The Scam That Won’t Quit: Malicious “TradingView Premium” Ads Jump from Meta to Google and YouTube

Over the past year, Bitdefender researchers have been monitoring a persistent malicious campaign that initially spread via Facebook Ads, promising “free access” to TradingView Premium and other trading or financial platforms.
According to researchers at Bitdefender Labs, this campaign has now expanded beyond Meta platforms, infiltrating both YouTube and Google Ads, exposing content creators and regular users alike to increased risks.
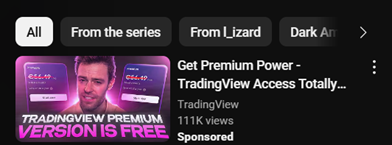

Unlike legitimate ads, these malicious campaigns redirect users to malware-laced downloads aiming to steal credentials and compromise accounts.
You can read more about these global malvertising campaigns here:
- Malvertising Campaign on Meta Expands to Android, Pushing Advanced Crypto-Stealing Malware to Users Worldwide
- Weaponizing Facebook Ads: Inside the Multi-Stage Malware Campaign Exploiting Cryptocurrency Brands
- Pi2Day Scams: Crypto Users Targeted in Coordinated Facebook Ad Campaign Delivering Malware and Stealing Wallets
- Facebook Ad Scam Tricks Investors with Fake Messages and Malware Disguised as ‘Verified Facebook App’
Hijacked Google Ads account and TradingView Impersonation on YouTube: How the Scam Works
Looking into the specifics of the scam impersonating TradingView, researchers found that threat actors hijacked the Google advertiser account of a design agency in Norway. Separately, the cybercrooks also took over a YouTube account to which they could begin redirecting victims through Google’s ads system. Once again, the verified status of the compromised YouTube channel, combined with its new branding and TradingView visuals, allowed cybercriminals to impersonate the official TradingView channel. The rebranded channel was designed to be nearly indistinguishable from TradingView’s by:
- Reusing official branding, with logos, banners, and visual elements identical to the real TradingView.
- Mirroring playlists – playlists on the homepage are linked from the official TradingView channel, making the fake channel look active, even though it has no videos of its own.
- Abusing the verified badge on YouTube – since the channel was previously verified for legitimate reasons, users assume authenticity without checking deeper.
You may also want to read: Malicious Facebook Ads Push Fake ‘Meta Verified’ Browser Extensions to Steal Accounts
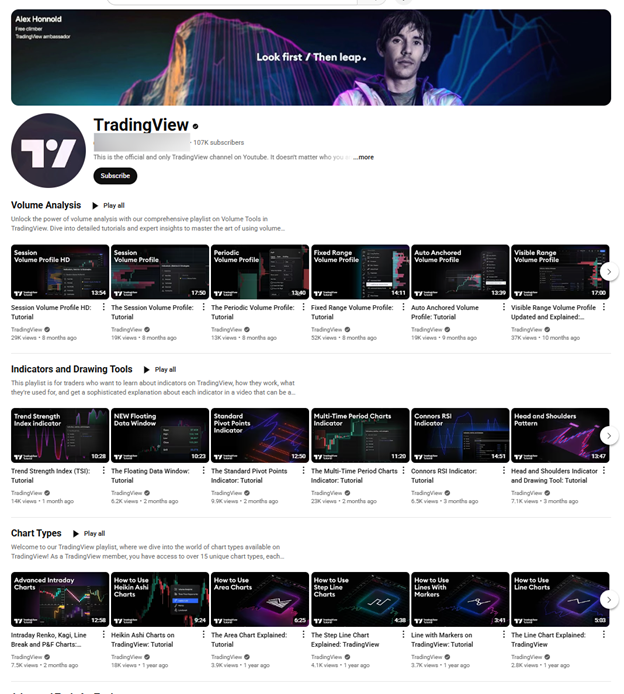
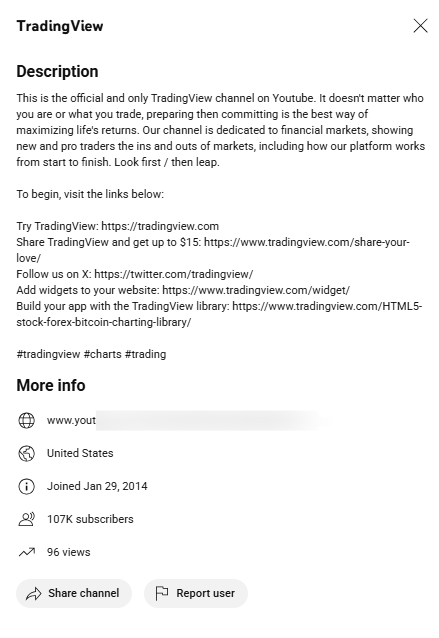
Upon closer inspection, several red flags emerge:
- The channel handle is different (not @TradingView);
- The channel itself contains no original content, only having 96 registered views, which would be impossible for a legitimate channel given Tradingview’s popularity;
- The impersonation relies entirely on unlisted ad videos shown only through paid placements, avoiding public scrutiny;
One ad video is titled “Free TradingView Premium – Secret Method They Don’t Want You to Know”. Despite being unlisted, it gained over 182,000 views in just a few days through aggressive advertising.
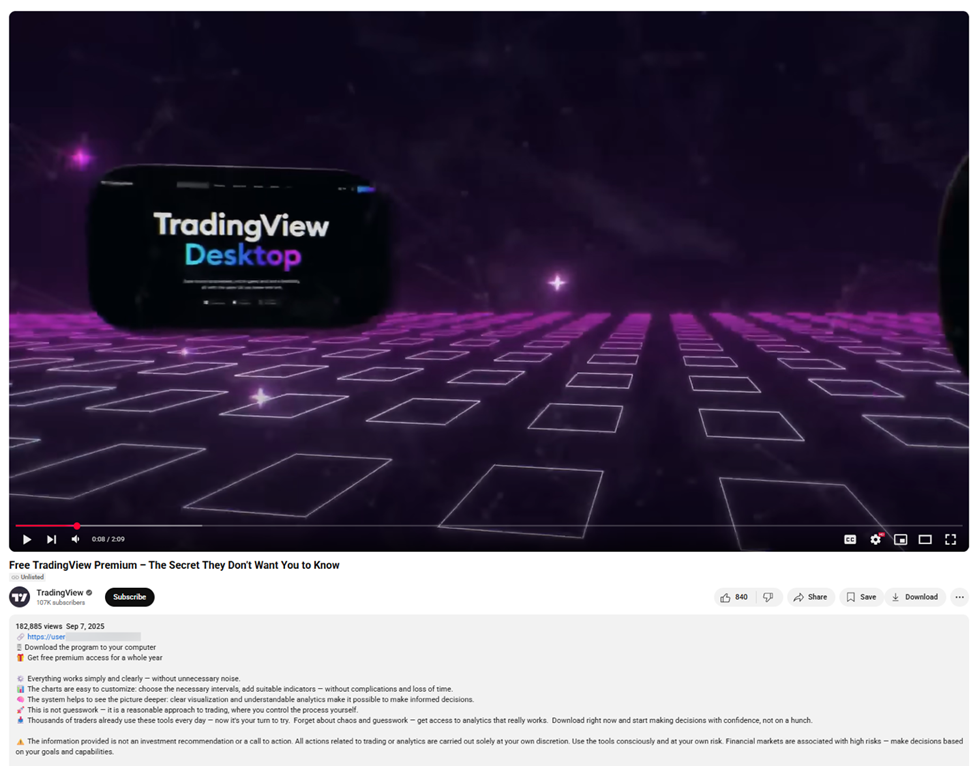
The video’s generic promotional content mentions the capabilities of the TradingView application. The description of the unlisted video includes a link where the user can download the malicious executable. Just as in the Meta ads, the user might end up on a benign page if the attackers don’t think the requests were made from a valid target.
Why unlisted videos? The unlisted status is deliberate, of course. By not being publicly searchable, these malicious videos avoid casual reporting and platform moderation. Instead, they are shown exclusively through ad placements, ensuring they reach their targets while remaining hidden from public view.
The description promises benefits such as simplified trading, personalized indicators, and “reasonable” trading strategies. To build trust, it even includes disclaimers about financial risks. However, these messages mask the real intent:
- Redirecting victims to malware downloads;
- Using phishing pages to steal credentials;
- Spreading across multiple channels and domains.
How Business Accounts Become Weapons
This case highlights a growing risk: when a company’s Google account is compromised, its connected YouTube channel can be stripped of all original content and repurposed for scam and other malicious activities.
Here’s how compromise can occur:
- You or your staff members fall for a phishing email, malicious attachment, or credential-stealing campaign that gives attackers access to the Google account.
- Since YouTube is tied to Google, the attackers gain control of the channel.
- To erase any trace of the original business identity, attackers delete existing videos, branding, and playlists.
- The account is rebranded to impersonate a popular brand such as TradingView. Verified badges and existing subscriber counts lend credibility.
- Instead of building organic reach, attackers exploit Google Ads to push malware-laden unlisted videos directly to users.
Malware Analysis
Upon analyzing the malware, Bitdefender researchers identified that, while it shares traits with past samples (such as those detected as Generic.MSIL.WMITask), the initial downloader was custom-built to resist detection and analysis.
- Oversized downloader – at over 700 MB, it is too large for most automated analysis platforms to process.
- Anti-sandbox capabilities – it checks for virtualized or sandboxed environments, making both automated and manual dynamic analysis difficult.
- Multi-stage infection – once it bypasses these defenses, the malware proceeds with techniques consistent with past infostealer campaigns.
While the old samples were communicating with the “front-end” via plain HTTP requests on various ports (30303, 30308) and routes (/s, /set, /q, /query), the new sample communicates using websockets, on the port 30000 and the /config route.
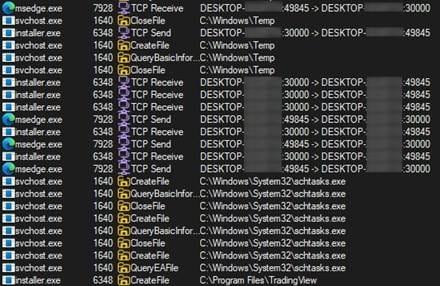
The cybercrooks changed the Front-End scripts so they are not as easy to investigate. The code is first obfuscated and encrypted with AES-CBC.
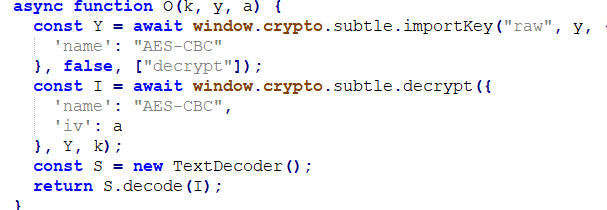
Then, the decrypted service worker code is also obfuscated. Upon deobfuscation, it can be seen that it uses https://jimmywarting.github.io/StreamSaver.js to deliver the malicious file (when the user downloads it). This can be done to avoid detection and to make manual analysis more difficult. We can also see the configuration for communicating with the malicious executable:
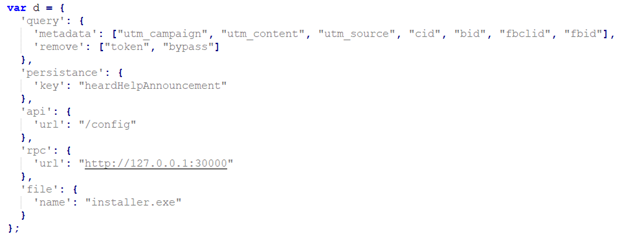
As seen in the previous samples, the sample uses PostHog for user tracking, while also using Facebook Pixel tracking, Google Ads Conversion Tracking, Microsoft Ads Pixel and Adprofex postback. These tracking efforts, obviously without user consent, offer a clear idea of how these threat actors might end up targeting users on multiple platforms, while also allowing them to block certain requests or display benign content to users not considered valid targets.
The installer.exe malware (another difference is the type of executable - the old sample was a .msi file) proceeds to create a Scheduled Task called EdgeResourcesInstallerV12-issg with the payload it received through websockets.
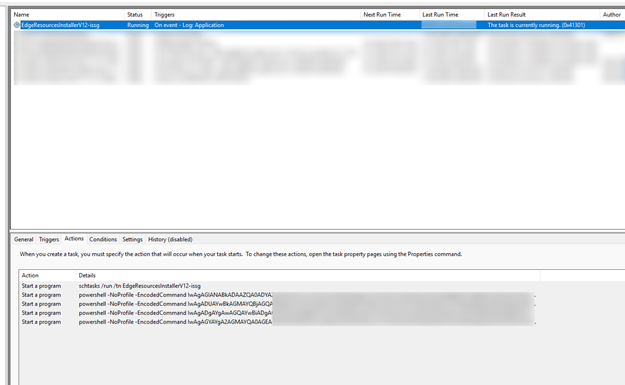
Through these scheduled tasks, the malware adds Windows Defender exclusions and downloads and executes the next stage using the Invoke-Expression powershell cmdlet. The whole malicious process can be seen below in a simplified form.
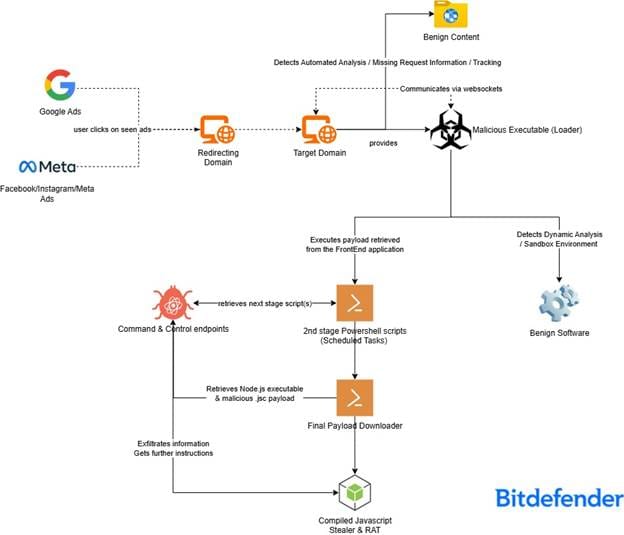
Bitdefender detects the initial loader as Variant.DenoSnoop.Marte.1, the intermediate powershells with various detections and the final payload as Trojan.Agent.GOSL. The malware (final payload), named JSCEAL by Checkpoint and WeevilProxy by WithSecure, is a sophisticated stealer with both espionage and remote access capabilities.
Capabilities include:
- Intercepting all user network traffic (acting as a proxy)
- Collecting cookie and password data
- Keylogging and taking screenshots
- Stealing cryptocurrency wallet data
- Ensuring long term persistence, and more
Bitdefender’s prolonged analysis of this malicious advertising campaign found:
- Over 500 domains and subdomains tied to this malicious infrastructure;
- Emerging macOS and Android samples designed to extend the attack beyond Windows (which are detected as Variant.MAC.Amos.9 and Android.Trojan.Dropper.AVV & Android.Trojan.Banker.AVM);
- Multiple hijacked or impersonated channels/pages pushing identical campaigns
- At least a couple of stolen Google accounts were observed;
- Thousands of Facebook pages (mostly with fewer than 5 likes and generic names and images) distributing malicious ads;
- Threat actors are creating hundreds of ads daily in multiple languages (especially English, Vietnamese and Thai) while rotating used domains and employing new strategies.
An up-to-date, complete list of indicators of compromise is available to Bitdefender Advanced Threat Intelligence users here.
How to Stay Safe (for Users)
If you encounter ads promising free access to premium trading tools or software:
- Check the channel handle and subscriber count.
- Be wary of unlisted videos. It is not common for real companies to run unlisted ad-only campaigns.
- Don’t download software from third-party links – use official websites only.
- Always report suspicious ads directly to YouTube or Google Ads
- Use security solutions from Bitdefender to block malicious links and malware before it can damage your device and compromise data.
- Use free scam detection tools like Bitdefender Scamio and Bitdefender Link Checker to scrutinize links, offers, and ads.
Defending Against Account Takeovers (for Content Creators and Businesses)
Creators and organizations with a YouTube presence are also targets of these campaigns. Hijacked accounts not only damage reputations but also put followers at risk. Here’s a quick checklist of what you can do now to stay safe:
- Enable strong multi-factor authentication (MFA) for your online accounts.
- Review account recovery options by ensuring backup emails and phone numbers are valid and secure.
- Regularly audit channel roles and permissions. Don’t forget to revoke access for inactive managers.
- Monitor for unusual activity, such as sudden changes in branding or video uploads, that can signal compromise.
- Leverage comprehensive security tools like Bitdefender Security for Creators, which provides account takeover protection, phishing detection, and enhanced monitoring for creator accounts on YouTube, Facebook and Instagram. If you’re a small business owner, check out Bitdefender Ultimate Small Business Security here.
- Stay informed and practice scam awareness — impersonation and ad abuse campaigns evolve quickly, so ongoing awareness is crucial. Stick to our blog for more insights on scam tactics and campaigns targeting consumers, content creators and small businesses.
tags
Author
I’m a software engineer with a strong focus on cybersecurity, on a mission to make the digital world safer and more resilient. I love building solutions that protect people and organizations globally.
View all postsI'm a software engineer with a passion for cybersecurity & digital privacy.
View all postsYou might also like
Bookmarks






