ClickFix Malware Chain Expands: Fake TradingView and Sora 2 Ads On Meta Now Target macOS Users

Threat actors behind a long-running malvertising campaign impersonating popular investment and trading platforms, such as TradingView, are back with a new trick, targeting macOS users.
As usual, the campaign uses sponsored Facebook ads that promote fake AI and trading apps, including “Sora 2” and “TradingView Desktop,” to deliver a new macOS payload as part of the malvertising campaign that previously targeted Windows and Android users.
Read more about these global malvertising campaigns here:
- The Scam That Won’t Quit: Malicious “TradingView Premium” Ads Jump from Meta to Google and YouTube
- Malvertising Campaign on Meta Expands to Android, Pushing Advanced Crypto-Stealing Malware to Users Worldwide
- Weaponizing Facebook Ads: Inside the Multi-Stage Malware Campaign Exploiting Cryptocurrency Brands
- Pi2Day Scams: Crypto Users Targeted in Coordinated Facebook Ad Campaign Delivering Malware and Stealing Wallets
- Facebook Ad Scam Tricks Investors with Fake Messages and Malware Disguised as ‘Verified Facebook App’
Two campaigns linked to one cybercriminal infrastructure
Bitdefender researchers Andreea Olariu and Ionut Baltariu have tracked two closely related malvertising waves within this ongoing operation:
November 5–6 – Fake TradingView Premium Ads
The first phase impersonated TradingView Desktop and TradingView Premium products. The malicious ads were distributed via Meta and targeted macOS users only, redirecting them to https://tradingview.promo2026[.]com.
The fake website mimicked TradingView’s interface and offered a “Download for macOS” button. Instead of a legitimate installer, the page presented a Base64-encoded terminal command that, once executed, downloaded and launched a malicious script.
These ads were active for a couple of days before Meta removed them.

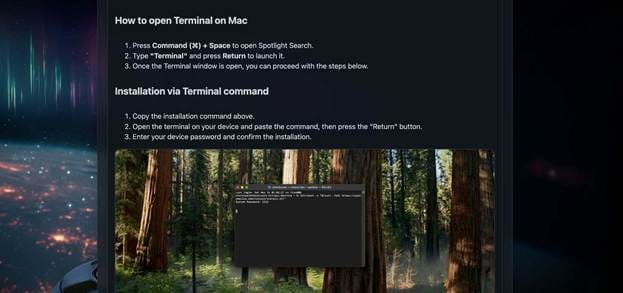
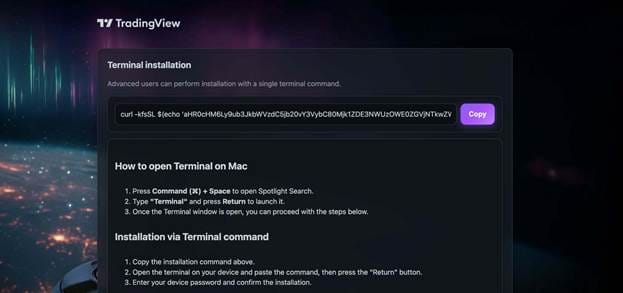
November 9 – Fake Sora 2 Ads
Days later, the same Meta page started promoting Sora 2, a lure clearly designed to appeal to content creators. The malicious ad directed users to sorachatgpts[.]com
Unlike the TradingView wave, this one targeted both macOS and Windows users:
- macOS variant: used a ClickFix-style technique, urging readers to run a terminal command that decoded and fetched a second-stage MacStealer payload.
- Windows variant: delivered a ZIP archive containing a malicious executable and multiple DLLs.
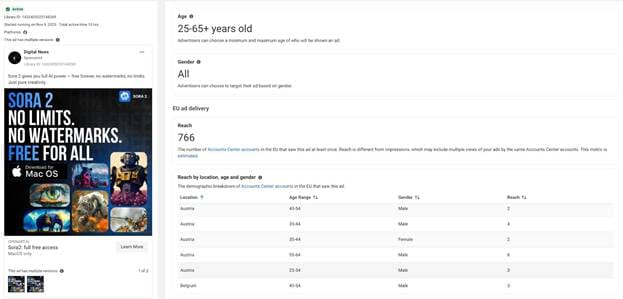
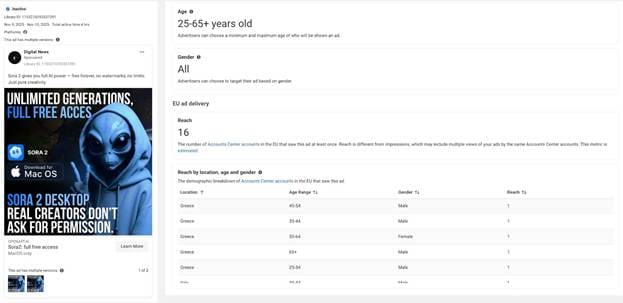
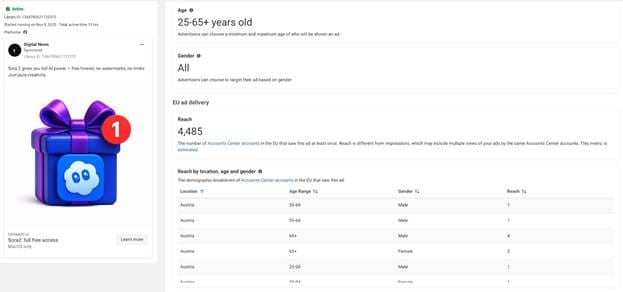
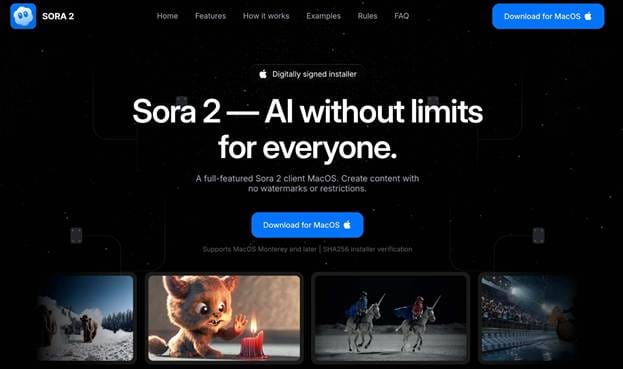
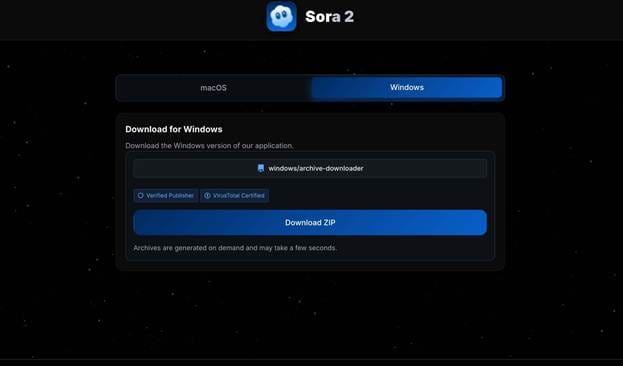
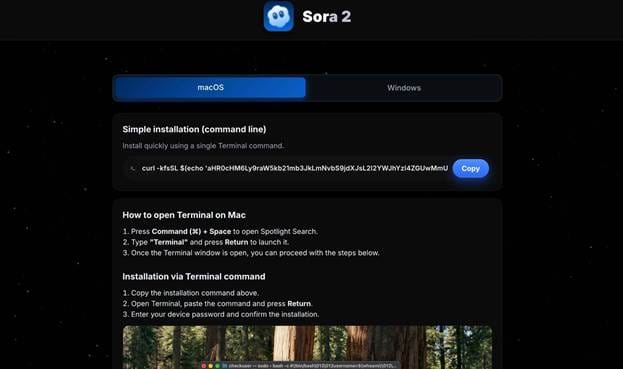
Despite the cosmetic differences, both waves share identical visual templates, delivery mechanisms, and hosting infrastructure, confirming that they are part of the same coordinated malvertising campaign.
Inside the macOS Infection Chain - MacSync Stealer version 1.0.8
The macOS payload represents a new refinement to this operation. Once the user executes the encoded command, the infection unfolds in multiple layers:
Stage 1 – Loader Script
Downloads and runs a gunzip-encoded shell snippet that retrieves the next payload.
Stage 2 – AppleScript Infostealer
The next-stage script is a full-featured MacSync Stealer, capable of:
- Exfiltrating files and documents from the system
- Displaying a fake macOS password prompt to harvest credentials
- Stealing browser data (cookies, login databases, extensions)
- Collecting Telegram, macOS Notes, and crypto-wallet information
- Compressing everything into /tmp/osalogging.zip and exfiltrating it via HTTP POST with a specific API key and browser-like User-Agent
The malware also establishes persistence by replacing legitimate crypto-wallet applications like Ledger Live and Trezor Suite with trojanized versions downloaded from the same C2 server.
What the Stealer Targets
The updated MacSync Stealer version 1.0.8 is highly aggressive, collecting:
- Crypto wallets: Exodus, Electrum, Atomic, Guarda, Coinomi, Sparrow, Wasabi, Monero, Litecoin Core, Trust Wallet, and many others.
- Browser extensions: MetaMask, Phantom, Coinbase Wallet, OKX, Rabby, Bybit, Solflare, Binance Extension Wallet (deprecated), plus dozens more.
- Password managers: Bitwarden, 1Password, Dashlane, LastPass, Keeper, NordPass, Zoho Vault, and over 20 others.
This shows that this campaign isn’t just about traditional credential theft but escalates into full data-exfiltration campaigns that blend infostealers and crypto-drainers.
The operation demonstrates how malvertising has become a preferred delivery vector for cross-platform malware, allowing threat actors to inject fake installers directly into users’ social feeds through paid and “verified” ads.
Although Meta has removed some of the malicious ads, Bitdefender research shows that similar campaigns are likely to reappear under new branding, as the same threat actors continue to adapt their lures.
How to Stay Safe
- Avoid installing software via ads. Always download apps directly from official websites or the App Store.
- Never run copy-paste terminal commands from unverified sources as this is a common trick to trigger hidden downloads.
- Use reliable protection like Bitdefender Premium Security, which detects and blocks macOS and Windows stealers in real time.
- Check the advertiser’s identity before clicking any “Download Now” button in sponsored ads.
- Use free scam detection from Bitdefender such as Link Checker and Scamio.
- Stay vigilant and follow cybersecurity blogs and alerts like Bitdefender hotforsecurity for the latest updates on malicious campaigns and scams.
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsYou might also like
Bookmarks
