Bitdefender Threat Debrief | July 2025

Global Hits the Ground Running with RaaS Release
This Threat Debrief release covers key changes among ransomware groups, including the emergence of Global, a recent update on Qilin’s rise, and developments connected to DragonForce and Scattered Spider.
Ransomware is a moving target, and our goal with this monthly Bitdefender Threat Debrief is to help you stay ahead of the curve. To do this, we combine information from openly available sources (OSINT) - things like news reports and research – with data we gather by analyzing Data Leak Sites (DLSs), websites where ransomware groups post details about their victims. It’s important to remember that we can't independently verify all of these claims but are confident in the trends we see over time.
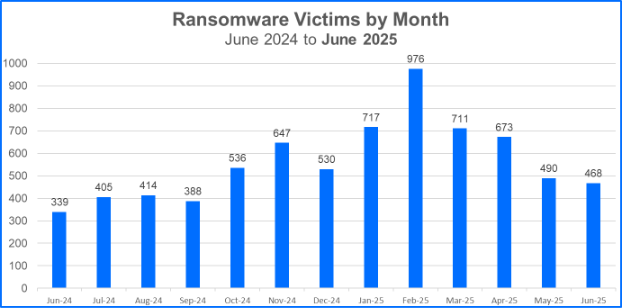
For this month's report, we analyzed data from June 1 to June 30 and recorded a total of 468 victims claimed. This is a 38% increase compared to June 2024.
Featured Story: Global Hits the Ground Running with RaaS Release
Who are they?
Global is a RaaS (ransomware as a service) group that emerged in late June. The group has attacked organizations based in the United States, Great Britain, and Australia as well as other regions. Global’s activities have been associated with $$$, a BlackLock contributor, and they have a DLS (dedicated leak site) that features 16 posts. $$$ is an alias associated with the creation of several ransomware groups, including Mamoma and BlackLock, which were both defaced by DragonForce in March.
How many victims have they claimed?
Global has claimed 16 victims since its start in June. In comparison, BlackLock claimed 9 victims in June and has accumulated 33 victims since its rebrand from El Dorado in the fall of 2024.
What are they offering?
Global markets its locker as the fastest currently available with support for Windows, ESXi, and NAS systems. According to correspondence from their DLS, it also offers other capabilities, including EDR evasion, partial encryption to expedite the locking process, and a self-delete option. The Global panel is bundled with various features, including 24/7 support, a mobile version, regular updates, expanded storage, AI-driven support, and a negotiation panel.
What separates Global from BlackLock?
While $$$ is the alias that connects the BlackLock and Global entities, the RaaS panels for each may suit different affiliates. The Global platform provides a system for affiliates who may need greater support with a ready-made solution to thrive. In contrast, BlackLock RaaS operations have been reported as exercising great discretion and also requiring some specialization. Internal teams and collaborators may take on roles essential for Initial Access Broker type services or other tasks such as code development. One of BlackLock’s hallmarks has also been its incorporation of code written in Go.
What might this mean for future operations?
Global is in a lucrative position, opening their doors to affiliates who may need a structured, pre-packaged toolkit built with resources to fill gaps that exist in their own operational plans. A profit of 85% of any earnings collected from campaigns for affiliates and the omission of any deposit in the process also creates ample opportunities for potential affiliates to join with fewer concerns over financial deficits.
It is unknown if DragonForce has some stake in BlackLock following their defacement of Mamona and the BlackLock data leak sites. As a result, BlackLock’s and by extension Global’s ties to DragonForce have yet to be validated. While Global does not replace BlackLock, if one were displaced by DragonForce, it could spell trouble for the other, resulting in the loss of their affiliates or connected resources.
Ransomware Awareness and Defense
Ransomware threats, from small and insular extortion groups to large, allied networks, continue to present great challenges for organizations seeking to protect their assets and reputation. As the threat landscape undergoes frequent changes, understanding the elements that influence ransomware operations and a successful or unsuccessful compromise is vital to implement a sound and informed defensive strategy.
For a comprehensive analysis of the current ransomware playbook, including how these attacks are executed and how to defend against them, read our frequently updated ransomware whitepaper.
Additional Ransomware News
Now, let’s explore other notable shifts and findings since last month’s Threat Debrief.
- Qilin claims the greatest number of victims and adds a strategic feature: Qilin set a record by claiming 89 victims in a month, the group’s highest total to date. The group also added a Call Lawyer feature to its affiliate panel. The feature is intended to offer affiliates legal guidance and a scheme to exert additional pressure on victims. This feature comes several months after other updates to the panel, such as the Distributed Denial of Service functionality, were released.
- REvil cybercriminals are released: Four REvil members convicted in 2022 for their involvement in the group’s ransomware operations are out of jail. Andrei Bessonov, Mikhail Golovachuk, Roman Muromsky, and Dmitry Korotayev were freed from Russian custody for serving more than three years in pre-trial detention. This ruling comes nearly a year after a separate case involving the sentencing of REvil members Daniil Puzyrevsky, Ruslan Khansvyarov, Alexei Malozemov, and Artem Zayets; these members refuted their charges and have sentences ranging from 4.5 to 6 years.
- A DragonForce ransomware variant emerges: Devman is a ransomware group that has now been connected with a DragonForce variant. DragonForce gained notoriety for operating as a ransomware cartel, likely to pressure rivals and emerging groups into joining forces with them. The DragonForce variant has several unusual characteristics, including the encryption of a ransom note. Devman completed their RaaS release project, Devman 2.0, this month. The group has published multiple ransoms ranging from $60,000 to $10 million. While the extent of Devman’s relationship with DragonForce remains unclear, it came to light months after Devman’s affiliation with Qilin.
- Scattered Spider attacks organizations in aviation and transportation: The hacker group initially connected to attacks against retail organizations, employing techniques also used by DragonForce, has recently launched attacks against organizations providing transit services. Scattered Spider continues to pose a significant threat to organizations as they leverage social engineering tactics such as impersonation to bypass conventional controls and gain privileged access to critical systems.
- Hunters International announces the end of their operations a second time: Despite the announcement, a working theory persists to refute the finality of this claim. Hunters may instead have regrouped under the name World Leaks, operating with a focus on data exfiltration instead of encryption. World Leaks has claimed more than 25 victims since initial reports of their data theft activities were published in April. That total surpasses the number of victims that Hunters International claimed in previous months, as Hunters averaged just over 7 victims a month.
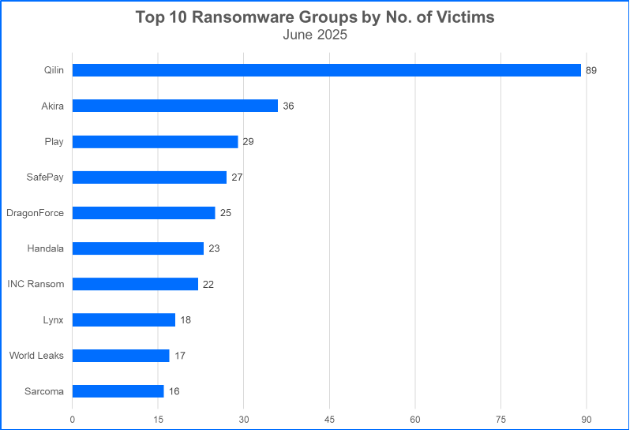
Top 10 Ransomware Families
Bitdefender's Threat Debrief analyzes data from ransomware leak sites, where groups publicize their claimed number of compromised organizations. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and may be unreliable. Additionally, this method only captures the number of victims claimed, not the actual financial impact of these attacks.
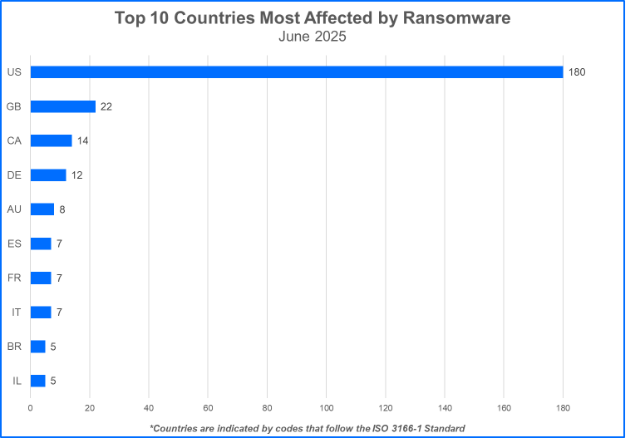
Top 10 Countries Targeted by Ransomware
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. Now, let’s see the top 10 countries that took the biggest hit from these attacks.
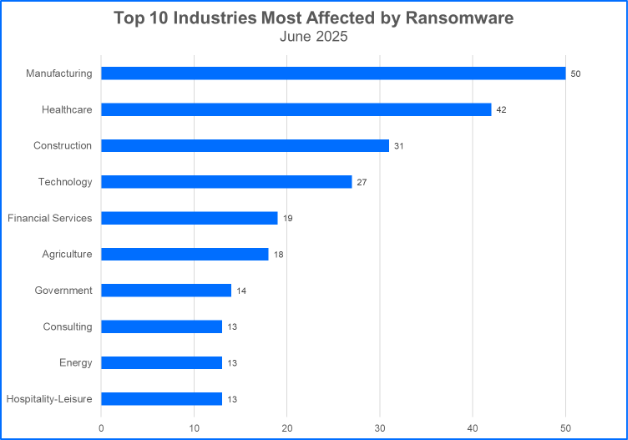
Top 10 Industries
Ransomware gangs may target organizations in the critical infrastructure ecosystem, select other organizations that offer services tailored to the consumer marketplace, or attack both. Here are the Top 10 industries that were hit by ransomware groups.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Gabriel Macovei, Andrei Mogage, and Rares Radu for their help putting this report together.
tags
Author
Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsYou might also like
Bookmarks

