Bitdefender Threat Debrief | June 2025

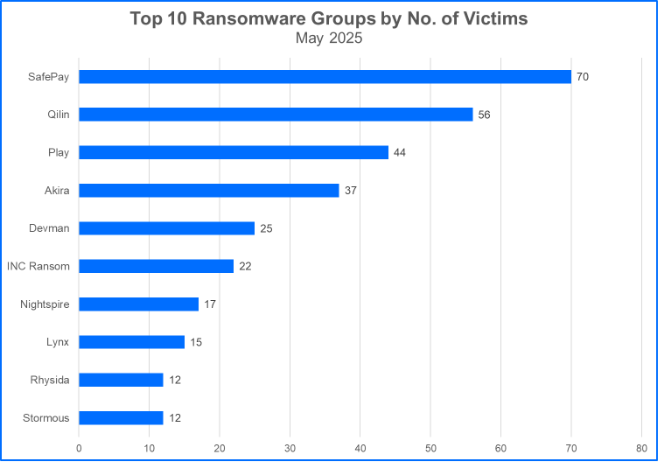
SafePay Ransomware Surpasses Qilin and Play, Claiming the Greatest Number of Victims in May
This month's Threat Debrief covers several shifts in the ransomware ecosystem, including SafePay’s recent increase in victims, a strategic leak of Conti and TrickBot data, plus the latest exploits leveraged by Qilin and other groups.
Ransomware is a moving target, and our goal with this monthly Bitdefender Threat Debrief is to help you stay ahead of the curve. To do this, we combine information from openly available sources (OSINT) - things like news reports and research – with data we gather by analyzing Data Leak Sites (DLSs), websites where ransomware groups post details about their victims. It’s important to remember that we can't independently verify all of these claims but are confident in the trends we see over time.
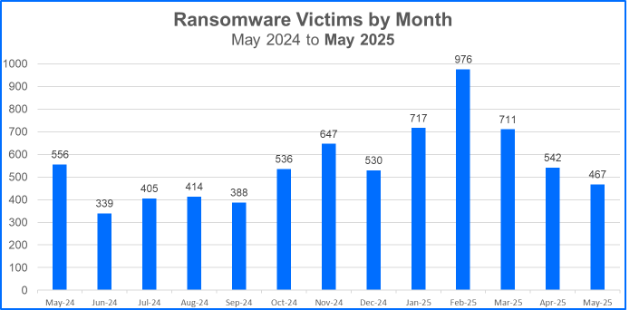
For this month's report, we analyzed data from May 1 to May 31 and recorded a total of 467 victims claimed.
Featured Story: SafePay Surpasses Qilin and Play, Claiming the Greatest Number of Victims in May
Who are they?
SafePay is a ransomware group that was discovered in the fall of 2024. The group claims that they have not and do not offer Ransomware-as-a-Service (RaaS). While simplistic in nature, lacking a blog or open forum, their data leak site lists victims and stolen data.
What systems and industries have been affected by SafePay?
SafePay binaries have several iterations to attack not only endpoints, but also hypervisors. Once executed, systems are encrypted, and the .safepay extension is appended to affected files and directories. The top industries represented in their victim demographic are currently manufacturing, healthcare, education and research, consulting, and government.
How many victims have they claimed?
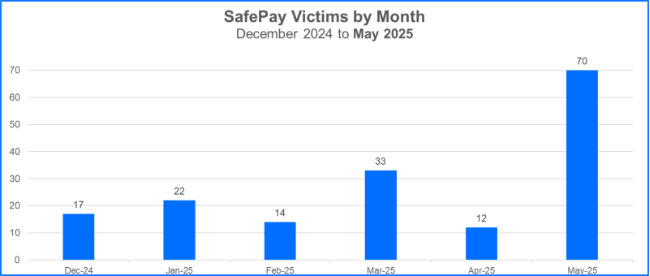
To date, SafePay has claimed more than 200 victims. They claimed 70 victims in May, more than doubling the prior record set for their highest number of victims claimed per month. Their second highest number of victims claimed per month, 33, was reported in March of this year.
How is LockBit involved?
SafePay has used ransomware that features code elements found in LockBit 3.0. Excluding the use of this code in a time following the LockBit builder leak, there are no other known links between LockBit and SafePay. SafePay does however have a Cyrillic kill switch functionality, meaning that if it identifies that a Cyrillic language keyboard is set, it will not execute the ransomware. This leads many to identify SafePay as a potential Russian-affiliated or allied threat actor.
What tactics has SafePay used?
SafePay has leveraged PowerShell scripts for reconnaissance and post-exploitation tasks. They’ve also used Living Off the Land tactics to inhibit system recovery methods and disable Windows Defender. Indicators of data exfiltration are tied back to repeatedly observed activities that involve WinRAR and the use of command line tools or in some cases, FTP.
Ransomware Awareness and Defense
Ransomware groups may experience ebbs and flows in their operations over time. This may be due to several factors, including the success rate of opportunistic attacks or modeling attacks based on tactics employed by past threat actors. It is essential to stay informed about relevant threats and the measures you can take to secure your organization’s assets and reduce the likelihood of a successful ransomware attack.
For a comprehensive analysis of the current ransomware playbook, including how these attacks are executed and how to defend against them, please read our Ransomware whitepaper.
Notable Ransomware News
Now, let’s explore other notable news and findings since our last Threat Debrief release.
- Conti and TrickBot operations exposed: A leaker known as GangsExposed published files and names associated with Conti and TrickBot campaigns on a Telegram channel. The leak includes correspondence between Conti leadership, photos, and other data that dates back to 2020. One alleged leader in those ransomware operations, Stern or Vitaly Nikolaevich Kovalev, was identified by German authorities and may reside in Russia.
- Critical Fortinet vulnerabilities are exploited in Qilin attacks: Qilin claimed the second rank in this month’s Top 10 ransomware groups. This threat actor has exploited CVE-2024-21762 and CVE-2024-55591 in recent campaigns. These flaws pose a significant threat to environments that feature affected Fortinet/FortiGate systems, as most zero-day flaws do. It is advised that organizations review their latest patches to ensure their systems are up to date.
- The next chapter of Operation Endgame disrupts cybercrime operations: A joint effort by Europol and other law enforcement agencies in France, Germany, Canada, and the United Kingdom, has resulted in the seizure of illicit domains and nearly 4 million USD in cryptocurrency. Distribution channels for several ransomware strains, including Oakbot, DanBot, and TrickBot were eradicated. The AVCheck domain was also seized, barring cybercriminals from accessing a service to test their crypted malware samples against anti-virus services.
- Ransomware group Datacarry emerges with a climbing victim count: Datacarry is a ransomware group that emerged a few weeks ago. Datacarry has claimed more than 10 victims at the time of this Threat Debrief publication, claiming victim organizations based in the United States, Belgium, Great Britain, and Switzerland. Their data leak site is also unique; although it is not as interactive as others, it features a desktop-like interface that allows visitors to navigate to folders containing leaked data.
- IMN Crew adds 8 victims to its DLS: IMN Crew is a newer ransomware group that claimed 8 victims in May. They’ve had a data leak site for over a month and have published data stolen from victim organizations based in the United States, Great Britain, Indonesia, and Sweden.
- The FBI and CISA publish a joint advisory with updates on Play: The publication highlights some changes since the last advisory, including patterns in Play’s correspondence with victims by both email and phone. The group continues to launch attacks against critical infrastructure and also exploits vulnerabilities in the SimpleHelp RMM tool to execute remote code.
Top 10 Ransomware Families
Bitdefender's Threat Debrief analyzes data from ransomware leak sites, where groups publicize their claimed number of compromised organizations. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and may be unreliable. Additionally, this method only captures the number of victims claimed, not the actual financial impact of these attacks.
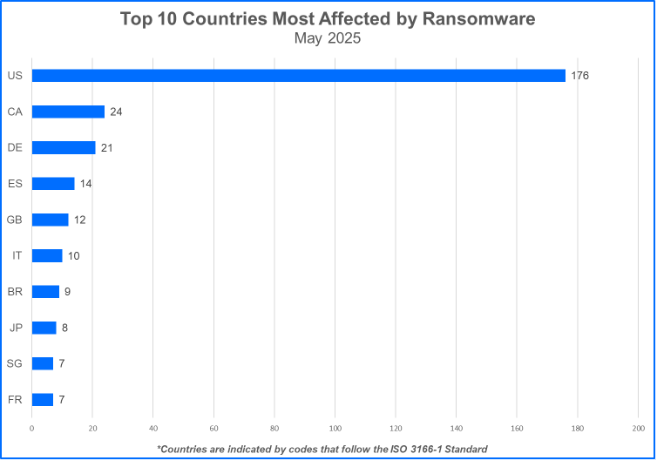
Top 10 Countries
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on countries with large or growing economies. Now, let’s see the top 10 countries that took the biggest hit from these attacks.
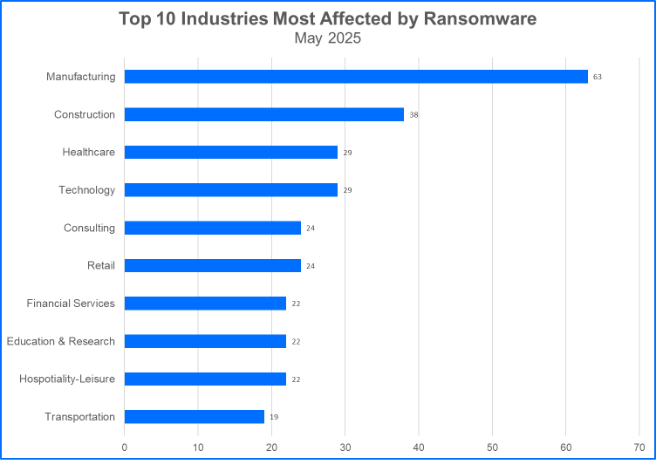
Top 10 Industries
Ransomware gangs may target organizations in the critical infrastructure ecosystem, select other organizations that offer services tailored to the consumer marketplace, or attack both. Here are the Top 10 industries that have been targeted by ransomware groups.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can also read our previous Threat Debrief, here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This provides us with one of the industry’s most comprehensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Gabriel Macovei, Andrei Mogage, and Rares Radu (sorted alphabetically) for their help putting this report together.
tags
Author
Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











