suspicious links or situations with other family members
- Regularly review settings on social media and mobile apps

Conclusion
Although teaching cyber hygiene to non-tech family members can be challenging, it is a form of digital caregiving that can prevent unpleasant situations and foster confidence, independence, and peace of mind.
The more empowered and confident your loved ones feel in protecting themselves against digital threats, the more secure your whole family becomes. Our advice is to start small, be patient, and celebrate progress, no matter how small, because every safe login and ignored scam attempt is a win.
Frequently asked questions about cyber hygiene for everyday users
Can a non-technical person do cybersecurity?
Non-technical users can definitely learn cybersecurity by gaining basic awareness and gradually advancing to more advanced techniques, such as structured courses and hands-on practice.
What is an example of cyber hygiene?
Cyber hygiene encompasses a series of recommendations designed to maintain your digital privacy and security, including using robust, unique passwords, avoiding clicking on random links, refraining from sharing sensitive information with strangers, and regularly updating software.
What are the most common problems associated with poor cyber hygiene?
Some common issues that may arise due to poor cyber hygiene include data breaches, privacy violations, financial losses, crypto theft, blackmail, and coercion.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks